
Pentest-Tools-Framework
Pentest-Tools-Framework是一个专为渗透测试设计的框架,其中包含了大量漏洞利用脚本、漏洞扫描器以及渗透测试工具。它是一款功能十分强大的框架,并给广大渗透测试初学者们提供了大量的工具,它甚至还可以帮助我们成功利用各种内核漏洞以及网络漏洞。
Pentest-Tools-Framework是一款免费的软件,并且非常适合渗透测试初学者使用。除此之外,该工具还提供了UX/UI接口,易于使用且方便管理。
工具安装
广大研究人员可以使用下列命令完成Pentest-Tools-Framework的下载、安装和配置:
root@kali~# git clone https://github.com/pikpikcu/Pentest-Tools-Framework.git
root@kali~# cd Pentest-Tools-Framework
root@kali~# pip install -r requirements.txt
root@kali~# python install.py
root@kali~# PTF
渗透模块
漏洞利用:
利用软件中的漏洞对计算机系统进行攻击的计算机程序、代码或命令序列。攻击的目的可以是夺取对系统的控制权,并破坏其功能!
漏洞扫描:
扫描指定的Internet资源、存档或网站的程序。网络扫描器还可以扫描打开的端口或您的本地网络和IP!
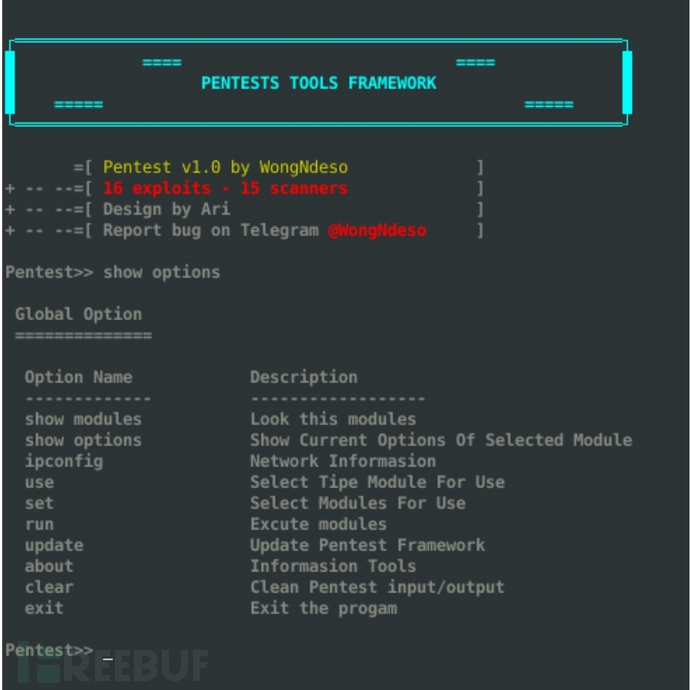
Pentest-Tools-Framework选项
-------------------------------------------------------------------------------------
| Global Option |
-------------------------------------------------------------------------------------
| Command Description |
|-----------------------------------------------------------------------------------|
| show modules | 查看模块 |
| show options | 显示当前模块信息 |
| ipconfig | 网络配置信息 |
| shell | 执行命令行Shell >[ctrl+C 退出shell ] |
| use | 选择需要使用的Tipe模块 |
| set | 选择需要使用的 |
| run | 执行模块 |
| update | 更新工具 |
| banner | PTF Banner |
| about | 关于工具 |
| credits | Credits && 鸣谢 |
| clear | 清除输入/输出 |
| exit | 退出程序 |
-------------------------------------------------------------------------------------
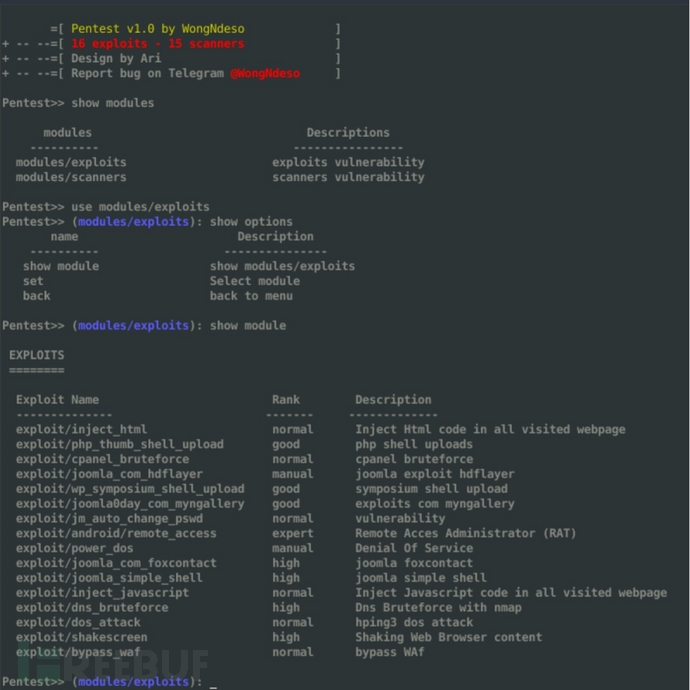
功能模块
漏洞利用/46
+-----------------------------------------------------------------------------------------------------------------------------------+
| EXPLOITS |
-------------------------------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
-------------------------------------------------------------------------------------------------------------------------------------
| exploit/abrt_privilege_escalation | normal | ABRT提权 |
| exploit/web_delivery | good | Web Delivery脚本 |
| exploit/apache | good | Apache漏洞利用 |
| exploit/shellshock | good | cgi-bin/漏洞shellshock |
| exploit/davtest | good | webdav 服务器测试 |
| exploit/auto_sql | good | 自动化sqlmap |
| exploit/ldap_buffer_overflow | normal | Apache模块mod_rewrite LDAP协议缓冲区溢出 |
| exploit/vbulletin_rce | good | vBulletin 5.x 0day pre-quth RCE 漏洞利用 |
| exploit/cmsms_showtime2_rce | normal | CMS Made Simple (CMSMS) Showtime2 文件上传RCE |
| exploit/awind_snmp_exec | good | AwindInc SNMP 服务命令注入 |
| exploit/webmin_packageup_rce | excellent | Webmin Package更新远程命令执行 |
| exploit/samsung_knox_smdm_url | good | Samsung Galaxy KNOX Android 浏览器远程命令执行 |
| exploit/cisco_dcnm_upload_2019 | excellent | Cisco数据中心网络管理器未认证远程代码执行 |
| exploit/zenworks_configuration | excellent | Novell ZENworks 配置管理任意文件上传 |
| exploit/cisco_ucs_rce | excellent | Cisco UCS Director 未验证的远程代码执行 |
| exploit/sonicwall | normal | Sonicwall SRA <= v8.1.0.2-14sv 远程漏洞利用 |
| exploit/bluekeep | good | cve 2019 0708 bluekeep远程代码执行 |
