 FreddyLu666
FreddyLu666- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
在这篇文章中,我们将演示如何使用Sysmon日志来分析和了解恶意软件的各种行为,其中包括如何通过Firefox从Dropbox下载、运行、并使用Windows工具进行安装。本文将介绍Sysmon日志中各种有用的Event ID,以及如何识别和分析Windows操作系统上的恶意活动。

要解决的问题
在开始本文的内容之前,我们需要先在脑海里记住以下几个问题,并带着这些问题来阅读本文:
1、Sysmon日志中,Event ID 11相关的事件日志总共有多少?
2、每当在内存中创建进程时,都会记录Event ID为1的事件,其中包含命令行、哈希、进程路径、父进程路径等详细信息。这些信息对于安全分析人员来说非常有用,因为它可以让我们看到系统上执行的所有程序,这意味着我们可以发现任何正在执行的恶意进程,以及感染目标系统的恶意程序是什么?
3、威胁行为者使用了哪个云盘来分发恶意软件?
4、初始恶意文件在磁盘上创建了很多文件,并更改了时间戳,那么它对PDF文件修改的时间戳为多少?(这也是一种防御规避技术,更改文件创建日期可以让文件其看起来很旧)
5、恶意文件会在磁盘上存储一些文件,那么磁盘上的“once.cmd”创建在哪里?完整路径和文件名是什么?
6、恶意文件会试图访问伪域名,很可能是为了检查网络连接状态,那么恶意软件会试图连接到哪个伪域名?
7、恶意进程会试图访问哪个IP地址?
8、恶意进程在使用一个UltraVNC后门变种感染目标设备后会自行终止运行,那么这个进程是什么时候终止运行的?
希望大家阅读完本文之后,能够解决上述的这八个问题。
Sysmon
背景
Sysmon日志是由Microsoft系统监视器(Sysmon)生成的事件日志,它们提供有关Windows上的系统级操作的详细信息,并记录进程启动、网络连接、文件和注册表修改、驱动程序和服务活动以及WMI操作等活动,通过分析Sysmon日志,安全专家可以检测潜在风险、发现异常并响应安全事件,以增强整体系统监控和安全性。在不断变化的网络安全环境中,提前防范威胁非常重要。
Sysmon日志在这项工作中发挥着至关重要的作用,它提供了有价值的见解,并使组织能够加强其安全态势。Windows是企业环境中的主要操作系统,全面了解Windows事件日志、其独特特征和局限性以及通过Sysmon进行增强的潜力至关重要。
Event ID
Sysmon日志中所使用的全部Event ID都已经在微软的Sysmon页面上进行了介绍,其中包括:
1:进程创建
2:文件创建时间修改
3:网络连接
5:进程终止
11:文件创建
12:注册表对象创建和删除
13:注册表值设置
22:DNS查询
23:文件删除(带归档)
26:文件删除(不带归档)
工具
本文所进行的安全分析都将在一台Windows VM虚拟机中执行,并配置好Linux Bash Shell的Windows子系统。由于分析过程中会遇到大量的JSON数据,因此本文选择使用jq工具,该工具可以使用choco包管理器安装,安装命令如下:
choco install jq
数据
概览
下载的zip压缩文件中只有一个文件:
oxdf@hacky$ unzip -l unit42.zip Archive: unit42.zip Length Date Time Name --------- ---------- ----- ---- 1118208 2024-02-14 08:43 Microsoft-Windows-Sysmon-Operational.evtx --------- ------- 1118208 1 file
这些就是来源于目标系统的Sysmon日志,解压之后,我们会看到一个大小为1.1MB的Windows事件日志:
oxdf@hacky$ file Microsoft-Windows-Sysmon-Operational.evtx Microsoft-Windows-Sysmon-Operational.evtx: MS Windows Vista Event Log, 3 chunks (no. 2 in use), next record no. 170 oxdf@hacky$ ls -lh Microsoft-Windows-Sysmon-Operational.evtx -rwxrwx--- 1 root vboxsf 1.1M Feb 13 22:43 Microsoft-Windows-Sysmon-Operational.evtx
进程日志
笔者认为,用于将Windows事件日志格式转换为JSON的最佳处理工具就是Eric Zimmerman开发的EvtxeCmd.exe。接下来运行该工具,并将日志文件提供给EvtxeCmd.exe,并使用--json [file]参数运行:
PS > EvtxECmd.exe -f .\Microsoft-Windows-Sysmon-Operational.evtx --json . EvtxECmd version 1.5.0.0 Author: Eric Zimmerman (saericzimmerman@gmail.com) Command line: -f .\Microsoft-Windows-Sysmon-Operational.evtx --json . json output will be saved to .\20240408132435_EvtxECmd_Output.json Maps loaded: 438 Processing \Microsoft-Windows-Sysmon-Operational.evtx... Chunk count: 3, Iterating records... Record # 4 (Event Record Id: 118750): In map for event 26, Property /Event/EventData/Data[@Name="Archived"] not found! Replacing with empty string Record # 27 (Event Record Id: 118773): In map for event 10, Property /Event/EventData/Data[@Name="SourceProcessGuid"] not found! Replacing with empty string Record # 27 (Event Record Id: 118773): In map for event 10, Property /Event/EventData/Data[@Name="TargetProcessGuid"] not found! Replacing with empty string Record # 46 (Event Record Id: 118792): In map for event 26, Property /Event/EventData/Data[@Name="Archived"] not found! Replacing with empty string Event log details Flags: None Chunk count: 3 Stored/Calculated CRC: 9B75E006/9B75E006 Earliest timestamp: 2024-02-14 03:41:26.4441194 Latest timestamp: 2024-02-14 03:43:26.8870662 Total event log records found: 169 Records included: 169 Errors: 0 Events dropped: 0 Metrics (including dropped events) Event ID Count 1 6 2 16 3 1 5 1 7 15 10 1 11 56 12 14 13 19 15 2 17 7 22 3 23 26 26 2 Processed 1 file in 0.6669 seconds FLARE-VM 04/08/2024 09:24:35
