Afuzz:一款功能强大的自动化Web路径模糊测试工具
 Alpha_h4ck
Alpha_h4ck- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
Afuzz:一款功能强大的自动化Web路径模糊测试工具
 本文由
Alpha_h4ck 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
Alpha_h4ck 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载

关于Afuzz
Afuzz是一款功能强大的自动化Web路径模糊测试工具,该工具专为Web安全专家和漏洞奖励Hunter设计,可以帮助我们以自动化的形式扫描和收集目标Web应用程序中的页面、语言和相关统计分析等数据。
功能介绍
1、Afuzz可以通过自动化的形式检测目标Web应用程序所使用的开发语言;
2、使用黑名单过滤无效页面;
3、使用白名单寻找漏洞奖励Hunter感兴趣的页面内容;
4、过滤页面中的随机内容;
5、以多种方式判断404错误页面;
6、扫描完成后执行统计数据分析,并生成最终的结果;
7、支持HTTP2;
工具安装
由于该工具基于Python开发,因此我们首先需要在本地设备上安装并配置好Python环境。接下来,广大研究人员可以直接使用下列命令将该项目源码克隆至本地:
git clone https://github.com/rapiddns/Afuzz.git
然后切换到项目目录中,使用pip工具和项目提供的requirements.txt文件安装该工具所需的其他依赖组件:
cd Afuzz pip install -r requirements.txt
依赖组件安装完成后,执行下列安装脚本即可:
python setup.py install
除此之外,我们还可以直接使用pip工具安装Afuzz:
pip install afuzz
工具选项
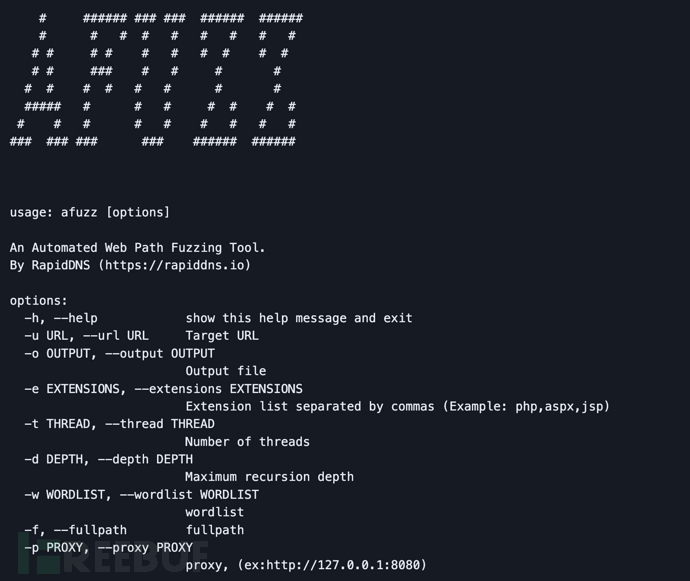
参数解释
-h, --help 显示工具帮助信息和退出 -u URL, --url URL 设置目标URL -o OUTPUT, --output OUTPUT 输出文件路径 -e EXTENSIONS, --extensions EXTENSIONS 扩展列表,逗号分隔 (例如: php,aspx,jsp) -t THREAD, --thread THREAD 线程数量 -d DEPTH, --depth DEPTH 最大递归深度 -w WORDLIST, --wordlist WORDLIST 字典文件路径 -f, --fullpath 完整路径 -p PROXY, --proxy PROXY 代理, (例如:http://127.0.0.1:8080)
工具运行
使用命令
afuzz -u https://target
afuzz -e php,html,js,json -u https://target
afuzz -e php,html,js -u https://target -d 3
多线程使用
afuzz -e aspx,jsp,php,htm,js,bak,zip,txt,xml -u https://target -t 50
工具运行样例
afuzz -u http://testphp.vulnweb.com -t 30
扫描结果
数据表
+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+ | http://testphp.vulnweb.com/ | +-----------------------------+---------------------+--------+-----------------------------------+-----------------------+--------+--------------------------+-------+-------+-----------+----------+ | target | path | status | redirect | title | length | content-type | lines | words | type | mark | +-----------------------------+---------------------+--------+-----------------------------------+-----------------------+--------+--------------------------+-------+-------+-----------+----------+ | http://testphp.vulnweb.com/ | .idea/workspace.xml | 200 | | | 12437 | text/xml | 217 | 774 | check | | | http://testphp.vulnweb.com/ | admin | 301 | http://testphp.vulnweb.com/admin/ | 301 Moved Permanently | 169 | text/html | 8 | 11 | folder | 30x | | http://testphp.vulnweb.com/ | login.php | 200 | | login page | 5009 | text/html | 120 | 432 | check | | | http://testphp.vulnweb.com/ | .idea/.name | 200 | | | 6 | application/octet-stream | 1 | 1 | check | | | http://testphp.vulnweb.com/ | .idea/vcs.xml | 200 | | | 173 | text/xml | 8 | 13 | check | | | http://testphp.vulnweb.com/ | .idea/ | 200 | | Index of /.idea/ | 937 | text/html | 14 | 46 | whitelist | index of | | http://testphp.vulnweb.com/ | cgi-bin/ | 403 | | 403 Forbidden | 276 | text/html | 10 | 28 | folder | 403 | | http://testphp.vulnweb.com/ | .idea/encodings.xml | 200 | | | 171 | text/xml | 6 | 11 | check | | | http://testphp.vulnweb.com/ | search.php | 200 | | search | 4218 | text/html | 104 | 364 | check | | | http://testphp.vulnweb.com/ | product.php | 200 | | picture details | 4576 | text/html | 111 | 377 | check | | | http://testphp.vulnweb.com/ | admin/ | 200 | | Index of /admin/ | 248 | text/html | 8 | 16 | whitelist | index of | | http://testphp.vulnweb.com/ | .idea | 301 | http://testphp.vulnweb.com/.idea/ | 301 Moved Permanently | 169 | text/html | 8 | 11 | folder | 30x | +-----------------------------+---------------------+--------+-----------------------------------+-----------------------+--------+--------------------------+-------+-------+-----------+----------+```
JSON格式数据
{
"result": [
{
"target": "http://testphp.vulnweb.com/",
"path": ".idea/workspace.xml",
"status": 200,
"redirect": "",
"title": "",
"length": 12437,
"content_type": "text/xml",
"lines": 217,
"words": 774,
"type": "check",
"mark": "",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/.idea/workspace.xml"
},
{
"target": "http://testphp.vulnweb.com/",
"path": "admin",
"status": 301,
"redirect": "http://testphp.vulnweb.com/admin/",
"title": "301 Moved Permanently",
"length": 169,
"content_type": "text/html",
"lines": 8,
"words": 11,
"type": "folder",
"mark": "30x",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/admin"
},
{
"target": "http://testphp.vulnweb.com/",
"path": "login.php",
"status": 200,
"redirect": "",
"title": "login page",
"length": 5009,
"content_type": "text/html",
"lines": 120,
"words": 432,
"type": "check",
"mark": "",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/login.php"
},
{
"target": "http://testphp.vulnweb.com/",
"path": ".idea/.name",
"status": 200,
"redirect": "",
"title": "",
"length": 6,
"content_type": "application/octet-stream",
"lines": 1,
"words": 1,
"type": "check",
"mark": "",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/.idea/.name"
},
{
"target": "http://testphp.vulnweb.com/",
"path": ".idea/vcs.xml",
"status": 200,
"redirect": "",
"title": "",
"length": 173,
"content_type": "text/xml",
"lines": 8,
"words": 13,
"type": "check",
"mark": "",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/.idea/vcs.xml"
},
{
"target": "http://testphp.vulnweb.com/",
"path": ".idea/",
"status": 200,
"redirect": "",
"title": "Index of /.idea/",
"length": 937,
"content_type": "text/html",
"lines": 14,
"words": 46,
"type": "whitelist",
"mark": "index of",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/.idea/"
},
{
"target": "http://testphp.vulnweb.com/",
"path": "cgi-bin/",
