 CDxiaodong
CDxiaodong- 关注
使用porttunnel
准备两台可以互通的电脑
B:49.235.226.125
C:123.60.85.184
以及本地ipA
A可以通B和C
B可以通C不能通A
C可以通B不能通A
其实再在实际应用中是A只能通B,B只能通C’
然后C不出网,然后B将C转发给A使得
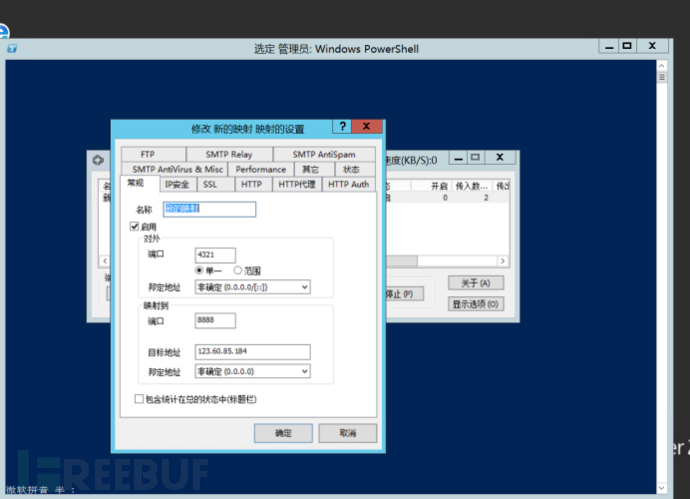
设置成这样4321是B主机对外端口 对外主机白名单不限制
80是C的apache服务器端口
网站打开Bip:4321
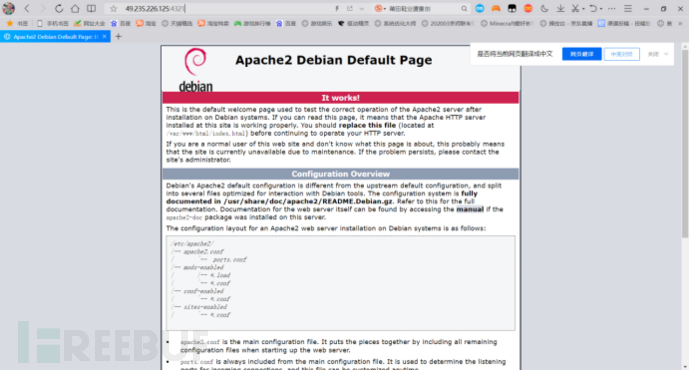
成功转发
下面是一些:porttunnel手册
[ 主要的一些选项 ]
对外绑定地址/端口: PortTunnel监听的地址/端口。
映射目标地址/端口: 将要映射到的服务器地址/端口。
包含统计在总的状态中(标题栏): 将本映射的连接信息、传入速度、传出速度加入总的连接 信息中,并显示在主窗口标题中。
[ IP 安全选项 ] 主窗口中的内容是允许或禁止的IP地址列表,如果这个列表很长,可以在下面输入IP地址, 点击查找即可寻找到包含输入IP地址的行。
处理无效IP的方法有三种: 禁止-取消此次访问 重定向-如果端口和地址不为空则重定向到指定的地址和端口 无回应-对客户端的请求不回应使之超时(不推荐这样做)
允许/禁止IP地址列表的设置方法: 可以使用外部文件来定义允许/禁止IP地址,只要增加以下内容:
i,c:\valid_ips.txt
然后建立文件 c:\valid_ips.txt,文件内容为允许/禁止的IP地址,例如:
y,127.0.0.1
y,12.34.56.78
n,*
等等...
