 本文由
我有一个小毛驴我从来都不骑 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
我有一个小毛驴我从来都不骑 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
作者:天启@涂鸦智能安全实验室
前言:
上一篇文章,介绍了如何使用burpsuite自带的project option配置文件沉淀我们平时测试的规则,以达到快准全地测试系统!但是有一个问题:像SSRF或者一些直接无法回显的漏洞,我们该如何能第一时间知道呢?此篇文章由此而来!
0x01 申请所需要的各种key
0x011企业微信机器人的key
在一个正常的企业群里面,点击申请,步骤如下所示
第一步
第二步
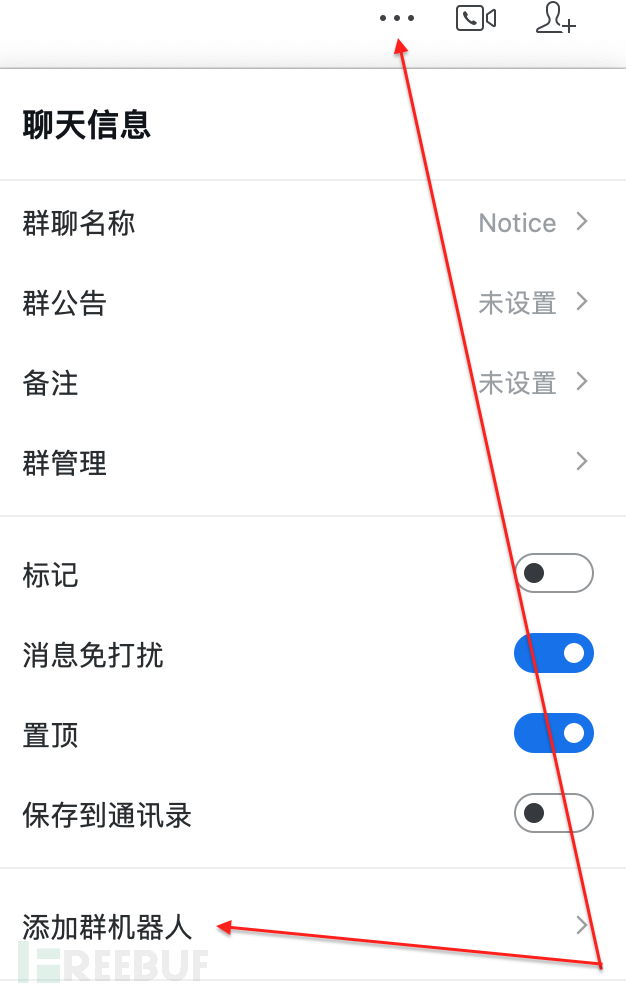
第三步
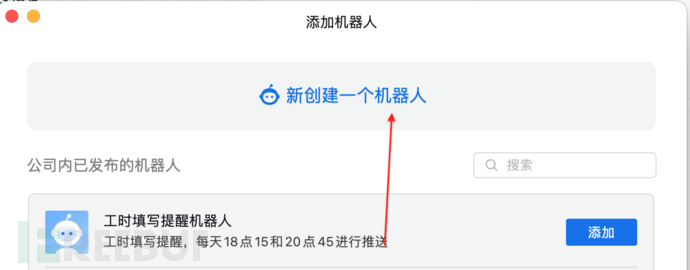
第四步
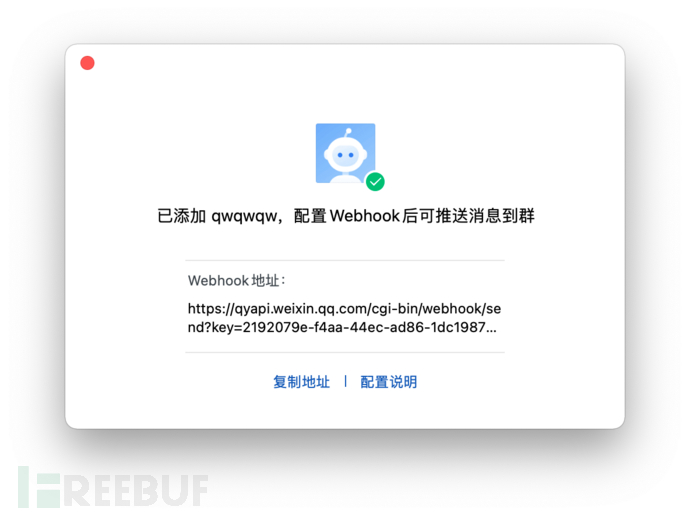
robotAPI=https://qyapi.weixin.qq.com/cgi-bin/webhook/send?key=2192079e-f4aa-44ec-ad86-1dc198727100
0x012 ceye.io key获取
登录http://ceye.io/profile,获取ceye_token,也就是API Token,然后拼接
ceyeDNS = "http://api.ceye.io/v1/records?token=ceye_token&type=dns"
ceyeHTTP = "http://api.ceye.io/v1/records?token=ceye_token&type=http"
0x02 监控脚本
项目地址:https://github.com/ba1ma0/WeWork_DNSLOG_Robot
在脚本中填写各种需要的配置信息
import json
import datetime
import time
import requests
import json
from datetime import timedelta
###该工具的主要作用是每隔5s请求一次ceye.io,如果有新的dnslog记录则推送到企业微信
#####################################################人工配置#####################################################
robotAPI = "https://qyapi.weixin.qq.com/cgi-bin/webhook/send?key=wechat_robot_token" #wechat_robot_token是在企业微信群中申请的机器人链接
ceyeDNS = "http://api.ceye.io/v1/records?token=ceye_token&type=dns" #ceye_token是在ceye.io申请的token
ceyeHTTP = "http://api.ceye.io/v1/records?token=ceye_token&type=http" #ceye_token是在ceye.io申请的token
staffNoList = ['01221455'] #机器人发送消息时需要被at的人!需要at全部人的时候直接@all即可
sleepTime = 5 #程序每隔5s请求一次ceye.io获取dnslog记录!
#####################################################人工配置#####################################################
IPAPI = "http://ip-api.com/json/testflagIP"
baiduAPI = "https://sp0.baidu.com/8aQDcjqpAAV3otqbppnN2DJv/api.php?query=testflagIP&co=&resource_id=6006&oe=utf8"
ceye_dns_previous = ''
ceye_http_previous = ''