"status": 403,
"redirect": "",
"title": "403 Forbidden",
"length": 276,
"content_type": "text/html",
"lines": 10,
"words": 28,
"type": "folder",
"mark": "403",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/cgi-bin/"
},
{
"target": "http://testphp.vulnweb.com/",
"path": ".idea/encodings.xml",
"status": 200,
"redirect": "",
"title": "",
"length": 171,
"content_type": "text/xml",
"lines": 6,
"words": 11,
"type": "check",
"mark": "",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/.idea/encodings.xml"
},
{
"target": "http://testphp.vulnweb.com/",
"path": "search.php",
"status": 200,
"redirect": "",
"title": "search",
"length": 4218,
"content_type": "text/html",
"lines": 104,
"words": 364,
"type": "check",
"mark": "",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/search.php"
},
{
"target": "http://testphp.vulnweb.com/",
"path": "product.php",
"status": 200,
"redirect": "",
"title": "picture details",
"length": 4576,
"content_type": "text/html",
"lines": 111,
"words": 377,
"type": "check",
"mark": "",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/product.php"
},
{
"target": "http://testphp.vulnweb.com/",
"path": "admin/",
"status": 200,
"redirect": "",
"title": "Index of /admin/",
"length": 248,
"content_type": "text/html",
"lines": 8,
"words": 16,
"type": "whitelist",
"mark": "index of",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/admin/"
},
{
"target": "http://testphp.vulnweb.com/",
"path": ".idea",
"status": 301,
"redirect": "http://testphp.vulnweb.com/.idea/",
"title": "301 Moved Permanently",
"length": 169,
"content_type": "text/html",
"lines": 8,
"words": 11,
"type": "folder",
"mark": "30x",
"subdomain": "testphp.vulnweb.com",
"depth": 0,
"url": "http://testphp.vulnweb.com/.idea"
}
],
"total": 12,
"target": "http://testphp.vulnweb.com/"
}字典(重要)
1、Afuzz所使用的字典是一个text文本文件,每一个路径单独每一行;
2、关于后缀,Afuzz会使用-e参数提供的后缀替换%EXT%关键词,如果没设置-e的话,则使用默认值;
3、我们可以基于域名来生成字典,Afuzz可以使用主机替换%subdomain%,使用根域名替换%rootdomain%,使用子域名替换%sub%,使用域名替换%domain%;
使用样例
普通后缀:
index.%EXT%
设置asp和aspx后缀将生成下列字典:
index index.asp index.aspx
主机:
%subdomain%.%ext% %sub%.bak %domain%.zip %rootdomain%.zip
传递https://test-www.hackerone.com和php后缀将生成下列字典:
test-www.hackerone.com.php test-www.zip test.zip www.zip testwww.zip hackerone.zip hackerone.com.zip
项目地址
Afuzz:【GitHub传送门】
参考链接
免责声明
1.一般免责声明:本文所提供的技术信息仅供参考,不构成任何专业建议。读者应根据自身情况谨慎使用且应遵守《中华人民共和国网络安全法》,作者及发布平台不对因使用本文信息而导致的任何直接或间接责任或损失负责。
2. 适用性声明:文中技术内容可能不适用于所有情况或系统,在实际应用前请充分测试和评估。若因使用不当造成的任何问题,相关方不承担责任。
3. 更新声明:技术发展迅速,文章内容可能存在滞后性。读者需自行判断信息的时效性,因依据过时内容产生的后果,作者及发布平台不承担责任。
本文为 Alpha_h4ck 独立观点,未经授权禁止转载。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐
Tetragon:一款基于eBPF的运行时环境安全监控工具
2025-01-21
DroneXtract:一款针对无人机的网络安全数字取证工具
2025-01-21
CNAPPgoat:一款针对云环境的安全实践靶场
2025-01-21
文章目录