PortTunnel每30秒会自动检测外部定义文件的改变(每30秒一次),然后自动调入新的内容。 你可以利用Perl或其它程序来改变外部定义文件的内容已达到自己的目的,你甚至可以在定义 文件中嵌套其它的定义文件,下面的例子说明了这种灵活性:
----- [start example] ----- ----- [in ftp port mapping IP security tab] ----- i,c:\ftp_valid_ips.txt ----- [end] ----- ----- [in irc port mapping IP security tab] ----- i,c:\irc_valid_ips.txt ----- [end] ----- ----- [in file c:\ftp_valid_ips.txt] ----- i,c:\global_ban_list.txt y,34.56.78.99 // a friend I let use ftp i,c:\global_ok_list.txt n,* ----- [end] ----- ----- [in file c:\irc_valid_ips.txt] ----- i,c:\global_ban_list.txt y,12.45.12.45 // a friend I let use irc i,c:\global_ok_list.txt n,* ----- [end] ----- ----- [in file c:\global_ok_list.txt] ----- y,66.66.66.66 // a friend I let use every thing ----- [end] ----- ----- [in file c:\global_ban_list.txt] ----- n,33.44.66.77 // a lamer I hate ---- [end] ----- ----- [end example] -----
IP安全选项中有详细的定义允许/禁止IP地址的方法。
[ HTTP 有关选项 ] 使用HTTP代理服务器: 通过HTTP代理服务器来映射。 举例来说,你在单位需要通过HTTP代理上网,若想访问IRC服务器,则需如下设置:
1. 建立一个端口映射: 127.0.0.1:6667 映射到你的单位的HTTP代理服务器,如: proxy.company.local:8080 2. 勾选“使用HTTP代理服务器”,并输入你想访问的IRC服务器地址,如: ircserver.ircnetwork.net:6667
3. 设置你的IRC客户端程序访问地址 127.0.0.1:6667
注: 如果你单位的代理服务器禁止了IRC端口,那就没有办法来访问外部的IRC服务器。
代理服务器口令: 若代理服务器需要身份验证,请在此输入
修改端口号: 如果PortTunnel监听端口和映射到的端口不一致则需要勾选此项,例如, 映射从 localhost:81 到 host1:82 客户端发送 GET http://test.server:81/folderHTTP/1.1 Host: test.server PortTunnel 将端口改为 GET http://test.server:82/folderHTTP/1.1 Host: test.server:88 然后 IIS 会返回 HTTP/1.0 302 Moved Temporarily Location: http://test.server:82/folder/PortTunnel 将返回内容中的端口改为 HTTP/1.0 302 Moved Temporarily Location: http://test.server:81/folder/这样做便不会导致HTTP的访问错误。
加入 X-Client-Address 到请求报文: 在HTTP请求中增加下列内容 X-Client-Address: aab.bbb.ccc.ddd 这有助于某些日志程序正确记录访问地址
[ FTP 有关选项 ] 传送'PORT' 与 'PASV' 命令:勾选此项有助于FXP文件传输,或通过代理服务器访问FTP的 客户端正确连接FTP服务器。
使用替换地址用于PASV回应: 若你的FTP服务器在网络防火墙之后或经过了地址转换,则需 在勾选并填写公用的外部IP地址。
只对不在同一个C类网络的客户端采取以上替换: 若在同一网络之内则无需替换。
使用下列端口范围用于PASV模式: 限制PASV使用的端口范围。
加入 IDNT: 如果FTP服务器支持IDNT则勾选。RaidenFTPD需要在 .ftpd 文件中增加:
BOUNCERIP = “PortTunnel 正在运行的机器的IP地址”
[ SMTP 有关选项 ] smtp 快速设置: 1. 打开 “SMTP 接收筛选” 2. 增加所有需支持的域名,例如
y,mydomain.tld
y,another.domain.that.I.host
- 增加信任的外部地址,例如 y,127.0.0.1 // localhost y,192.168.* // lan y,myfriend 4. 若需要 POP3 身份验证则 在 “通过筛选则” 中选择 “SMTP通过POP3服务器进行身份校验” 输入POP3地址和断口
下面是具体的 RCPT_TO 控制程序:
if (SMTP_FILTER) { ip_check_result = Lookup_IP_In_SMTP_SourceIP_List(...); if (ip_check_result=='n') goto smtp_blocked; dest_domain_check_result = Lookup_dest_domain_in_SMTP_DestDomain_List(...); if (dest_domain_check_result=='n') goto smtp_blocked; if (ip_check_result=='y') goto smtp_ok; if (smtpauth_succeeded) goto smtp_ok; } if (SMTP_ANTISPAM_CHECK) { if (test_for_IP_in_antispam_rbl(...)) goto smtp_blocked; } if (SMTP_FILTER) { if (dest_domain_check_result=='y') goto smtp_ok; if (SMTP_AFTERFILTER_AUTH) { if (smtpauth_succeeded) goto smtp_ok; else goto smtp_blocked; } if (SMTP_AFTERFILTER_ALLOW) goto smtp_ok; if (SMTP_AFTERFILTER_BLOCK) goto smtp_blocked; }
[ SMTP AntiVirus&Misc options (licensed only)] AntiVirus: Scan with Sophos
AntiVirus: Scan with AVG (Removed since Grisoft won't support me)
Misc: Add Recieved Header: Sample: Received: from <helo> ([<ip>])\r\n\tby <thishost> with PortTunnel;\r\n\t<datetime>\r\n Options: <datetime> rfc822 date+time <ip> remote ip <helo> helo/ehlo <thishost> hostname that porttunnel is running on <mailfrom> <rcptto> [ end SMTP AntiVirus&Misc options ]
[ SSL 有关选项 ] read all the legal stuff about openssl on www.openssl.org, and make sure you are allow to do this first .... :-)
[old] download http://www.modssl.org/contrib/openssl-0.9.6c-win32.zip[old] and place libeay32.dll and ssleay32.dll in the same folder as [old] porttunnel.exe. If the files are found the message 'OpenSSL not found' [old] is replaced by the OpenSSL version found and its release date.
