Threatcl:一款威胁模型记录与归档工具
关于Threatcl
Threatcl是一款功能强大的威胁记录模型,可以帮助广大研究人员更加清楚地记录威胁,并推动安全态势的提升。

威胁模型的记录方式有很多种。从简单的文本文件到更详细的 Word 文档,再到集中式解决方案中完全装备的威胁模型。威胁模型最有价值的两个属性是能够清晰地记录威胁,并能够推动有价值的变革。
功能介绍
Threatcl旨在通过关注以下目标,提供 DevOps 优先的方法来记录系统威胁模型:
1、简单文本文件格式;
2、简单的客户端驱动用户体验;
3、集成到版本控制系统 (VCS);
工具要求
Go
工具安装
由于该工具基于Go开发,因此我们首先需要在本地设备上安装并配置好最新版本的Go环境。
源码获取
广大研究人员可以直接使用下列命令将该项目源码克隆至本地:
git clone https://github.com/threatcl/threatcl.git
然后切换到项目目录中,使用下列命令构建项目代码:
cd threatcl make bootstrap make build
发布版本
我们还可以直接访问该项目的【Releases页面】下载最新版本的Threatcl,并将相关二进制文件移动到PATH下。
Homoebrew安装
brew install threatcl/repo/threatcl
Docker运行
docker run --rm -it ghcr.io/threatcl/threatcl:latest
工具使用
$ threatcl Usage: threatcl [--version] [--help] <command> [<args>] Available commands are: dashboard 从现有的HCL威胁模型文件生成标记文件 dfd 从现有的HCL威胁模型文件生成数据流图PNG或DOT文件 export 将威胁模型导出为其他格式 generate 生成HCL威胁模型 list 列出HCL文件中发现的威胁模型 terraform 解析'terraform show-json'的输出 validate 验证现有的HCL Threatmodel文件 view 查看现有的HCL Threatmodel文件
hreatcl list和命令threatcl view可用于列出和查看来自threatcl spec HCL 文件中的数据:
$ threatcl list examples/* # File Threatmodel Author 1 examples/tm1.hcl Tower of London @xntrik 2 examples/tm1.hcl Fort Knox @xntrik 3 examples/tm2.hcl Modelly model @xntrik
验证Threatcl规范 HCL 文件:
$ threatcl validate examples/* Validated 3 threatmodels in 3 files
该threatcl export命令用于将threatcl威胁模型导出为本机 JSON 表示形式(默认情况下),或导出为OTM JSON 表示形式,甚至导出回hcl:
$ threatcl export -format=otm examples/tm1.hcl
[{"assets":[{"description":"including the imperial state crown","id":"crown-jewels","name":"crown jewels","risk":{"availability":0,"confidentiality":0,"integrity":0}}],"mitigations":[{"attributes":{"implementation_notes":"They are trained to be guards as well","implemented":true},"description":"Lots of guards patrol the area","id":"lots-of-guards","name":"Lots of Guards","riskReduction":80}],"otmVersion":"0.2.0","project":{"attributes":{"initiative_size":"Small","internet_facing":true,"network_segment":"dmz","new_initiative":true},"description":"A historic castle","id":"tower-of-london","name":"Tower of London","owner":"@xntrik"},"threats":[{"categories":["Confidentiality"],"description":"Someone who isn't the Queen steals the crown","id":"threat-1","name":"Threat 1","risk":{"impact":0,"likelihood":null}}]},{"assets":[{"description":"Lots of gold","id":"gold","name":"Gold","risk":{"availability":0,"confidentiality":0,"integrity":0}}],"mitigations":[{"attributes":{"implemented":true},"description":"A large wall surrounds the fort","id":"big-wall","name":"Big Wall","riskReduction":80}],"otmVersion":"0.2.0","project":{"attributes":{"initiative_size":"Small","internet_facing":true,"new_initiative":false},"description":"A .. fort?","id":"fort-knox","name":"Fort Knox","owner":"@xntrik"},"threats":[{"categories":["Confidentiality"],"description":"Someone steals the gold","id":"threat-1","name":"Threat 1","risk":{"impact":0,"likelihood":null}}]}]threatcl generate命令用于输出通用boilerplate threatcl规范 HCL 文件,或者以交互方式向用户提问,然后输出threatcl规范 HCL 文件:
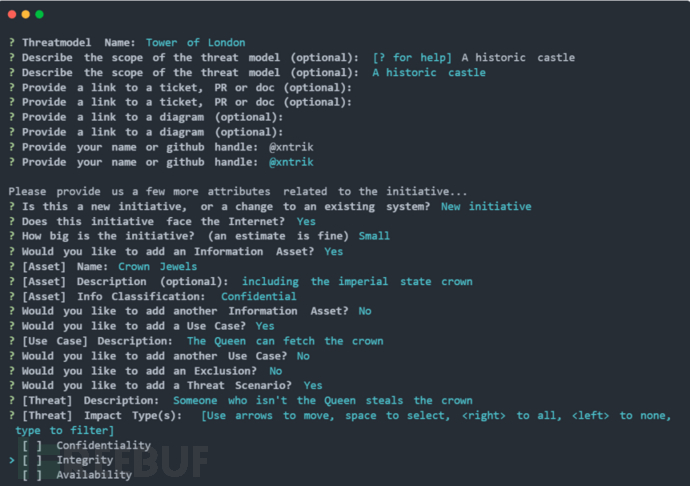
threatcl generate interactive
将threatclcli 软件和threatcl规范结合起来,从业者可以在 HCL 中定义系统威胁模型,例如:
threatmodel "Tower of London" {
description = "A historic castle"
author = "@xntrik"
attributes {
new_initiative = "true"
internet_facing = "true"
initiative_size = "Small"
}
information_asset "crown jewels" {
description = "including the imperial state crown"
information_classification = "Confidential"
}
usecase {
description = "The Queen can fetch the crown"
}
third_party_dependency "community watch" {
description = "The community watch helps guard the premise"
uptime_dependency = "degraded"
}
threat {
description = "Someone who isn't the Queen steals the crown"
impacts = ["Confidentiality"]
expanded_control "Guards" {
description = "Trained guards patrol tower"
risk_reduction = 75
}
}
data_flow_diagram_v2 "dfd name" {
// ... see below for more information
}
}工具运行演示
许可证协议
本项目的开发与发布遵循MIT开源许可协议。
项目地址
Threatcl:【GitHub传送门】
参考资料
本文为 独立观点,未经允许不得转载,授权请联系FreeBuf客服小蜜蜂,微信:freebee2022
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐
文章目录