在输出数据的底部,给出了识别到的日志类型,其中有56条日志与Event ID 11有关。
数据格式
生成的JSON数据是一系列日志记录,JSON中的每一行代表一条日志记录:
PS > cat .\20240408132435_EvtxECmd_Output.json | select -first 1
{"PayloadData1":"ProcessID: 4292, ProcessGUID: 817bddf3-3514-65cc-0802-000000001900","PayloadData2":"RuleName: -","PayloadData3":"Image: C:\\Program Files\\Mozilla Firefox\\firefox.exe","PayloadData4":"QueryName: uc2f030016253ec53f4953980a4e.dl.dropboxusercontent.com","PayloadData5":"QueryStatus: 0","PayloadData6":"QueryResults: type: 5 edge-block-www-env.dropbox-dns.com;::ffff:162.125.81.15;198.51.44.6;2620:4d:4000:6259:7:6:0:1;198.51.45.6;2a00:edc0:6259:7:6::2;198.51.44.70;2620:4d:4000:6259:7:6:0:3;198.51.45.70;2a00:edc0:6259:7:6::4;","UserName":"DESKTOP-887GK2L\\CyberJunkie","MapDescription":"DNSEvent (DNS query)","ChunkNumber":0,"Computer":"DESKTOP-887GK2L","Payload":"{\"EventData\":{\"Data\":[{\"@Name\":\"RuleName\",\"#text\":\"-\"},{\"@Name\":\"UtcTime\",\"#text\":\"2024-02-14 03:41:25.269\"},{\"@Name\":\"ProcessGuid\",\"#text\":\"817bddf3-3514-65cc-0802-000000001900\"},{\"@Name\":\"ProcessId\",\"#text\":\"4292\"},{\"@Name\":\"QueryName\",\"#text\":\"uc2f030016253ec53f4953980a4e.dl.dropboxusercontent.com\"},{\"@Name\":\"QueryStatus\",\"#text\":\"0\"},{\"@Name\":\"QueryResults\",\"#text\":\"type: 5 edge-block-www-env.dropbox-dns.com;::ffff:162.125.81.15;198.51.44.6;2620:4d:4000:6259:7:6:0:1;198.51.45.6;2a00:edc0:6259:7:6::2;198.51.44.70;2620:4d:4000:6259:7:6:0:3;198.51.45.70;2a00:edc0:6259:7:6::4;\"},{\"@Name\":\"Image\",\"#text\":\"C:\\\\Program Files\\\\Mozilla Firefox\\\\firefox.exe\"},{\"@Name\":\"User\",\"#text\":\"DESKTOP-887GK2L\\\\CyberJunkie\"}]}}","UserId":"S-1-5-18","Channel":"Microsoft-Windows-Sysmon/Operational","Provider":"Microsoft-Windows-Sysmon","EventId":22,"EventRecordId":"118747","ProcessId":3028,"ThreadId":4452,"Level":"Info","Keywords":"Classic","SourceFile":"Z:\\hackthebox-sherlocks\\unit42\\Microsoft-Windows-Sysmon-Operational.evtx","ExtraDataOffset":0,"HiddenRecord":false,"TimeCreated":"2024-02-14T03:41:26.4441194+00:00","RecordNumber":1}我们还可以使用jq对结果JSON数据进行处理,并获取到记录进程的Event ID统计信息:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -sc 'group_by(.EventId) | map({EventId: .[0].EventId, count: length}) |.[]'
{"EventId":1,"count":6}
{"EventId":2,"count":16}
{"EventId":3,"count":1}
{"EventId":5,"count":1}
{"EventId":7,"count":15}
{"EventId":10,"count":1}
{"EventId":11,"count":56}
{"EventId":12,"count":14}
{"EventId":13,"count":19}
{"EventId":15,"count":2}
{"EventId":17,"count":7}
{"EventId":22,"count":3}
{"EventId":23,"count":26}
{"EventId":26,"count":2}进程
了解数据
首先,我们要先查看进程事件,以了解目标设备上正在运行哪些程序,然后将这些事件信息保存到一个文件中(过滤出Event ID为1的事件并保存):
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -c 'select(.EventId == 1)' > eventid1.json
现在,我们就可以查看保存好的日志文件并了解日志中的字段信息了:
PS > cat .\eventid1.json | jq -s '.[0]'
{
"PayloadData1": "ProcessID: 5584, ProcessGUID: 817bddf3-3679-65cc-2902-000000001900",
"PayloadData2": "RuleName: technique_id=T1027,technique_name=Obfuscated Files or Information",
"PayloadData3": "SHA1=282F855BEB4FACF0726E13ECCADB7D3411B30B85,MD5=A1F5FF25E3D0F160BC7CE7CA57349D83,SHA256=B412C45DE423534D85F121ABC348FB38020FDA804EA0A972708B7447B0E7325D,IMPHASH=F84029681F81FED23E3E067364DA1699",
"PayloadData4": "ParentProcess: C:\\Program Files\\Mozilla Firefox\\firefox.exe",
"PayloadData5": "ParentProcessID: 4292, ParentProcessGUID: 817bddf3-3514-65cc-0802-000000001900",
"PayloadData6": "ParentCommandLine: \"C:\\Program Files\\Mozilla Firefox\\firefox.exe\"",