| exploit/eternalblue | good | MS17-010 EternalBlue SMB 远程 Windows 内核池崩溃 |
| exploit/inject_html | normal | 向所有已访问页面注入HTML代码 |
| exploit/robots | normal | robots.txt 检测 |
| exploit/jenkins_script_console | good | Jenkins-CI Script-Console Java 执行 |
| exploit/php_thumb_shell_upload | good | php shell 上传 |
| exploit/cpanel_bruteforce | normal | cpanel b爆破 |
| exploit/cms_rce | normal | CMS Made Simple 2.2.7 - (已验证) 远程代码执行 |
| exploit/joomla_com_hdflayer | manual | joomla漏洞利用 |
| exploit/wp_symposium_shell_upload | good | symposium shell upload |
| exploit/joomla0day_com_myngallery | good | exploits com myngallery |
| exploit/jm_auto_change_pswd | normal | 漏洞扫描 |
| exploit/android_remote_access | expert | Remote Acces Administrator (RAT) |
| exploit/power_dos | manual | 拒绝服务 |
| exploit/tp_link_dos | normal | TP_LINK DOS, 150M Wireless Lite N Router, Model No. TL-WR740N |
| exploit/joomla_com_foxcontact | high | joomla foxcontact |
| exploit/joomla_simple_shell | high | joomla 简单 shell |
| exploit/joomla_comfields_sqli_rce | high | Joomla Component Fields SQLi 远程代码执行 |
| exploit/inject_javascript | normal | 向所有已访问页面注入JS代码 |
| exploit/dns_bruteforce | high | nmap DNS爆破 |
| exploit/dos_attack | normal | hping3 dos 攻击 |
| exploit/shakescreen | high | 震动Web 浏览器内容 |
| exploit/bypass_waf | normal | 绕过WAF |
| exploit/enumeration | high | 简单枚举 |
| exploit/restrict_anonymous | normal | 凭证获取 |
| exploit/openssl_heartbleed | high | 导出 openssl_heartbleed |
| exploit/samba | good | Samba 漏洞利用 |
| exploit/smb | good | lbitary samba exploit |
| exploit/webview_addjavascriptinterface | good | Android 浏览器和We |
| exploit/webview_addjavascriptinterface | good | Android 浏览器和WebView addJavascriptInterface代码执行 |
-------------------------------------------------------------------------------------------------------------------------------------
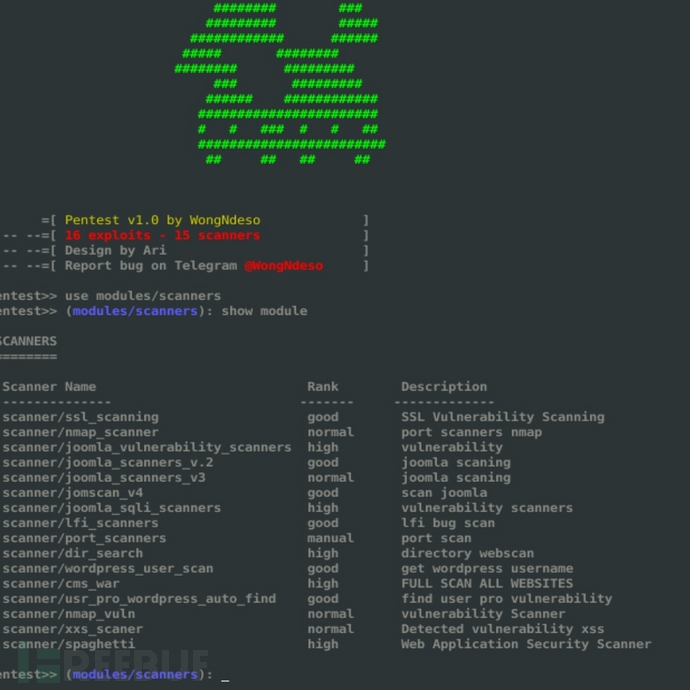
扫描器/59
+------------------------------------------------------------------------------------------------------------------------------------+
| SCANNERS |
--------------------------------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
--------------------------------------------------------------------------------------------------------------------------------------
| scanner/enumiax | good | 协议用户名枚举 |
| scanner/wordpress_user_dislosure | normal | wordpress 5.3 用户披露 |
| scanner/botnet_scanning | normal | 僵尸网络扫描 |
| scanner/check_ssl_certificate | normal | SSL 证书 |
| scanner/http_services | normal | 从HTTP服务收集页面标题 |
| scanner/dnsrecon | normal | 记录枚举 |
| scanner/sslscan | normal | SSL 扫描 |
| scanner/ssl_cert | normal | Nmap 脚本ssl-cert |
| scanner/dns_zone_transfer | normal | Dns空间转移 |
| scanner/dns_bruteforce | normal | Dns 爆破 |
| scanner/zone_walking | normal | Zone walking |
| scanner/web_services | normal | 获取网站服务的HTTP头 |
| scanner/http_enum | normal | 查找已知路径的Web应用 |