[new] openssl 0.9.7 dlls are now included in the standard msi of PortTunnel [new] Note: the 0.9.6 dlls will not work with porttunnel anymore.
connection from client to porttunnel: the following values are for connections between a client, e.g. a webbrowser, and porttunnel.
connection from porttunnel to server: the following values are for connections between porttunnel and a server, e.g. a werbserver.
note: if the connection from the server is already encrypted and the client should use the servers encryption and server certificates, you should choose the encryption method none at this point, to keep the original encryption.
method: choose an encryption methode out of none, ssl v2, ssl v3, ssl v2/3, tls v1.
ciphers: choose some ciphers out of EXPORT:@STRENGTH and ALL:@STRENGTH or enter others by yourself (further information at www.openssl.org).
certificate: enter the FULL PATH to your certificate file and choose the correspondending format from the listbox. Please make sure the security (under NTFS) is set right.
key: enter the FULL PATH to your key file and choose the correspondending format from the listbox. Please make sure the security (under NTFS) is set right. If the key is stored in the certificate file, you can leave this field blank.
password: if the private key has a password, enter it here. you can also remove the password out of the key file by entering "openssl rsa -in key.pem -out key.pem". this process needs you to enter the password once.
how to make a "self signed" certificate: grab openssl.exe from the above zip or compile it from the source on www.openssl.orgplace it, and the two dlls in a folder along with openssl.cnf (grabbed from the source tar on openssl.org)
openssl req -new -x509 -newkey rsa:1024 -nodes -days 9999 -config openssl.cnf -out steelbytes.pem -keyout steelbytes.pem
Country Name (2 letter code) []: AU
State or Province Name (full name) []: Victoria
Locality Name (eg, city) []: Melbourne
Organization Name (eg, company) []: www.SteelBytes.com
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []: *.steelbytes.com
Email Address []:
how to then test it:
openssl s_server -accept 443 -cipher ALL:@STRENGTH -www -bugs -cert steelbytes.pem
start https://www.steelbytes.com/
notes: Internet Explorer seems to preffer SSL v2/3 I don't currently distribute compiled versions of the openssl dll files for legal reasons (I've gotta look into if it's ok in Australia) tested with, 0.9.6c dlls from modssl.org, and 0.9.6d (compiled with VS.NET) Refer to the following URL to learn how to get your MS IIS keys working with openssl (replace ssleay through openssl there): http://www.thawte.com/support/server/msiis4.html#iistossl* Refer to the following URL to learn more about the pem format in conjunction with ssl certs bought from a CA: http://www.thawte.com/support/server/apachessl.html#pemcert
[ 日志文件和状态选项 ] 日志: 将连接信息写入日志文件,可以包含错误信息、警告信息、连接信息以及全部信息。
记录所有数据: 将所有传入、传出数据全部记录到指定的目录内,每个连接建立一个文件。
记录连接状态: 将连接信息(连接数、禁止数、数据量等)写入文件。
日期格式: d Day of month as digits with no leading zero for single-digit days dd Day of month as digits with leading zero for single-digit days. ddd Day of week as a three-letter abbreviation. dddd Day of week as its full name. M Month as digits with no leading zero for single-digit months. MM Month as digits with leading zero for single-digit months. MMM Month as a three-letter abbreviation. MMMM Month as its full name. y Year as last two digits, but with no leading zero for years less than 10. yy Year as last two digits, but with leading zero for years less than 10. yyyy Year represented by full four digits. gg Period/era string. This element is ignored if the date to be formatted does not have an associated era or period string. For example, to the following Wed, Aug 31 94 use the following string dd',' MMM dd yy
时间格式: h Hours with no leading zero for single-digit hours; 12-hour clock hh Hours with leading zero for single-digit hours; 12-hour clock H Hours with no leading zero for single-digit hours; 24-hour clock HH Hours with leading zero for single-digit hours; 24-hour clock m Minutes with no leading zero for single-digit minutes mm Minutes with leading zero for single-digit minutes s Seconds with no leading zero for single-digit seconds ss Seconds with leading zero for single-digit seconds t One character time marker string, such as A or P tt Multicharacter time marker string, such as AM or PM For example, to get the following 11:29:40 PM use the following string hh':'mm':'ss tt
[ 其它选项 ] 启用空闲自动断开: 客户端空闲自动断开的连接时间(秒)
启用每个连接传入/出速度限制(KB/s): 每个连接的最大使用带宽
启用每个映射传入/出速度限制(KB/s): 每个(当前)映射的最大使用带宽
缓冲区大小(KB): 然感觉PortTunnel影响了吞吐量(连接数巨大时),则试着增加缓冲区
同时连接数限制: 当前映射的最大同时连接数量
每个IP的同时连接数限制: 每个IP的最大同时连接数量
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)