"UserName": "DESKTOP-887GK2L\\CyberJunkie",
"ExecutableInfo": "\"C:\\Program Files\\Mozilla Firefox\\pingsender.exe\" https://incoming.telemetry.mozilla.org/submit/telemetry/cb88145b-129d-471c-b605-4fdf09fec680/event/Firefox/122.0.1/release/20240205133611?v=4 C:\\Users\\CyberJunkie\\AppData\\Roaming\\Mozilla\\Firefox\\Profiles\\avsa4d81.default-release\\saved-telemetry-pings\\cb88145b-129d-471c-b605-4fdf09fec680 https://incoming.telemetry.mozilla.org/submit/telemetry/6fcd92a2-cc60-4df6-b6fb-66356dd011c1/main/Firefox/122.0.1/release/20240205133611?v=4 C:\\Users\\CyberJunkie\\AppData\\Roaming\\Mozilla\\Firefox\\Profiles\\avsa4d81.default-release\\saved-telemetry-pings\\6fcd92a2-cc60-4df6-b6fb-66356dd011c1",
"MapDescription": "Process creation",
"ChunkNumber": 0,
"Computer": "DESKTOP-887GK2L",
"Payload": "{\"EventData\":{\"Data\":[{\"@Name\":\"RuleName\",\"#text\":\"technique_id=T1027,technique_name=Obfuscated Files or Information\"},{\"@Name\":\"UtcTime\",\"#text\":\"2024-02-14 03:41:45.304\"},{\"@Name\":\"ProcessGuid\",\"#text\":\"817bddf3-3679-65cc-2902-000000001900\"},{\"@Name\":\"ProcessId\",\"#text\":\"5584\"},{\"@Name\":\"Image\",\"#text\":\"C:\\\\Program Files\\\\Mozilla Firefox\\\\pingsender.exe\"},{\"@Name\":\"FileVersion\",\"#text\":\"122.0.1\"},{\"@Name\":\"Description\",\"#text\":\"-\"},{\"@Name\":\"Product\",\"#text\":\"Firefox\"},{\"@Name\":\"Company\",\"#text\":\"Mozilla Foundation\"},{\"@Name\":\"OriginalFileName\",\"#text\":\"pingsender.exe\"},{\"@Name\":\"CommandLine\",\"#text\":\"\\\"C:\\\\Program Files\\\\Mozilla Firefox\\\\pingsender.exe\\\" https://incoming.telemetry.mozilla.org/submit/telemetry/cb88145b-129d-471c-b605-4fdf09fec680/event/Firefox/122.0.1/release/20240205133611?v=4 C:\\\\Users\\\\CyberJunkie\\\\AppData\\\\Roaming\\\\Mozilla\\\\Firefox\\\\Profiles\\\\avsa4d81.default-release\\\\saved-telemetry-pings\\\\cb88145b-129d-471c-b605-4fdf09fec680 https://incoming.telemetry.mozilla.org/submit/telemetry/6fcd92a2-cc60-4df6-b6fb-66356dd011c1/main/Firefox/122.0.1/release/20240205133611?v=4 C:\\\\Users\\\\CyberJunkie\\\\AppData\\\\Roaming\\\\Mozilla\\\\Firefox\\\\Profiles\\\\avsa4d81.default-release\\\\saved-telemetry-pings\\\\6fcd92a2-cc60-4df6-b6fb-66356dd011c1\"},{\"@Name\":\"CurrentDirectory\",\"#text\":\"C:\\\\Program Files\\\\Mozilla Firefox\\\\\"},{\"@Name\":\"User\",\"#text\":\"DESKTOP-887GK2L\\\\CyberJunkie\"},{\"@Name\":\"LogonGuid\",\"#text\":\"817bddf3-311e-65cc-a7ae-1b0000000000\"},{\"@Name\":\"LogonId\",\"#text\":\"0x1BAEA7\"},{\"@Name\":\"TerminalSessionId\",\"#text\":\"1\"},{\"@Name\":\"IntegrityLevel\",\"#text\":\"Medium\"},{\"@Name\":\"Hashes\",\"#text\":\"SHA1=282F855BEB4FACF0726E13ECCADB7D3411B30B85,MD5=A1F5FF25E3D0F160BC7CE7CA57349D83,SHA256=B412C45DE423534D85F121ABC348FB38020FDA804EA0A972708B7447B0E7325D,IMPHASH=F84029681F81FED23E3E067364DA1699\"},{\"@Name\":\"ParentProcessGuid\",\"#text\":\"817bddf3-3514-65cc-0802-000000001900\"},{\"@Name\":\"ParentProcessId\",\"#text\":\"4292\"},{\"@Name\":\"ParentImage\",\"#text\":\"C:\\\\Program Files\\\\Mozilla Firefox\\\\firefox.exe\"},{\"@Name\":\"ParentCommandLine\",\"#text\":\"\\\"C:\\\\Program Files\\\\Mozilla Firefox\\\\firefox.exe\\\"\"},{\"@Name\":\"ParentUser\",\"#text\":\"DESKTOP-887GK2L\\\\CyberJunkie\"}]}}",
"UserId": "S-1-5-18",
"Channel": "Microsoft-Windows-Sysmon/Operational",
"Provider": "Microsoft-Windows-Sysmon",
"EventId": 1,
"EventRecordId": "118772",
"ProcessId": 3028,
"ThreadId": 4412,
"Level": "Info",