| scanner/ddos_reflectors | normal | UDP DDOS 扫描 |
| scanner/grabbing_detection | normal | 轻量级 banner 收集检测 |
| scanner/discovery | normal | 端口扫描 |
| scanner/bluekeep | good | CVE-2019-0708 BlueKeep Microsoft 远程桌面 RCE 漏洞检测 |
| scanner/drupal_scan | good | drupal 扫描 |
| scanner/eternalblue | good | SMB RCE 漏洞检测 |
| scanner/header | good | nmap header扫描 |
| scanner/firewalk | good | firewalk |
| scanner/whois | high | whois 查询 |
| scanner/dmitry | good | 信息收集 |
| scanner/admin_finder | normal | Admin 查询 |
| scanner/heartbleed | normal | heartbleed漏洞扫描 |
| scanner/wordpress_scan | normal | wordpress漏洞扫描 |
| scanner/ssl_scanning | good | SSL漏洞扫描 |
| scanner/dns_bruteforce | normal | dns 爆破 |
| scanner/nmap_scanner | normal | nmap端口扫描 |
| scanner/https_discover | normal | https 扫描 |
| scanner/smb_scanning | good | SMB服务器漏洞扫描 |
| scanner/joomla_vulnerability_scanners | high | joomla漏洞扫描 |
| scanner/mysql_empty_password | good | mysql空密码检测 |
| scanner/joomla_scanners_v.2 | good | joomla漏洞扫描 |
| scanner/joomla_scanners_v3 | normal | joomla漏洞扫描 |
| scanner/jomscan_v4 | good | 扫描joomla |
| scanner/webdav_scan | normal | webdav漏洞扫描 |
| scanner/joomla_sqli_scanners | high | joomla漏洞扫描 |
| scanner/lfi_scanners | good | lfi漏洞扫描 |
| scanner/port_scanners | manual | 端口扫描 |
| scanner/dir_search | high | 目录扫描 |
| scanner/dir_bruteforce | good | 目录爆破 |
| scanner/wordpress_user_scan | good | 获取wordpress用户 |
| scanner/cms_war | high | 网站完整扫描 |
| scanner/usr_pro_wordpress_auto_find | norma | 查找用户漏洞 |
| scanner/nmap_vuln | normal | nmap漏洞扫描器 |
| scanner/xss_scaner | normal | xss漏洞检测 |
| scanner/spaghetti | high | Web 应用安全扫描器 |
| scanner/dnslookup | normal | dnslookup扫描 |
| scanner/reverse_dns | normal | DNS反向查询 |
| scanner/domain_map | normal | 域名映射 |
| scanner/dns_report | normal | dns 报告 |
| scanner/find_shared_dns | normal | 查找共享dns |
| scanner/golismero | normal | golismero扫描漏洞 |
| scanner/dns_propagation | low | dns 选举 |
| scanner/find_records | normal | 查询记录 |
| scanner/cloud_flare | normal | cloud flare |
| scanner/extract_links | normal | 链接提取 |
| scanner/web_robot | normal | web robots扫描器 |
| scanner/enumeration | normal | http枚举 |
| scanner/ip_locator | good | ip Detected LOcator |
--------------------------------------------------------------------------------------------------------------------------------------
POST/8
+----------------------------------------------------------------------------------------------------------+
| POST |
------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
------------------------------------------------------------------------------------------------------------
| post/enumeration | normal | http枚举 |
| post/vbulletin | high | 漏洞利用 |
| post/wordpress_user_scan | good | 扫描器 |
| post/dir_search | high | 扫描器 |
| post/cms_war | high | 扫描器 |
| post/usr_pro_wordpress_auto_find | normal | 扫描器 |
| post/android_remote_access | good | 漏洞利用 |