WeWorktPostheaders = {'Content-Type':'application/json'}
WeWorktPostContent = ""
WeWorktPostdataTemp = {
"msgtype": "text",
"text": {
"content": WeWorktPostContent,
"mentioned_list":staffNoList,
}
}
#WeWorktPostdata = json.dumps(WeWorktPostdata)
#获取IP的相关详细信息
def getIPLocation(ip):
try:
IpInfoResult = json.loads(requests.get(baiduAPI.replace("testflagIP",str(ip))).text)
info = IpInfoResult['data'][0]['location']
#print(info)
except Exception as e:
try:
IpInfoResult = json.loads(requests.get(IPAPI.replace("testflagIP",str(ip))).text)
info = IpInfoResult['isp'] + "物理地址 "+ IpInfoResult['country'] + " " + IpInfoResult['region'] + " " + IpInfoResult['city']
#print(info)
except Exception as e:
print(e)
info = "IP :"+str(ip)
pass
return info
#UTC时间转换为标准的北京时间字符串
def UTC2BJtime(UTCtimeStr):
BJTime = datetime.datetime.strptime(UTCtimeStr,'%Y-%m-%d %H:%M:%S') + timedelta(hours=8)
BJTimeStr = datetime.datetime.strftime(BJTime,'%Y-%m-%d %H:%M:%S')
return BJTimeStr
#比较dnslog的结果
def comparePrevious():
global ceye_dns_previous,ceye_http_previous
result = {'dnsChange':False,'dns':'','httpChange':False,'http':''}
try:
dnsResult = json.loads(requests.get(ceyeDNS).text)
if dnsResult['data'] != []:
if dnsResult['data'][0]['id'] not in ceye_dns_previous:
ceye_dns_previous = str(dnsResult['data'][0])
#print (ceye_dns_previous)
result['dnsChange'] = True
result['dns'] = dnsResult['data'][0]
except Exception as e:
print(e)
pass
try:
httpResult = json.loads(requests.get(ceyeHTTP).text)
if httpResult['data'] != []:
if httpResult['data'][0]['id'] not in ceye_http_previous:
ceye_http_previous = str(httpResult['data'][0])
result['httpChange'] = True
result['http'] = httpResult['data'][0]
except Exception as e:
print(e)
pass
#print(str(result))
return result
while True:
WeWorktPostdata = WeWorktPostdataTemp
WeWorktPostdata1 = WeWorktPostdataTemp
#print(WeWorktPostdata)
try:
result = comparePrevious()