"Keywords": "Classic",
"SourceFile": "Z:\\hackthebox-sherlocks\\unit42\\Microsoft-Windows-Sysmon-Operational.evtx",
"ExtraDataOffset": 0,
"HiddenRecord": false,
"TimeCreated": "2024-02-14T03:41:45.3058822+00:00",
"RecordNumber": 26
}概览
我们先分析父进程PayloadData4、进程ExecutableInfo、ID为PayloadData1和PayloadData5的进程和时间戳:
PS > cat .\eventid1.json | jq -s '.[] | [.TimeCreated, .PayloadData4, .ExecutableInfo, .PayloadData1, .PayloadData5]' [ "2024-02-14T03:41:45.3058822+00:00", "ParentProcess: C:\\Program Files\\Mozilla Firefox\\firefox.exe", "\"C:\\Program Files\\Mozilla Firefox\\pingsender.exe\" https://incoming.telemetry.mozilla.org/submit/telemetry/cb88145b-129d-471c-b605-4fdf09fec680/event/Firefox/122.0.1/release/20240205133611?v=4 C:\\Users\\CyberJunkie\\AppData\\Roaming\\Mozilla\\Firefox\\Profiles\\avsa4d81.default-release\\saved-telemetry-pings\\cb88145b-129d-471c-b605-4fdf09fec680 https://incoming.telemetry.mozilla.org/submit/telemetry/6fcd92a2-cc60-4df6-b6fb-66356dd011c1/main/Firefox/122.0.1/release/20240205133611?v=4 C:\\Users\\CyberJunkie\\AppData\\Roaming\\Mozilla\\Firefox\\Profiles\\avsa4d81.default-release\\saved-telemetry-pings\\6fcd92a2-cc60-4df6-b6fb-66356dd011c1", "ProcessID: 5584, ProcessGUID: 817bddf3-3679-65cc-2902-000000001900", "ParentProcessID: 4292, ParentProcessGUID: 817bddf3-3514-65cc-0802-000000001900" ] [ "2024-02-14T03:41:56.5596188+00:00", "ParentProcess: C:\\Windows\\explorer.exe", "\"C:\\Users\\CyberJunkie\\Downloads\\Preventivo24.02.14.exe.exe\" ", "ProcessID: 10672, ProcessGUID: 817bddf3-3684-65cc-2d02-000000001900", "ParentProcessID: 1116, ParentProcessGUID: 817bddf3-311f-65cc-0a01-000000001900" ] [ "2024-02-14T03:41:57.6052379+00:00", "ParentProcess: C:\\Windows\\System32\\services.exe", "C:\\Windows\\system32\\msiexec.exe /V", "ProcessID: 10220, ProcessGUID: 817bddf3-3685-65cc-2e02-000000001900", "ParentProcessID: 740, ParentProcessGUID: 817bddf3-307b-65cc-0b00-000000001900" ] [ "2024-02-14T03:41:57.7881524+00:00", "ParentProcess: C:\\Windows\\System32\\msiexec.exe", "C:\\Windows\\syswow64\\MsiExec.exe -Embedding 5364C761FA9A55D636271A1CE8A6742D C", "ProcessID: 6996, ProcessGUID: 817bddf3-3685-65cc-2f02-000000001900", "ParentProcessID: 10220, ParentProcessGUID: 817bddf3-3685-65cc-2e02-000000001900" ] [ "2024-02-14T03:41:57.9059712+00:00", "ParentProcess: C:\\Users\\CyberJunkie\\Downloads\\Preventivo24.02.14.exe.exe", "\"C:\\Windows\\system32\\msiexec.exe\" /i \"C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\main1.msi\" AI_SETUPEXEPATH=C:\\Users\\CyberJunkie\\Downloads\\Preventivo24.02.14.exe.exe SETUPEXEDIR=C:\\Users\\CyberJunkie\\Downloads\\ EXE_CMD_LINE=\"/exenoupdates /forcecleanup /wintime 1707880560 \" AI_EUIMSI=\"\"", "ProcessID: 10324, ProcessGUID: 817bddf3-3685-65cc-3002-000000001900", "ParentProcessID: 10672, ParentProcessGUID: 817bddf3-3684-65cc-2d02-000000001900" ] [ "2024-02-14T03:41:58.1794583+00:00", "ParentProcess: C:\\Windows\\System32\\msiexec.exe", "C:\\Windows\\syswow64\\MsiExec.exe -Embedding 5250A3DB12224F77D2A18B4EB99AC5EB", "ProcessID: 10280, ProcessGUID: 817bddf3-3686-65cc-3102-000000001900", "ParentProcessID: 10220, ParentProcessGUID: 817bddf3-3685-65cc-2e02-000000001900" ]
从中我们可以了解到下列内容
1、貌似这个事件并没有跟恶意软件有关,pingsender.exe是Firefox的一个功能,它的存在表示目标设备运行了Firefox;
2、Downloads文件夹下有一个可执行程序正在运行,其父进程为explorer.exe,这表明目标用户通过双击运行了该程序;
3、services.exe启动了msiexec.exe,目前还无法判断这个事件是否跟之前的事件有关,但这本质上还是一种安装行为,在时间上与之前的事件很接近;
4、msiexec.exe调用了自身的32位版本,调用行为是由之前的事件创建的;
5、第二个日志中下载的代码调用了msiexec进行安装;
6、第三个日志中的msiexec再一次调用了自己的32位版本;