| post/samba | good | 漏洞利用 |
------------------------------------------------------------------------------------------------------------
密码/7
+----------------------------------------------------------------------------------------------------------+
| PASSWORD |
------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
------------------------------------------------------------------------------------------------------------
| password/base64_decode | good | base64解码 |
| password/md5_decrypt | good | md5解密 |
| password/sha1_decrypt | good | sha1解密 |
| password/sha256_decrypt | good | sha256解密 |
| password/sha384_decrypt | good | sha384解密 |
| password/sha512_decrypt | good | sha512解密 |
| password/ssh_bruteforce | good | ssh密码爆破 |
------------------------------------------------------------------------------------------------------------
监听器/14
+------------------------------------------------------------------------------------------------------------------------------------+
| LISTENERS MODULES |
--------------------------------------------------------------------------------------------------------------------------------------
| COMMANDS Rank Description |
--------------------------------------------------------------------------------------------------------------------------------------
| android_meterpreter_reverse_tcp | good | Android Meterpreter, Android Reverse TCP Stager |
| android_meterpreter_reverse_https | good | Android Meterpreter, Android Reverse HTTPS Stager |
| java_jsp_shell_reverse_tcp | good | Java JSP Command Shell, Reverse TCP Inline |
| linux_x64_meterpreter_reverse_https | good | linux/x64/meterpreter_reverse_https |
| linux_x64_meterpreter_reverse_tcp | good | Linux Meterpreter, Reverse TCP Inline |
| linux_x64_shell_reverse_tcp | good | Linux Command Shell, Reverse TCP Stager |
| osx_x64_meterpreter_reverse_https | good | OSX Meterpreter, Reverse HTTPS Inline |
| osx_x64_meterpreter_reverse_tcp | good | OSX Meterpreter, Reverse TCP Inline |
| php_meterpreter_reverse_tcp | good | PHP Meterpreter, PHP Reverse TCP Stager |
| python_meterpreter_reverse_https | good | Python Meterpreter Shell, Reverse HTTPS Inline |
| python_meterpreter_reverse_tcp | good | python/meterpreter_reverse_tcp |
| windows_x64_meterpreter_reverse_https | good | Windows Meterpreter Shell, Reverse HTTPS Inline (x64) |
| windows_x64_meterpreter_reverse_tcp | good | Windows Meterpreter Shell, Reverse TCP Inline x64 |
| cmd_windows_reverse_powershell | good | Windows Command Shell, Reverse TCP (Powershell) |
+------------------------------------------------------------------------------------------------------------------------------------+
工具运行截图
查看帮助信息:
扫描器:
渗透模块:
项目地址
Pentest-Tools-Framework:【GitHub传送门】
* 参考来源:pikpikcu,FB小编Alpha_h4ck编译,转载请注明来自FreeBuf.COM
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





