针对某系统XXE漏洞分析
 Met32
Met32- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
1.XXE分析
某系统XXE漏洞分析,去年的东西,目前补丁以及新版本已经修复。
由于网上文章调用栈不全,为此分析
首先在Filter中CTPSecurityFilter中有校验
完整doFilter如下:
public void doFilter(ServletRequest request, ServletResponse response, FilterChain filterChain) throws IOException, ServletException {
CanalMapMonitor.startMonitor((HttpServletRequest)request);
try {
TraceFilter.insertIntoMDC((HttpServletRequest)request);
String queryString = ((HttpServletRequest)request).getQueryString();
if (null != queryString) {
Matcher matcher = this.pattern.matcher(queryString);
if (matcher.find()) {
securityLogger.info("url包含敏感信息:" + ((HttpServletRequest)request).getRequestURL() + "?" + queryString);
}
}
String tenantId;
if (SystemEnvironment.isCloudDeployMode()) {
StringBuffer url = ((HttpServletRequest)request).getRequestURL();
String uri = ((HttpServletRequest)request).getRequestURI();
String scheme = request.getScheme() + "://";
String contextUrl = url.substring(scheme.length(), url.length() - uri.length());
tenantId = MultiTenantConfigInitializer.getTenantIdByDomainName(contextUrl);
} else {
if (contextName == null) {
contextName = SystemEnvironment.getContextPath().substring(1);
}
tenantId = contextName;
}
AppContext.removeThreadContext("REQUIRE_CHECK_GUEST");
AppContext.removeThreadContext("REQUIRE_VALIDATE_USER_ROLE");
AppContext.setCurrentTenantId(tenantId);
CTPSecurityFilter.Result result = authenticate(request, response);
if (result.getAuthenticator().directReturn((HttpServletRequest)request)) {
return;
}
User currentUser = AppContext.getCurrentUser();
if (currentUser != null) {
try {
LoginOpt.refreshOnlineUser(currentUser);
} catch (BusinessException var34) {
logger.error("", var34);
}
}
if (result.getResult()) {
StringBuilder resourceKey = new StringBuilder();
if (this.isProtectedUri((HttpServletRequest)request, resourceKey)) {
try {
Entry entry = SphU.entry(resourceKey.toString());
Throwable var10 = null;
try {
filterChain.doFilter(request, response);
} catch (Throwable var33) {
var10 = var33;
throw var33;
} finally {
if (entry != null) {
if (var10 != null) {
try {
entry.close();
} catch (Throwable var31) {
var10.addSuppressed(var31);
}
} else {
entry.close();
}
}
}
} catch (BlockException var36) {
this.sendErrorWhenNotHttp(response);
}
} else {
filterChain.doFilter(request, response);
}
} else if (response instanceof HttpServletResponse) {
try {
result.getAuthenticator().afterFailure((HttpServletRequest)request, (HttpServletResponse)response);
} catch (Exception var) {
throw new IOException(var);
}
} else {
this.sendErrorWhenNotHttp(response);
}
} finally {
AppContext.removeCurrentTenantId();
AppContext.clearThreadContext();
TraceFilter.clearMDC();
CanalMapMonitor.stopMonitor();
}
}跟进authenticate方法
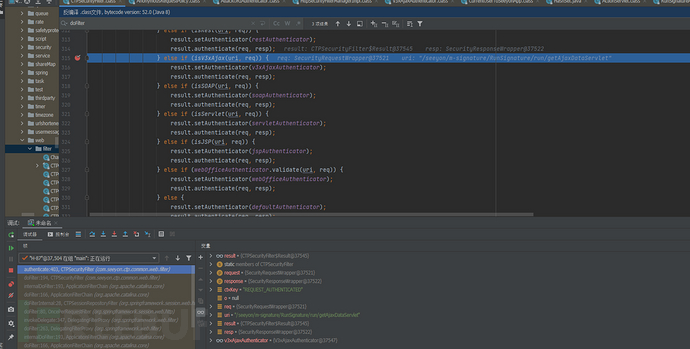
此处判断为如下:
private static boolean isV3xAjax(String uri, HttpServletRequest request) {
return uri.endsWith("getAjaxDataServlet");
}并将该map进行了设置
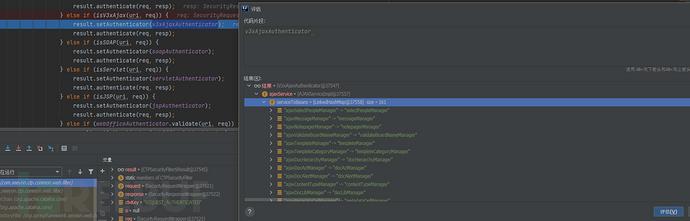
在authenticate中,可以发现获取了GET参数获取到了S和M
可试读前30%内容
¥ 9.9 全文查看
9.9元开通FVIP会员
畅读付费文章
畅读付费文章
最低0.3元/天
免责声明
1.一般免责声明:本文所提供的技术信息仅供参考,不构成任何专业建议。读者应根据自身情况谨慎使用且应遵守《中华人民共和国网络安全法》,作者及发布平台不对因使用本文信息而导致的任何直接或间接责任或损失负责。
2. 适用性声明:文中技术内容可能不适用于所有情况或系统,在实际应用前请充分测试和评估。若因使用不当造成的任何问题,相关方不承担责任。
3. 更新声明:技术发展迅速,文章内容可能存在滞后性。读者需自行判断信息的时效性,因依据过时内容产生的后果,作者及发布平台不承担责任。
本文为 Met32 独立观点,未经授权禁止转载。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
一文读懂Xpath注入与利用
2023-12-18
剖析哥斯拉WebShell管理工具
2023-09-04
浅析白盒白名单SQL注入绕过利用
2023-08-02
文章目录