很明显,2和5是相关的,然后3、4、6是相关的。
Preventivo24.02.14.exe.exe
在搜索引擎中搜索“Preventivo24.02.14.exe.exe”、“Preventivo24.02.14”和“Preventivo.exe”之后,我了解到了一些看似可疑的东西:
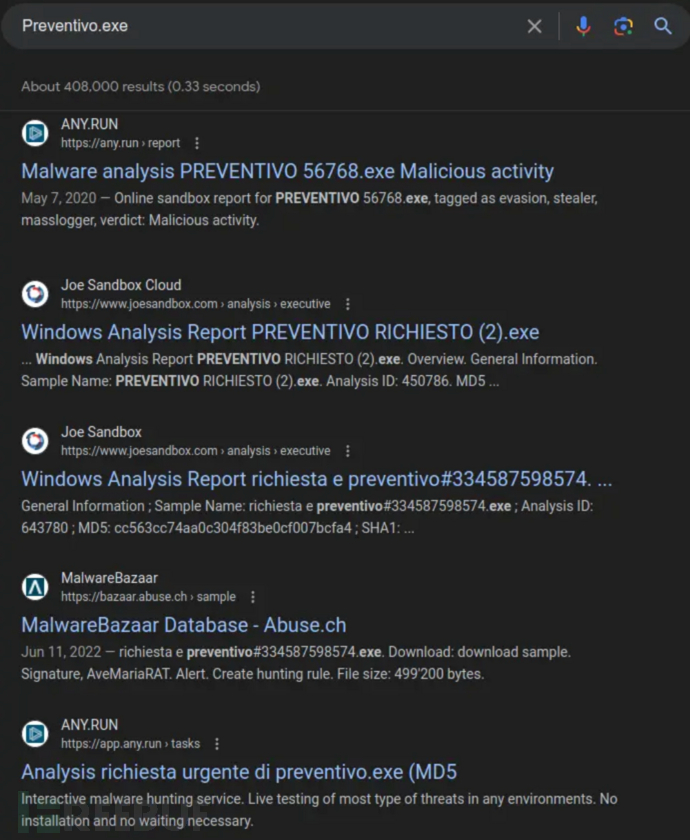
日志中还提供了源代码的哈希:
PS > cat .\eventid1.json | jq -s '.[1]'
{
"PayloadData1": "ProcessID: 10672, ProcessGUID: 817bddf3-3684-65cc-2d02-000000001900",
"PayloadData2": "RuleName: technique_id=T1204,technique_name=User Execution",
"PayloadData3": "SHA1=18A24AA0AC052D31FC5B56F5C0187041174FFC61,MD5=32F35B78A3DC5949CE3C99F2981DEF6B,SHA256=0CB44C4F8273750FA40497FCA81E850F73927E70B13C8F80CDCFEE9D1478E6F3,IMPHASH=36ACA8EDDDB161C588FCF5AFDC1AD9FA",
"PayloadData4": "ParentProcess: C:\\Windows\\explorer.exe",
"PayloadData5": "ParentProcessID: 1116, ParentProcessGUID: 817bddf3-311f-65cc-0a01-000000001900",
"PayloadData6": "ParentCommandLine: C:\\Windows\\Explorer.EXE",
"UserName": "DESKTOP-887GK2L\\CyberJunkie",
"ExecutableInfo": "\"C:\\Users\\CyberJunkie\\Downloads\\Preventivo24.02.14.exe.exe\" ",
"MapDescription": "Process creation",
"ChunkNumber": 0,
"Computer": "DESKTOP-887GK2L",
"Payload": "{\"EventData\":{\"Data\":[{\"@Name\":\"RuleName\",\"#text\":\"technique_id=T1204,technique_name=User Execution\"},{\"@Name\":\"UtcTime\",\"#text\":\"2024-02-14 03:41:56.538\"},{\"@Name\":\"ProcessGuid\",\"#text\":\"817bddf3-3684-65cc-2d02-000000001900\"},{\"@Name\":\"ProcessId\",\"#text\":\"10672\"},{\"@Name\":\"Image\",\"#text\":\"C:\\\\Users\\\\CyberJunkie\\\\Downloads\\\\Preventivo24.02.14.exe.exe\"},{\"@Name\":\"FileVersion\",\"#text\":\"1.1.2\"},{\"@Name\":\"Description\",\"#text\":\"Photo and vn Installer\"},{\"@Name\":\"Product\",\"#text\":\"Photo and vn\"},{\"@Name\":\"Company\",\"#text\":\"Photo and Fax Vn\"},{\"@Name\":\"OriginalFileName\",\"#text\":\"Fattura 2 2024.exe\"},{\"@Name\":\"CommandLine\",\"#text\":\"\\\"C:\\\\Users\\\\CyberJunkie\\\\Downloads\\\\Preventivo24.02.14.exe.exe\\\" \"},{\"@Name\":\"CurrentDirectory\",\"#text\":\"C:\\\\Users\\\\CyberJunkie\\\\Downloads\\\\\"},{\"@Name\":\"User\",\"#text\":\"DESKTOP-887GK2L\\\\CyberJunkie\"},{\"@Name\":\"LogonGuid\",\"#text\":\"817bddf3-311e-65cc-a7ae-1b0000000000\"},{\"@Name\":\"LogonId\",\"#text\":\"0x1BAEA7\"},{\"@Name\":\"TerminalSessionId\",\"#text\":\"1\"},{\"@Name\":\"IntegrityLevel\",\"#text\":\"Medium\"},{\"@Name\":\"Hashes\",\"#text\":\"SHA1=18A24AA0AC052D31FC5B56F5C0187041174FFC61,MD5=32F35B78A3DC5949CE3C99F2981DEF6B,SHA256=0CB44C4F8273750FA40497FCA81E850F73927E70B13C8F80CDCFEE9D1478E6F3,IMPHASH=36ACA8EDDDB161C588FCF5AFDC1AD9FA\"},{\"@Name\":\"ParentProcessGuid\",\"#text\":\"817bddf3-311f-65cc-0a01-000000001900\"},{\"@Name\":\"ParentProcessId\",\"#text\":\"1116\"},{\"@Name\":\"ParentImage\",\"#text\":\"C:\\\\Windows\\\\explorer.exe\"},{\"@Name\":\"ParentCommandLine\",\"#text\":\"C:\\\\Windows\\\\Explorer.EXE\"},{\"@Name\":\"ParentUser\",\"#text\":\"DESKTOP-887GK2L\\\\CyberJunkie\"}]}}",
"UserId": "S-1-5-18",
"Channel": "Microsoft-Windows-Sysmon/Operational",
"Provider": "Microsoft-Windows-Sysmon",
"EventId": 1,
"EventRecordId": "118793",
"ProcessId": 3028,
"ThreadId": 4412,
"Level": "Info",
"Keywords": "Classic",
"SourceFile": "Z:\\hackthebox-sherlocks\\unit42\\Microsoft-Windows-Sysmon-Operational.evtx",
"ExtraDataOffset": 0,
"HiddenRecord": false,
"TimeCreated": "2024-02-14T03:41:56.5596188+00:00",
"RecordNumber": 47
}搜索这些哈希之后,我们发现目标代码已经被上传到了很多恶意软件沙箱,例如Malware Bazaar、AnyRun、JoeSandbox和VirusTotal,这些平台都已经将其标记为了恶意代码:
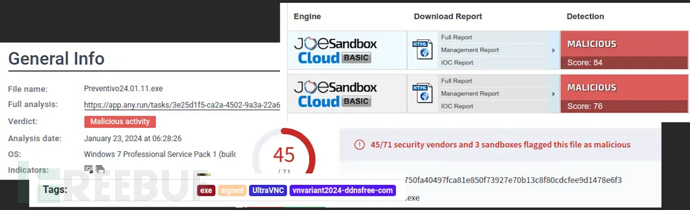
从事件日志中还可以看到,恶意代码的完整路径为“C:\Users\CyberJunkie\Downloads\Preventivo24.02.14.exe.exe”,进程的PID为10672。