if result['dnsChange'] == True:
ipInfo = getIPLocation(result['dns']['remote_addr'])
WeWorktPostContent = "*****************************DNS请求*****************************\n请求ID : "+result['dns']['id']+ "\n请求时间 : "+UTC2BJtime(result['dns']['created_at'])+"\n"+"请求IP : "+result['dns']['remote_addr']+"\nIP信息 : "+ipInfo+"\n请求DNS : "+result['dns']['name']+"\n*****************************DNS请求*****************************"
WeWorktPostdata['text']['content'] = str(WeWorktPostContent)
WeWorktPostdata = json.dumps(WeWorktPostdata)
#print(WeWorktPostdata)
res = requests.post(url=robotAPI, data=WeWorktPostdata, headers=WeWorktPostheaders)
#print(res)
if result['httpChange'] == True:
ipInfo = getIPLocation(result['http']['remote_addr'])
WeWorktPostContent = "*****************************HTTP请求*****************************\n请求ID : "+result['http']['id']+ "\n请求时间 : "+UTC2BJtime(result['http']['created_at'])+"\n"+"请求IP : "+result['http']['remote_addr']+"\nIP信息 : "+ipInfo+"\n请求http : "+result['http']['name']+"\n*****************************HTTP请求*****************************"
WeWorktPostdata1['text']['content'] = str(WeWorktPostContent)
WeWorktPostdata1 = json.dumps(WeWorktPostdata1)
res = requests.post(url=robotAPI, data=WeWorktPostdata1, headers=WeWorktPostheaders)
#print(res)
except Exception as e:
print(e)
pass
#print("Sleep 5s")
time.sleep(sleepTime)0x03 开始捡洞
首先后台运行脚本: nohup python3 DNSLOG.py
然后配合上一篇文章,我们就可以高效,准确地捡一些我们日常可能没有注意到的一些漏洞了
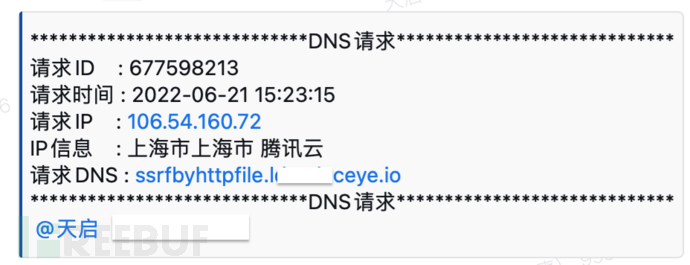
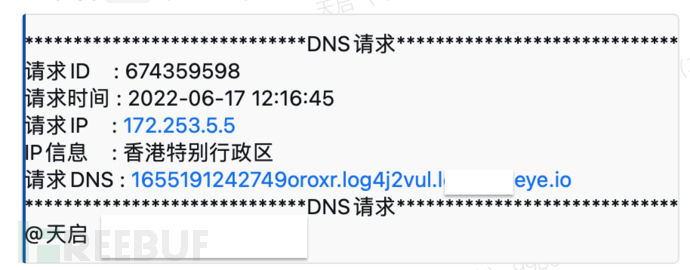
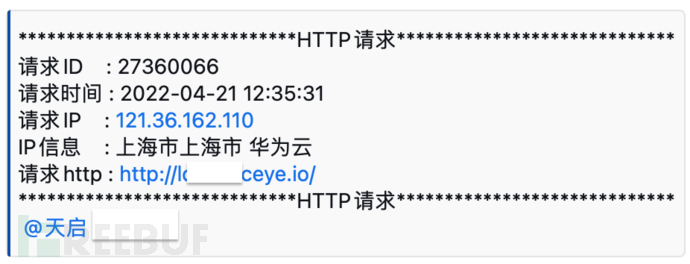
0x04 关于后期
后期工作中遇到了新的规则或者新的想法,我也会持续更新相关项目!以使其更好用!
相关项目地址:
https://github.com/ba1ma0/WeWork_DNSLOG_Robot
https://github.com/ba1ma0/SDLC_Vuln_Auto_Find
漏洞悬赏计划:涂鸦智能安全响应中心( https://src.tuya.com)欢迎白帽子来探索。
招聘内推计划:涵盖安全开发、安全测试、代码审计、安全合规等所有方面的岗位,简历投递sec#tuya.com,请注明来源。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)