恶意软件源
文件创建
如果在恶意软件被下载的时候,Sysmon已经在运行了,那么它就会生成事件ID为11的事件。我们可以使用“jq -c”来选择这些事件,并按行输出。此时,还可以使用findstr(类似于Linux中的grep)来获取包含4292的日志条目,而4292则是之前进程分析中Firefox的进程ID。然后,读取结果数据并打印文件时间戳:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -c 'select(.EventId == 11)' | findstr 4292 | jq -s '.[] | [.TimeCreated, .PayloadData4]' [ "2024-02-14T03:41:26.4630328+00:00", "TargetFilename: C:\\Users\\CYBERJ~1\\AppData\\Local\\Temp\\skZdsnwf.exe" ] [ "2024-02-14T03:41:26.4635006+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\Downloads\\skZdsnwf.exe.part" ] [ "2024-02-14T03:41:26.4639993+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\Downloads\\skZdsnwf.exe.part" ] [ "2024-02-14T03:41:26.4644853+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\Downloads\\Preventivo24.02.14.exe.exe" ] [ "2024-02-14T03:41:30.4745302+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\Downloads\\Preventivo24.02.14.exe.exe:Zone.Identifier" ] [ "2024-02-14T03:41:45.2125243+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Mozilla\\Firefox\\Profiles\\avsa4d81.default-release\\prefs-1.js" ] [ "2024-02-14T03:41:45.2136161+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Mozilla\\Firefox\\Profiles\\avsa4d81.default-release\\prefs-1.js" ]
我们可以看到,03:41:26时它开始下载一个temp临时文件,之后便被重命名为了Preventivo24.02.14.exe.exe(同一秒)。4秒钟之后,另一个数据流将该文件标记为了“从互联网下载”,我们也可以说它是从Firefox下载的。此时,其他进程看起来就不是很重要了。
DNS
那么,Firefox到底是从哪里下载它的?于是我们打算从DNS记录入手,即Event ID 22,要使用的命令结构和之前类似:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -c 'select(.EventId == 22)' | findstr 4292 | jq -s '.[] | [.TimeCreated, .PayloadData4, .PayloadData3]' [ "2024-02-14T03:41:26.4441194+00:00", "QueryName: uc2f030016253ec53f4953980a4e.dl.dropboxusercontent.com", "Image: C:\\Program Files\\Mozilla Firefox\\firefox.exe" ] [ "2024-02-14T03:41:45.7793186+00:00", "QueryName: d.dropbox.com", "Image: C:\\Program Files\\Mozilla Firefox\\firefox.exe" ]
在下载开始之后不到0.1秒便执行了第一次查询,可以判断恶意软件来自于Dropbox。
第二次查询发生在19秒之后,也就是恶意软件启动前的11秒,目前还搞不清楚此时发生了什么,但我们也先标记好。
恶意软件活动
文件创建
现在,我们从恶意进程(PID 10672)入手,通过日志分析,我们可以看到恶意软件在目标设备上创建了六个文件:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -c 'select(.EventId == 11)' | findstr 10672 | jq -s '.[] | [.TimeCreated, .PayloadData4]' [ "2024-02-14T03:41:58.4048771+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\c.cmd" ] [ "2024-02-14T03:41:58.4056902+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\cmmc.cmd" ] [ "2024-02-14T03:41:58.4065154+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\on.cmd" ] [ "2024-02-14T03:41:58.4075055+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\once.cmd" ] [ "2024-02-14T03:41:58.4104279+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\taskhost.exe" ] [ "2024-02-14T03:41:58.4225212+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\viewer.exe" ]
这些文件全部都在同一时间创建,可以看到once.cmd文件的完整路径为“C:\Users\CyberJunkie\AppData\Roaming\Photo and Fax Vn\Photo and vn 1.1.2\install\F97891C\WindowsVolume\Games\once.cmd ”。
DNS
这个进程发送的DNS请求如下:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -c 'select(.EventId == 22)' | findstr 10672 | jq -s '.[] | [.TimeCreated, .PayloadData4, .PayloadData3]' [ "2024-02-14T03:41:58.7648370+00:00", "QueryName: www.example.com", "Image: C:\\Users\\CyberJunkie\\Downloads\\Preventivo24.02.14.exe.exe" ]
请求的域名为www.example.com,这个域名很明显不是由威胁行为者控制的,而且也不是一个活动域名,也有可能是为了误导分析人员而设置的。
网络
日志中只有一个网络事件(Event ID 3),来自于进程PID 10672:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -c 'select(.EventId == 3)' | findstr 10672 | jq .
{
"PayloadData1": "ProcessID: 10672, ProcessGUID: 817bddf3-3684-65cc-2d02-000000001900",
"PayloadData2": "RuleName: technique_id=T1036,technique_name=Masquerading",
"PayloadData3": "SourceHostname: -",
"PayloadData4": "SourceIp: 172.17.79.132",
"PayloadData5": "DestinationHostname: -",
"PayloadData6": "DestinationIp: 93.184.216.34",
"UserName": "DESKTOP-887GK2L\\CyberJunkie",
"MapDescription": "Network connection",
"ChunkNumber": 2,
"Computer": "DESKTOP-887GK2L",
"Payload": "{\"EventData\":{\"Data\":[{\"@Name\":\"RuleName\",\"#text\":\"technique_id=T1036,technique_name=Masquerading\"},{\"@Name\":\"UtcTime\",\"#text\":\"2024-02-14 03:41:57.159\"},{\"@Name\":\"ProcessGuid\",\"#text\":\"817bddf3-3684-65cc-2d02-000000001900\"},{\"@Name\":\"ProcessId\",\"#text\":\"10672\"},{\"@Name\":\"Image\",\"#text\":\"C:\\\\Users\\\\CyberJunkie\\\\Downloads\\\\Preventivo24.02.14.exe.exe\"},{\"@Name\":\"User\",\"#text\":\"DESKTOP-887GK2L\\\\CyberJunkie\"},{\"@Name\":\"Protocol\",\"#text\":\"tcp\"},{\"@Name\":\"Initiated\",\"#text\":\"True\"},{\"@Name\":\"SourceIsIpv6\",\"#text\":\"False\"},{\"@Name\":\"SourceIp\",\"#text\":\"172.17.79.132\"},{\"@Name\":\"SourceHostname\",\"#text\":\"-\"},{\"@Name\":\"SourcePort\",\"#text\":\"61177\"},{\"@Name\":\"SourcePortName\",\"#text\":\"-\"},{\"@Name\":\"DestinationIsIpv6\",\"#text\":\"False\"},{\"@Name\":\"DestinationIp\",\"#text\":\"93.184.216.34\"},{\"@Name\":\"DestinationHostname\",\"#text\":\"-\"},{\"@Name\":\"DestinationPort\",\"#text\":\"80\"},{\"@Name\":\"DestinationPortName\",\"#text\":\"-\"}]}}",
"UserId": "S-1-5-18",
"Channel": "Microsoft-Windows-Sysmon/Operational",
"Provider": "Microsoft-Windows-Sysmon",
"EventId": 3,
"EventRecordId": "118910",
"ProcessId": 3028,
"ThreadId": 4424,
"Level": "Info",
"Keywords": "Classic",
"SourceFile": "Z:\\hackthebox-sherlocks\\unit42\\Microsoft-Windows-Sysmon-Operational.evtx",
"ExtraDataOffset": 0,
"HiddenRecord": false,
"TimeCreated": "2024-02-14T03:41:58.9054838+00:00",
"RecordNumber": 164
}连接到的IP地址为93.184.216.34。
时间戳
恶意软件修改文件时间戳的行为记录为Event ID2,总共有16个相关的恶意软件进程事件:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -c 'select(.EventId == 2)' | findstr 10672 | jq -s '.[] | [.TimeCreated, .PayloadData4, .PayloadData5, .PayloadData6]' [ "2024-02-14T03:41:57.5590448+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\main1.msi", "CreationTimeUTC: 2024-01-14 08:14:23.713", "PreviousCreationTimeUTC: 2024-02-14 03:41:57.545" ] [ "2024-02-14T03:41:58.4045440+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\powercfg.msi", "CreationTimeUTC: 2024-01-10 18:12:27.357", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.389" ] [ "2024-02-14T03:41:58.4053804+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\c.cmd", "CreationTimeUTC: 2024-01-10 18:12:26.295", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.389" ] [ "2024-02-14T03:41:58.4061207+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\cmmc.cmd", "CreationTimeUTC: 2024-01-10 18:12:26.373", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.404" ] [ "2024-02-14T03:41:58.4069465+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\on.cmd", "CreationTimeUTC: 2024-01-10 18:12:26.436", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.404" ] [ "2024-02-14T03:41:58.4078369+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\once.cmd", "CreationTimeUTC: 2024-01-10 18:12:26.458", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.404" ] [ "2024-02-14T03:41:58.4086077+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\cmd.txt", "CreationTimeUTC: 2024-01-10 18:12:26.326", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.404" ] [ "2024-02-14T03:41:58.4093822+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\UltraVNC.ini", "CreationTimeUTC: 2024-01-10 18:12:26.530", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.404" ] [ "2024-02-14T03:41:58.4101450+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\TempFolder\\~.pdf", "CreationTimeUTC: 2024-01-14 08:10:06.029", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.404" ] [ "2024-02-14T03:41:58.4128728+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\taskhost.exe", "CreationTimeUTC: 2024-01-10 18:12:26.513", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.404" ] [ "2024-02-14T03:41:58.4231673+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\viewer.exe", "CreationTimeUTC: 2024-01-10 18:12:26.670", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.420" ] [ "2024-02-14T03:41:58.4258718+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\ddengine.dll", "CreationTimeUTC: 2024-01-10 18:12:26.406", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.420" ] [ "2024-02-14T03:41:58.4277653+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\UVncVirtualDisplay\\UVncVirtualDisplay.dll", "CreationTimeUTC: 2024-01-10 18:12:26.905", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.420" ] [ "2024-02-14T03:41:58.4288308+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\vnchooks.dll", "CreationTimeUTC: 2024-01-10 18:12:26.686", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.420" ] [ "2024-02-14T03:41:58.4299750+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\UVncVirtualDisplay\\uvncvirtualdisplay.cat", "CreationTimeUTC: 2024-01-10 18:12:26.889", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.420" ] [ "2024-02-14T03:41:58.4308868+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\WindowsVolume\\Games\\UVncVirtualDisplay\\UVncVirtualDisplay.inf", "CreationTimeUTC: 2024-01-10 18:12:27.013", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.420" ]
有很多文件跟这个事件有关,但其中只有一个是PDF文件:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq -c 'select(.EventId == 2)' | findstr 10672 | findstr pdf | jq -s '.[] | [.TimeCreated, .PayloadData4, .PayloadData5, .PayloadData6]' [ "2024-02-14T03:41:58.4101450+00:00", "TargetFilename: C:\\Users\\CyberJunkie\\AppData\\Roaming\\Photo and Fax Vn\\Photo and vn 1.1.2\\install\\F97891C\\TempFolder\\~.pdf", "CreationTimeUTC: 2024-01-14 08:10:06.029", "PreviousCreationTimeUTC: 2024-02-14 03:41:58.404" ]
其中,PDF文件的时间戳被修改为了“2024-01-14 08:10:06”。
终止执行
日志记录中只有一条进程终止事件(Event ID 5),该事件属于恶意软件:
PS > cat .\20240408132435_EvtxECmd_Output.json | jq 'select(.EventId == 5)'
{
"PayloadData1": "ProcessID: 10672, ProcessGUID: 817bddf3-3684-65cc-2d02-000000001900",
"UserName": "DESKTOP-887GK2L\\CyberJunkie",
"ExecutableInfo": "C:\\Users\\CyberJunkie\\Downloads\\Preventivo24.02.14.exe.exe",
"MapDescription": "Process terminated",
"ChunkNumber": 2,
"Computer": "DESKTOP-887GK2L",
"Payload": "{\"EventData\":{\"Data\":[{\"@Name\":\"RuleName\",\"#text\":\"-\"},{\"@Name\":\"UtcTime\",\"#text\":\"2024-02-14 03:41:58.795\"},{\"@Name\":\"ProcessGuid\",\"#text\":\"817bddf3-3684-65cc-2d02-000000001900\"},{\"@Name\":\"ProcessId\",\"#text\":\"10672\"},{\"@Name\":\"Image\",\"#text\":\"C:\\\\Users\\\\CyberJunkie\\\\Downloads\\\\Preventivo24.02.14.exe.exe\"},{\"@Name\":\"User\",\"#text\":\"DESKTOP-887GK2L\\\\CyberJunkie\"}]}}",
"UserId": "S-1-5-18",
"Channel": "Microsoft-Windows-Sysmon/Operational",
"Provider": "Microsoft-Windows-Sysmon",
"EventId": 5,
"EventRecordId": "118907",
"ProcessId": 3028,
"ThreadId": 4412,
"Level": "Info",
"Keywords": "Classic",
"SourceFile": "Z:\\hackthebox-sherlocks\\unit42\\Microsoft-Windows-Sysmon-Operational.evtx",
"ExtraDataOffset": 0,
"HiddenRecord": false,
"TimeCreated": "2024-02-14T03:41:58.7996518+00:00",
"RecordNumber": 161
}该事件发生于“2024-02-14 03:41:58”。
分析结果
时间线
时间(UTC) | 描述 | 参考 |
2024-02-14T03:41:26.4 | Firefox向Dropbox发送DNS查询 | DNS (22) |
2024-02-14T03:41:26.5 | Firefox恶意软件下载 | 文件创建(11) |
2024-02-14T03:41:30.4 | Windows将恶意软件标记为“下载” | 文件创建 (11) |
2024-02-14T03:41:45.8 | Firefox向Dropbox发送DNS查询 | DNS (22) |
2024-02-14T03:41:56.6 | Preventivo24.02.14.exe.exe启动 | 进程创建 (1) |
2024-02-14T03:41:57.9 | 恶意软件执行msiexec | 进程创建 (1) |
2024-02-14T03:41:58.4 | 恶意软件向磁盘写入文件 | 文件创建 (11) |
2024-02-14T03:41:58.4 | 恶意软件修改了15个文件的时间戳 | 时间戳修改 (2) |
2024-02-14T03:41:58.6 | 恶意软件连接到93.184.216.34 | Network (3) |
2024-02-14T03:41:58.8 | 恶意软件向www.example.com发送DNS请求 | DNS (22) |
2024-02-14 03:41:58.8 | 恶意软件终止自身运行 | 进程终止 (5) |
问题的答案
1、56
2、C:\Users\CyberJunkie\Downloads\Preventivo24.02.14.exe.exe
3、Dropbox
4、2024-01-14 08:10:06
5、C:\Users\CyberJunkie\AppData\Roaming\Photo and Fax Vn\Photo and vn 1.1.2\install\F97891C\WindowsVolume\Games\once.cmd
6、www.example.com
7、93.184.216.34
8、2024-02-14 03:41:58
参考资料
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
https://github.com/SwiftOnSecurity/sysmon-config
https://twitter.com/SwiftOnSecurity
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
https://0xdf.gitlab.io/2018/12/19/jq.html
https://github.com/EricZimmerman/evtx
参考链接
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)











